Keeping your army secret
Introduction
Having someone discover one of your hacking drones can lead to an unplanned and early end to a penetration test. This can really ruin your day and possibly your reputation as a penetration tester. Devices must be initially placed, maintained, and ideally removed without alerting anyone at the target organization. This chapter will discuss several techniques that should lessen the chances of discovery during a penetration test.
There are a few general principles that apply to avoiding detection. Naturally, you need to avoid drawing attention to yourself or your equipment. The LEDs on the BeagleBone Black are very bright. Even if you install a BeagleBone Black inside something, the light might be visible. Recall from a previous chapter that these LEDs can be disabled with the following script:
#!/bin/bash # simple script to turn off all user LEDs echo none > /sys/class/leds/beaglebone\:green\:usr0/trigger echo none > /sys/class/leds/beaglebone\:green\:usr1/trigger echo none > /sys/class/leds/beaglebone\:green\:usr2/trigger echo none > /sys/class/leds/beaglebone\:green\:usr3/trigger
Another general principle is that you need to blend in when operating in the vicinity of your target. This means that nothing should draw attention to you and your activities. You should dress similar to those around you. Your vehicle should blend in. At all times, you must act as though you belong wherever you are.
Hiding Devices
A BeagleBone is a very compact computer. It is not so small as to be undetectable, however. The device must be hidden. There are a number of ways that things might be hidden including in natural objects, in and around structures, and inside toys and trinkets.
Hiding Devices in Natural Objects
When hiding devices outside, you may wish to take advantage of natural objects such as plants. The device must blend in and also be protected from the elements. A small piece of brown or green tarp can be loosely wrapped around the device to protect it from moisture. Take care not to wrap the drone too tightly as this can cause overheating. Use caution when placing a device directly on the ground if there is a chance of significant rain or melting snow during the penetration test.
Don't limit yourself to placing drones at ground level. Trees and other high perches can be great choices for hiding spots. Most people never look up as they are walking to and from their cars and office buildings. A drone can be hidden in a fake birds' nest and the like. If there are evergreen trees nearby, the loose tarp technique can be used. If the target building has multiple stories, be sure to consider what your hidden drone might look like when viewed from above. Outdoor hiding spots are shown in Figures 8.1 and 8.2.


Hiding Devices in and Around Structures
Many buildings offer natural hiding places. If the target is located within the top floors of a building, the roof can be a good location for a few drones. Remember to protect your device from the elements.
Have a look around your target. Do you see any boxes for cable television, phones, power, or anything similar? These could be good places to hide a drone and protect it from the elements at the same time. Be careful not to hide drones in metal boxes as this will prevent wireless communications. The light fixture shown in Figure 8.3 could be used to hide a drone.

Landscape features represent another drone-hiding possibility. Many rocks around buildings are actually hollow composite shells. These are excellent places to hide a drone provided they are not rigidly attached to the ground. A small fake rock of your own could be used, but be careful not to use anything that would stand out as new or out of place.
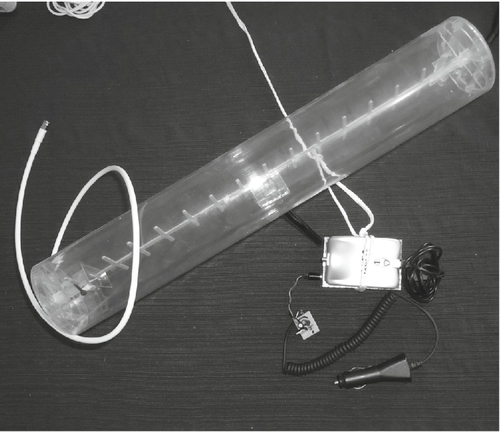
Vehicles represent many opportunities for hiding things. They also feature large batteries that can be used to power drones. Inside of the vehicles, child seats are a great place to put things. A blanket can be thrown on top of equipment in the child seat. Nobody thinks twice about blankets in baby seats. A drone with a unidirectional wireless antenna ready to be installed in a car seat is shown in Figure 8.4.
There are plenty of structures inside that can be used to hide devices as well. Drones can be hidden under desks. There are two basic options for securing drones to desks. If the desks are metal, magnets can be used to secure drones. Magnets can also be used to attach drones to the back of most computers as they tend to have steel cases. Be careful when attaching something to the back of a computer under a desk with a modesty panel that does not reach to the floor. Ensure that your device isn't visible from any likely angle.
The other option is to affix a drone to the bottom of a desk with tape. A dark color duct tape can work well. One downside of this technique is that it might leave residue on your drone cases and/or the furniture. Tape can be a better option when hiding a drone under an unused desk without a computer. Empty desks with active network jacks and available power outlets are your friends. Desk hiding spaces are shown in Figures 8.5 and 8.6.


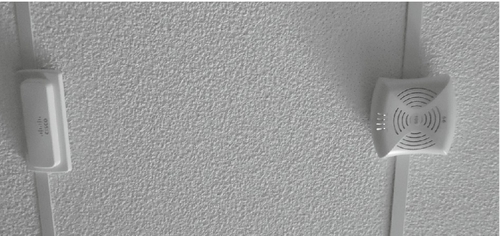
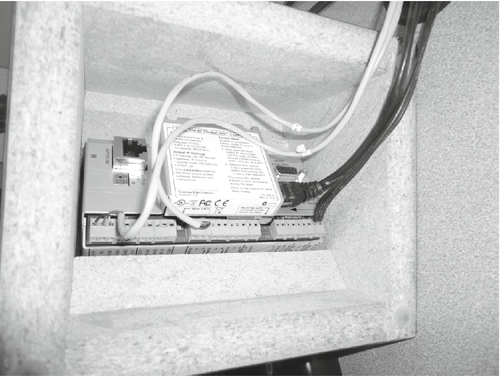
Drop ceilings are very common in office buildings. They allow wires to be run easily, absorb sound, and have other desirable properties. They can also be a great place to hide things such as hacking drones. It is not unusual to have power and network ports available inside a drop ceiling. If the office has any wireless access points or projectors installed in the ceiling, these should be the first places to check for power and network connections. Good starting points for placing drones in drop ceilings are shown in Figures 8.7 and 8.8.

Storage closets can also be useful for hiding drones. If possible, hiding a drone on a high shelf is best. The back of a low shelf is second best if the shelves are not taller than eye level for a tall employee. Wiring closets can also be good as they feature convenient power and network access. When using a wiring closet, try to find something that looks infrequently used to hide your drone behind.
There are other potential hiding places around a typical office. Artificial plants can be used. Before digging in the pots, check to see if there is an artificial bottom. A couple of inches are more than enough to fit a BeagleBone, batteries, and a wireless adapter. If the company has any wall-mounted televisions, there may be enough space behind them to wedge a drone in place. Look around and be creative. Just a few possibilities I noticed while walking around my office building are shown in Figures 8.9–8.15.





Using Toys and Trinkets to Hide Devices
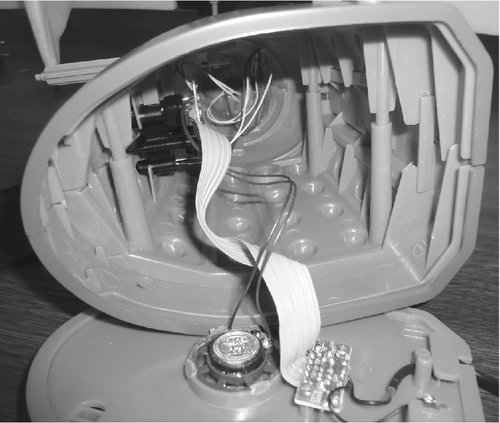
People like their toys. This is especially true of technical people. The best toys for our purposes are powered by USB or wall power. One such toy is the Dalek Desk Defender used in the penetration test in the previous chapter. This toy has more than enough space to house a BeagleBone, XBee radio, and Alfa wireless adapter. The USB power for the toy can also be tapped to power the drone.
The Doctor Who TARDIS 4 Port USB hub is another convenient option for installing a drone into the office of a Doctor Who fan. Other toys such as the talking TARDIS would also work but are less desirable because they are battery-powered. The Dalek Desk Defender and talking TARDIS devices are shown in Figures 8.16–8.18.


Not every office has Doctor Who fans. A little research can tell you what interests your target's employees have. Once you know what kinds of things would be welcome editions to the office or would easily blend in with existing items, you can go shopping for something to implant your drones inside. A store such as ThinkGeek might be a good place to start. Searching on the keyword USB might yield several appropriate items that could provide power to your hidden drones.
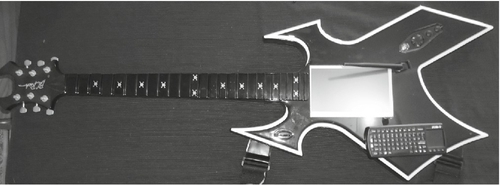
The focus of this chapter has been on hiding hacking drones. Full hacking desktops may also be hidden in toys and other items. In most cases, if you can hide a desktop in something, a drone can also be concealed within the same object. Hacking desktops embedded in other objects are shown in Figures 8.19–8.21.


Installing Devices
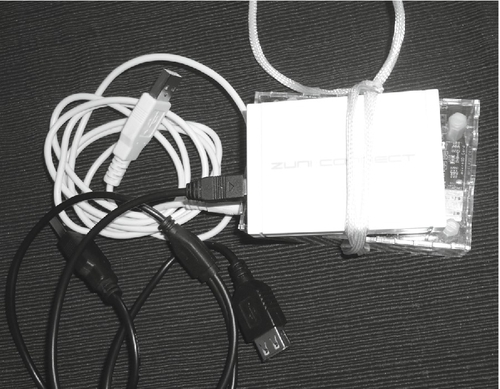
Once you have a plan for where and what kind of devices you are going to plant, it is time to get to work. Devices must be placed while avoiding detection. Battery-powered drones may require maintenance in the form of fresh batteries during an extended penetration test. Ideally, things can be covertly retrieved at the conclusion of the test as well. Drones ready for deployment are shown in Figures 8.22–8.24.
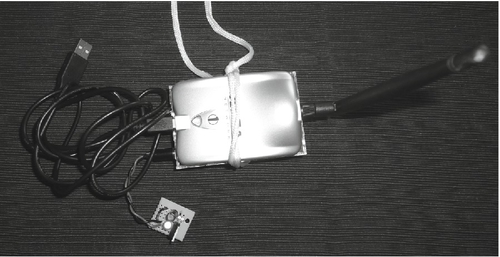
Initial Hiding
In the ideal situation, devices are planted inside when nobody is around. This can be a challenge, however. The building may be locked. It is worth asking your client for keys. Alternatively, you could try out your lock-picking skills. If your client's locks are easily picked, that is something they would likely want to know.
Lock picking and physical penetration testing are beyond the scope of this book. The Open Organisation Of Lockpickers (TOOOL) can be a good source of information (http://toool.us). Deviant Ollam has written two books on lock picking, Practical Lock Picking and Keys to the Kingdom, both published by Syngress, which might prove useful to the novice picker. I do not recommend you attempt to learn lock picking during a penetration test. Only attempt this if you have experience and a reasonable expectation of success.
Merely gaining access after hours may not be enough if there is a security system at the client's office. If the client is unwilling to give up a security code, you might have to find another way to gain access after hours. If this is not easily done, you may have to resort to planting devices while others are present.
Planting devices while other people are around may require some social engineering. My definition of social engineering is pretending to be something you are not in order to get someone to give you something they should not (in this case, access to the facility). There are many good social engineers to learn from in this world. Kevin Mitnick is perhaps one of the better known social engineers. His book The Art of Deception is a highly recommended reading.
Christopher Hadnagy is a more contemporary social engineer. He has written two books on the subject including Social Engineering: The Art of Human Hacking, which has a chapter on pretexting. A good amount of information on pretexting can be found at http://www.social-engineer.org/framework/Social_Engineering_Framework.
Pretexting is the creation of a story that allows you to gain access to a site or information that you would not normally receive. Successful pretexting requires research and planning. What works well in one situation might utterly fail in another. For example, wearing blue coveralls and trying to pass yourself off as being with BellSouth in Atlanta, Georgia, is likely to be much less successful than wearing the same and claiming to be from British Telecom in London.
Successful pretexts can vary widely. One of the simplest pretexts is to pretend to be a customer or potential client. This is not likely to get you much access, but in some cases, it may be enough to plant a drone or two inside the office. If you are going to plant devices in the middle of the day, you need to be quick and discrete. If you are going to risk planting things in the office, you might want to focus on wall or USB-powered devices if your test will run for more than two days (the approximate run time for a drone on D cell batteries).
On the more sophisticated end of pretexts, you might impersonate a worker or job applicant. Getting a job with the cleaning subcontractor might take a while and might be harder than it first appears thanks to bonding issues and government regulations. Leave getting a job as a cleaner or abducting workers to gain access to the facility after hours to the movies.
It is unlikely that most companies will perform any sort of background check prior to interviewing job applicants. Preemployment tests of programming and/or software design skills are fairly common when applying for software positions. Applicants are typically left alone during these tests. Take care not to perform too well on these tests. If you look like a top candidate, it could extend your time in the office with no benefit to you.
While all of the stuff described above might sound like fun, if your target is using wireless networking, it may be unnecessary. I do not want to discourage you from trying to plant a few wired drones. Rather, I would hope you realize that wired drones in the building are not a requirement for a successful penetration test.
Maintaining Devices
Ideally, all drones will run without the need for maintenance for the duration of the penetration test. If your test involves drones running off of batteries smaller than a car battery, you may need to replace power packs every couple of days. If you used the power supplies described in a previous chapter, changing batteries can be as simple as unplugging one battery pack and plugging in a fresh set.
Removing Devices
Hacking drones are relatively cheap, but you probably want them back at the end of the penetration test. True, you could just pick them up after the test is over, and employees at the client organization have found out about the penetration test. There are some downsides to just picking up your equipment later.
People talk. If you let people know all the places you hid your drones and exactly how you went about planting them, they might tell other people. If word starts getting around, it could make things harder for future penetration tests.
Removing your equipment while avoiding detection is a good practice for planting devices on future penetration tests. Coming and going unnoticed can also have a positive impact on your professional reputation. Because there are few, if any, negative consequences of being discovered while retrieving drones at the end of a test, you will likely be more relaxed than during initial planting. When you are relaxed, you draw less attention to yourself, greatly decreasing your chances of discovery.
Summary
In this chapter, a number of techniques for keeping your penetration test secret were discussed. Hopefully, what was presented here will provide food for thought for your own penetration tests. In the next chapter, we will investigate another way of delivering drones to your target using aerial drones.