When looking at cloud scale and high speed data networks, the trend is to monitor and trigger events for suspicious flows based on NetFlow and IP Flow Information Export (IPFIX). Most network devices, routers/switches, and firewalls support NetFlow and IPFIX. These flow methods make the data traffic passing through devices visible. You can relate these methods to Wireshark capture, which holds information such as source IP, destination IP, and TCP/UDP ports. Wireshark capture works in a similar way to a phone call recording, while flows are the call logs containing metadata information. A flow reporting system continuously monitors flows and has the ability to connect host reputation databases in order to check any odd traffic patterns:
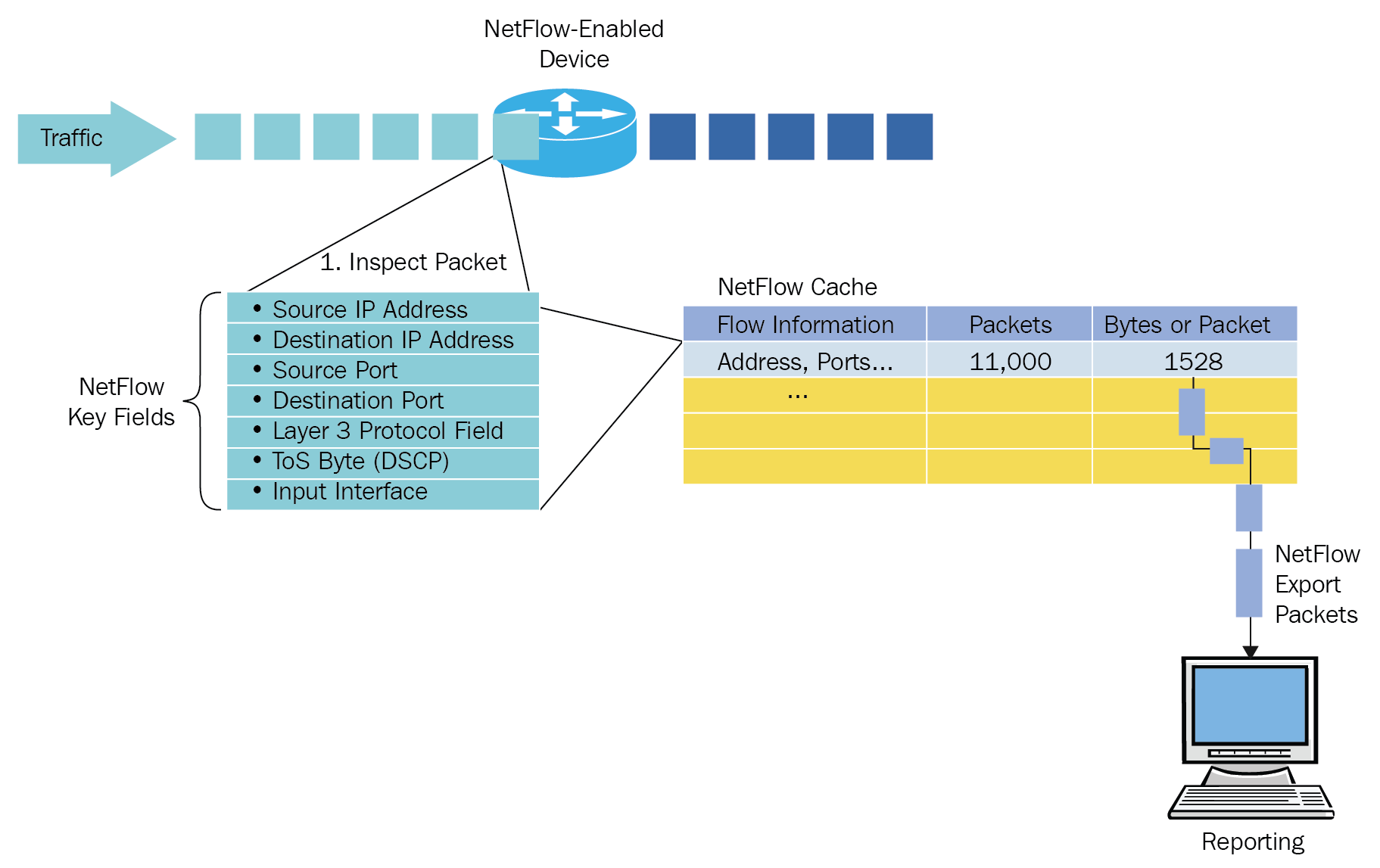
On a Cisco router, this configuration can be done for NetFlow v9. Before the release of NetFlow v9, flows were limited to roughly 20 common fields and the rest of the packet contents were discarded. The introduction to NetFlow v9 made it possible for data export logic to be used for any details found within a packet:
match ipv4 protocol
match ipv4 source address
match ipv4 destination address
match transport source-port
match transport destination-port
match interface input
collect routing source as
collect routing destination as
collect transport tcp flags
collect interface output
collect counter bytes
collect counter packets
Let's assume that you are exporting TCP flag information along with traffic flow, and you also know the source and destination for network flows. Having this information makes it easy to detect SYN (a TCP flag) attacks. With flow technologies, cyber threat detection focuses primarily on monitoring traffic behavior rather than performing DPIs (such as a firewall) and triggering events based on a threat signature match. DPI methods do not scale very well for large infrastructures, such as cloud service providers, in which traffic comes in Tera/Peta bits per second. Due to a lack of traffic handling capabilities, this makes it almost impossible to scan all traffic with expensive equipment, such as firewall and IPS systems.