BGP FlowSpec is a new method defined in RFC 5575 that can be used to prevent DDoS attacks in an automated fashion by leveraging BGP. The BGP flow specification (FlowSpec) feature allows you to automatically propagate the filtering and policing functionality to service a provider's upstream BGP peer routers. This will mitigate the effects of a DDoS attack on your network. Most vendors still have this implementation in their roadmaps. For support, please check with ISP before implementing this solution.
BGP FlowSpec uses a more granular approach and provides you with the flexibility to effectively construct instructions to match a particular data flow with source, destination, L4 parameters, and packet specifics, such as length, and fragment. In this example, the customer router (which is the FlowSpec router) advertises these flows to the ISP edge routers. These edge routers then install the flows in the hardware. Once the flow is installed in the hardware, the transit routers are able to do a lookup to see if incoming traffic matches the defined flows and take appropriate action.
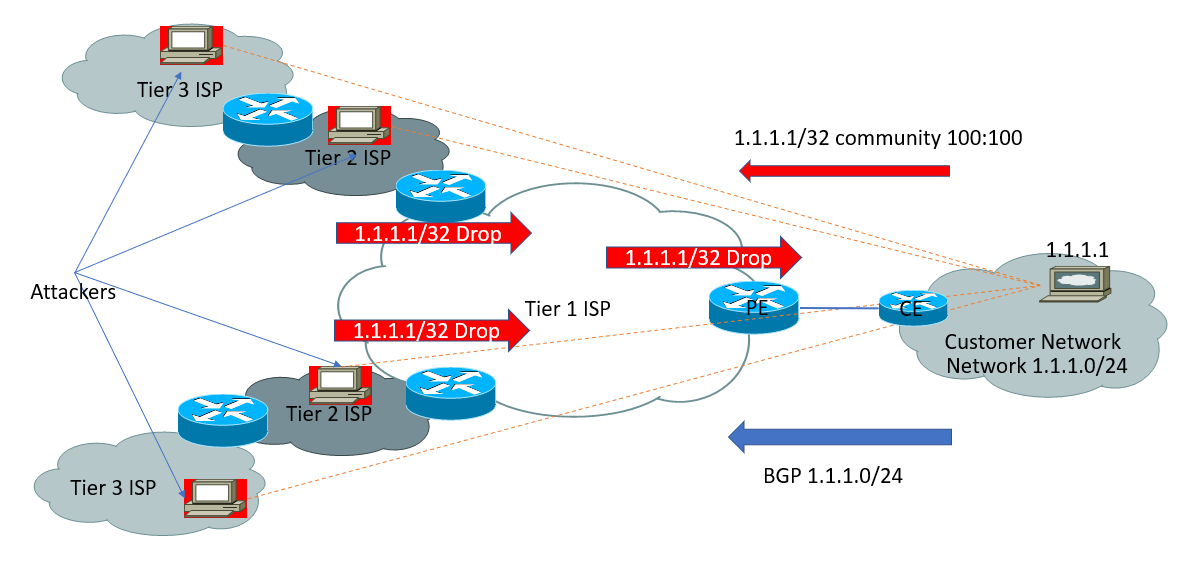
In the following diagram, a customer advertises the 1.1.1.1/32 host network with special community 100:100 to the service provider. Once this community is matched at the service provider end, all the traffic destined for the customer network will be dropped by all edge routers within service provider 1.
These are the specifications for BGP FlowSpec and the list of actions that can be taken.
BGP FlowSpec can include the following information:
- Type 1–Destination Prefix
- Type 2–Source Prefix
- Type 3–IP Protocol
- Type 4–Source or Destination Port
- Type 5–Destination Port
- Type 6–Source Port
- Type 7–ICMP Type
- Type 8–ICMP Code
- Type 9–TCP flags
- Type 10–Packet length
- Type 11–DSCP
- Type 12–Fragment Encoding
Actions are defined using BGP Extended Communities:
- Traffic-Rate (drop/police)
- Next-hop Redirect
- VRF Redirect
- DHCP Marking