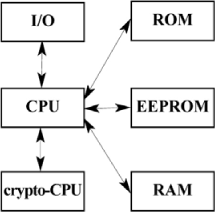
Figure 16.1. Interactions between a smart card’s components
The inherent lack of security in the world of wireless data networks pushes users to secure their digital environment. The network can no longer be considered a trustworthy environment. It is necessary from now on to use safe mechanisms that make it possible to use networks without risk.
The smart card was initially designed with the purpose of securing banking transactions. It has also put forward its security advantages in second-generation mobile telephone networks, within the GSM standard. Smart card technology has been tried and tested and is standardized by the ISO 7816 standard. Its mobile character along with its capability of handling information makes it a perfect candidate for securing data networks.
In this chapter, we will present the microprocessor smart card’s different characteristics that could make this technology the cornerstone of Internet security.
We will also present the microprocessor contact smart card, while keeping in mind that its contactless counterpart benefits from the same possibilities, as well as those characteristics of a contactless interface.
The smart card is not a new technology. In fact, since the end of the 1960s, European, American and Japanese researchers have been considering it [RAN 00, JUR 03].
Many people around the world have contributed to the implementation of this technology, but it is the French who gave rise to the current smart card. In 1974, the first patent on the memory card was registered. In 1978, a French engineer invented the microprocessor card with the SPOM patent1.
Its information processing capabilities equips it with a certain intelligence2. The smart card will not undergo any major changes in its functioning principle3.
Since the beginning of the 1980s, industrial applications have been appearing. In France, the use of the smart card as a method of payment in public phone booths and its use in the banking industry caused a new industry to emerge [TOW 02].
A smart card is created in a series of steps relating to its different parts: the chip, the plastic support and the external module. All these parts are standardized, which makes a segmented industrialization possible.
The smart card can be considered a microscopic computer. In fact, it is composed of the same functional elements as computers. It integrates a microprocessor, often a second microprocessor specialized in the acceleration of cryptographic operations, memory, a communication port and functions with an operating system. The power of current cards is often compared to that of the first microprocessor, the IBM-PC4. The fundamental difference with a true computer is that all these elements are on a single silicone substrate, on an electronic chip5, whereas they are separated into several electronic components in a computer.
Figure 16.1 presents the different components on the chip as well as their interactions. The microprocessor (CPU) through which all information flows plays a preponderant role.
Smart card processors are most often based on an 8-bit design and are operated at a speed of 3.3 MHz. The new generation of 32-bit processors achieves a speed of 33 MHz.
A smart card’s memory is generally less than 64 Ko. New types of memory, such as Flash or FeRAM, make it possible to achieve a laboratory memory capacity close to a megabyte. In a few years, it is possible that this capacity will be in the order of gigabytes [VER 00].
Today, it is nevertheless possible to simulate larger storage capacity in a smart card.
For example, there are solutions such as [BIG 98], which combine encrypted data storage on the network and the use of a personal smart card that makes it possible to restrict access to this information to only the card carrier.
Typically, the viewing of sensitive images such as x-rays in the medical field is therefore limited to the doctor who is treating the concerned patient.
This electronic chip is inserted in a plastic card that serves as transportation support. The format of the plastic card is similar to that of old magnetic cards whose format is ID-I6. However, the ID-000 format, made popular by the use of SIM cards in GSM terminals, is much smaller, as shown in Figure 16.2.
As it is naturally very fragile, the chip must be protected. For this reason, it is covered with a module that ensures a physical protection and serves as an interface with the external environment. It feeds the chip with an electronic current, provides it with a clock and allows it to communicate. This visible module7 is what physically differentiates a smart card from a magnetic card. It is composed of eight contact zones, as indicated in Figure 16.3.
Each contact’s role is described below:
– C1: electric feed;
– C2: re-initialization;
– C3: clock;
– C4: unused;
– C5: electric mass;
– C6: no longer used (initially programming tension);
– C7: serial communication;
– C8: unused.
We note that on these eight standard contacts, only five are used. Some manufacturers use contacts C4 and C8, reserved for future use, in conformance with the ISO 7816 standard, to add supplementary functions to the card, such as the possibility of communicating via USB8 instead of the standard serial link.
To use a smart card, it must be inserted into an active electronic device capable of interacting with it9. Such a reader exchanges standardized messages with the card. These messages authorize the reading and writing in the card’s memory. Despite its denomination, a smart card reader therefore makes it possible to write data into a card.
A smart card can be compared to a micro-server that uses a half-duplex communication protocol.
Smart card communication can be done by the intermediary of APDU messages10. There are two types11: command APDUs and response APDUs (see Figure 16.4).
Command APDUs are always sent by the entity12 that wishes to use the card, whereas response APDUs are sent by the card in response to command APDUs. Figures 16.5 and 16.6 show the different fields13 that make up the command APDUs and the response APDUs.
Significance of the initials:
– CLA: the class of the instruction to be sent (ISO, proprietary, etc.);
– INS: instruction to be executed by the card;
– P1: first instruction parameter;
– P2: second instruction parameter;
– Lc: length of the optional data field;
– Le: length of the expected APDU response;
– SW1 and SW2: card status indicators.
There can be several types of command APDUs.
When the optional part is non-existent, the command sent to the card is to execute an instruction without entrance or exit data (for example, a command to destroy data stored on the card). The card’s response indicates if there were any processing errors (0x9000 indicates success).
If the optional part contains a Le field, the card also returns the data.
In the case of an LC field and a data field without an Le field, the data will be sent and processed by the card but no data will be sent back.
A communication protocol common to all smart cards has been defined: ISO 7816-4. This is an archaic protocol based on message exchange. It only defines reading and writing operations for raw data without defining the high level interface such as data flows or files, which slows the development of applications that use a smart card.
To hide this protocol, several approaches propose an interaction with the card with the help of higher abstraction level protocols.
In [ITO 99], the author proposes accessing the smart card file system transparently by integrating it into UNIX type system file structure in the manner of NFS [SAN 85]. The operating system’s automatic handling of the complexity of the ISO 7816 communication protocol greatly facilitates the development of applications.
There exist different approaches to access smart cards via the HTTP protocol, whose use is widespread in the World Wide Web (WWW).
[BAR 99] proposes accessing the card by URLs that are relayed by an HTTP proxy. This proxy, working on the computer on which the card is connected, translates the card’s destination URLs into a series of specific APDUs.
The authors of [REE 00] followed a very different road by implementing an HTTP server directly into a smart card. They implemented a TCP/IP communication specific stack between the card and the computer to which it is connected in order to link the network card.
To open the world of GSM networks to the Internet, the authors of [GUT 00] propose implementing an HTTP server in SIM cards by using the SIM Toolkit14. To function with the current mobile GSM terminals, the authors recommend the GSM operator’s use of HTTP proxies. These encapsulate the HTTP requests into SMSs15 that they send to the mobile terminal.
Java’s RMI method is used in [MIC 01] to describe the smart card’s resources. Two APDUs are successively used to choose and invoke the smart card’s service. This method is limited to the use in the Java environment.
The evolution of smart card readers followed that of microcomputer communication ports. The oldest readers communicate through serial or parallel microcomputer ports. These ports, which were not electronically powered, required an external source of electricity16. In a marginal way, certain keyboard manufacturers integrate a reader into their products. Another attempt at the democratization of the use of smart cards relies on a card reader introduced in floppy disk drives already integrated in machines. Portable microcomputers also have readers that are dedicated to the PCCARD17 format. From now on, most new smart card readers use the USB port for all of its advantages18. Certain microcomputer makers deliver certain models with a reader directly integrated into the machine.
In [ITO 01b], the authors propose the use of a remote smart card, which would make it possible to benefit from the advantages of smart cards on machines that do not have a reader. Their solution consists of keeping the smart card in a safe place, where it would be permanently connected to a computer linked to the network. The traditional services relying on local cryptographic resources, such as SSH [YLO 96] or PGP [ZIM 95], must be modified to use the remote smart card’s cryptographic resources by using the Simple Password Exponential Key Exchange (SPEKE) protocol [JAB 96].
Recent technological advances in this matter have led us to think that readers will soon disappear, the cards having integrated communication port management. In fact, electronic chip manufacturers have succeeded in integrating the complete USB protocol management into the chip. Thus, the simple fact of physically linking such a card to a microcomputer’s USB port makes it possible for the terminal to use it without a reader. The suppression of the reader, which is a costly device, causes a reduction in cost. In addition, the use of smart cards becomes easier as they can now be used in terminals that have no readers. This major technological advance facilitates the adoption of smart cards in networks.
A smart card reader needs a specific driver to be recognized and used by the operating system to which it is attached. For a long time, there were no standards. To write an application that used a smart card, the reader was programmed in a proprietary manner. Changing the reader meant re-writing the application so that it could have a dialogue with the new reader. To write such an application, it was necessary to work in narrow collaboration with the manufacturers of smart card readers to have information on the particular functioning of each reader destined to be used by the application. These difficulties have considerably slowed the use of smart cards in data networks.
In the 1990s, the various players on the smart card and micro-processing market met within the “PC/SC19 Workgroup” to standardize a design whose goal was to efficiently integrate the smart card in microcomputers. The PC/SC design was published at the end of 1996. Due to this standard, applications are able to use the PC/SC API without worrying about the type of reader they use.
The PC/SC design was conceived independently of all operating systems. In fact, the only official implementation is integrated in Microsoft systems20. Today, smart card readers are all equipped with their PC/SC system driver.
At the same time, another organization was formed, the OpenCard consortium, to provide a purely Java design destined to use smart cards in a multiplatform environment. In 1997, the OpenCard Framework (OCF) was published. Its use makes it possible to write a Java application (or an applet) that functions in any operating system equipped with a virtual Java machine. The readers’ OCF driver must also be written in Java for portability reasons.
Unfortunately, there are very few smart card readers that are delivered with their OCF drivers. The reader manufacturers prefer providing their product with a single driver, the purely Windows PC/SC driver. Fortunately, there is a gateway between PC/SC and OCF, which makes it possible to write Java programs that use OCF while benefiting from the PC/SC driver provided with the readers.
Since 1998, the MUSCLE project21 has developed a free implementation22 of the PC/SC design for UNIX systems, called PCSC Lite, which is interoperable with the Microsoft version23 with the goal of facilitating the use of existing Windows applications in UNIX systems. Today, PCSC Lite functions in the most current UNIX systems and with OCF programs.
The development of the smart card was done with the goal of maximizing security. It contains specific defense mechanisms.
The electronic chip, which is the basis of all smart cards, is a component that was designed with the single goal of providing strong physical security to the data that it contains. The fact that the memory and the microprocessor are part of a single physical component confers to the smart card an as yet unequalled level of security.
It is in fact quite complex to intercept the exchanges between the microprocessor and the memory if these two entities are physically unified within a single electronic component.
Since their conception in the 1970s, corruption attempts on smart cards have multiplied. The people doing that do not lack in imagination to attempt to get around the security mechanisms.
Attempts in modifying the microprocessor’s behavior are based on altering the card’s power supply or its clock. It can also be cut out to make it possible to directly read the memory cells. Exposure to various rays is another possible form of attack.
Different conception particularities secure the smart card against all types of attack. Memory management is much more complex, such that all direct reading attempts will fail. Captors placed within the chip have the goal of detecting abnormal external behavior, such as suspicious variations in the clock or in the power supply, or even an attempt of extracting the chip. It can react differently according to information uploaded by its sensors, by interrupting all current operations or by self-destruction.
Recently produced smart cards are also protected against passive attacks by monitoring their electric consumption. This in fact reveals information on the chip’s behavior.
Many types of portable devices that are easy to use from one computer to another are sometimes designed as alternative solutions to the smart card. We will show that these solutions do not guarantee the same services as those offered by the microprocessor smart card.
In existence long before smart cards, and having the same physical format in common, although not quite secure, the magnetic card is still used throughout the world as a credit card.
The magnetic card is a tried and tested technology, which has been standardized24 for a long time. Due to its inherent technological simplicity, it can be mass-produced at a low cost. This type of card is based on banking network security.
A magnetic card has no great data storing capacity. It is not possible to record more than a million bits on it.
In addition, the magnetic card has no means of protection against reading or writing on its magnetic stripes, thus making it possible to copy such cards and accidentally altering the data when passing in a magnetic field25.
As a result, there are security problems with regard to confidentiality and authenticity of stored data. In addition, the card only serves as data storing support and has no processing capacity.
With the adoption of standard USB interfaces, new available transmission speeds26 coupled with the possibility of directly providing power supply to the external device have made it possible to develop removable active cryptographic modules.
Equipped with a cryptographic processor and a memory capable of storing a private key, a cryptographic token makes it possible to deploy security solutions based on asymmetric cryptography, of PKI type.
In addition to the fact that there is very little available memory for storing information, the security module is dissociated from the EEPROM. This makes it possible to extract secret information contained in the cryptographic token [KIN 00]. The retrieval of keys is therefore possible and annihilates the system’s security.
With the reduction in price of electronic components in the last few years, and notably of Flash memory, a new kind of mobile data device has appeared.
Flash memory is equipped with a very large information storage density, which explains the existence of USB keys with storage capacities reaching several gigabytes. Based on the standard “USB storage”, these new devices function directly in all recent microcomputer operation systems without requiring a specific intermediary reader.
Even if some models attempt to control access via a password, data is readable in Flash memory. Such a device also does not have any processing capabilities. It serves solely as support for information storage.
Data processing security often calls upon cryptographic algorithms. After recalling the various types of available mathematical tools, we will see how the smart card, due to its advanced cryptographic capabilities, is particularly adapted to reinforcing security in networks.
The different available tools in cryptography rely on two concepts: data encryption and hashing.
The current encryption algorithms follow the Kerckhoff principal [KER 83a, KER 83b]: an encryption algorithm’s security should never rely on the algorithm’s confidentiality but rather on a secret key. The encryption algorithms that have not respected this rule have always ended up broken, like those used in the GSM [GOL 97], DVD [STE 99] or Adobe’s electronic book [SKL 01]. To reinforce the security of an algorithm that follows this principle, it is enough to increase the size of the key used.
Secret key encryption algorithms function as indicated in Figure 16.7. A key makes it possible to encrypt and decrypt the data. The conception of the algorithms is such that it should never be possible to deduce the original data from the encrypted data without having the key. This principle forces the emitter and the receiver to keep the key secret, which can create key distribution problems in a system where many players participate in the data exchange. In fact, key compromise signifies the compromise of the whole system. On the other hand, encryption and decryption operations with secret keys are very fast.
The principal secret key encryption algorithm used is the Data Encryption Standard (DES). It is being replaced by its successor, the Advanced Encryption Standard (AES).
At the same time that the smart card appeared, the concept of asymmetrical cryptography saw the light of day through a new cryptographic principle that implemented two particular keys [DIF 76, MER 78]. As shown in Figure 16.8, encryption and decryption actions are dissociated and each implements a different key. These keys are calculated in such a way that knowing one key does not make it possible to deduce the other key. This new principle implies keeping one of the keys secret and distributing the second. The flexibility of asymmetrical algorithms is counterbalanced by slow encryption and decryption operations, much slower than those of symmetrical cryptography, which limits these algorithms to processing fewer data.
The most frequently used public key encryption algorithm is RSA27.
Hashing algorithms are functions that apply to data of all sizes and that calculate a fixed-size message digest, as shown in Figure 16.9. A hashing function must be made in such a way that it is very difficult to find two messages with the same message digest.
The most widely used hashing algorithms are Message Digest 5 (MD5) and the Secure Hash Algorithm (SHA).
When we communicate with a remote entity, we must be sure that the remote entity is the one we think it is. In our everyday lives we can, for example, authenticate a person by their telephone number or by their address. The guarantee that the messages that I send to a person really get to the person in question lies in my confidence in the phone operator or the postal service to contact the right person. This confidence does not exist in the Internet.
In the digital world, authentication is made possible through the use of cryptographic tools.
The most current method consists of verifying that the remote entity has an authenticating secret in its possession.
Symmetrical cryptographic algorithms offer a solution to this problem, as shown in Figure 16.10.
The wary entity sends a random message to the entity to be authenticated. The latter encrypts the message with its secret key and sends it back. The wary entity only has to decrypt the received message and compare the result with the random message. If they are the same, this proves that the remote entity is in possession of the secret key and the authentication is a success.
Smart cards are well adapted to this scheme. In fact, they are conceived to keep information safe, a key for example, and can contain a cryptographic processor that accelerates private key encryption algorithms such as DES or AES.
However, there is still the problem of secret key distribution when several entities communicate. The compromise of this key means the compromise of the entire system.
Asymmetrical cryptographic algorithms make it possible to address the authentication problem in a manner that is more satisfying than symmetrical algorithms.
As in the case of symmetrical cryptography, the wary entity will send a random message to the entity to be authenticated, which will encrypt it with its private key and send it back. The wary entity will try to decrypt the response with the public key, which is known by the entity to be authenticated.
If the decrypted message corresponds to the initial random message, this proves that the remote entity is in possession of the private key of the entity its claims to be and the authentication is successful. This scheme is more satisfying than the case of symmetrical cryptography, as the implicated entities do not have to share any secrets.
Once again, the smart card is adapted to this situation. In fact, a smart card, along with being appropriate for the secure storage of a key and capable of implementing algorithms such as RSA, makes it possible to generate the keys necessary for asymmetrical cryptographic algorithms.
This considerably reinforces the confidentiality of the secret key that will never leave the card.
To ensure the confidentiality of sensitive data in a risky environment, they must be made unusable to all non-authorized people.
The symmetrical and asymmetrical cryptographic algorithms seen previously fulfill this task, as in Figure 16.11, where we see the process of data delivery.
Current smart cards, equipped with cryptographic processors, are particularly adapted to the confidential transportation of data.
The current processing power of smart cards does not enable the encryption or decryption of large quantities of data in a reasonable time frame.
However, technological advances such as changes in communication interfaces for faster interfaces, new types of memory, as well as faster processors, tend to reduce this processing time.
In [BLA 96], the author proposes a solution to this problem of encryption speed in the current smart cards. It exposes a new protocol, the Remotely Keyed Encryption Protocol (RKEP), which makes it possible for a smart card to symmetrically encrypt a rapid flow of data by using the power of the computer to which it is linked.
The strength of this protocol is that it makes it possible to use a computer in which the smart card has no confidence because there is no transmission of secret information from the chip. The RKEP establishes a low flow information exchange between the smart card and the computer to which it is connected, providing to the computer enough information to be able to encrypt or decrypt the rapid flow of data.
More than ever with the advent of wireless networks, the information exchanged in the networks is susceptible to alterations, whether voluntary attack or involuntary (technical failure). There is therefore a need to verify if the received information really corresponds to the information that was sent. This verification is carried out by means of an electronic signature.
For this, we combine asymmetrical encryption and the principle of hashing, as in Figure 16.12.
The sender calculates the message digest of the data to be sent, then encrypts this message digest with its private key to create a signature that will be sent with the data. The receiver will receive the data with the signature. They will decrypt the signature with the help of the sender’s known public key and will verify if the resulting message digest corresponds to the message digest obtained when it hashes the received data itself. If they are equal, this will prove the integrity of the received data.
Once again, the smart cards contain the cryptographic material necessary for this task.
In cryptography, random numbers play a very important role. It is primordial to have a good random number generator to ensure a proper running of the cryptographic algorithms.
Smart cards contain a material random number generator. They are the ideal complement for all microcomputer that wants to make the most of cryptographic algorithms.
In [ITO 01a], the author proposes reinforcing the security of the contents of a hard drive by encrypting each of the files with a random password. It uses a smart card to carry this out. From a secret in the card and relative to the files to be encrypted or decrypted, the card will generate a different password for each file. The random number generator it contains will ensure the security of these files.
Data networks carry many security problems. We will study different solutions, based on the use of the smart card, that improve network security.
[SCH 99] addresses the problem of authentication of data transmitted over the Internet to personal services, such as the use of licensed software. The author proposes identifying the user by sharing a secret key between a personal smart card and the application.
The software that requires user information sends the information request to the card along with a random number. The card first verifies the identity of its carrier: it asks for a PIN code. Then, the card sends the required information, signed, to the application with the secret key shared.
The application that receives the message recalculates the signature from the sent information and on the known secret key. If the signature, so generated, corresponds to the one sent, the data sent by the user are authenticated.
[MIL 88] defines the Kerberos protocol. This protocol makes it possible to authenticate a user on a remote server through communication encrypted with a secret key. The weakness in this protocol lies in the security of the password storage as well as the choice of user password. The user generally chooses a low security password that does not resist dictionary attacks.
In [BOL 91], the authors warn against the use of the Kerberos protocol without the help of specific material.
One solution to secure Kerberos with the smart card is presented in [ITO 98]. It consists of using a randomly generated password within the card. The password stays in the card and then all cryptographic calculations are carried out in the card on the password that never leaves the card.
In a network environment, to access remote services a user can find himself using a potentially hostile computer. One possibility would be downloading the services into a smart card to execute them in a secure environment. The current limitations of smart cards do not make it possible to implement this principle.
[LOU 02] addresses this problem by installing mathematical bases to secure the execution of mobile code with a smart card.
The execution of a small part of the calculations by the card extends the smart card security to the entire environment.
Wireless networks have profited from the low cost of Wi-Fi technology28 to become widely used. Unfortunately, serious security breaches [BOR 01] were discovered in the WEP29 protocol, the protocol destined to control access and ensure confidentiality in Wi-Fi networks. These failures make it possible to get round the measures implemented by the WEP protocol.
The IEEE 802.1X security architecture makes it possible to remedy this problem. It involves three parties:
– the supplicant;
– the authenticator;
– the authentication server.
The user’s station, the supplication, wants to connect to the network30. The authenticator is the network point of entry31. The authentication server is linked to an AAA32 infrastructure that contains the users’ network profiles and their authentication parameters.
The exchanges necessary for the connection use the EAP33 protocol. They use keys specific to the user’s station.
In [URI 03], the authors propose the use of a smart card that implements the EAP protocol in which the supplicant’s authentication keys are stored. Executing cryptographic operations within a smart card prevents the duplication of authentication keys and consequently excludes illicit connections.
The smart card was conceived with the purpose of reinforcing security. In the world of data networks and notably that of wireless networks where security is an important issue, the smart card is capable of responding to this security need. Although the addition of a smart card to a system renders it more secure, the security of the network protocol that uses it is fundamental.
[BAR 99] BARBER J., “The Smart Card URL Programming Interface”, Gemplus Developper Conference (GDC’99), Paris, France, 1999.
[BIG 98] BIGET P., VANDEWALLE J.-J., “Extended Memory Card”, European Multimedia Microprocessor Systems and Electronic Commerce Conference (EMMSEC), Bordeaux, France, 1998.
[BLA 96] BLAZE M., “High-Bandwidth Encryption with Low-Bandwidth Smart cards”, Springer, Fast Software Encryption, 33–40, 1996.
[BOL 91] BOLLEVIN S. M., MERITT M., “Limitations of the Kerberos Authentication System”, USENIX Winter 1991 Technical Conference, 253–268, Dallas, USA, 1991.
[BOR 01] BORISOV N., GOLDBERG I., WAGNER D., “Intercepting Mobile Communications: The Insecurity of 802.11”, 7th Annual International Conference on Mobile Computing and Networking, Rome, Italy, 2001.
[DIF 76] DIFFIE W. HELLMAN M. E., “New Directions in Cryptography”, in IEEE Transactions on Information Theory, 644–654, 1976.
[GOL 97] GOLIC J. D., “Cryptanalysis of Alleged A5 Stream Cipher”, Advances in Cryptology – EUROCRYPT’97, Konstanz, Germany, 1997.
[GUT 00] GUTHERY S., KEHR R., POSEGGA J., VOGT H., “GSM SIMs as Web Servers”, 7th International Conference on Intelligence in Services and Networks (IS&N’2000), Athens, Greece, 2000.
[ITO 98] ITOI N., HONEYMAN P., ARBOR A., “Smart card Integration with Kerberos V5”, 7 CITI Technical Report 98, 51–62, 1998.
[ITO 99] ITOI N., HONEYMAN P., REES J. ARBOR A., SCFS: A UNIX Filesystem for Smart cards, USENIX Workshop on Smart Card Technology, 107–118, Chicago, USA, 1999.
[ITO 01a] ITOI N., SC-CFS: Smart Card Secured Cryptographic File System, 10th USENIX security Symposium, Washington DC, USA, 271–280, 2001.
[ITO 01b] ITOI N., FUKUZAWA T., HONEYMAN P., Secure Internet Smart Cards, Lecture Notes in Computer Science, 2041, 73–89, 2001.
[JAB 96] JABLON D. P., “Strong password-only authenticated key exchange”, ACM Computer Communications Review, 1996.
[JUR 03] JURGENSEN T. M., GUTHERY S. B., Smart Cards the Developer’s Toolkit, 2–3, Prentice Hall, 2003.
[KER 83a] KERCKHOFF A., “La Cryptographie Militaire”, 5–38, Journal des sciences militaires, 1883.
[KER 83b] KERCKHOFF A., “La Cryptographie Militaire”, 161–191, Journal des sciences militaires, 1883.
[KIN 00] KINGPIN, “Attacks on and Countermeasures for USB Hardware Token Devices”, 5th Nordic Workshop on Secure IT Systems (NordSec 2000), 35–57, Reykjavik, Iceland, Reykjavik University, 2000.
[LOU 01] LOUREIRO S., Mobile Code Protection, PhD Thesis, EURECOM Institute, 2001.
[LOU 02] LOUREIRO S., BUSSARD L., ROUDIER Y., “Extending Tamper-Proof Hardware Security to Untrusted Execution Environments”, 5th Smart Card Research and Advanced Application Conference, San Jose, USA, 2002.
[MER 78] MERKLE R., Secure Communication Over Insecure Channels, Communications of the ACM, 294–299, 1978.
[MIC 01] MICROSYSTEMS S., JavaCard 2.2 Remote Method Invocation Design Draft 1 Revision 1.1, 2001.
[MIL 88] MILLER S., NEUMAN C., SCHILLER J., SALTZER J., “Kerberos Authentication and Authorization System”, Project Athena Technical Plan, Section E.2.1, 1988.
[RAN 00] RANKL W., EFFING W., Smart Card Handbook, 2–5, John Wiley & Sons, 2000.
[REE 00] REES J., HONEYMAN P., “Webcard: a Java Card Web Server”, 4th Working Conference on Smart Card Research and Advanced Applications, CARDIS 2000, Bristol, UK, 197–208, 2000.
[SAN 85] SANDBERG R., GOLDBERG D., KLEIMAN S., WALSH D., LYON B., Design and Implementation of the Sun Network Filesystem, USENIX Conference, 119–130, Portland, USA, 1985.
[SCH 99] SCHOLTEN I., BAKKER J., “Authentication on WWW using smart cards”, Information Technology Shaping European Universities (EUNIS’99), Helsinki, Finland, 1999.
[SKL 01] SKLYAROV D., MALYSHEV A., “eBooks security – theory and practice”, conference DEF CON 9, Las Vegas, USA, 2001.
[STE 99] STEVENSON F. A., Cryptanalysis of Contents Scrambling System, 1999.
[TOW 02] TOWNEND R. C., “Finance: History, Development & Market Overview, Smart Card News”, 2002, http://www.smartcard.co.uk/resources/articles/finance.html.
[UGO 92] UGON M., GUILLOU L., QUISUATER J., “The Smart Card: A standardized security device dedicated to public cryptology”, 1992.
[URI 03] URIEN P., LOUTREL M., “The EAP smart card. A tamper resistant device dedicated to 802.11 wireless networks”, Third Workshop on Applications and Services in Wireless Networks, Berne, Switzerland, 2003.
[VER 00] VERTIGER P., DESPONT P., DRECHSLER U., DÜRIG U., HÄBERLE W., LUTWYCHE M., ROTHUIZEN H., STUTZ R., WIDMER R., BINNIG G., “The Millipede – More than one thousand tips for future AFM data storage”, IBM Journal of Research and Development, 44, 3, 2000.
[YLO 96] YLONEN T., “SSH – Secure login connections over the internet”, 6th USENIX Security Symposium, San Jose, USA, 37–42, 1996.
[ZIM 95] ZIMMERMANN P. R., The Official PGP User’s Guide, 1995.
1 Chapter written by Vincent GUYOT.
1 Self-Programmable One-chip Microcomputer [UGO 92].
2 Hence its English name of smart card or smartcard.
3 The SPOM patent is still used by microprocessor smart card makers.
4 Which appeared in 1981.
5 Hence the name smart card.
6 Standardized in the ISO 7810 standard.
7 The form of this module makes it possible to instantly identify its manufacturer.
8 Universal Serial Bus, which is a standard used to connect external peripheries to microcomputers.
9 To ensure the card carrier’s legitimacy, all exchange generally begins by PIN code verification or a biometric test that can definitely block the card in case of an error.
10 Application Protocol Data Units.
11 Defined by the ISO 7816-4 standard.
12 That always initiates the communication.
13 Each is a byte in size, except the data field that has a variable size.
14 Development platform for standardized GSM 02.19 and GSM 03.19 applications.
15 Short Message System.
16 By the PS/2 port, an electric transformer or batteries.
17 Formerly PCMCIA.
18 Electric powered for peripheries and increased communication speed.
19 Personal Computer/Smart Card.
20 The PC/SC design is included in this system since Windows 2000.
22 In the Open-Source sense.
23 As it uses the same API.
24 ISO 7811-1 to ISO 7811-6.
25 Magnets, CRT monitors, etc.
26 Port speeds: serial 0.1 Mbit/s, parallel 0.8 Mbit/s, USB 12 Mbit/s, USB2 480 Mbit/s.
27 From the name of those who conceived it, Rivest, Shamir and Adleman.
28 IEEE 802.11 standard.
29 Wired Equivalent Privacy.
30 Typically a laptop equipped with a Wi-Fi interface.
31 Typically a Wi-Fi access point.
32 Authentication, Authorization, Accounting.
33 Extensible Authentication Protocol.