Chapter 15. Techniques Used by Attackers
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
 Understand the basic techniques used by hackers.
Understand the basic techniques used by hackers.
 Be able to formulate strategies to defend against common attacks.
Be able to formulate strategies to defend against common attacks.
 Understand how to use some hacking tools.
Understand how to use some hacking tools.
Introduction
This book is about network defense. However, I am a strong proponent of the idea that you should “know your enemy.” Put another way, how can you truly defend against attacks if you do not understand those attacks? I often advise network security students to become familiar with at least the basics of hacking techniques. The purpose of this chapter is to introduce you to the basics. No, reading this chapter won’t make you a skilled hacker, but that is not the goal. What it will do for you is make you familiar with some common attacks.
Before you can try to understand the mentality of the hacking community you must first know what the term hacker means. Most people use it to describe any person who breaks into a computer system. In the hacking community, however, a hacker is an expert on a particular system or systems, a person who simply wants to learn more about the system. Hackers feel that looking at a system’s flaws is the best way to learn about that system. For example, someone well-versed in the Linux operating system who works to understand that system by learning its weaknesses and flaws would be a hacker.
This process does often mean seeing whether a flaw can be exploited to gain access to a system. This “exploiting” part of the process is where hackers differentiate themselves into three groups:
 A white hat hacker is usually called a penetration tester today. It is someone who is hacking with permission of the owners of the target system. This is actually a good idea. Have a skilled person test your network’s defenses.
A white hat hacker is usually called a penetration tester today. It is someone who is hacking with permission of the owners of the target system. This is actually a good idea. Have a skilled person test your network’s defenses.
 A black hat hacker is the person normally depicted in the media. After she gains access to a system, her goal is to cause some type of harm. She might steal data, erase files, or deface Web sites. Black hat hackers are sometimes referred to as crackers.
A black hat hacker is the person normally depicted in the media. After she gains access to a system, her goal is to cause some type of harm. She might steal data, erase files, or deface Web sites. Black hat hackers are sometimes referred to as crackers.
 A gray hat hacker is normally a law-abiding citizen, but in some cases will venture into illegal activities. Some sources give an alternative definition, of someone who was formerly a black hat hacker and has changed.
A gray hat hacker is normally a law-abiding citizen, but in some cases will venture into illegal activities. Some sources give an alternative definition, of someone who was formerly a black hat hacker and has changed.
Regardless of how hackers view themselves, intruding on any system without permission of the system owner is illegal. Also, regardless of the motivation behind the intrusion, the methods are usually the same.
Preparing to Hack
Skilled hackers rarely simply start an attack. They first want to gather information about the target before attacking. This is akin to a skilled bank robber first casing the bank to learn all he can before actually trying to rob it. A skilled hacker wants to understand everything he can about the target organization and its system. This preparation phase is important. It is also a reason why a security-conscious organization should be very careful about what information is allowed in public.
Passively Searching for Information
The first step in any computer attack is a passive search. This is any attempt to gather information that does not actually involve connecting to the target system. If the target system has firewall logs, an intrusion detection system (IDS), or similar capabilities, then an active scan might alert the company. The first step is to simply search the Web for the organization in question. You might discover that it has an announcement stating a move to a new router model, or that it uses IIS 7.0 for its web server. Any information about the target system enables the attacker to narrow his search for vulnerabilities. In the second example, he can now simply search for “security flaws in IIS 7.0” or some similar search term.
The possibility also exists that the attacker will learn about people in the organization. Knowing actual names, phone numbers, office locations, and so on can aid in a social engineering attack. The more information one has on a target organization, the easier the attack will be.
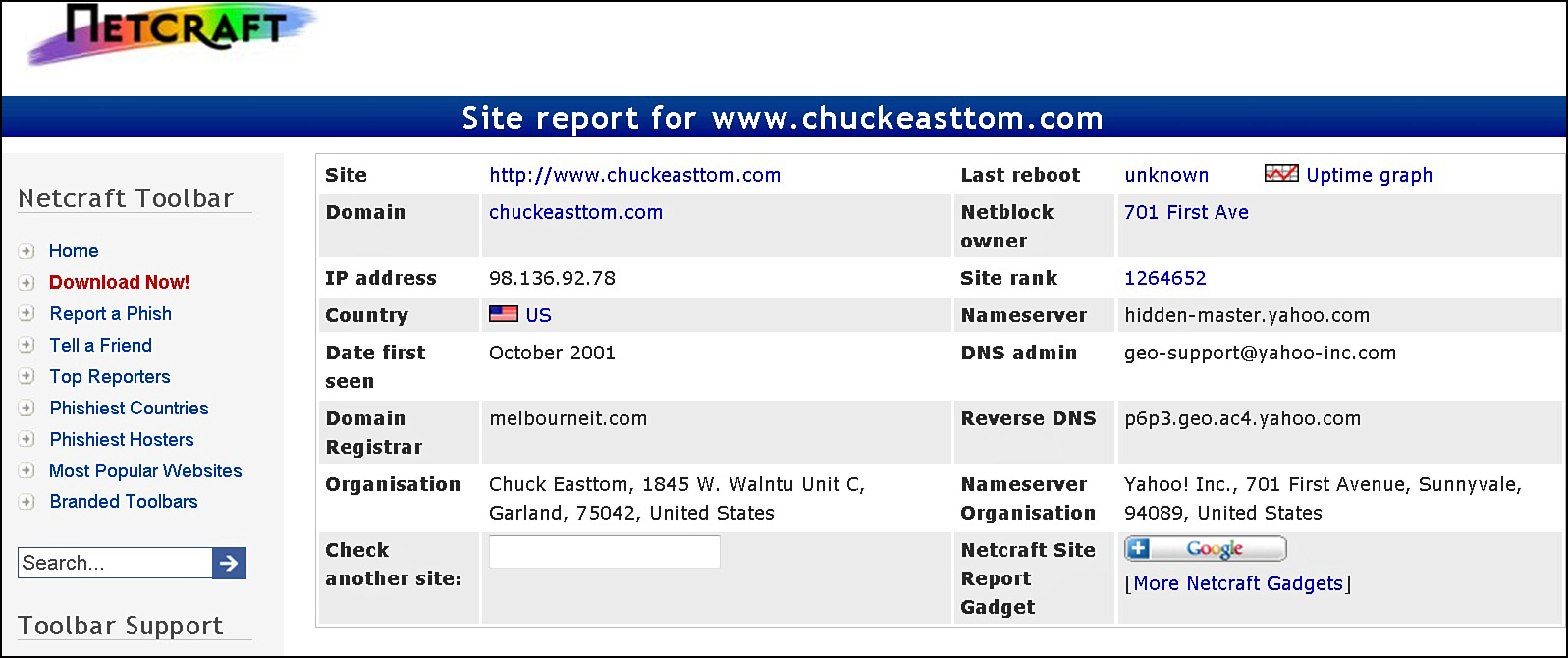
Several Web sites can help with this. The website www.NetCraft.com, shown in Figure 15.1, can provide information about a target web server.
This website gives information regarding the web server and operating system being used by a specific website. This helps him to decide what sort of attack to attempt. The attacker might also be able to see the last time the system was rebooted. Patches and upgrades often require a reboot, so this information will tell him whether the system has been patched recently. Best of all, from the intruder’s point of view, this is all done without the attacker directly accessing the target system.
One can also get a lot of information from the Web site www.Archive.org (see Figure 15.2). This Web site archives all the Web sites on the Internet. You can then view how that Web site looked at a previous point in time.

FIGURE 15.2 Archive.org.
By looking at older versions of the website an attacker might learn of changes in the company. For example, if the company lists personnel and it shows a different security director every year, that information is very useful. It shows high turnover. That means the current director is new, might not fully understand the systems, and also might be more focused on keeping his job than on the details of security.
Frankly, any information you find on the Web might be useful. Disgruntled employees might complain in a chat room. Perhaps technical personnel like to discuss problems/issues on discussion boards, and in doing so reveal key information about the target system.
Active Scanning
Although passive scanning can yield a lot of useful information, at some point the attacker needs to do an active scan, which involves some level of actual connection to the target system. It is the most likely to be detected, but also the most likely to yield actionable information:
 Port scanning: This is a process of scanning the 1024 well-known ports or even all the ports (there are 65,535) and seeing which ports are open. This can tell an attacker a great deal. For example, port 161 indicates the target is using Simple Network Management Protocol, which might provide a vulnerability that can be exploited. Port 88 tells an attacker that the target system uses Kerberos authentication.
Port scanning: This is a process of scanning the 1024 well-known ports or even all the ports (there are 65,535) and seeing which ports are open. This can tell an attacker a great deal. For example, port 161 indicates the target is using Simple Network Management Protocol, which might provide a vulnerability that can be exploited. Port 88 tells an attacker that the target system uses Kerberos authentication.
 Enumerating: This is a process whereby the attacker tries to find out what is on the target network. Items such as shared folders, user accounts, and similar items are sought after. Any of these can provide a point of attack.
Enumerating: This is a process whereby the attacker tries to find out what is on the target network. Items such as shared folders, user accounts, and similar items are sought after. Any of these can provide a point of attack.
 Vulnerability assessment: This is the use of some tool to seek out known vulnerabilities. The attacker might also try to manually assess vulnerabilities. The latter can be done in many ways. We discuss one of these methods later in this section.
Vulnerability assessment: This is the use of some tool to seek out known vulnerabilities. The attacker might also try to manually assess vulnerabilities. The latter can be done in many ways. We discuss one of these methods later in this section.
A number of tools are freely available on the Internet for active scanning. They range from the very simple to the complex. Anyone involved in preventing computer crimes, or investigating computer crimes should be familiar with a few of these. We will examine a few of them later in this section.
When you are doing a port scan, you have a number of options. The most common types of scans and their limitations are as follow:
 Ping scan: This scan sends a ping packet to the target IP address. This is to check to see whether a given port is open. The problem with ping scanning is that many firewalls block ICMP packets. Internet Control Message Protocol (ICMP) is the protocol used by ping and tracert (traceroute for Unix/Linux users).
Ping scan: This scan sends a ping packet to the target IP address. This is to check to see whether a given port is open. The problem with ping scanning is that many firewalls block ICMP packets. Internet Control Message Protocol (ICMP) is the protocol used by ping and tracert (traceroute for Unix/Linux users).
 Connect Scan: This type of scan actually tries to make a full connection to the target IP address at a given port. This is the most reliable type of scan. It will not yield false positives or false negatives. However, it is the scan most likely to be detected by the target network.
Connect Scan: This type of scan actually tries to make a full connection to the target IP address at a given port. This is the most reliable type of scan. It will not yield false positives or false negatives. However, it is the scan most likely to be detected by the target network.
 SYN Scan: This scan is based on knowledge of how network connectivity works. Any time you connect to any server an exchange of packets negotiates the connection. Your machine sends a packet with a SYN flag, which means synchronize. Basically you are asking permission to connect. The server responds with a packet that has a SYN-ACK flag, a synchronize-acknowledge. That is the server saying “ok, you can connect.” Your computer then sends a packet with an ACK flag, acknowledging the new connection. A SYN scan simply sends a connection request to each port. This is to check to see whether the port is open. Because servers and firewalls routinely get SYN packets, this is unlikely to trigger any alarms on the target system.
SYN Scan: This scan is based on knowledge of how network connectivity works. Any time you connect to any server an exchange of packets negotiates the connection. Your machine sends a packet with a SYN flag, which means synchronize. Basically you are asking permission to connect. The server responds with a packet that has a SYN-ACK flag, a synchronize-acknowledge. That is the server saying “ok, you can connect.” Your computer then sends a packet with an ACK flag, acknowledging the new connection. A SYN scan simply sends a connection request to each port. This is to check to see whether the port is open. Because servers and firewalls routinely get SYN packets, this is unlikely to trigger any alarms on the target system.
 FIN scan: This scan has the FIN flag, or connection finished flag set. This is also usually not going to attract unwanted attention at the target network because connections are being closed routinely, so packets with the FIN flag set are not unusual.
FIN scan: This scan has the FIN flag, or connection finished flag set. This is also usually not going to attract unwanted attention at the target network because connections are being closed routinely, so packets with the FIN flag set are not unusual.
Other scans include the Null scan, with no flags set, and the XMAS scan, with several flags set. Whatever the specific scan used, most will leave some trace of the attack in the server or firewall logs.
NsAudit
NSAudit is a popular and flexible tool. It can be challenging for a novice to learn. You can download it for free at http://www.nsauditor.com/. The opening screen, shown in Figure 15.3, should make it obvious the additional choices that are available.
FIGURE 15.3 NSAudit opening screen.
Let’s take a look at some of the more commonly used options. Click Network Scanner to open it; see Figure 15.4.

FIGURE 15.4 NSAudit Network Scanner.
You can also select the type of scan, as shown in Figure 15.5.
FIGURE 15.5 Selecting scan type.
You can also set the aggressiveness level of the scan, as shown in Figure 15.6. The aggressiveness level determines how many times per minute to scan ports, as well as how many ports to simultaneously scan. The more aggressive the scan, the quicker the results, but the more likely one is to trigger an alarm on the target system.

FIGURE 15.6 Scan aggressiveness level.
The ability to select both type of scan and the level of aggressiveness is one thing that makes NSAudit such a flexible and useful tool.
On the Tools drop-down menu is Remote Explorer, shown in Figure 15.7.

FIGURE 15.7 Remote Explorer.
Remote Explorer tool allows you to attempt to connect to another computer either using your current log-on credentials or some others. This tool is excellent for simply trying to connect and checking to see whether you can access a remote system.
Enumerating
Enumeration is simply finding out what computers, shared folders, and users are on a given network or machine. It requires connection to that target machine or network. Many of the port scanners mentioned also allow the attacker to perform enumeration. Tools are also available that just do enumeration. Let’s first look at the enumeration capabilities within NSAudit. If you search under Tools, you will find a button labeled Enumerate Computers, shown in Figure 15.8.

FIGURE 15.8 NSAudit Enumerate Computers button.
Click it to see a number of choices as to what you want to enumerate, as shown in Figure 15.9.

FIGURE 15.9 NSAudit enumeration choices.
You can choose to enumerate all computers, or just the domain controller, or servers, or MS SQL database servers. As you can see you have a number of choices. When you run the enumerator the output is in XML format as shown in Figure 15.10.

FIGURE 15.10 NSAudit enumeration results.
You can see that a great deal of information is provided about every computer on that network. You get a list of all the computers on the network, and you can see what services they are running. Any running service is a potential attack vector.
Other enumeration products enumerate only one thing. For example, ShareEnum, available for download from http://technet.microsoft.com/en-us/sysinternals/bb897442.aspx, simply tries to find all shared folders on the network. This can be useful because a shared folder is a possible attack vector for the hacker to use. You can see ShareEnum in Figure 15.11.

FIGURE 15.11 ShareEnum.
Another good enumeration tool is FreeNetEnumerator also available from the NSAudit Web site. It has a simple, easy-to-use interface, which you can see in Figure 15.12.
FIGURE 15.12 FreeNetEnumerator.
You can see that FreeNetEnumerator provides the same information NSAudit provides, but in an easy-to-read format (see Figure 15.13). This tool is made for someone who is a novice at enumeration.

FIGURE 15.13 FreeNetEnumerator results.
These are just a few enumeration tools available on the Internet. After an attacker has access to your network, then he can use one of these tools to map out the rest of the network and learn what computers, servers, shared folders, and users are on that network. He can also learn what operating system is being used on each machine. This valuable information enables the attacker to plan out his attack.
Manual Scanning
There are also manual ways to scan a system for vulnerabilities. Perhaps the most commonly used is the telnet command, which works in Linux or Windows and is used to attempt to connect to a machine in order to perform administrative tasks. By default, telnet uses port 23. However, you can attempt to telnet into any port you want. You simply open a command window, and type in telnet, the address or URL you want to telnet into, and the port number. It will look something like what you see in Figure 15.14.

FIGURE 15.14 telnet.
This is an excellent scanning tool because not only does it tell you whether a port is open, but it also tells you whether you can log on to that port, thus providing the attacker a way into the system. The results could be one of two:
 You are informed you could not connect.
You are informed you could not connect.
 The screen goes blank, indicating it is ready for commands (that is, you did connect).
The screen goes blank, indicating it is ready for commands (that is, you did connect).
Even if you can connect, you still might only have very limited access. The next thing a hacker will attempt, if this is a web server, is to retrieve the banner so that he knows for certain what operating system is being used. You do that by typing in HEAD /HTTP/1.0 and then press Enter twice. If the retrieval is successful the hacker will know precisely what operating system is being used.
The Attack Phase
After passive scanning, port scanning, enumerating, and gathering information about the target site, the attacker will be ready to actually attack the target system. This is the part where he or she applies the knowledge gained in the scanning phases.
Physical Access Attacks
If an attacker can physically sit in front of any machine connected to your network, there are a number of ways he can use that to gain access to your entire network. His first step is simply to be able to log on to that machine. He need not be able to log on to the network yet, just that machine. Let’s look at a few techniques that would allow an attacker to log on to a machine, even if he does not have a password.
Bypassing the Password
One exciting way to break into Windows computers is to simply bypass the password all together. You don’t find out what the password is; you just skip it. It basically requires about 5 minutes at the workstation with a Linux live CD. Here are the steps:
1. Use any Linux boot disk. Some people prefer one distribution over another but it really does not matter.
2. Boot to the CD.
3. After booting into Linux, find and access the NTFS volume (that is, the Windows wolume). The following commands will do this (note your NTFS volume might not be sda1; this is just used for an example).
fdisk -l | grep NTFS
mkdir -p /mnt/windows
mount -t ntfs-3g /dev/sda1 /mnt/windows
4. Move to the Windows System 32 directory and make a backup copy of the magnify application. This is shown here.
cd /mnt/windows/Windows/System32
mv Magnify.exe Magnify.bck
5. Make a copy of cmd.exe (the command prompt) and change its name to Magnify.exe.
cp cmd.exe Magnify.exe and reboot
6. Reboot into Windows (whatever version is on that workstation). When the machine boots up, instead of logging in, choose Accessibility Options and ‘magnify’.
What launches is a command prompt with system-level privileges.
Using OphCrack
One popular tool for getting into a machine locally is OphCrack, which you can download from http://ophcrack.sourceforge.net/. It is based on an understanding of how Windows passwords work. Windows passwords are stored in a hash file in one of the system directories, usually C:\WINDOWS\system32\config\ in a Security Accounts Manager (SAM) file. Because the file contains hashed entries, you could not simply read the user names and passwords. If you simply try random passwords, most systems will lock you out after a few tries, so it would be great if you could get the SAM file away from Windows and try to crack it. However, it is a locked file. The operating system will not let you copy it or do anything with it. What OphCrack does is boot the system in Linux so that the Windows operating system is not loaded, and the SAM file is not protected. It then uses a process called a rainbow table to crack the entries in the SAM. A rainbow table is a table of all possible hashes of all possible character combinations. OphCrack just searches the SAM for a match. When it finds it, it knows the username and password, as shown in Figure 15.15.

FIGURE 15.15 OphCrack.
Note that this screenshot was taken from a live machine, so all nonstandard user accounts and all passwords have been redacted. To make this work, all you have to do is put the CD into the system and reboot. During the boot-up process, press F12 for a boot menu, then choose Boot from CD. After the attacker has a valid login account, particularly an administrator account, he can log on to that computer. This won’t let him join the domain, but he now has a foothold on your network.
Tricking Tech Support
After gaining access to a local account, perhaps using one of the techniques mentioned earlier, the attacker will want to get domain admin privileges. The Net User command can help do this via the following two-line script:
net user /domain /add localaccountname password
net group /domain "Domain Admins" /add localaccount
By saving that script in the All Users startup folder and getting a domain admin to log on to this machine, the script will run (in the background, not visible) and the local account will now be a domain admin. How do you get a domain admin to log on? In many organizations, the tech support personnel are in the domain admin group. So the attacker now merely needs to do something to render the machine not fully operational. When a tech support person logs on to fix that problem, the script runs.
Remote Access Attacks
Obviously, physical access to a workstation on the target network is not always possible. Although remote attacks are far less likely to succeed, they still have the potential to succeed. A number of possible remote attack methods exist, but this section focuses on a couple of the most common: SQL injection and cross-site scripting.
SQL Injection
SQL injection is a popular attack against Web applications. A login screen requires a username and password, which must be checked against a database to see whether they are valid. All databases speak Structured Query Language (SQL). If the programmer who created the login is not careful it might be susceptible to SQL injection. Here is how that attack works. SQL looks a lot like English. For example, to check a username and password an intruder might want to query the database and see whether any entry in the users table matches the username and password that was entered. If there is, then a match exists. The SQL in the programming code for the Web site has to use quotation marks to separate the SQL code from the programming code. So you might have something that looks like this:
'SELECT * FROM tblUsers WHERE USERNAME = '" + txtUsername.Text +' AND PASSEORD = '" +
txtPassword.Text +"'"
Entering username 'admin' and password 'password' code produces the SQL command:
SELECT * FROM tblUsers WHERE USERNAME = 'admin' AND PASSWORD = 'password'
SQL injection adds something at the end of the password. For example, entering 'password ' OR X=X' causes the program to create this query:
SELECT * FROM tblUsers WHERE USERNAME = 'admin' AND PASSWORD = 'password' OR X=X'
This tells the database and application to allow login if there is a match for a username and password, or if X=X, which it always will. Now if the programmer wrote the login properly, this method will not work—but in all too many cases it does work. And then the intruder has logged into your web application and can do whatever any authorized user can do.
After the attacker has logged in, he might want to enumerate the other accounts rather than just the first by putting this in the username box (and keeping the password box the same). Assuming the first user found was named ‘john’, then finding the next user with this SQL statement is possible with
' or '1' ='1 and firstname <> 'john
or by trying
' or '1' ='1 and not firstname = 'john
Obviously, firstname might not be a name of a column in that database. An intruder might have to try various permutations to get one that works. Also remember MS Access and SQL Server allow multi-word column names with brackets (that is, [First Name]) but MySql and PostGres do NOT accept brackets.
An attacker can continue this method with other names blocked (as he finds them) by putting these names in the username box (keeping the password box the same).
' or '1' ='1 and firstname <> 'john' and firstname <> ' bob
or by trying:
' or '1' ='1 and not firstname = 'john' and not firstname = 'john
Beyond enumerating users, one can send over pretty much any SQL statements. Here are a few examples:
x'; DROP TABLE users; --
rather than ' or '1' ='1 that deletes the table 'users'.
Many database servers have built-in email; one can get the server to e-mail the password as follows:
x'; UPDATE members SET email = 'me@somewhere.net' WHERE email = 'somebody@example.com
SQL injection is a serious problem. However, you can easily counter it by simply having all user input filtered.
Cross-Site Scripting
An attacker injects client-side script into web pages viewed by other users. The term cross-site scripting originally referred to the act of loading the attacked, third-party web application from an unrelated attack site, in a manner that executes a fragment of JavaScript prepared by the attacker in the security context of the targeted domain.
Essentially, an attacker enters scripts into an area that other users interact with. So that when they go to that part of the site, the attacker’s script runs, rather than the intended Web site functionality. This can include redirecting users.
Summary
As you can see hackers can use a number of techniques to compromise your system and this chapter shows just a few of them. Some require physical access to some machine on your network, others are remote attacks. Increased awareness of these attack methods leads to better defense against them. Spending some time studying hacking techniques is advisable for all network security professionals.
Test Your Skills
Multiple Choice Questions
1. What does the following command do?
Telnet <IP Address> <Port 80>
HEAD /HTTP/1.0
<Return>
<Return>
A. This command returns the home page for the IP address specified.
B. This command opens a backdoor Telnet session to the IP address specified.
C. This command allows a hacker to determine the sites security.
D. This command returns the banner of the website specified by IP address.
2. If you send a SYN to an open port, what is the correct response?
A. SYN
B. ACK
C. FIN
D. SYN/ACK
3. You scan a target network and find port 445 is open and active. What does this tell you?
A. The system uses Linux.
B. The system uses Novell.
C. The system uses Windows.
D. The system has an IDS.
4. Julie has been hired to perform a penetration exam on Examsheets.net. She begins by looking at IP address ranges owned by the company and details of domain name registration. She then goes to news groups and financial Web sites to see whether any of the company’s sensitive information or technical details are online. What is Julie doing?
A. Passive information gathering
B. Active information gathering
C. Attack phase
D. Vulnerability mapping
5. John has performed a scan of the web server with NMAP but did not gather enough information to accurately identify which operating system is running on the remote host. How could he use a web server to help in identifying the OS that is being used?
A. Telnet to an open port and grab the banner
B. Connect to the web server with an FTP client
C. Connect to the web server with a browser and look at the web page
D. Telnet to port 8080 on the web server and look at the default page code
6. You are carrying out the last round of testing for your new Web site before it goes live. The Web site has many subpages and connects to a SQL Server backend that accesses your product inventory in a database. You come across a web security site that recommends inputting the following code into a search field on web pages to check for vulnerabilities:
<script>alert("Test My Site.")</script>
When you type this and click on search, you receive a pop-up window that says:
" Test My Site."
What is the result of this test?
A. Your Web site is vulnerable to web bugs.
B. Your website is vulnerable to cross-site scripting.
C. Your website is vulnerable to SQL injection.
D. Your website is not vulnerable.
7. The tool OphCrack does what?
A. Decrypts Windows passwords
B. Performs a rainbow table attack
C. Brute-force attacks Windows
D. Blanks out the password
8. Which of the following is the most reliable type of scan?
A. Syn
B. Passive
C. Fin
D. Connect
9. Trying to identify the machines on a target network is called _____.
A. Enumeration
B. Scanning
C. Checking
D. Assessing
Exercises
Exercise 15.1: OphCrack
Use OphCrack to crack the passwords on your own workstation.
Exercise 15.2: Bypassing the password
Use a Linux Live CD to bypass the password on either your own computer or a lab computer.
 Understand the basic techniques used by hackers.
Understand the basic techniques used by hackers. Be able to formulate strategies to defend against common attacks.
Be able to formulate strategies to defend against common attacks. Understand how to use some hacking tools.
Understand how to use some hacking tools.