Chapter 6
Planning Facilities Protection and Recovery
In This Chapter
 Keeping your processing facilities safe
Keeping your processing facilities safe
 Choosing an alternate processing site
Choosing an alternate processing site
This chapter focuses on the recovery of facilities — information processing facilities, mostly, but also work locations for critical personnel. You can’t plan just where the computers will go: You must also plan where people will work. Although this is an IT-centric book, you can’t take people completely out of the equation. Even if others in the organization are doing the business- and process-centric business continuity and disaster recovery planning that includes alternate work locations for all categories of personnel, I still give ’em an honorable mention here — this book primarily talks about recovering IT systems, but we all know that people need to have a place to work, too.
Protecting facilities can help an organization reduce or eliminate the effects of a disaster, improving the chances that an organization will survive a disaster — the overarching objective of DR planning.
This chapter discusses various strategies for alternate processing sites — places where you can get computers up and running after a disaster strikes so critical business processes that rely on information systems can resume functioning.
Protecting Processing Facilities
Information processing facilities are high concentrations of computers and equipment that support critical business processes. Within a single room, equipment supporting virtually all of an organization’s critical processes is usually stacked on special equipment racks placed side by side, with masses of power cables and network cables connecting this equipment to power supplies and networks. A room of very modest size, say 20 feet by 20 feet, can be as critical as 50,000 square feet of office space housing 250 workers who use the information systems contained in that small room.
Not only is the equipment expensive, but the business value derived from the use of the equipment is potentially very high. In many businesses, most operations cease to function if the supporting information systems become unavailable for any reason. Many of the reasons that operations stop have a lot to do with the environmental features (power, cooling, and so on) present in the facility in which these information systems are housed.
The types of mechanisms for protecting IT equipment include
 Physical access control
Physical access control
 Electric power
Electric power
 Fire detection and suppression
Fire detection and suppression
 Chemical hazards
Chemical hazards
 Water/flooding detection
Water/flooding detection

The following sections discuss the features in the preceding list and how those features protect information processing equipment.
Controlling physical access
The high value of information systems — and both the asset value of those systems and their support of revenue-producing business processes — makes today’s information processing facilities akin to Fort Knox. Data centers are often an organization’s highest concentration of wealth-producing or wealth-enabling assets. Consequently, access to these places needs to be tightly controlled, so only authorized personnel with a valid business reason for being there are permitted to enter and leave.

Data centers often employ several physical access controls that work together to both detect and prevent unwanted entry by unauthorized personnel. The most common controls are
 Video surveillance
Video surveillance
 Key-card entry controls
Key-card entry controls
 Man traps
Man traps
 Biometric entry controls
Biometric entry controls
 Security guards
Security guards
 Hardened facilities
Hardened facilities
 Locking cabinets
Locking cabinets
 Equipment cages
Equipment cages
In the following sections, I describe these controls in more detail.

Video surveillance
Surrounding a building, inside and out, with security guards, watching every entrance and room, is prohibitively expensive. The common remedy for watching everything everywhere is an extensive video surveillance system that can record the movements of people in a facility. Such a system consists of several components:
 Fixed-focus cameras: These cameras are permanently pointed in one direction and can’t be easily moved.
Fixed-focus cameras: These cameras are permanently pointed in one direction and can’t be easily moved.
 Pan/tilt/zoom cameras: Personnel viewing this type of camera in real time can remotely control the camera by panning and tilting (changing the direction in which the camera points) and zooming (making an object’s apparent distance from the camera closer or further away). Figure 6-1 shows several pan/tilt/zoom cameras housed within protective domes on the exterior of a building.
Pan/tilt/zoom cameras: Personnel viewing this type of camera in real time can remotely control the camera by panning and tilting (changing the direction in which the camera points) and zooming (making an object’s apparent distance from the camera closer or further away). Figure 6-1 shows several pan/tilt/zoom cameras housed within protective domes on the exterior of a building.
 Viewing monitors: Many organizations have staff dedicated to real-time viewing of surveillance camera views. Processing equipment can place one or more images onto a single monitor, and businesses frequently use many monitors so that staff can see many views of the interior and exterior of a building at the same time. Figure 6-2 shows a surveillance center that includes several viewing monitors, as well as equipment used to control pan/tilt/zoom surveillance cameras. You can also see in the figure that several of the monitors show images from four cameras at the same time.
Viewing monitors: Many organizations have staff dedicated to real-time viewing of surveillance camera views. Processing equipment can place one or more images onto a single monitor, and businesses frequently use many monitors so that staff can see many views of the interior and exterior of a building at the same time. Figure 6-2 shows a surveillance center that includes several viewing monitors, as well as equipment used to control pan/tilt/zoom surveillance cameras. You can also see in the figure that several of the monitors show images from four cameras at the same time.
 Recording equipment: Video surveillance systems can record onto video tape, optical disc, or computer hard drives. Three common recording methods are in use:
Recording equipment: Video surveillance systems can record onto video tape, optical disc, or computer hard drives. Three common recording methods are in use:
• Motion activated: The system records a still photo or a short video sequence when the scene in front of the camera changes, such as when a person walks by.
• Regular still photos: A still image recorded every one to ten seconds.
• Continuous video: Images from each video camera are recorded continuously.
You should keep records for at least several weeks, and perhaps as long as a year or more.

|
Figure 6-1: Surveillance cameras on the exterior of a building. |

|
|
Figure 6-2: Surveillance monitors and camera control equipment. |

|
Key-card entry controls
Information processing facilities — and many regular working locations — contain key-card entry systems that control who can enter work facilities. Key-card systems can also restrict entry to elevators, specific rooms, or individual building floors.
Key-card controls use a variety of technologies, sometimes in combination, to control access. The common types of key-card controls are
 Magnetic stripe reader: A key card contains a magnetic stripe, or magstripe, that’s similar to the technology used on credit cards. An employee swipes the key card through the magnetic stripe reader, which momentarily unlocks a door or opens a turnstile, permitting entry.
Magnetic stripe reader: A key card contains a magnetic stripe, or magstripe, that’s similar to the technology used on credit cards. An employee swipes the key card through the magnetic stripe reader, which momentarily unlocks a door or opens a turnstile, permitting entry.
 Contact-less proximity card reader: A key card contains an RFID (Radio Frequency Identification) or similar technology that permits the card’s owner to hold it close to the reader, thereby unlocking the door or turnstile. Figure 6-3 shows a person using a contact-less proximity card reader.
Contact-less proximity card reader: A key card contains an RFID (Radio Frequency Identification) or similar technology that permits the card’s owner to hold it close to the reader, thereby unlocking the door or turnstile. Figure 6-3 shows a person using a contact-less proximity card reader.
 Smart card reader: A key card contains a smart card memory chip, and a smart card reader reads that card’s contents when the user inserts the card into that reader. A smart card differs from magstripe and proximity cards because it uses small metal contacts to complete an electrical circuit between the reader and the electronics contained within the card. Newer smart card technology is contact-less and works in the same way that contact-less proximity card readers (described in the preceding bullet) do.
Smart card reader: A key card contains a smart card memory chip, and a smart card reader reads that card’s contents when the user inserts the card into that reader. A smart card differs from magstripe and proximity cards because it uses small metal contacts to complete an electrical circuit between the reader and the electronics contained within the card. Newer smart card technology is contact-less and works in the same way that contact-less proximity card readers (described in the preceding bullet) do.
|
Figure 6-3: A contact-less proximity card reader permits users to enter a secure room or facility. |

|
Photo by HID Corporation
 PIN pad: In order to provide additional security for sensitive locations, businesses sometimes use both card readers and PIN pads. In this situation, the employee has to both use his or her key card and enter a PIN (Personal Identification Number, generally a numeric code) to gain entry. A combination of a proximity card reader and PIN pad is shown in Figure 6-4.
PIN pad: In order to provide additional security for sensitive locations, businesses sometimes use both card readers and PIN pads. In this situation, the employee has to both use his or her key card and enter a PIN (Personal Identification Number, generally a numeric code) to gain entry. A combination of a proximity card reader and PIN pad is shown in Figure 6-4.
PIN-pad door locks
Doors can utilize a standalone PIN pad entry. Larger businesses often use PIN pad entry on rooms with sensitive records or information processing equipment, and smaller organizations that don’t need a centralized system can use these locks for main building access. A typical standalone PIN-pad door lock device is shown in Figure 6-5.
Biometric entry controls
Organizations that want security stronger than key cards and PIN pads turn to biometric entry controls. Biometric controls measure a specific characteristic of a person’s body to determine whether the person is authorized to enter. (See Figure 6-6.)
|
Figure 6-4: A combi-nation of a proximity card and PIN pad entry control. |

|
Photo by International Electronics, Inc.
|
Figure 6-5: A PIN-pad entry control. |

|
Photo by International Electronics, Inc.
|
Figure 6-6: A biometric fingerprint reader. |

|
Photo by HID Corporation
The most common types of biometric controls include
 Fingerprint: An optical reader reads a fingerprint and compares it to the registered fingerprints on file. Figure 6-6 shows a typical fingerprint reader.
Fingerprint: An optical reader reads a fingerprint and compares it to the registered fingerprints on file. Figure 6-6 shows a typical fingerprint reader.
 Hand scan: An optical reader reads the geometry of a person’s entire hand. A typical hand scan device that also includes a PIN pad is shown in Figure 6-7.
Hand scan: An optical reader reads the geometry of a person’s entire hand. A typical hand scan device that also includes a PIN pad is shown in Figure 6-7.
 Retina scan: A subject’s retina is scanned by a special reader.
Retina scan: A subject’s retina is scanned by a special reader.
 Face scan: A camera scans a person’s face and compares it to the registered image.
Face scan: A camera scans a person’s face and compares it to the registered image.
Other types of biometric identity verification systems include keystroke, signature, and voice.
|
Figure 6-7: A biometric hand reader and PIN-pad device. |

|
Photo by Ingersoll-Rand Corporation
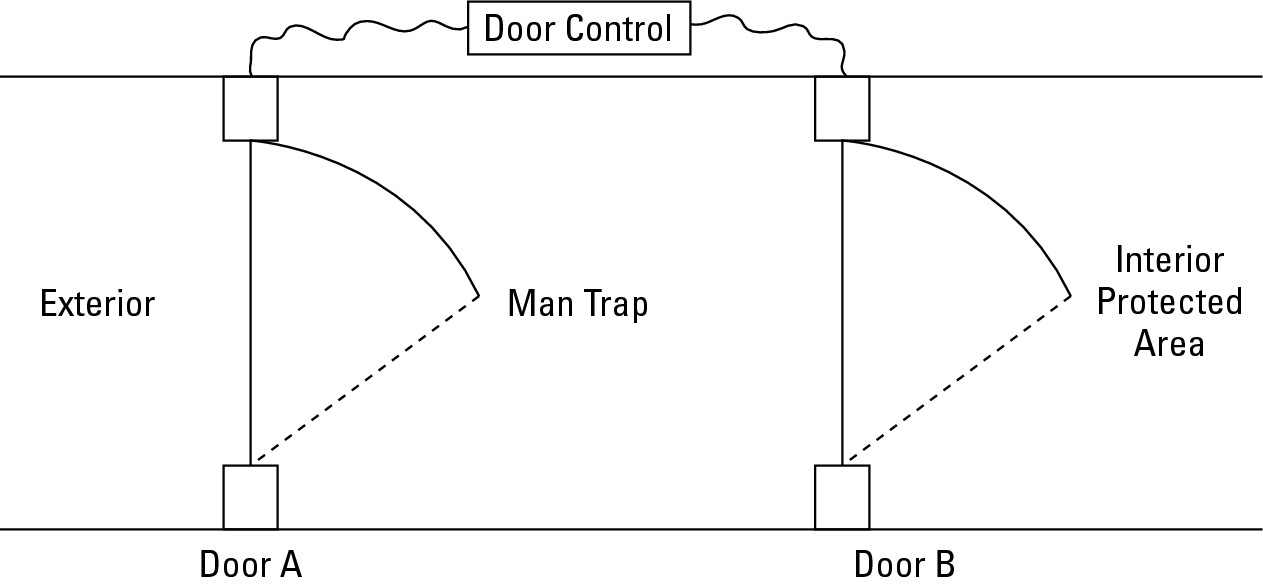
Man traps
Man traps are human entry mechanisms that utilize two doors, and only one door may be open at a time. Man traps can be manually operated (by a guard) or automatically operated, usually in conjunction with other access controls, such as key-card readers or PIN pads.
Here’s a typical sequence for passing through a man trap:
1. Person identifies him- or herself to a guard or electronic control.
2. First door opens. Person walks into the trap.
3. First door closes with the person inside the trap.
4. Second door opens. Person exits the trap.
5. Second door closes.
6. The man trap is now available for another person to enter or exit.
A typical man trap diagram is shown in Figure 6-8.
|
Figure 6-8: A man trap provides one-at-a-time control for entry and exit of personnel. |
|
The primary rules that enforce passage through a man trap are
 An electronic or manual control governs when each door can be opened.
An electronic or manual control governs when each door can be opened.
 Only one door can be open at a time.
Only one door can be open at a time.
 People can travel in only one direction at a time.
People can travel in only one direction at a time.
Because man traps can be expensive to purchase and operate, they’re usually used to protect only highest-value areas, such as data centers and cash vaults.
Security guards
Security guards are personnel who are trained and designated to perform several functions, including
 Checking identification of visitors
Checking identification of visitors
 Examining the personal effects of persons entering or leaving a facility
Examining the personal effects of persons entering or leaving a facility
 Monitoring building entrances and exits
Monitoring building entrances and exits
 Inspecting visiting vehicles prior to their entry
Inspecting visiting vehicles prior to their entry
 Apprehending persons of suspicious nature
Apprehending persons of suspicious nature
 Registering building visitors
Registering building visitors
 Operating video surveillance systems
Operating video surveillance systems
 Escorting visitors
Escorting visitors
 Registering information about equipment that personnel are taking out of the building
Registering information about equipment that personnel are taking out of the building
 Receiving incoming shipments
Receiving incoming shipments
Security guards fill a needed gap that varies from organization to organization, depending on security requirements and perceptions. The primary strength of security guards is that they possess the powers of judgment and intuition, unmatched in electronic-based control systems.
Hardened facilities
This catch-all category includes facilities that house information-processing equipment, particularly for highest-value organizations (large financial institutions, for instance) that have a lot to lose if their systems are damaged.
Some examples of features in a hardened facility include
 No exterior windows: Nothing to throw heavy objects through and no way to see from the street what’s going on inside.
No exterior windows: Nothing to throw heavy objects through and no way to see from the street what’s going on inside.
 Bulletproof glass: If the facility does have a few windows, bullets won’t pierce them.
Bulletproof glass: If the facility does have a few windows, bullets won’t pierce them.
 Fences: Eight-foot–high chain link — or even solid walls — with three or more strands of barbed wire or razor wire on top. Walls make effective pre-detonation screens (armored shields that can stop a projectile explosive from detonating on the building itself) if you’re concerned that someone may use heavy weapons against your facility.
Fences: Eight-foot–high chain link — or even solid walls — with three or more strands of barbed wire or razor wire on top. Walls make effective pre-detonation screens (armored shields that can stop a projectile explosive from detonating on the building itself) if you’re concerned that someone may use heavy weapons against your facility.
 Equipment bracing: Equipment cabinets and racks, and the systems in them, need to be securely fastened and braced, not only for personnel safety, but also to mitigate seismic (earthquake) risks. You don’t want to put a bunch of servers and other equipment up on racks only to have those racks fall down or the equipment fall off the racks, damaging the equipment and seriously injuring personnel.
Equipment bracing: Equipment cabinets and racks, and the systems in them, need to be securely fastened and braced, not only for personnel safety, but also to mitigate seismic (earthquake) risks. You don’t want to put a bunch of servers and other equipment up on racks only to have those racks fall down or the equipment fall off the racks, damaging the equipment and seriously injuring personnel.
 Electromagnetic shields: If you’re really concerned about the continuous onslaught of electromagnetic radiation in the kilohertz, megahertz, and gigahertz bands, consider putting in shielding that blocks all of that incoming noise. These shields are sometimes called TEMPEST (Transient Electromagnetic Pulse Emanation Standard) or Faraday cages. Cellphones and pagers can’t receive signals in such environments.
Electromagnetic shields: If you’re really concerned about the continuous onslaught of electromagnetic radiation in the kilohertz, megahertz, and gigahertz bands, consider putting in shielding that blocks all of that incoming noise. These shields are sometimes called TEMPEST (Transient Electromagnetic Pulse Emanation Standard) or Faraday cages. Cellphones and pagers can’t receive signals in such environments.
 Window coating: In particular, the sort that prevents laser listening devices from working.
Window coating: In particular, the sort that prevents laser listening devices from working.
 Bollards and crash gates: You don’t want angry or determined people to drive their vehicles into your building. Figure 6-9 shows an effective retractable vehicle crash barrier in action. Bollards are those heavy, short vertical posts that are used along roadways and in front of buildings to prevent vehicles from driving into certain areas.
Bollards and crash gates: You don’t want angry or determined people to drive their vehicles into your building. Figure 6-9 shows an effective retractable vehicle crash barrier in action. Bollards are those heavy, short vertical posts that are used along roadways and in front of buildings to prevent vehicles from driving into certain areas.
|
Figure 6-9: Vehicle barriers can effectively stop unwanted vehicles from entering a secure facility. |

|
Photo from B&B ARMR Corporation
Locking storage cabinets
Information processing facilities have a lot of valuable items that you should lock away out of sight. Some items that need to be locked away include
 System documentation
System documentation
 Release media (CD-ROM and other media that contain purchased software)
Release media (CD-ROM and other media that contain purchased software)
 Backup media
Backup media
 Spare parts
Spare parts
The quality of the locking storage cabinets should depend on the value of the contents they’re protecting.
Equipment cabinets and cages
Usually found in multi-tenant commercial colocation data centers and companies with factions that don’t trust each other, equipment cabinets and cages allow equipment to be cordoned off to prevent physical access by persons who otherwise do have a legitimate reason to be in the data center. Figure 6-10 shows locking equipment cabinets in a modern processing center.
|
Figure 6-10: Cages let you protect equipment in multi-tenant and colocation data centers. |

|
Cages and cabinets can range in size from a single 30-inch cabinet to caged areas that cover hundreds of square feet. You typically lock them with metal keys or an electronic access control system, such as a PIN pad or key-card reader.
Getting charged up about electric power
Electricity is the critical ingredient for information systems and supporting equipment. Servers and network equipment get cranky when any of the common and not-so-common electrical anomalies occur, including sags, surges, spikes, transients, brownouts, noise, and outright failures.
Dirty electricity, and also frequent brownouts and blackouts, not only cause unscheduled downtime, but can also have a significant effect on the life expectancy of equipment. IT equipment requires clean — really clean — power.
You need some of this equipment in your facility to protect your IT equipment from power problems:
 Remote power controllers: These smart, network-attached plug strips let you switch power off and on to each plug. They’re invaluable for remotely controlled equipment in lights-out data centers (centers that are unstaffed most of the time). Beats having to get dressed just to power cycle a server.
Remote power controllers: These smart, network-attached plug strips let you switch power off and on to each plug. They’re invaluable for remotely controlled equipment in lights-out data centers (centers that are unstaffed most of the time). Beats having to get dressed just to power cycle a server.
 Uninterruptible Power Supply (UPS): Absolutely non-negotiable, in my opinion. You might not need a large one, but you need one. They not only store several minutes of electricity in batteries, they also (usually) filter out all the dirty power that makes your systems sick.
Uninterruptible Power Supply (UPS): Absolutely non-negotiable, in my opinion. You might not need a large one, but you need one. They not only store several minutes of electricity in batteries, they also (usually) filter out all the dirty power that makes your systems sick.
 Line conditioners: A possible adjunct to UPS, line conditioners smooth out the bumps and dips in incoming power.
Line conditioners: A possible adjunct to UPS, line conditioners smooth out the bumps and dips in incoming power.
 Power Distribution Unit (PDU): A PDU is a device that distributes electric power to individual circuits and plugs. Some PDUs also step down voltage from 240 to 120 volts, and some have remote control capability.
Power Distribution Unit (PDU): A PDU is a device that distributes electric power to individual circuits and plugs. Some PDUs also step down voltage from 240 to 120 volts, and some have remote control capability.
 Electric generator: If your organization can’t tolerate occasional utility outages, put an electric generator on your shopping list. Generators work in conjunction with a UPS: In the event of a utility power failure, the UPS immediately begins providing power from its batteries for the seconds or minutes the generator requires to start and get up to speed. Larger installations may require more than one generator, for both capacity and redundancy reasons.
Electric generator: If your organization can’t tolerate occasional utility outages, put an electric generator on your shopping list. Generators work in conjunction with a UPS: In the event of a utility power failure, the UPS immediately begins providing power from its batteries for the seconds or minutes the generator requires to start and get up to speed. Larger installations may require more than one generator, for both capacity and redundancy reasons.
 Diverse power feeds: For really critical facilities, consider having the public utility bring in two separate power feeds that enter the building from opposite ends and that feed from different substations.
Diverse power feeds: For really critical facilities, consider having the public utility bring in two separate power feeds that enter the building from opposite ends and that feed from different substations.
 Switching equipment: Large installations with multiple power feeds, generators, and UPSs need switching equipment that can ensure the continuous flow of electricity to your systems in any situation.
Switching equipment: Large installations with multiple power feeds, generators, and UPSs need switching equipment that can ensure the continuous flow of electricity to your systems in any situation.
In addition to the equipment in the preceding list, another highly critical aspect to power management is planning. Planning is especially important for larger installations that are utilizing newer blade technology, which consumes more power per square foot than older technologies.
Detecting and suppressing fire
Early fire detection is critical in information processing centers. If you can identify a fire in its earliest stages, you can deal with it before serious damage occurs.
When fire does erupt, you need to extinguish it as quickly as possible, with minimum damage inflicted on otherwise-uninvolved equipment. Using water to extinguish a fire in a data center isn’t such a great idea, unless you want to replace all of your water-soaked equipment because some technician let his soldering iron get too hot and smoky.
Smoke and fire detection
Where there’s smoke, there’s fire. The old saying isn’t far from the truth. Effective fire detection starts with smoke detection. When fire is in its early stages, it may emit smoke in very small amounts.
The options for smoke and fire detection are
 Photoelectric: Smoke scatters light in the air. Photoelectric smoke detectors work by detecting this scattering.
Photoelectric: Smoke scatters light in the air. Photoelectric smoke detectors work by detecting this scattering.
 Ionization: In a small ionization chamber, smoke alters the process of ionization and triggers the alarm.
Ionization: In a small ionization chamber, smoke alters the process of ionization and triggers the alarm.
 Air sampling: A network of air sampling pipes throughout the facility draws air into a centralized, highly sensitive sampling chamber. By design, this setup can detect fire earlier than other types of detectors because it can get a higher quality air sampling by using only one really good sampling device rather than many less expensive units.
Air sampling: A network of air sampling pipes throughout the facility draws air into a centralized, highly sensitive sampling chamber. By design, this setup can detect fire earlier than other types of detectors because it can get a higher quality air sampling by using only one really good sampling device rather than many less expensive units.
 Temperature: When the fire becomes more active, it heats the air around it. Temperature or rate-of-rise sensors detect the change in temperature.
Temperature: When the fire becomes more active, it heats the air around it. Temperature or rate-of-rise sensors detect the change in temperature.
 Manual stations: People in the facility can run to the nearest fire alarm panel and manually turn on the alarm if they know that a fire has started. Similarly, an observant surveillance operator can detect smoke or fire through the video surveillance.
Manual stations: People in the facility can run to the nearest fire alarm panel and manually turn on the alarm if they know that a fire has started. Similarly, an observant surveillance operator can detect smoke or fire through the video surveillance.
Many locations have laws that require a computing facility to include two or more of these detection systems.
Fire alarms and evacuation
Because human life and safety are the primary concerns in any disaster situation, fire alarms need to be properly designed and maintained so that personnel know when a fire breaks out and how to quickly evacuate the premises. You also need well-placed exit signs, of course, to help people find their way out of a building when the alarms go off.
Fire alarms in commercial buildings are commonly connected to local fire departments. This connection automatically notifies firefighters, speeding their arrival and hopefully reducing damage.
Fire suppression
When a fire has started in an information processing facility, you need to extinguish the fire as soon as possible, before it damages costly equipment. You can use several means of controlling and extinguishing fire, including
 Fire extinguishers: These portable devices are usually located throughout office buildings and data centers. Fire extinguishers come in several types for fighting different kinds of fires. Here are the kinds available in the United States:
Fire extinguishers: These portable devices are usually located throughout office buildings and data centers. Fire extinguishers come in several types for fighting different kinds of fires. Here are the kinds available in the United States:
• Class A: Ordinary combustibles, such as wood and paper
• Class B: Flammable liquids
• Class C: Energized (powered on and active) electrical equipment
• Class D: Combustible metals
• Class K: Cooking oils
Some fire extinguishers fall into a combination of the different types — for instance, an extinguisher can be classified both Class A and Class B.
 Sprinkler systems: These systems send a steady spray of water onto large areas, cooling the fire until it can no longer sustain itself. Water causes severe damage to information processing equipment, so you don’t want sprinklers fighting fires in data centers. However, building codes often require sprinkler systems as a backup to other types of suppression.
Sprinkler systems: These systems send a steady spray of water onto large areas, cooling the fire until it can no longer sustain itself. Water causes severe damage to information processing equipment, so you don’t want sprinklers fighting fires in data centers. However, building codes often require sprinkler systems as a backup to other types of suppression.
You can find several types of sprinkler systems:
• Wet pipe: When sufficient heat reaches near a sprinkler head, a fusible link melts, releasing water through the sprinkler head.
• Dry pipe: The pipes are dry until smoke or heat activates the system, at which time water flows through the pipes and out of the sprinkler heads. Water flows only from heads whose fusible links have melted.
• Deluge: Used in locations where rapidly spreading fire is a concern. All sprinklers are open (they have no fusible links that must melt), and upon activation, all sprinkler heads discharge water simultaneously.
• Pre-action: A hybrid of dry pipe and deluge. Typically, the system requires a preceding event, such as smoke detection, which charges the pipes with water, converting the system to a wet-pipe system. When further smoke alarms, heat alarms, or heat at the sprinkler heads occur, water flows.
• Foam and water: As you might guess, sprinklers discharge a mixture of low-expansion foam and water.
Figure 6-11 shows a close-up of a sprinkler head. This illustration clearly shows the transparent fusible link capsule. This capsule melts in heat caused by a fire, which activates the flow of water.
|
Figure 6-11: The link capsule in a sprinkler head. |

|
 Gaseous fire suppression: Most often found in data centers, these systems flood the area with an inert gas, thereby depriving the fire of oxygen. The system works by discharging the gas when someone pulls a fire alarm in the facility or when one or more smoke or heat detectors are activated. The gas is stored in large tanks inside or immediately outside the protected area. Gases often used include FM-200, Argonite, and Inergen. Organizations once commonly used Halon 1301, but it’s been discontinued since the signing of the Montreal Protocol in 1989, which outlawed the use of ozone-depleting substances.
Gaseous fire suppression: Most often found in data centers, these systems flood the area with an inert gas, thereby depriving the fire of oxygen. The system works by discharging the gas when someone pulls a fire alarm in the facility or when one or more smoke or heat detectors are activated. The gas is stored in large tanks inside or immediately outside the protected area. Gases often used include FM-200, Argonite, and Inergen. Organizations once commonly used Halon 1301, but it’s been discontinued since the signing of the Montreal Protocol in 1989, which outlawed the use of ozone-depleting substances.

Chemical hazards
Many organizations work with hazardous chemicals and materials as a part of their business. In the United States, the Occupational Health and Safety Administration (OSHA) and the Environmental Protection Agency (EPA) have strict guidelines concerning the acquisition, storage, and use of a vast number of hazardous substances, as well as specific contingency plans for treating spills and accidental releases of these substances.
In many cases, these spills and releases may trigger disasters. Mandatory evacuations alone are enough to trigger a business disaster: If everyone has to leave a facility, how can the business continue operations?
Often, businesses are subject to not only U.S. federal laws, but also state and local laws governing the same substances. I’m not going to attempt to untangle this sticky web of regulation and substance-related contingency plans. If your business deals in hazardous substances (as defined by OSHA and the EPA, or other agencies that have jurisdiction where your business is located), you need to gain expertise in handling those substances, in addition to the more generalized disaster recovery planning that this book covers.
Keeping your cool
Information processing equipment operates very happily within a fairly narrow band of temperature and humidity. These environment restrictions becomes a challenge when the equipment consumes a lot of electricity and throws off so much heat! Getting rid of the heat at the same rate that it’s produced is no small task. And with the amount of heat that newer equipment discharges per square foot of space, cooling equipment must deliver much more punch than in the past.
The life expectancy of information processing equipment drops sharply (sometimes by more than 90 percent) with just a single high temperature spike. When systems catch a high fever, they’re not long for this world.
Because temperature control is so vital, an information processing center must have redundancy in its HVAC (Heating, Ventilation, and Air Conditioning) systems, so the failure (or planned maintenance) of one HVAC system doesn’t put the data center at risk. Also, the control systems that manage the HVAC systems must be robust themselves, so they don’t ever fail to direct the HVAC systems to do the right thing.
Because HVAC is so vital, you need to protect it by having backup power (UPS and generators) along with computing equipment. If HVAC stops operating for more than a few minutes, you need to shut down computing equipment right away to prevent overheating and damage.
Staying dry: Water/flooding detection and prevention
Information systems and water don’t mix very well at all. For this reason, water-based fire suppression systems (as a first line of defense) have fallen out of favor because water discharge can severely damage computing equipment.
You can do a few things to make sure that water doesn’t become a problem. You may not have to worry about some of these measures, depending on your local conditions:
 Local flooding risk: Find a hydrologist who can provide a realistic assessment of flooding potential for your facility. Take the results to an architect who may recommend mitigating features for your site that can ensure any flood waters are directed away from your facility.
Local flooding risk: Find a hydrologist who can provide a realistic assessment of flooding potential for your facility. Take the results to an architect who may recommend mitigating features for your site that can ensure any flood waters are directed away from your facility.
 Building survey: Look for risks within your facility that may pose a water hazard. Check that roof drains and other features are operating properly.
Building survey: Look for risks within your facility that may pose a water hazard. Check that roof drains and other features are operating properly.
Here’s my personal flood-in-the-building story: Years ago, a hot water heater on the fifth floor of a building exploded, sending water cascading downstairs into the second floor data center, taking a national public data network off the air for a few hours. Water was dripping out of servers. Needless to say, it pays to carefully understand the risks posed by even innocuous features in a building.
 Emergency procedures: If your building is prone to any sort of water accumulation, you may need to have emergency procedures and supplies on hand, such as sand bags, pumps, or other means for keeping water out or removing water if it gets in.
Emergency procedures: If your building is prone to any sort of water accumulation, you may need to have emergency procedures and supplies on hand, such as sand bags, pumps, or other means for keeping water out or removing water if it gets in.

Regularly test pumps or other complex apparatuses for readiness.
 Water detectors: Install electronic water detectors in the lowest places in your information processing center and connect them to whatever alarm management or network management system seems appropriate for proper alert-and-action capabilities. With this water-detector setup in place, if water somehow gets into your information processing center, you can find out about it while you may still have time to deal with it and avert a disaster.
Water detectors: Install electronic water detectors in the lowest places in your information processing center and connect them to whatever alarm management or network management system seems appropriate for proper alert-and-action capabilities. With this water-detector setup in place, if water somehow gets into your information processing center, you can find out about it while you may still have time to deal with it and avert a disaster.
 Equipment location within a building: For facilities in or near areas prone to flooding, you should locate equipment in the building above potential flood levels.
Equipment location within a building: For facilities in or near areas prone to flooding, you should locate equipment in the building above potential flood levels.
 Water-resistant storage: Get water-resistant safes and media vaults so flooding, fire suppression, and other discharges of water don’t damage valuable documents and storage media.
Water-resistant storage: Get water-resistant safes and media vaults so flooding, fire suppression, and other discharges of water don’t damage valuable documents and storage media.
 Humidity control: Have equipment for removing excess humidity on hand or readily available in the event a discharge of water occurs.
Humidity control: Have equipment for removing excess humidity on hand or readily available in the event a discharge of water occurs.

Selecting Alternate Processing Sites
Despite every reasonable means available to prevent a disaster or minimize a disaster’s impact, some events are so intense that you have no choice but to temporarily or permanently abandon a data processing facility and resume operations elsewhere. Extreme natural and man-made disasters do occur, and in your locale, you know which types are more likely to trigger a real disaster for your organization.
So the main question is: If you have a disaster, where you gonna go? The following sections are devoted to helping you answer that question for your organization.
You have several alternatives for relocating your systems if your data center ends up a smoking crater:
 Cold sites: Processing facilities with no computers installed
Cold sites: Processing facilities with no computers installed
 Warm sites: Processing facilities with computers that require installation and configuration
Warm sites: Processing facilities with computers that require installation and configuration
 Hot sites: Processing facilities with computers that are ready to perform business processing
Hot sites: Processing facilities with computers that are ready to perform business processing
 Other business locations: Other facilities that the organization owns
Other business locations: Other facilities that the organization owns
 Mobile sites: Processing facilities in trailers
Mobile sites: Processing facilities in trailers
 Contracted facilities: Processing facilities owned by other organizations
Contracted facilities: Processing facilities owned by other organizations
 Reciprocal facilities: Mutual-aid arrangements
Reciprocal facilities: Mutual-aid arrangements
The following sections give you detailed explanations of the alternatives in the preceding list.
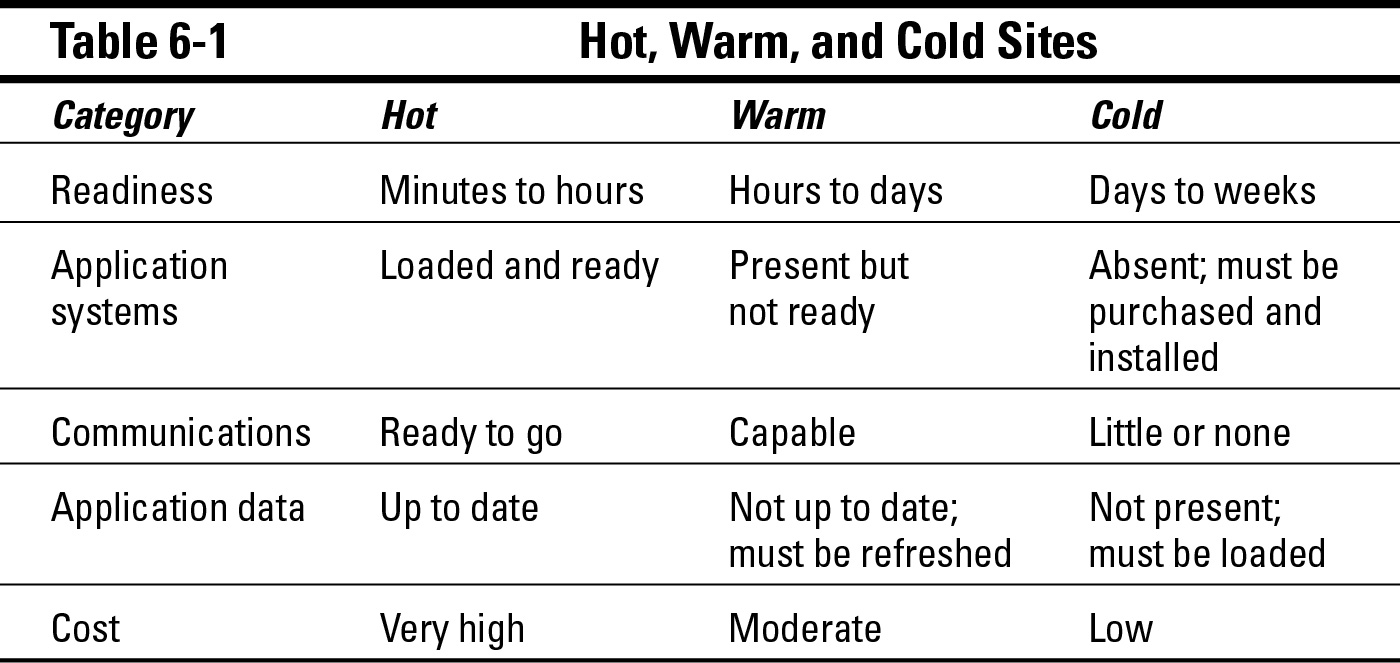
Hot, cold, and warm sites
You have a few ways to consider alternate processing sites. You can consider who owns an alternate site and the business relationship between your organization and the alternate site’s owner. You can also consider the alternate site’s readiness to take on the burden of production information processing — I discuss this readiness consideration in this section.
In terms of readiness, alternate processing centers are categorized in three levels: hot, cold, and warm. I describe these levels in the following sections.
Hot sites
A hot site is a location that’s ready to assume production application processing with little or no preparation. Systems, networks, and applications are all in place and up-to-date, and perhaps live data is already on the site or can be loaded up fairly quickly. Generally speaking, a hot site can assume processing with only a few minutes’ or hours’ notice.
Hot sites are the most expensive because keeping a hot site ready to assume production duties requires continuous effort. But, for businesses with highly time-sensitive applications, the expense of a hot site may be well worth the cost.
Cold sites
Cold sites are generally just empty processing centers with little or no networking equipment, and few (if any) systems. Communications facilities may or may not be in place. Think of a cold site as an empty room, with physical and environmental controls in place, but no information processing equipment.
The time required to get a cold site up to full battle readiness is at least several days and possibly a week or longer.
Warm sites
Warm sites are, well, in the middle between ready-to-go hot sites and the empty shells of cold sites. Warm sites may have servers and network equipment in place, but no software or data loaded. A warm site might need from one to five days to get up and running.
Table 6-1 compares hot, warm, and cold sites.

Other business locations
Some businesses already have more than one processing site or have the ability to implement a second processing site in one of its premises. The capability to build your own alternative processing site may cost less than going with outside service bureaus or colocation facilities.
Some points to consider when thinking about other business locations as alternate processing sites include
 Siting risks: Is the site free from risks associated with airports, railroads, hazardous materials, flooding, storms, landslides, and other factors?
Siting risks: Is the site free from risks associated with airports, railroads, hazardous materials, flooding, storms, landslides, and other factors?
 Environment support: Does the site have sufficient HVAC and power capacity, or can you add it?
Environment support: Does the site have sufficient HVAC and power capacity, or can you add it?
 Physical security: Does the other business location have sufficient physical security controls, such as fencing, video surveillance, key card systems, and so on?
Physical security: Does the other business location have sufficient physical security controls, such as fencing, video surveillance, key card systems, and so on?
 Proximity to primary processing site: Is the site far enough away from the existing information processing facility to not be considered in the same risk zone? Such a minimum distance might range from 100 to 500 miles, depending on the nature of the risks, such as earthquakes, volcanoes, hurricanes, tsunamis, and so on. Consult with local experts regarding the threats associated with nearby natural threats.
Proximity to primary processing site: Is the site far enough away from the existing information processing facility to not be considered in the same risk zone? Such a minimum distance might range from 100 to 500 miles, depending on the nature of the risks, such as earthquakes, volcanoes, hurricanes, tsunamis, and so on. Consult with local experts regarding the threats associated with nearby natural threats.
 Transportation: Is the alternate site sufficiently close to major transportation systems, such as airports, railroads, seaports, or freeways, to make those systems accessible in an emergency?
Transportation: Is the alternate site sufficiently close to major transportation systems, such as airports, railroads, seaports, or freeways, to make those systems accessible in an emergency?
 Supporting services: Are supporting services near enough to the alternate site? Examples of supporting services that you may need to take into consideration include shipping, police and fire, lodging and restaurants, public utilities, building construction and repair, and network connectivity.
Supporting services: Are supporting services near enough to the alternate site? Examples of supporting services that you may need to take into consideration include shipping, police and fire, lodging and restaurants, public utilities, building construction and repair, and network connectivity.
 Laws and codes: Are the building codes and laws concerning security and other matters for the alternate processing center suitable for your needs?
Laws and codes: Are the building codes and laws concerning security and other matters for the alternate processing center suitable for your needs?
You may identify other factors that you think are important for your particular business activity and other needs.
Data center in a box: Mobile sites
Organizations such as APC, Sun Microsystems, and SunGard have developed emergency mobile data centers that they can deliver to a business location. These companies offer the following features:
 APC InfraStruXure Express: 2,500-square-foot mobile data center on a semi-truck trailer platform that includes power, cooling, 12 equipment racks, and satellite communications.
APC InfraStruXure Express: 2,500-square-foot mobile data center on a semi-truck trailer platform that includes power, cooling, 12 equipment racks, and satellite communications.
http://www.apc.com/products/infrastruxure/index.cfm
 Sun Microsystems Project Blackbox: Self-contained data center in a shipping container that can be sent anywhere in the world by truck, ship, rail, or air. Equipped with integrated power and cooling, and a configurable selection of servers and network equipment.
Sun Microsystems Project Blackbox: Self-contained data center in a shipping container that can be sent anywhere in the world by truck, ship, rail, or air. Equipped with integrated power and cooling, and a configurable selection of servers and network equipment.
 SunGard: Mobile data center on a semi-truck trailer platform that includes a generator, voice and data communications access, terminals and printers, equipment racks, work areas, kitchen, restrooms, lighting, and physical security. SunGard has several of these units available for dispatch within 48 hours.
SunGard: Mobile data center on a semi-truck trailer platform that includes a generator, voice and data communications access, terminals and printers, equipment racks, work areas, kitchen, restrooms, lighting, and physical security. SunGard has several of these units available for dispatch within 48 hours.
Go to www.availability.sungard.com and search for Mobile Data Center.
An emergency mobile data center may be appropriate for your business if you need a temporary data center up and running quickly in a location that has no other facilities available.
Colocation facilities
Commercial data centers, also known as colocation facilities or just colos, are big business in nearly every metropolitan area in the world. The big players, such as AT&T, have dozens of facilities throughout the world; many regional and local companies have carrier-grade data centers, as well.
Colocation facilities are multi-tenant data centers in which an organization such as yours leases as much space as it needs — from as little as a portion of a single rack to hundreds of square feet. The colo provides several features:
 Physical security: Security guards, key card entrances, video surveillance, fences, and perhaps other measures, such as hardened buildings, guard dogs, crash barriers, and so on.
Physical security: Security guards, key card entrances, video surveillance, fences, and perhaps other measures, such as hardened buildings, guard dogs, crash barriers, and so on.
 Network/Internet connectivity: Provides connectivity to the Internet — just hook up your router, firewall, switches, and so on.
Network/Internet connectivity: Provides connectivity to the Internet — just hook up your router, firewall, switches, and so on.
 Power, including emergency power: Some facilities have redundant power feeds, generators, UPSs, and so on.
Power, including emergency power: Some facilities have redundant power feeds, generators, UPSs, and so on.
 HVAC: Redundant air-conditioning and humidity controls to get rid of all the heat that your servers throw off.
HVAC: Redundant air-conditioning and humidity controls to get rid of all the heat that your servers throw off.
 System monitoring and management: Systems monitoring, management, backups, and so on, manned 24/7 by colo staff members so you don’t have to.
System monitoring and management: Systems monitoring, management, backups, and so on, manned 24/7 by colo staff members so you don’t have to.
The cost advantage of a colocation facility is potentially significant. In particular, they’re expensive to build and maintain, and your organization needs to pay only its share in the form of monthly fees. Colocation facilities do have a downside: They’re expensive, although less so than building one of your own.
Reciprocal facilities
Before colocation facilities came into being, one of the few options available for alternate processing sites was the reciprocal facility. A reciprocal facility is a legal arrangement between two parties, in which each pledges to make a portion of its facility available to the other party in the event that the other party experiences a disaster that forces it to abandon its own data center.
In plain and simple English, the agreement is, “I let you use a portion of my data center if you experience a disaster, and you let me use a portion of your data center if I experience a disaster.”
In the era of mainframe computers, the reciprocal agreement applied not only to the physical space, but to the use of the organization’s mainframe computer(s). So a reciprocal agreement was also a timesharing or service-bureau type agreement because an organization would permit another organization to run its programs on its mainframe.
The two organizations needed to have the same kind of mainframe computers so that application programs on one would also run on the other. The organizations needed to conduct an initial test to check the viability of a long-term reciprocal agreement and perhaps regular testing to make sure that the systems were still compatible.
In today’s environment, a reciprocal agreement may or may not include the use of the other organization’s systems — it may cover just the floor space and power for your systems in the other organization’s data center. Still, a reciprocal agreement can cost much less than the alternative, colocation facilities.