IP’s flexibility and simplicity have met the needs in data processing network matters; however, its starting goal was not to ensure secure communication, which is a reason behind a strong absence of functionalities. The ease of attacks and the will to use IP for sensitive applications have incited the development of security solutions such as filtering routers, firewalls and secure protocols and applications. IPSec is a standard that defines a security extension for the IP protocol to make it possible to secure the IP layer and the higher layers. It was developed, at first, for the new generation IPv6 protocol and was then carried over to IPv4. The security services provided by IPSec are confidentiality, authentication and data integrity, anti-replay protection and access control.
The rapid evolution and deployment of wireless networks based on the IEEE 802.11 standard for Internet access present new security problems that did not exist previously in telegraphic networks. The WEP (Wired Equivalent Privacy) protocol was developed with the intention of bringing security solutions to wireless networks. However, this WEP protocol proved not to be adapted as it contains security weaknesses and presents key distribution problems. Then, there was the development of a security architecture called RSN (Robust Security Network). This architecture is based on the IEEE 802.1X standard, which offers strong authentication and authorization mechanisms and dynamic key distribution mechanisms for communication encryption in wireless links. In this chapter, we will detail the two security architectures IPSec and IEEE 802.1x.
IPSec is a group of data security mechanisms that is integrated in TCP/IP to process each emitted or received IP packet. This processing can be the rejection of the packet, the application of security mechanisms or the permission to pass. Its integration in TCP/IP makes IPSec exploitable by higher layers by offering a unique security mechanism for all of the applications.
IPSec aims at preventing various possible attacks on the IP networks by preventing in particular the spying of the data circulating on the network or being passed off as something else. For this, IPSec can provide the following security services:
– Confidentiality: the data that is transported can only be read by the emitter and the receiver. No information circulates unencrypted on the network. It is also possible to encrypt the IP packet headers.
– Data authenticity and access control: this consists of two services, which are the data source authentication and the integrity of the data.
– Authentication guarantees that the received data come from the declared expediter.
– Integrity guarantees that the data has not been modified.
– Authenticity of each received packet makes it possible to implement access control, particularly to protect access to resources or private data.
– Anti-replay protection: this makes it possible to detect an attack attempt consisting of resending a valid packet previously intercepted on the network. The whole of these services are based on modern cryptographic mechanisms which give them a high level of security.
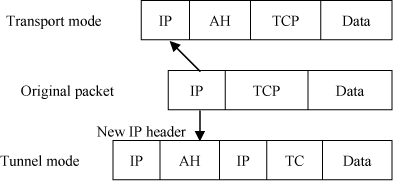
IPSec uses two protocols, AH and ESP, to ensure communication authentication, integrity and confidentiality. IPSec can be used to secure either the entire IP packet, or the layers above it. The appropriate modes are called tunnel mode and transport mode.
In transport mode only the content of the IP packet is protected. This mode is useable on terminal equipment (clients, servers).
In tunnel mode: the whole content of the IP packet is protected by its encapsulation into a new packet. This mode is used by network equipment (routers, firewalls, etc.).
The AH (Authentication Header) and ESP (Encapsulating Security Payload) protocols can be used either separately or combined.
The AH protocol ensures the authenticity of non-confidential IP packets (without encryption). The principle of this protocol is to add a supplementary field to the IP packet, which makes it possible, upon receipt, to verify the authenticity of the data. A sequence number makes it possible to detect replay attempts. AH calculates an HMAC based on the secret key, the packet payload and the consistent parts of the IP header. Then, the AH header is added to the packet. The AH header is illustrated in Figure 14.2.
The AH header is 24 bytes long. The next header field is the same as the one in the IP header. In tunnel mode, the next header field is equal to “4” because it is an encapsulation of the IP packet within another IP packet. In the transport mode, if we encapsulate TCP, the next header field is 6. Given that AH protects IP by including the immutable parts in the IP header, it therefore does not cross the NATs.
This protocol guarantees data confidentiality and can thus guarantee authenticity. The ESP principle is to generate, from an IP packet, a new packet in which the data (possibly the header) is encrypted. It can also ensure authenticity by adding an authentication block and anti-replay protection by using a sequence number. After packet encryption and HMAC calculation, the ESP header is generated and added to the packet. The ESP header consists of two parts, as illustrated in Figure 14.3.
The initialization vector (IV) is used in the encryption process. Symmetric encryption algorithms are susceptible to attacks if the IV is not used. The initialization vector ensures that the encryption of two identical pieces of information (payload) gives two different pieces of information. IPSec uses block encryption, which means using stuffing in the case where the length of the encrypted data is not a multiple of the size of the block. The HMAC is calculated on the basis of useful information in the packet and does not take the IP header into consideration.
To protect packet integrity, IPSec uses HMACs. To derive the HMAC, IPSec uses hash algorithms such as MD5 and SHA in order to calculate the hash based on the secret key and the IP packet contents. This HMAC is then integrated into the IPSec header and the receiver of the packet can verify the HMAC and see if it has the secret key.
To guarantee IP packet confidentiality, the IPSec protocol uses symmetrical encryption algorithms. The IPSec standard imposes the implementation of NULL and DES. Currently, more powerful algorithms are used such as 3DES, AES and Blowfish.
To ensure protection against service denial attacks, IPSec uses a sliding window. A sequence number is assigned to each packet and the packet is only accepted if the number is within the window. Old packets are immediately suppressed. This solution protects against replay.
To encapsulate and decapsulate IPSec packets, the extremities need to store the participants’ secret keys, algorithms and IP addresses. All these necessary IPSec parameters are stored in security associations (SA). These SAs are stored in an SAD (Security Association Database).
An SA is composed of the following parameters:
– source and destination IP addresses of the extremities that are protecting the IP packets;
– IPSec protocol (AH or ESP);
– the algorithm and the secret key used by IPSec;
– index (SPI). A 32-bit number identifying the SA;
– IPSec mode: tunnel or transport;
– size of the anti-replay protection window;
– lifetime of the SA.
A security association can only protect one single direction of traffic. To protect the two directions, IPSec needs two security associations. Other information stored in the SP (Security Policy) is necessary to define what type of traffic needs protection.
An SP specifies the following parameters:
– source and destination packet addresses. In transport mode, these are the same addresses as in the SA;
– the protocol (and port) to be protected;
– the SAs to be used.
The secret keys and the algorithms must be shared between all the participants of a secured session. This can be carried out by a manual approach and an automatic approach, both of which are defined as follows:
– Manual: a first approach for key exchange is the manual management, which consists of enabling the administrator to manually configure each piece of equipment using IPSec with the appropriate parameters. This approach is practical in a small-sized and static environment; on the other hand, it is not at all convenient in a large-scale environment. In addition, it is based on a static definition of the parameters without renewal.
– Automatic: the second approach is the automatic management by means of an appropriate protocol. The parameter management protocol relative to IPSec is IKE (Internet Key Exchange), which is not only related to keys. This protocol does not manage (negotiate, update, suppress) all the security parameters. IKE is a high-level protocol whose role is to open and manage a pseudo-connection on top of IP (AH and ESP directly act on the IP level). IKE includes, at the beginning of the negotiation, a mutual authentication of the participants that can be based either on a shared secret or on public keys. The exchange of public keys used by IKE can be done manually directly in the framework of IKE by the exchange of online certificates, or by means of a public key infrastructure (PKI).
The security services offered by IPSec are based on choices defined by the network administrator by means of security policies. These policies are stored in a Security Policy Database (SPD). An SPD is composed of a list of rules, where each rule carries a number of criteria that make it possible to determine what part of the traffic is concerned.
Consulting the SPD makes it possible to decide, for each packet, if it should follow security services and if it will be allowed to pass or, on the contrary, be blocked. This basis indicates to IKE what SA it must negotiate and in particular which secure tunnels it must establish.
All the details concerning IPSec can be viewed on the IPSec workgroup page of IETF at http://www.ietf.org/html.charters/ipsec-charter.html.
The IEEE 802.1x standard (Port-Based Network Access Control) defines a mechanism that makes it possible to control access to resources on a local IEEE 802 network that can be wired or wireless. It offers mechanisms that make it possible to authenticate and authorize users connecting point-to-point on a local network’s port.
The 802.1x standard was conceived to be used in wireless networks but it is now widely used in 802.11-type wired networks. Thus it offers the possibility to access points to control network access and to distribute or obtain key information on the part of authenticated users. The development of the 802.1x standard was subscribed from the following needs:
– Rapid 802.11 network deployment in public and private locations.
– A wireless network operator wishes to control the users that are accessing it. Currently, we can connect easily enough on any 802.11 network.
– The need to use AAA. AAA technology such as the Radius protocol is widely used to control the access of users on the networks. 802.1x can use the existing infrastructures to offer AAA functionality to the users.
– The need to dynamically distribute the keys. The WEP (Wired Equivalent Privacy) protocol was created to offer security on a wireless network by using symmetrical encryption keys. One of the limitations of this approach is the management and distribution of keys.
The 802.1x standard makes it possible to distribute WEP keys to users and to access points.
It should be noted that WEP technology was completed by taking into account IEEE 802.1x authentication and by the regular modification of keys due to TKIP technology. This new standard is called WPA (Wireless Protected Access). This WPA technology was completed in June 2004 by the 802.11i standard, which still includes IEEE 802.1x authentication and incorporates a new encryption algorithm, AES, much more robust than RC4, which is in WPA. This new standard is called WPA2.
There are three entities in the 802.1x protocol architecture:
– The client, who represents a user wanting to connect to the network.
– The authentication system, which:
- communicates with the client and submits client information to the appropriate authentication server,
- enables the user, if authenticated, to use the network,
- acts independently from the authentication method used as it acts as relay between the authentication server and the client.
– An authentication server which contains users’ information as well as their network use rights. The most widely used and deployed today is the Radius server.
The 802.1x architecture offers, to the authentication system, the possibility of creating two network connection points for users. The first connection point, called the uncontrolled port, makes it possible to exchange blocks of EAP data between the client and the authentication system. The second connection point, called the control port, makes it possible to transfer client traffic if it has been authorized.
The 802.1x standard relies on the use of the EAP (Extensible Authentication Protocol) for user authentication. The EAP was developed as an extension of the PPP protocol in order to make it possible to deploy and use authentication mechanisms in a given network. The EAP was created to enable the addition of authentication modules at the level of client access and authentication server.
EAP extendibility is ensured by:
– the installation of an EAP library on the client and on the server; different types of EAP protocols can be supported;
– the modification of the EAP type can be carried out at any moment;
– the support of authentication schemes such as:
- generic Token Card,
- OTP (One-Time Password),
- TLS (Transport Level Security),
- chip cards,
- certificates,
- future authentication technologies.
An EAP session unfolds as follows:
– Establishment of a link.
– No choice in authentication protocol.
– Each PPP pair negotiates to execute EAP during the authentication phase.
– Authentication phase.
– Negotiation of the EAP authentication scheme to use as EAP type.
– Choice of EAP type (finished).
– Message exchange between the client (user) and the authentication server.
– Conversation, which consists of authentication information requests and responses.
The EAPOL protocol (EAP over LAN) is an EAP message encapsulation protocol on an LAN network. It makes it possible to notify EAP sessions by beginning and end session messages.
The 802.1x standard enables:
– Logic access. In a wireless 802.11 network, a station must create an association with the access point before using the network. The protocol that creates the association enables the client and the access point to exchange their MAC addresses. This creates a logic access that the station can use to communicate with the access point and thus dynamically derive the available WEP keys. Once the association is established, the client can then be authenticated by using the EAP protocol.
– WEP key management. The 802.1x standard does not exclude and does not require the WEP protocol or any other encryption protocol. It offers a mechanism that makes it possible to distribute encrypted information from an access point to a client using the EAPOL-Key message. This can be done in a session. Thus, if an illintentioned person obtains a WEP key, it will not be of any use after the user ends the session.
The diagram in Figure 14.6 describes the EAP authentication phase. As previously indicated, a client must first be associated with the access point before exchanging EAP messages.
The exchanged EAP messages between client and access point are transported by the EAPOL protocol. EAP messages are then transmitted by the Radius protocol between the access point and the Radius server. This makes it possible to create an authentication session between the client and the authentication server. Once the user is authenticated, the EAP-Key message is sent with the goal of exchanging key information between the access point and the client.
The IEEE 802.1x standard makes it possible to implement security mechanisms on local 802 networks and particularly on wireless IEEE 802.11 networks. In addition, the fact that access points use the EAP protocol for authentication makes it possible to support multiple authentication methods such as certificates, chip cards, etc. Currently, the 802.1x is the most deployed security standard in wireless networks and is supported by the majority of access point equipment and by computer operating systems.
[ATK 98] KENT S., ATKINSON R., “IP Encapsulating Security Payload (ESP)”, RFC 2406, November 1998.
[BLU 98] BLUNK L., VOLLBRECHT J., “RFC 2284: PPP Extensible Authentication Protocol (EAP)”, IETF, March 1998.
[GRA 02] GRAHAM J. W. II, “Authenticating Public Access networking”, SIGUCCS’02, Providence, Rhode Island, USA, 20-23 November, 2002.
[IPS 98] KENT S., ATKINSON R., “RFC 2401: Security Architecture for the Internet Protocol”, IETF, November 1998.
[JAS 01] JASON J., RAFALOW L., VYNCKE E., “IPsec Configuration Policy Model”, Internet Draft, November 2001.
[KEN 98] KENT S., ATKINSON R., “IP Authentication Header”, RFC 2402, November 1998.
[KRA 97] KRAWCZYK K., BELLARE M., CANETTI R., “HMAC: Keyed-Hashing for Message Authentication”, RFC 2104, February 1997.
[MAD 98] MADSON C., GLENN R., “The Use of HMAC-MD5 within ESP and AH”, RFC 2403, November 1998.
[MAL 02] MALLADI R., AGRAWAL D. P., “Current and Future Applications of Mobile and Wireless Networks”, Communications of the ACM, vol. 45, no. 10, October 2002.
[NIK 02] NIKANDER P., “Authorization and Charging in Public WLANs using FreeBSD and 802.1x”, USENIX annual technical conference, 10-15 June 2002.
[P8021.X] “Standard for Port-Based Network Access Control”, IEEE Draft P802.1X/D11, LAN MAN Standards Committee of the IEEE Computer Society, 27 March 2001.
[RIG 00] RIGNEY C., WILLENS S., RUBENS A., SIMPSON W., “RFC 2865: Remote Authentication Dial in User Service (Radius)”, IETF, June 2000.
[SCH 03] SCHMIDT T., TOWNSEND A., “Why WI-FI Wants to Be Free”, Communications of the ACM, vol. 46, no. 5, May 2003.
[VAR 00] VARSHNEY U., VETTER R., “Emerging Mobile and Wireless Networks”, Communications of the ACM, vol. 43, no. 6, June 2000.
[WLAN 99] IEEE. 802.11b/d3.0 Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specification, August 1999.
[ZHA 02] ZHANG J. et al., “Virtual Operator-Based AAA in Wireless LAN Hot Spots with Ad-Hoc Networking Support”, Mobile Computing and Communications Review, vol. 6, no. 3, 2002.
1 Chapter written by Idir FODIL.