Chapter 7. Psychological Weapons
Information in this Chapter
Social engineering is the act of influencing a person's behavior by manipulating the person's emotions, or gaining and betraying his or her trust to gain access to his or her system. This can be done in person, over the phone, via an e-mail, via social media, or through other methods. The goal of a social engineering attack is to create a relationship with the target so that he or she will take some sort of action or provide information that violates his or her organization's policies or security practices. As such, social engineering is a dangerous threat vector for organizations and individuals alike, and training and vigilance are required to defend against it. Besides explaining what social engineering is, this chapter discusses how the military approaches and defends against social engineering to provide security professionals with the knowledge needed to tackle this threat vector and stop it in its tracks.
Keywords
Counterintelligence, Elicitation, General access attack, Graham-Leach-Bliley Act, Human Intelligence operator, Mirroring, Pretexting, Social engineering, Targeted access attack
We have talked about technical attacks in Chapter 5 and Chapter 6. Now it is time to talk about using the target's behaviors to gain access to their information. Psychological Operations (PSY OPS) are planned operations to convey selected information and indicators to foreign audiences to influence their emotions, motives, objective reasoning, and ultimately the behavior of foreign governments, organizations, groups, and individuals [1]. Militaries have been conducting Psychological Operations (PSY OPS), or Influence Operations, for centuries. The United States stood up Army Special Forces (Green Berets) to win the hearts and minds rather than just force to achieve victory. Comparable techniques are used by Human Intelligence (HUMINT) collectors and the Intelligence community to get enemy personnel to betray their countries by becoming spies. Similar techniques have been used in civilian society by con artists whose ability to gain someone's trust so they can take advantage of them is how they make a living. Many of the methods are used by salespeople to influence buyers to purchase the most expensive car. Now these techniques are being modified by hackers to get users to violate policies and common sense thus allowing them access to critical data and are commonly referred to as Social Engineering.
Social Engineering Explained
Social Engineering (SE) is the act of influencing someone's behavior through manipulating their emotions, or gaining and betraying their trust to gain access to their system. This can be done in person, over the phone, via an email, through social media, or a variety of other methods. The difference between social engineering and other attacks is the vectors are through the person, or as hackers say the “wetware.”
The goal of an SE attack is to create a relationship, gain the target's trust and get them to take an action or provide some information that is a violation of their organization's policies or personal basic security practices. Some folks have the gift of gab and can do it with a cold call but most attackers will take time to prepare a story based on information known about the target. This attack vector has grown rapidly in the past few years and for some target sets is the dominant technique.
Is Social Engineering Science?
How is this a science? There have been many recent publications on kinesics (the study of body and facial expressions) like Paul Ekman's books on micro-facial expressions and What Every Body Is Saying: An Ex-FBI Agent's Guide to Speed- Reading People by Marvin Karlins and Joe Navarro. These, combined with books on subjects like Emotional Intelligence: Why It Can Matter More Than IQ by Daniel Goleman and Blink: The Power of Thinking Without Thinking by Malcolm Gladwell, that talks about how intuition is based on insights the person may not be consciously aware of, start to develop a body of knowledge that can be applied as a science rather than an art. These studies are developing the baseline to take this discipline from an art to a science.
This leads to the question: can SE be taught, or is it a natural ability? There is some debate on whether SE skills can be taught, but this is basically the same debate that exists for leadership, salesmanship, or any other ability. Though the arguments are often very passionate, most will agree in the end that some people have natural tendencies that make them great when they study and train in the discipline they want to master whereas others can go through the same process and only become average. So whereas some individuals will naturally become very proficient at technical hacking they may struggle to use social engineering techniques like the “cold call” but everyone can learn the basics and find where their talents lay. Many of the tactics techniques and procedures we will discuss are a blend of technical and SE attacks.
SE Tactics Techniques and Procedures (TTPs)
A typical SE exploit depends on the target. There are two general scenarios: general access attacks and specific targeted access attacks. To use a metaphor (understanding most metaphors when applied to cyberspace are dangerous as they don't reflect the complexity of the environment), if we were ordered to steal a car in the next week that would be easy. In a general access attack, we could sit outside a convenience store waiting for someone to leave their car running then jump in and drive away (remember to check for a baby seat) or we could use a gun and carjack someone at a light; we could go old school and learn to hotwire a car or any number of other techniques. If we were told to steal the Mayor's car (a specific target), that would be a different story. In the first scenario we didn't need to do any reconnaissance; now we need to put a lot of effort into recon. We have to learn what the Mayor drives and figure out the best attack. We need to understand which attack has the least chance of getting caught, as the mayor controls the police force. Depending on our motivations we may want the theft to go unnoticed for a period of time, or we may want it to be dramatic so it gets on the evening news. The same rule is true with cyber attacks but as there is an element of personal interaction in SE it is even more relevant to understand the target.
First let's look at general attacks. These are attacks where the goal is to gain entry to any system or network. The attacker is indifferent to the owner of the system. A general phishing attack would be a good example (see note for definitions on types). The cost of sending out the emails is low; there are about 183 billion spam emails sent a day and 2.3% are phishing attacks [2]. These systems can be attacked or used to attack other systems (making them “zombies”). Harvesting a large number of systems is useful to build systems in between the attacker and the targets. There is NO need for reconnaissance as the attacker doesn't care where the system is or what is does; they can move directly to the attack phase and, due to the low costs, accept the lower number of compromised systems.
The next example of a general attack is to release a virus. A virus is a malcode program that the user needs to run to have it work. Attackers can load a virus into a Word document, PDF, PowerPoint, picture, or even a game. These infected files will open and run (i.e., someone can open the PowerPoint document and go through the slides) at the same time the virus infects the system. The downside to an attack like this is it can go viral and end up infecting systems it was not intended to attack. This kind of an attack can also be done with a worm which is a malcode program that doesn't need user interaction; it will infect a system and use it to infect others but this would not be a SE attack. It would be categorized as a technical attack. The proliferation of translation sites on the web and access to interesting news from the target's homeland have made this type of attack much easier to develop believable scenarios with proper grammar and cultural context that will get potential victims to take the bait.
Note
Standard types of attacks generally designed to steal identities:
• Phishing: This is where a mass email is sent to a large group of addresses (potentially millions). The email could try to lead the user to open an attachment or go to a web page, either of these actions would lead to the computer system being compromised (assuming the system in question was vulnerable).
• Pharming: misdirecting users to fraudulent Website.
• Spear Phishing: This is where a specific individual is targeted and a tailored email is sent that they will open and react to. Examples would be the Sys Admin for a network or Program Manager of a target. This requires good intelligence on the target.
• Whaling: This is a Spear Phishing attack against the senior level of leadership of the organization being targeted.
Now we will analyze target-specific attacks. The attacker will approach the target after learning as much about them as they can via what the military calls Open Source Intelligence (OSINT). Civilians would just call this “googling” someone. The attacker wants to understand the victim's interests, fears, motivations, attitudes and desires. This will allow the attacker to tailor the attack and increase the chances of success. Key information includes knowledge of significant dates (birth, marriage…), addresses, phone numbers, family members, interests, relationships, photographs, and work and education histories. If the target is active on social networking sites this is a great place to start; the greater their electronic footprint the better. There are many places to learn about the target:
• Personal info can be found on social media sites like Facebook or MySpace (this includes relationships, activities like sports, volunteering, religion practices, political beliefs, and so on)
• Professional information is on networking sites like LinkedIn or job sites like Monster (this also tells you what they are working on)
• Geolocation info on sites like Google Earth or location-based services like Foursquare
• Financial information like tax records and home ownership records
• What they are thinking can be read on via their Twitter pages or blogs
• Involvement in virtual worlds like Second Life or gaming site (where people can meet as any avatar they create)
• Membership info from organizations like academic alumni, clubs, professional organizations, or hobbies
Tip
Privacy has different meanings to individuals based on their generation and the culture they were raised in. For many of the younger generation who have been raised with computers (sometimes called Digital Natives) they have a large part of their lives online, to the point some have their diaries as part of their public web pages. Their expectations of privacy are different that most of the folks running the militaries and intelligence communities today. They can become vectors for attack if they have relationships with someone that has been targeted. It is important that both parties understand what is being posted and what is acceptable.
Types of SE Approaches
Once the attacker has gathered the background information necessary to understand some options to approach the target they must decide how aggressive they want to be. From least to most aggressive the approaches are: observation, conversation, interview, interrogation, and torture. They can start by digital or physical observation. Next comes a conversation (electronic, telephonic, or in person). This is often the phase where the attacker will determine who they want to recruit or attack. Typically this is known as elicitation which is generally the extraction of information through what seems to be casual conversation. To phrase this another way it is where the con is based on the SE's ability to spin a lie. This ability comes from pretexting which is developing a scenario where the SE gains the trust of the person who owns or has access to the information in order to get them to break their policies or violate common sense and give the information to the attacker. One method that is used in every type of attack but is especially useful here is mirroring. For example by adopting the target's speech mannerism (or email style) it will be much easier to get them to engage in a conversation.
Warning
The Financial Modernization Act of 1999 more commonly known as the Gramm-Leach-Bliley Act makes pretexting a crime. Under federal law it's illegal for anyone to [3]:
• Use false, fictitious, or fraudulent statements or documents to get customer information from a financial institution or directly from a customer of a financial institution.
• Use forged, counterfeit, lost, or stolen documents to get customer information from a financial institution or directly from a customer of a financial institution.
• Ask another person to get someone else's customer information using false, fictitious, or fraudulent statements or using false, fictitious, or fraudulent documents or forged, counterfeit, lost, or stolen documents.
• The Federal Trade Commission Act also generally prohibits pretexting for sensitive consumer information.
The next technique is to conduct an interview or outright interrogation. Both of these require the victim to submit to the attacker's authority. This can be done by posing as a customer who needs the information to make a decision, pretending to be someone from the government who has the right to the information, or through intimidation. These attacks can be done cold, or after a relationship has been developed. The attacker can perform them in person using props like badges, or over the phone/email using spoofing to make it appear like the contact is from a legitimate source. An example would be to call someone as the Tech Department or Help Desk and tell them they have to reset their account because of a mistake made during a recent update. Most people want to be helpful, and automatically trust their computer. That desire to help or trust in their system is the key to compromising them. Both of these techniques are not by their nature antagonistic. Often the most effective techniques are based on establishing common bonds. All of these techniques require building a relationship based on trust. Finally, after interrogation comes torture, but that is beyond SE practices. Figure 7.1 shows the flow of these techniques.
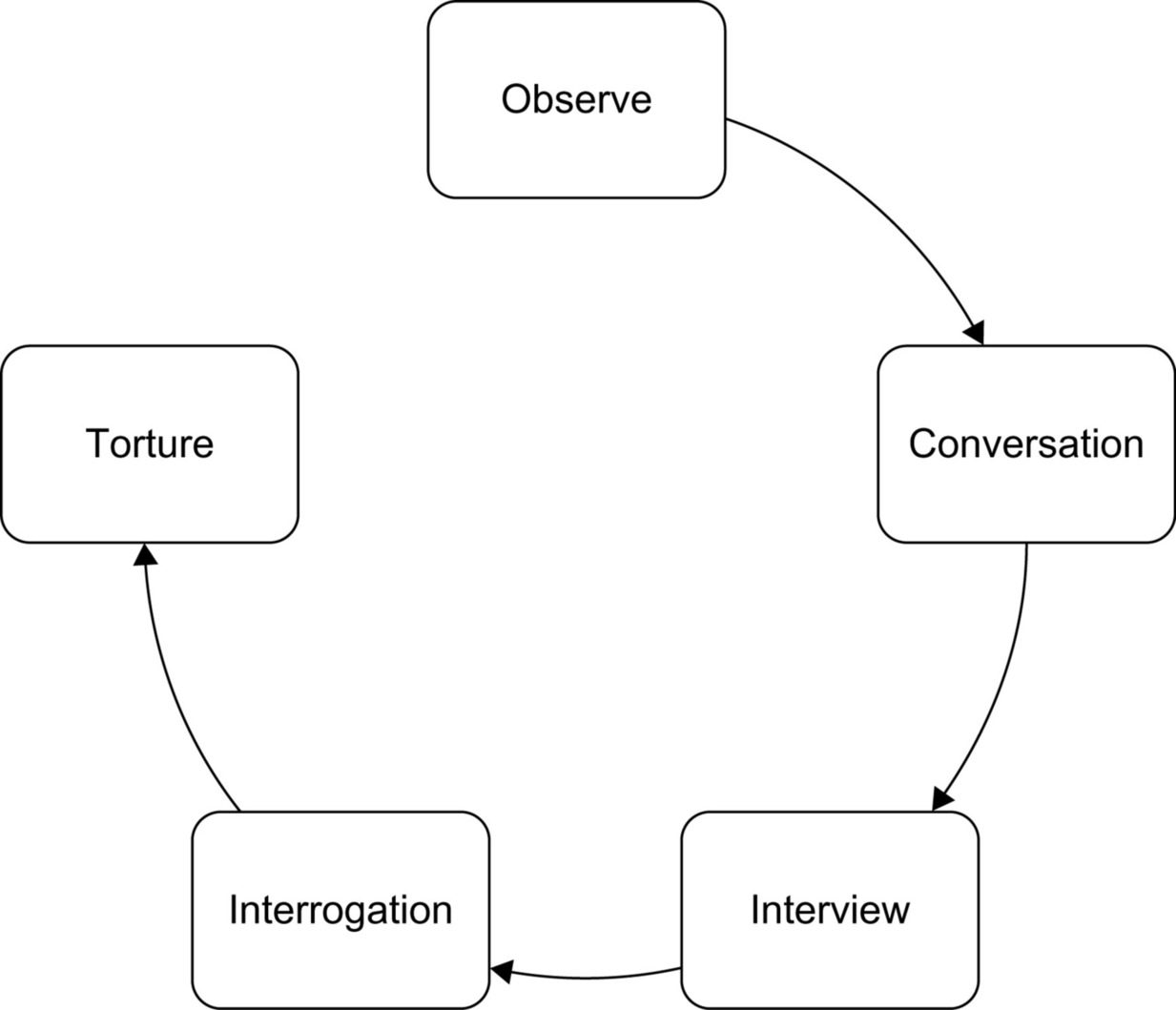 |
| Figure 7.1 Approach techniques from least to most aggressive |
Types of SE Methodologies
Some typical methodologies for general collection are divided into physical and electronic. Physical techniques include things like: Dumpster Diving (digging though target's trash), Shoulder Surfing (looking at their screen or keyboard while they work), Observation (tracking their activities—think stakeout), Spy Gear (like directional microphones/hidden cameras), and Impersonation (posing as utility worker). Electronic techniques include: Open web search (learn to use all the features of your search engine—i.e., Google will just search blogs…), Pay for Service sites like Intelius or U.S. Search, Credit Information Requests, Social networking site searches, Professional networking site searches and geolocation sites (i.e., Google Street View).
Though this information is generally open the SE may need some tools to make the research more effective. These include web sites and tools like:
• American Registry for Internet Numbers (IPs and Phone numbers for North America)
• Freedom of Information Act requests, OpenBook (Facebook searches)
• Maltego 3 (link mapping)
• Social Engineering Toolkit (technical hacks against the user)
• TwitScoop and Tweepz (Twitter searches)
• Trendistic (tracks terms hot on Twitter)
• TwitterMap (geolocation)
• PicFrog (image searches)
• TinyURL (allows URL redirection)
• Edgar [www.sec.gov/edgar] (corporate info)
• sites like Spokeo (people search) and Telespoof.com (caller ID spoofing)
• props (everything from clipboards to toolkits to deliveries)
• fake business cards, disguises (facial or uniforms), and fake or cloned badges.
This is just a quick list of some of the different types of tools that can be employed as part of social engineering.
One recent event that has captured the media's attention was the SE Capture the Flag event at DEFCON 18 called How Strong Is Your Schmooze?. There has always been a network based CTF event but in 2010 there was a SE CTF. Here is an excerpt from the report on the event:
Contestants were assigned a target company, with each having two weeks to use passive information gathering techniques to build a profile. No direct contact between the contestant and the target was allowed during this time. The information was compiled into a dossier that was turned in and graded as part of the contestant's score. During DefCon, contestants were then allowed 25 minutes to call their target and collect as many flags as possible, which made up the remainder of their score. Flags were picked to be non-sensitive information, and each was assigned a point value based on the degree of difficulty in obtaining the information associated with the flag. A few examples of the 25 flags are: In House IT Support, New Hire Process, Anti-Virus Used, Is there a Cafeteria, Wireless On-Site, Badges for Bldg Access and What OS Used.
Complex searches lead the contestants to gather quite a few PDFs or web pages that answered each of their inquires in full detail. One interesting surprise was the use of Google Street View as an information gathering tool. A primary factor in the success or failure of the contestant was the planning of the overall attack. The most interesting aspect of this has to do with how quickly and easily information could be obtained from all companies in a relatively short period of time, even with the caller under pressure. Final results were 15 companies called and 14 of them had flags captured[4].
How the Military Approaches Social Engineering
The military has been in the spy–counterspy business from the beginning; they are also experts at interrogation. Spying is the long con, whereas interrogation is generally the method used to get access to information in an immediate situation. This section will focus on the near term gathering of data (or the short con). We will look at the techniques used to extract information and discuss how they apply to SE.
First, we must understand that these techniques have been developed to work in both peacetime operations and combat situations. They are normally done in a controlled environment and are very similar to the techniques used by Law Enforcement Agencies. The basic principles are similar to SE and the foundational principles and many of the techniques apply well to SE attacks. The military trains interrogators and they will stay in that discipline their entire careers. They will become proficient in the languages and culture of their assigned region. Human Intelligence (HUMINT) operators or Interrogators are trained to deal with screening refugees, debriefing U.S. and allied forces, interrogating prisoners of war, interview collaborators, exploiting captured material, liaising with host nation, acting as interpreters if needed and interacting with the local population.
Army Doctrine
We will discuss how the Army deals with interrogation as they are the ones who are on the ground dealing with these issues. The basic techniques we will cover are from “FM 2-22.3 HUMAN INTELLIGENCE COLLECTOR OPERATIONS September 2006 [5].”
Goal: collector's objective during this phase is to establish a relationship with the source that results in the source providing accurate and reliable information in response to the HUMINT collector's questions.
Key principles: From a psychological standpoint, the HUMINT collector must be cognizant of the following behaviors:
• Want to talk when they are under stress and respond to kindness and understanding during trying circumstances.
• Show deference when confronted by superior authority.
• Operate within a framework of personal and culturally derived values.
• Respond to physical and, more importantly, emotional self-interest.
• Fail to apply or remember lessons they may have been taught regarding security if confronted with a disorganized or strange situation.
• Be more willing to discuss a topic about which the HUMINT collector demonstrates identical or related experience or knowledge.
• Appreciate flattery and exoneration from guilt.
• Attach less importance to a topic if it is treated routinely by the HUMINT collector.
• Resent having someone or something they respect belittled, especially by someone they dislike.
These principles are used to develop an approach, build rapport, and establish a relationship in which the HUMINT collector presents a realistic persona designed to evoke cooperation from the source. In the military things are usually done in accordance with established procedures and if it is a mission (like an interrogation) should have a documented plan. This is not to say they are not flexible and resist innovation but rather to say they want increase the chances of mission accomplishment and have found these lead to greater success. The HUMINT collector must ensure their body language and personal representation match their approach.
Some standard operating approach techniques are: direct, incentive, emotional (Love/Hate/Fear/Pride/Futility/Anger), “we know all” or “file/dossier,” rapid-fire (don't let them talk), Mutt and Jeff or good cop/bad cop, and false flag (misrepresentation of oneself). See Figure 7.2 for how these relate to each other. The direct approach is simple and straightforward. It is simply telling the person what they want and using interview/interrogation skills to convince them to cooperate and share the information. This technique is useful in a conventional war but not very useful in counterinsurgencies or for social engineering. Statistics from interrogation operations in World War II show that the direct approach was effective 90% of the time. In Vietnam and in Operations URGENT FURY (Grenada, 1983), JUST CAUSE (Panama, 1989), and DESERT STORM (Kuwait and Iraq, 1991), the direct approach was 95% effective. The effectiveness of the direct approach in Operations ENDURING FREEDOM (Afghanistan, 2001–2002) and IRAQI FREEDOM (Iraq, 2003) are still being studied; however, unofficial studies indicate that in these operations, the direct approach has been dramatically less successful [6]. The military is still analyzing the reasons but one common assumption is that the motivations of religious fanaticism are harder to compromise than traditional nationalism. There are some general types of direct questions that are useful: Initial (get the discussion going), Topical (focused on establishing how much they will communicate and what their level of knowledge is), Follow-up (making sure we have gained all the primary and peripheral information), Non-pertinent (establishing rapport and keeping discussion going), Repeat (seeing if they are consistent), Control (establish baseline), Prepared (for areas interviewer is unfamiliar with or highly technical topics). One of the key questions here is the control or baseline question. It establishes how someone behaves when they are telling the truth. Much like a polygraph test starts with questions like your name and address then gradually builds to questions related to guilty actions so they can compare the stress reactions to the baseline a SE must understand how the target behaves when not under stress.
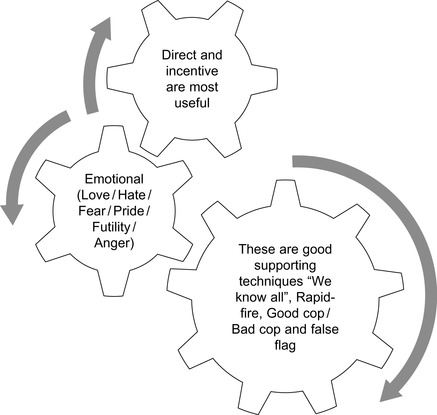 |
| Figure 7.2 The various approaches must be integrated |
The indirect approach, or using elicitation, can often be useful as we combine the information gathering with normal conversations with targets of interest without them knowing they are being interrogated. Elicitation is a sophisticated technique used when conventional collection techniques cannot be used effectively. Of all the collection methods, this one is the least obvious. However, it is important to note that elicitation is a planned, systematic process that requires careful preparation [7]. This is where the more the interviewer knows about the target the better, so they can have a natural flowing conversation. For example they may start by sharing information they have so the target assumes they know all about it and will openly discuss the details.
Next comes incentive. This is basically offering the target something they want or need. The first thing that comes to mind is bribing them, but it can be as simple as an email offering to increase their speed or access to the Internet. This approach can be very effective when tied to the right emotions. The emotional approach is where the target's emotions are brought into the interaction to get them to take an action that they would not normally do. A recent example of this is what is known as scareware. A good example would be when a pop-up box will announce there is a problem on the system that can be fixed by installing a free update. The update is a Trojan horse and doesn't do anything but compromise their system. This approach is based on Fear, other emotions that can be used are: Love (in its many forms), Hate or Anger (us against them), Pride (in themselves or their organization), and Futility (there is no other option). Picking the right emotion is easier in person because we can read the body language or on the phone where we can judge the tone of voice and modify the approach based on the situation. The goal of this method is to manipulate the target's emotions so they override their natural cognitive reactions.
Other well-known techniques are: “we know all” or “file/dossier”; this is where the interrogator would come in and lay a folder labeled “witness statements” or a DVD labeled “surveillance footage” on the desk. They would contain no actual information but allows the interrogator to start by saying something like, “we have the evidence we need but want to get your side of the story before we submit our final report.” For a SE the presentation of material that supports the belief that we know the basics but just need them to provide the details. If they are still not talking freely it may be time to try the rapid-fire method where we keep interrupting them so they get frustrated and jump in with key facts so we will listen. It is also used when the target is going to say something that the interrogator doesn't want them to say like “I never went to that site” because once they tell a lie it is harder to get to the truth as first we must make them admit they lied.
The last two methods we will discuss are Mutt and Jeff, or good cop/bad cop, and false flag. We have all seen the aggressive and compassionate interview team in movies. The target will identify with the compassionate person and tell their story so they will shield them from the aggressive one. It can also be a really abusive interrogator followed by one who apologized for the unprofessional behavior of their colleague. Typically the good cop would help the target rationalize their actions so they can talk about them openly. One way this method can be used by SE's is on social networking sites; we could present a Fakebook (fake FaceBook) personality created for the attack as a cyber bully and a second as someone defending the target. Finally using the false flag, for the military this might be having a new interrogator come in and pretend to be from a friendly country or a non-government origination like the Red Cross. This is very useful as it is simply misrepresentation and is a bedrock of Social Engineering.
We can see that most of the techniques used by the military are directly applicable to the civilian sector and can be applied to both physical and cyber environments. The most important aspects the military brings are proven Tactics, Techniques, and Procedures (TTPs) and careful mission preparation and planning. These when applied to Social Engineering will give the attacker a strong capability to be successful on their mission.
How the Military Defends Against Social Engineering
As the military approach to SE section discussed, the military has been in the spy–counterspy business from the beginning. The counterspy techniques are the same skills needed to defend against SE. Today's solider needs to understand counterintelligence (CI), counterterrorism, force protection and Operational Security (OPSEC) techniques. This section will focus on the tactical level actions than can be done for CI. First let's review the doctrinal definitions for the key concepts:
• Counterintelligence: Information gathered and activities conducted to protect against espionage, other intelligence activities, sabotage, or assassinations conducted by or on behalf of foreign governments or elements thereof, foreign organizations, or foreign persons, or international terrorist activities [8].
• Cyber Counterintelligence: Measures to identify, penetrate, or neutralize foreign operations that use cyber means as the primary tradecraft methodology, as well as foreign intelligence service collection efforts that use traditional methods to gauge cyber capabilities and intentions [9].
• Counterespionage: That aspect of counterintelligence designed to detect, destroy, neutralize, exploit, or prevent espionage activities through identification, penetration, manipulation, deception, and repression of individuals, groups, or organizations conducting or suspected of conducting espionage activities [10].
• Counterterrorism: Actions taken directly against terrorist networks and indirectly to influence and render global and regional environments inhospitable to terrorist networks [11].
• Force Protection: Preventive measures taken to mitigate hostile actions against Department of Defense personnel (to include family members), resources, facilities, and critical information. Force protection does not include actions to defeat the enemy or protect against accidents, weather, or disease [12].
• Operations Security (OPSEC): A process of identifying critical information and subsequently analyzing friendly actions attendant to military operations and other activities to: (a) identify those actions that can be observed by adversary intelligence systems; (b) determine indicators that adversary intelligence systems might obtain that could be interpreted or pieced together to derive critical information in time to be useful to adversaries; and (c) select and execute measures that eliminate or reduce to an acceptable level the vulnerabilities of friendly actions to adversary exploitation [13].
The military depends on confidentiality and secrecy. They deploy encryption, data classification, clearances for their personnel, and a thorough set of processes and regulations. Soldiers, Airmen, Seamen, and Marines understand the trust they have been given and the level of National Security compromise that could occur (not necessarily through a single loss of data but the aggregate knowledge impact as well). Cybersecurity has become a critical component of the National Counterintelligence Strategy (see Figure 7.3). The mission to secure the nation against foreign espionage and electronic penetration of the IC, DoD, and to protect U.S. economic advantage, trade secrets and know-how is becoming a core responsibility for them.
 |
| Figure 7.3 Counterintelligence is a national concern; this is the U.S. strategy to deal with it [14] |
CI has an offensive aspect as well. There is a need to set up traps or as they are called in cyberspace “honey pots” to attract insiders accessing information they are not authorized for. We need to have enticing files with embedded beacons that report back on where they are to see what has leaked out. We need to fund programs to gain access to the types of organizations that have the motives and means to attack the United States and see what they have stolen. We need to conduct exercises and tests on our personnel to assess our readiness level. Finally we need to enforce consequences on individuals caught violating policies.
How the Army does CI
Army regulation (AR 381-12 Threat Awareness and Reporting Program 4 October 2010 (for the old soldiers this was called Subversion and Espionage Directed against the U.S. Army or SAEDA)) establishes the training requirements and reporting procedures. It also lays out indicators or suspicious activities, such as foreign influence or connections, disregard for security practices, unusual work behavior, financial matters, foreign travel, undue interest, soliciting others, and extremist activity. This is basically a process that encourages every member of the staff to become a security officer and help police both themselves and their coworkers. The program is built around two key principles: situational awareness and behavior monitoring, both for themselves and the rest of the staff. If done well, it will counter the whole spectrum of crime, internal threats (disgruntled or unstable workers), external threats (foreign operatives and terrorist), and today's social engineers. If done poorly, it allows incidents like the recent unauthorized release of a large number of classified documents relating to the U.S. war in Iraq to WikiLeaks. For the sake of brevity, we're not going to delve into the processes of the Navy and Marine Corps, although they're both quite capable in their own right at these processes and procedures.
An Air Force Approach
The Air Force Public Affairs Agency has published a “Social Media” Guide, Social Media and the Air Force–Air Force Public Affairs Agency. Top 10 tips include items like: OPSEC is crucial to our mission, be aware of the image you present. The image you present will set the tone for your message and the enemy is engaged. You must engage there as well [15]. This is a very good example as it does a couple of things well. First the guide is more about what we should use rather than why we should not use the many different communication applications on the web. Second it is a formal policy that includes punitive consequences for misbehavior.
An important aspect of this defensive capability is to analyze the information that is leaking and conduct the appropriate investigation to determine what actions need to be taken. Historically there are examples like Aldrich Ames, Robert Hanssen, Colonel Vladimir Vetrov, a KGB defector known as the Farewell Dossier, Gregg Bergersen, and the 11 Russian spies recently deported from the United States, but these operations are time consuming, expensive, and risky where we can get much of the same material through cyber spying. The risk of getting caught is lower, the time to gain access is faster, and the cost is cheaper. We have talked extensively about computer network exploitation; when we combine that with Social Engineering we have a paradigm shift in spying capabilities. This requires us to look at the techniques that got these traditional spies caught, including careful analysis, auditing financial records, tips from co-workers, offensive operations to gain access to enemy files to see who they had turned into spies, and encouraging defectors to switch sides.
Summary
SE is a very dangerous threat vector to all organizations and individuals. It requires training and vigilance to defend against. For example simple questionnaire to someone on a social networking site asking them to answers question about themselves so they can become closer friends could include the same questions asked by the company to reset their password and now the organization is compromised. We need to make sure people are vigilant and cautious (remember we're not paranoid if they are out to get you). We can leverage lessons learned in the military to understand how these works and how we defend ourselves. Defenses against Social Engineering must be focused on behaviors.
The policies, culture, and training must be reinforced often to insure the work-force stays vigilant. Training the staff to have situational awareness is key to a good counter-SE program. This training must be continuous with messages from multiple sources—emails, meetings, and formal training. There needs to be exercises to test the staff like emails asking employees to go to a site and enter their password only to find a message from the company that they would have allowed hackers to gain access to the network if it was a real attack. Security audits should include SE attacks to validate the training is effective. There is a saying in the hacker community: “You can't patch stupid,” which often refers to the fact that if a organization has a great technical security infrastructure and they can get through them, just go after the people. People are not stupid; they just don't understand the risks they are taking with their actions. Training can fix that.
The bottom line is: this is the growth area for threat vectors via social media and the only way to defend against it is executive awareness, user training, and validation exercises.
Endnotes
1.
Department of Defense. Joint electronic library. http://www.dtic.mil/doctrine/; [accessed 07.09.10].
2.
Commtouch Software Ltd Q1 2010 internet threats trend report. http://www.commtouch.com/download/1679; [accessed 12.09.10].
3.
Financial Modernization Act of 1999. Federal Trade Commission. Facts for Consumers. http://www.ftc.gov/bcp/edu/pubs/consumer/credit/cre10.shtm; [accessed 07.11.10].
4.
Hadnagy, CJ, Aharoni M, and O’Gorman J. Defcon 18 social engineering CTF – how strong is your schmooze. socialengineer.org. http://www.social-engineer.org/resources/sectf/Social-Engineer_CTF_Report.pdf; [accessed 07.11.10].
5.
Army, U.S. FM 2-22.3 (FM 34-52) Human intelligence collector operations. Public affairs. http://www.army.mil/institution/armypublicaffairs/pdf/fm2-22-3.pdf; 2006.
6.
Ibid.
7.
Ibid.
8.
Department of defense. Joint electronic library. http://www.dtic.mil/doctrine/; [accessed 07.09.10].
9.
Ibid.
10.
Ibid.
11.
Ibid.
12.
Ibid.
13.
Ibid.
14.
Office of the director of national intelligence's office of the national counterintelligence executive. http://www.ncix.gov/publications/policy/2008_Strategy.pdf; [accessed 17.10.10].
15.
Social Media Guide. Air force public affairs agency emerging technology division. http://info.publicintelligence.net/USAFsocialmedia.pdf; [accessed 02.10.10].