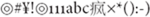 .”65
.”65| ∎ | 2 | ∎ |
THE POLITICS OF DIGITAL CONTENTION
Lawrence Lessig argues that software code is the basis of control in cyberspace and that architectures of Internet control can be built on the basis of code. Code can be open or closed; open code is harder to regulate than closed code. Therefore, whether and how the Internet is regulated depends on its architecture of code. Since architecture is built by people, it is ultimately the government that has the power to decide what architecture to build and how regulatable the Internet remains.1 His prediction that the Internet will become more and more regulated is coming true everywhere, and this is certainly so in China.2
Yet as power seeks domination, it incurs resistance. What are the forms and conditions of resistance in Chinese cyberspace? What forms does online activism assume in the face of a growing Internet-control regime? I will argue that the forms of online activism respond to the forms of control. Control is exercised both through the architecture of code and through the people who build and run the institutions and the technological architectures. Resistance happens at all levels. As technological architectures of control become more sophisticated, so do forms of resistance. As institutions of control become more refined, so do the countervailing forces.
Online activism responds to issue-specific political opportunities in China. First, issues that are more politically tolerable and resonant with the public are more likely to enter the public sphere and become contentious events. Second, while state power shapes online activism, activists respond creatively to state control. They negotiate power and express contention artfully through skillful use of the Internet, as well as legally and rightfully by operating “near the boundary of authorized channels.”3 Political domination shapes the forms of contention but cannot prevent it from happening. Third, power responds and adapts to contention as much as it tries to control it. Society constrains the state as much as the other way round.4 The result is that both power and contention undergo change in their interactions. This aspect of the relationship between Internet control and Internet activism is neglected in current scholarship. Both the forms and practices of state power and online activism have become more sophisticated over time. They adapt to each other in a process of mutual engagement. As activism becomes informational and digital, so does power, which has become more hegemonic in the Gramscian sense. The practices of Internet control mask something more subtle: the power apparatus uses these to adjust, modify, and expand its reach and influence. The coevolution of online activism and Internet control in the past decade presents an almost quasi-experimental case to evaluate the effects of this mutual engagement.
Media, Power, and Protest: Historical Lessons
Classical social theory defined the state as a compulsory political organization with the monopoly of the legitimate use of physical force in the enforcement of its order.5 Contemporary theorists have emphasized the state as an apparatus of information control. In his analysis of the rise of the modern nation-state, Giddens argues that nation-states are power structures with a monopoly over two types of resources, the allocative and the authoritative. Allocative resources refer to material facilities and goods. Authoritative resources refer to those used for the control of human activities, especially information. Thus Giddens argues that all states are information societies, in the sense that the generation of state power involves “the regularized gathering, storage, and control of information applied to administrative ends.”6 What Giddens calls authoritative resources Bourdieu refers to as informational capital.7 Extending the conventional view of the state as an institution of physical violence, Bourdieu argues that the state is also an institution of cultural and symbolic violence. It controls the production, use, and transmission of symbolic forms such as ideas, images, and information more generally.8 He mentions such examples of state-controlled information as census taking, national statistics, accounting, the building of archives, and the homogenizing of forms of communication.
A critical type of information resource is media. Historically, the Chinese state has had a tight control over media, yet people always managed to sabotage control. They either appropriated official media or created their own alternative media as a means of challenging power. The Red Guard press that flourished during the Cultural Revolution was not all conformist. Many “little newspapers,” leaflets, and wall posters contained critical information and even expressed an undercurrent of heterodox thought.9 One Beijing University student told a foreign visitor at that time: “In the wall posters we can now write about things that have been forbidden for twenty years. Do you really want to know what the Cultural Revolution is? It is a feast of criticism.”10
In the days after the Red Guard movement, when young students had been sent to the countryside as “educated youth,” there was a veritable underground culture of hand-copied volumes and “yellow songs” among these people.11 Some of these activities led to imprisonment and other forms of persecution. One person was imprisoned for ten years for writing a sentimental song.12 Yet the activities could not be stopped. The April Fifth movement in 1976 was a movement of poems. People pasted their hand-written poetry on paper wreaths dedicated to Zhou Enlai as a form of protest.13 The Democracy Wall movement occurred through an unofficial press of journals and wall posters. And for a short period in the middle of the student movement in 1989, student protesters won over state-controlled media, which turned from quiescence to full coverage of the unfolding events and thus contributed to the movement’s mobilization.
This historical survey shows that while state authorities seek to control media, people can subvert control by appropriating official media or creating their own small media. There is no reason to believe that this basic dynamic will change in the Internet age. What changes is the forms of power and resistance as they evolve in tandem. I will first review the evolution of state power in the Internet age and then examine the forms of resistance.
Chinese State Power Since 1989
After a period of stagnation following the repression of the student movement in 1989, economic reform in China entered a new stage officially known as the deep reform. Two central goals of the deep reform are to build a complete market economy and to maintain the rule of law. During this period, slow but meaningful political changes have taken place, making Chinese politics “more institutionalized, more predictable, and more performance oriented.”14 For example, these changes include the gradual separation of the political and administrative roles of the party-state and the smooth transition of leadership from the third to the fourth generation. The Chinese polity remains a system of one-party authoritarian rule. The legitimacy of the CCP and the political system is non-negotiable. As economists Yingyi Qian and Jinglian Wu put it, “the principle of Party supremacy” overrules any other considerations: “The Communist Party maximizes economic growth subject to the constraint of keeping itself in power.”15 Similarly, slow political changes are allowed provided they do not threaten the legitimacy and power of the party-state.
The nature of the Chinese political system in this period has been a focus of much analysis. Andrew Nathan characterizes it as resilient authoritarianism with institutionalization as its main feature. He shows evidence of institutionalization in several crucial areas—succession politics, selection of political elites, functional specialization of state bureaucracies, and the establishment of institutions for political participation aimed at strengthening CCP legitimacy. Elizabeth Perry agrees with Nathan about the authoritarian nature of the current regime but contends that this authoritarianism retains many elements of China’s revolutionary heritage and is therefore still “revolutionary.” Like the Maoist regime, for example, the current brand of “revolutionary authoritarianism” has mechanisms both for launching and absorbing popular grievances.16
Whether resilient or revolutionary, the current Chinese authoritarian polity is not devoid of institutions for citizen input. How well these institutions work is another matter. Other scholars have pointed out the serious contradictions in the Chinese polity. O’Brien and Li note its segmented and multilayered features and the divergent and conflictual interests between central authorities and local officials. Ching Kwan Lee underlines the tension between the state’s twin strategy of economic accumulation and political legitimation. The existence of official institutions for public input and the segmentation of the Chinese state together create political opportunities for popular protests. These political conditions partly explain the growing frequency of popular contention since the 1990s.17
As part of the broader landscape of popular contention in China, online activism is open to the same structural opportunities and constraints. It reflects this structural opening. However, political opportunities would have to be disaggregated in order to understand why some issues are more prevalent in online activism than others.
The Evolution of China’s Internet-control Regime
The totality of the institutions and practices of Internet control constitutes an Internet-control regime. Reflecting the fluid and multifaceted nature of the Internet, China’s Internet-control regime is constantly evolving. As online activism challenges the state, the state responds by adjusting and refining its institutions and methods of control.18
Three stages of evolution may be identified. The first stage, from 1994 to 1999, focused on the regulation of network security, Internet service provision, and institutional restructuring. The first major policy framework related to the Internet was set out in the “Regulations Concerning the Safety and Protection of Computer Information Systems.”19 These regulations went into effect on February 18, 1994, two months before China established full-functional Internet connectivity. They outlined the principles and institutions of governance and designated the Ministry of Public Security as the principal agency in charge. The second major policy document was the “Computer Information Network and Internet Security, Protection and Management Regulations,” issued by the Ministry of Public Security in December 1997. This regulation details the responsibilities of China’s Internet service providers (ISPs) and sets out nine types of information to be prohibited online. The nine prohibitions, so to speak, include standard items such as circulating information that violates laws or the constitution. They also include ambiguous types such as the spreading of rumors and “information that damages the credibility of state organs.”20 In terms of institutional restructuring, the major event in this stage was the merging in 1998 of the Ministry of Post and Telecommunications and the Ministry of Electronics Industry into the new Ministry of Information Industry (MII). Under this new scheme, MII is the primary regulatory agency of the information industry.21
The second stage, from 2000 to 2002, was characterized by the expansion and refinement of Internet control. The main development was the strengthening of content regulations targeting both Internet content providers (ICPs) and individual consumers. For example, in October 2000, MII announced regulations specifically targeting BBSs, stipulating that they must follow a licensing procedure. On November 7, 2000, the State Council issued regulations about the provision of news services online. These regulations permit official news media organizations to carry news in their Web sites but allow officially licensed commercial Web sites only to report news from official news channels.22 As I will discuss below, content control involves, among other things, the filtering and blocking of keywords using technological means. This is control through code. Thus BBS posts containing such phrases as “June Fourth” or “Falun Gong” may be automatically blocked. Technologies also allow state authorities to track down the authors of the posts. This marks an expansion in the forms and practices of power. In his discussion of censorship in arts and literature, Richard Kraus suggests that censorship targets the form of expression rather than content. “The Party often specifies the terms in which issues may be publicly discussed…. Rather than tell you what you are forbidden to say, the Party establishes standards for how you say what you say.”23 Internet filtering marks a move to restrict both form and content. The CCP now regularly distributes lists of forbidden terms to Web site owners for censoring. That this is possible at all is due largely to the capabilities of the new technologies. The same technology that allows Internet users to speak out allows the state to censor speech. Yet again, this is as much about technology as it is about people. Power exerts itself through codes, but the codes are designed and implemented by people. The procedure of compiling and handing out the “blacklist” of words is itself a mechanism of controlling Web businesses.
The third phase, from 2003 to the present, marks the expansion of Internet regulation and control from government to governance and governmentality. The dividing line was the transition of leadership from Jiang Zemin to Hu Jintao at the end of 2002 and beginning of 2003. If “government” consists of the formal institutions, rules, and practices of the state, then “governance” refers to the formal and informal institutions, rules, and practices of both the state and nonstate actors; “governmentality” denotes “the cultural and social context out of which modes of governance arise and by which they are sustained.”24 The guidelines for strengthening Internet control in this stage were set out in an unprecedented party decision, reached at the Fourth Plenum of the Sixteenth Congress of the Chinese Communist Party in September 2004, to strengthen its “ability to govern.” The decision set out new principles for Internet control in the following terms:
Attach great importance to the influence of the Internet and other new media on public opinion, step up the establishment of a management institution that integrates legal binding, administrative monitoring and management, occupational self-discipline, and technical guarantees, strengthen the building of an Internet propaganda team, and forge the influence of positive opinion on the Internet.25
This framework thus encompasses (1) institution building, (2) legal instruments, (3) ethical self-discipline, (4) technical instruments, and (5) proactive discursive production. It is a comprehensive new framework of governance that applies not only to the Internet but to the regulation of Chinese society as a whole.
With respect to Internet control, the framework is implemented through a number of new initiatives. First, the Chinese government continued to strengthen the regulation of the growing numbers of ICPs (which had reached over 600,000 by 2003).26 For example, in May 2003, the Ministry of Culture issued a twenty-seven-article provisional regulation concerning the management of cultural products created or circulated through the Internet, such as audiovisual products and games. On September 25, 2005, a new regulation about news services was issued to replace the “provisional regulation” issued on November 7, 2000. The new regulation added two additional categories of illegal information, bringing the total number of types of prohibitions from nine to eleven. The two additions are “information inciting illegal assemblies, association, demonstrations, protests, and gatherings that disturb social order” and “information concerning activities of illegal civic associations.”27 Apparently, these new additions are intended to control the use of the Internet for civil organization and mobilization, an important part of online activism.
Second, official campaigns were launched to promote corporate social responsibility, professional codes of conduct, and self-discipline regarding the ethical use of the Internet. In April 2004, the inaugural issue of the state-run magazine Wangluo chuanbo [New media] carried a cover story advocating the social responsibility of Internet media. On June 10, 2004, the China Internet Society, a government-organized NGO (GONGO), launched a Web site (net.china.cn) where citizens can report on “illegal and immoral information.” This is an attempt by the state authorities to mobilize the general public to monitor information online.28
Third, the emphasis on the forging of positive public opinion on the Internet is also reflected in some new policy initiatives. On the one hand, there are efforts to expand the influence of local news organizations. They are permitted to carry their own news, reprint news from other organizations, and provide information services using BBSs and text messaging. This marks a new step in the state’s efforts to incorporate the Internet into the regulative framework of mass media. Treating the Internet as new media, or the mediaization of the Internet, allows the state to extend its framework of mass-media control to the Internet. In this context, the concept of new media takes on different connotations than it does in other countries. From the point of view of the state, the emphasis is less on the newness and more on the “media-ness” of the Internet, because if it is media, the implication is that its management should follow China’s strict media policies.
On the other hand, a new mechanism of “Internet commentators” (wangluo pinglun yuan) was introduced in 2004 to guide and influence the production of online public opinion. Hired as volunteers or paid staff, these Internet commentators directly intervene in online discussions by writing responses to posts and joining the debates. Their mission, however, is not to promote critical debate but rather to covertly guide the direction of the debates in accordance with the principles laid down by the propaganda departments of the party.29 The guidance is covert, because Internet commentators do not sign into online forums as such. Rather, they sign in with anonymous user IDs, like any other Internet user. Because of the deceptive role these Internet commentators play, they have already earned themselves a bad name. The story goes that government authorities pay an Internet commentator 50 cents (in RMB) for each message he or she posts in an online forum. Internet commentators have thus come to be known derogatively as the “fifty-cent party” (wu mao dang).
Censoring and Policing Contention
The Internet regulation regime is designed to govern the Internet. Governance encompasses both institution building and implementation and enforcement. Enforcement boils down to controlling the eleven forbidden categories of information discussed above. Mechanisms of control are established at different levels and in different sectors. For example, the Ministry of Public Security, charged with the responsibility of safeguarding network security, is a bureaucracy reaching all the way down to township levels. The Ministry of Culture has a similar bureaucratic structure, but it is charged to manage the culture industry related to the Internet, especially Internet bars.
Because the eleven types of forbidden information are most likely to appear in the interactive functions of the Internet, these interactive functions are the main site of control. Policing of these sites directly affects user behavior, including contentious behavior. The case of BBS forums, undoubtedly the most popular of the interactive functions in Chinese cyberspace, illustrates how control mechanisms are at work.
The Ministry of Information Industry issued a regulation for managing Internet bulletin-board services on October 8, 2000. It defines electronic bulletin-board services as those services that provide electronic bulletin boards, electronic blank boards, electronic forums, Internet chat rooms, message boards, and other interactive formats for Internet clients to publicize information. Specific articles concern both ISPs and Internet users. ISPs are required to have managerial and technical personnel for managing bulletin boards. Web sites with bulletin-board services must display their permit numbers and keep records of published contents and customers’ registration information for sixty days.
Internet companies use both technical means and human labor to monitor contents in online forums.30 The main technical method is the use of software for filtering keywords. This means that companies that develop such software technologies may also be indirectly contributing to control.31 Lists of keywords for filtering are created by the News Office of the State Council and handed out to Internet companies on a regular basis.32 Major Internet companies that run online forums hire full-time editors to manage contents. Although their main job is to promote forum activity, content editors are also responsible for monitoring illicit information. In addition, online forums depend on volunteer moderators, known as banzhu (forum hosts), for management. These moderators are usually selected from the more active members of the forum users. In some cases, they are elected by users. Those who fail to fulfill their responsibilities to the satisfaction of forum members may be subject to “impeachment.” Because their chief responsibility and interest are to promote rather than control the forum, the more forum hosts can help to increase the posts and hits in the forum, the more popular they are. This sometimes conflicts with their other task of monitoring and censoring contents.
Public-security authorities intervene when violations are detected. Initial intervention consists of investigations of the contents and sources of problematic posts. Depending on the severity of violations, they may take different approaches. One is to alert Web site owners and request them to step up the monitoring of their forums. For example, in December 2004, public-security officers visited an NGO in Beijing to investigate several posts that had appeared on the organization’s Internet forums. The management of the organization was unaware of these posts. After all, dozens of them were posted daily in its online forums by anonymous users. Discussions in these forums usually did not touch on politically sensitive issues, yet somehow, several messages related to Falun Gong had popped up and been detected by the public-security authorities. Upon investigation, the public-security officers found that the organization was not directly responsible for the posts, but they did request its management to monitor its online forums more closely to prevent such posts from appearing again.33
Sometimes, Web owners temporarily shut down a forum to prevent it from becoming a site of protest. For example, on January 1, 2007, teachers in Guangzhou’s Huadu district went on strike to demand salary raises. A popular BBS for teachers immediately carried stories of the demonstrations. The demonstrators drew the support of the users of the forum. The next day, however, the forum published the following message: “Because the teachers’ demonstrations in Huadu district of Guangzhou city have significant influences, the discussions in our forum have seriously strayed away from the original intentions of this forum. This forum has decided to temporarily shut down the function to publish new posts.”34
When authorities consider the violations serious, they may close the Web sites permanently and arrest and prosecute individual violators. Two of the most influential university-based BBSs, Yitahutu and SMTH, were closed in 2004 and 2005 respectively. Yitahutu was associated with Beijing University; SMTH was run at Tsinghua University. They were not just popular with college students; about half of their users were from outside of the university communities. Some were alumni living overseas. Yannan Web was closed in 2005; Century China was shut down in 2006. These were influential intellectual Web sites. An Amnesty International report in 2004 lists the names of fifty-four people who were detained or imprisoned for using the Internet to disseminate information considered subversive.35 The activities included planning to set up an independent political party, calling for the rehabilitation of the 1989 prodemocracy movement, and opposing the persecution of Falun Gong members. The harsh punishments given to these activists suggest that issues about Falun Gong, the prodemocracy movement in 1989, and independent-party formation are hard to insert into Chinese cyberspace. It is not that they do not exist, but they are forced into surreptitious and guerilla-style existence. Under the new conditions of domination, resistance has taken on new forms.
Contradictions and Countercurrents
The building of institutions and architectures of control does not go unchallenged, and the challenges come from several directions. The first challenge comes from the contradictions within the institutions of control. The second comes from larger societal forces, specifically the growing public demands for information rights. The third challenge is the hidden transcripts of the information age—the ways in which citizens creatively use the Internet to bypass, evade, challenge, and resist control. I will briefly discuss the first two challenges in this section and then examine in more detail the digital “hidden transcripts” in the remainder of this chapter.
Yongnian Zheng distinguishes between an Internet regulatory regime and an Internet-control regime to highlight the contradictions between what he terms the “unenviable dual tasks” of promoting the information economy and controlling the political risks associated with the technology.36 Zheng also appropriately draws attention to the internal divisions and conflicts of interest among different state bureaucracies. The Ministry of Information Industry has different priorities than does the Ministry of Public Security, and these different priorities may cause tensions and conflicts. The contradictions have existed from the beginning. As in the United States, the development of the Internet in China depended on state support in policy and funding. Today, in view of the challenges posed by the Internet to authoritarian control, the Chinese government’s initial decision to link up the country to the Internet may appear puzzling to outside observers. The truth is that Chinese leaders initially saw the Internet primarily as a new economic sector, not as an arena of political contention. In the early and mid-1990s, the Chinese mass media was full of talk about the information superhighway. A new ideology was beginning to emerge, one that held that informatization was the key to modernization. A common talking point in this media discourse runs something like this: In the past, China lagged behind the West by one century; in the history of the Internet, China is only ten years behind. If we do not seize the opportunity to build our information superhighway, China will never catch up with Western developed powers.
Thus, to the extent that they were aware of its informational value, Chinese leaders saw the Internet as another tool for transmitting party policies to the citizens rather than as a tool of everyday communication. As Mueller and Tan argue, Chinese leaders “believe … that IT can give them both modernization and enhanced powers of central control and stability. Indeed, from the point of view of the Communist Party, China’s situation requires it to retain a significant degree of control over the flow of ideas and information.”37
Over the years, though state authorities have come to see more of the subversive aspect of the Internet, their enthusiasm for its economic benefits has not diminished. On June 3 and 4, 2007, the Chinese government convened a national conference on the construction and management of a Chinese-style Internet culture. According to the cover story in the July 2007 issue of the magazine Wangluo chuanbo [New media], a main theme of the conference was to promote a Chinese Internet culture that combines prosperity and control. The conference thus affirmed the importance of both a thriving and a controlled Internet. The magazine features an interview with a vice minister of culture, who elaborates on the idea of the coexistence of the apparently contradictory goals of prosperity and control. However, when I asked one of the editors what policy instruments would solve this contradiction, the answer was: “Nobody knows.”38
Besides these contradictions, there are countercurrents that undermine the regime of Internet control. These include all the factors I will analyze in the following chapters—business, culture, civil society, and globalization. What needs to be stressed here is the rising public demand for government transparency and accountability and for citizens’ rights to know. One important development in this regard is the promulgation of a national information-disclosure act in April 2007. Although information-disclosure acts have existed at the municipal level, this was the first of its kind at the level of the central government. Its formulation reflects popular demands for citizens’ rights to know, to which online activism itself has added forceful voices.39
In recent years, the conditions of risk society in China—natural disasters, emergencies, environmental risks, industrial accidents—have become evident with the SARS crisis in 2003, the Songhua River toxic pollution in 2005, and the snowstorms and earthquakes in 2008. These disasters have strengthened the awareness, both among government leaders and ordinary citizens, that risks are becoming a part of life and that managing risks requires more effective, accountable, and transparent institutions. In such a risk society, information disclosure and citizen participation become essential for effective and rapid state response. Thus the push for more Internet control is pulled by this countercurrent of popular struggles for transparency, accountability, and the right to know. These contradictions and countercurrents set the context for citizen struggles to negotiate state control of the Internet through everyday forms of resistance.
Issue Opportunity and Issue Resonance
The issues of online activism reflect such political negotiations. Scholars of social movements have argued that political structures may be more open to some issues of contention than others, depending on the relevance of the issues and the broader social context.40 This is also true in China. In Chinese politics, there are multiple issues with a clear hierarchy, and the state is more tolerant of some issues than others. Thus popular contention faces issue-specific opportunities. As argued above, issues that directly challenge the legitimacy of the party-state are minimally tolerated. Conversely, issues that do not challenge state legitimacy may be tolerated. Issues related to Falun Gong, the June Fourth movement, and independent-party formation rarely enter public discussion in Chinese cyberspace; they are strictly censored. Given the practices of political control, those issues that do enter the public sphere are likely to have some degree of political tolerability. The main issues in my sample of online activism fall into the following seven categories: (1) popular nationalism, (2) rights defense, (3) corruption and power abuse, (4) environment, (5) cultural contention, (6) muckraking, and (7) online charity. Of these, rights-defense activism may further be divided into issues concerning (1) vulnerable persons, (2) homeowners, (3) forced relocation, (4) hepatitis-B carriers and diabetes patients, (5) consumer rights (defined broadly), (6) human rights, and (7) other issues of urban middle-class concern. These are by no means exhaustive, but they cover the range of cases in my sample.
Most of these seven broad issue areas have some degree of political legitimacy. The one area that directly challenges the central state is human rights, and human-rights activists are the type of online activist most likely to meet with repression. In the other issue areas, the targets of contention are foreign nations (for example, Japan, in the case of nationalistic protests), real-estate developers, software companies, polluters, corrupt officials, and icons of popular culture. A major target is illegal and unethical business practices that central government authorities are incapable of containing. The demands expressed in these activities, such as environmental protection, the protection of consumer rights, and the containment of corruption, coincide with state agendas. Consumer-rights defense, for example, enjoys strong state support. Government authorities are just as concerned as citizens about the violations of consumer rights. As Beverley Hooper argues, “in the area of consumerism, people are asserting rights not vis a vis the state … but vis a vis the market, with the endorsement and encouragement of the state.”41 Defending the rights of disadvantaged groups and vulnerable persons has always had some degree of legitimacy in Chinese political culture because of their “moral economy” basis. As Elizabeth Perry puts it, the state “has demonstrated a certain degree of tolerance and even sympathy” toward such protests.42 Both types of rights defense may be traced back to the 1980s, but they gained impetus with the institution of China’s Consumer Protection Law in 1993.
Popular nationalism is a more complicated issue. Fourteen cases in my sample concern nationalistic protests online. Seven of them target Japan. One case was about Indonesia. The rest concern the United States, Taiwan, France, and Western media (in the anti-CNN campaign in 2008). To the extent that neonationalism helps to fill the ideological vacuum in China, the state supports its expression.43 In most cases, there was clear evidence of state support or acquiescence, prompting one author to argue that nationalistic protests are expressions of loyalty rather than dissent.44 But the history of popular contention shows that activists could appropriate officially supported campaigns to stake their own claims. And as online protests against Japan indicate, online nationalistic protests may open up new spaces for citizens to exert their discursive rights.45 Thus state actors are careful not to give free rein to popular nationalism.
Besides political tolerability, the main issues of online activism have public resonance. Numerous issues are brought into Chinese cyberspace and discussed daily. Yet only some of them provoke public contention. Most are flooded by the oceans of online posts and never get a chance to be read. One reason is that they lack resonance. A college student who posts messages to protest the lack of air conditioning in her classrooms may gain some classmates’ support, but the issue has little chance of going beyond the campus. Generally speaking, issues that are more relevant to the everyday experiences of the larger population, that appeal to the moral sense of right or wrong, and that have a more concrete attribution of blame have higher degrees of resonance.46
All seven areas of online activism have high degrees of public resonance. Indeed, they represent some of the most burning social, political, and cultural issues in China today. Each resonates with a large segment of the populace. This is certainly true of nationalism, environmental protection, anticorruption, and consumer rights. Even the hepatitis-B carriers’ antidiscrimination campaign is broadly based, because there are over 120 million hepatitis-B carriers in China.47 Similarly, the gaming communities, who fight for gamers’ consumer rights, have as many as thirty-one million players in 2006.48 Even when a relatively small proportion of these social groups begin to organize, they make up awesome numbers. The main issues of online activism therefore touch the everyday experiences of large numbers of people.
Rightful Resistance and Artful Contention
Even with political tolerance and public resonance, some issues may still be filtered. Like rightful resisters in rural China, online activists resort to lawful protests in order to avoid repression and to widen the channels of communication. Like rightful resisters, they operate “near the boundary of authorized channels.”49 In spontaneous protests, this sometimes translates into calls for reasoned protests rather than radical extremism. For example, at the beginning of the protest in May 2000 surrounding the murder of Beijing University student Qiu Qingfeng, in anticipation of possible control action by the university, posts appeared in Beijing University’s BBS forums that asserted the constitutional right of freedom of speech and warned the authorities against shutting down the BBS.50 Users also encouraged the BBS management to be permissive. One post in the “Triangle” forum addressed the BBS moderator in the following words: “Don’t be afraid. Let us vent our feelings and sadness as much as we want and express our grief for the dead. If we surrender [our right of expression] because of possible pressure, what else is left for us? —jinni, May 23, 2000.” Knowing that explicitly hostile language could backfire, some users warned that the protest should proceed in a forceful but rational manner. For example, one message reads: “Please make good use of the BBS. At present, the BBS management has made positive responses to our sentiments. In case the management comes under pressure [of the university authorities], please show your understanding. —fina, May 23, 2000.”51
During the anti-Japanese protests in 2005, the leading Web site organizing the campaign issued an announcement on April 11 urging that “organizers and participants must restrain their behavior in accordance with law and prevent the happening of radical behavior.”52 In other cases, activists rely less on spontaneous protests in BBS forums and more on nondisruptive and persuasive forms of action such as mobilizing campaigns through the mass media and litigation. For example, after winning the first case of litigation in 2003, activists in the hepatitis-B carriers’ antidiscrimination movement filed more than thirty court cases by 2007.53 These typically involved initial mobilization and organizing in their online communities (which had 300,000 registered users). It was partly because of their effective online organizing that their central Web site was abruptly closed down by the Beijing Communications Administration in November 2007.
Besides rightful resistance, people are engaged in all forms of artful contention. They invent ways of overcoming and resisting control and expressing dissent. First, artful contention entails artistic approaches to contention, such as using the new digital technologies to create products for contention. Indeed, one reason why people take part in contentious activities, especially in cultural contention, is the desire to pursue and display their creativity. Many creative Flash videos were produced and circulated online during the SARS and avian-flu crises. There are also many Flash videos on nationalistic and environmental themes. These videos are ways of expressing both artistic creativity and political viewpoints.54 Hacktivism is the pursuit of creativity through transgressive acts. In hacker culture, the ability to hack into sophisticated Web sites is a badge of honor and prestige.55
Second, artful contention requires skills to navigate the controlled structures of the Chinese Internet. Chinese Internet networks are unevenly controlled, with government and other official Web sites more tightly controlled than commercial and private ones. In addition, Web sites are not equally popular. Some online communities are small; others have hundreds of thousands of registered users. It is more likely for contention to spread in popular and nonofficial Web sites. This pattern was clear in the protests surrounding the death of Qiu Qingfeng in 2000. In that protest, the message that broke the news about the murder and triggered the protest appeared in a BBS forum at Beijing University. Within hours, it was crossposted to several popular commercial Web sites and university BBS forums. Yet no protest posts appeared in the official Strengthening the Nation forum (SNF) until the following day. SNF evidently censored posts related to the murder case,56 which probably explains why the first message about the murder case only appeared there almost forty hours after the news broke on Beijing University’s BBS. If contentious messages about the incident eventually did begin to appear on SNF, it indicated that it was no longer possible to censor them, because they were appearing on all the other large online communities.
The Shanxi kiln case is also revealing in this respect. The woman who brought the case to public attention through her online posting carefully thought through her strategies. She did not post from home or from her work unit but used a friend’s computer instead. Initially, she tried to post the information on the Xinhua Net, which is run by the official Xinhua News Agency. At the Xinhua forum, she tried a common method of evading censorship, which was to publish her letter in the form of a response to another post rather than as an independent post starting a new thread. Still, her post was blocked. Eventually, she succeeded in posting it in a BBS forum on the Great River Net using the same method.57 The Great River Net was the official news Web hub of the province of Henan and less tightly controlled than Xinhua Net.
The discursive features in cyberspace mean that much online activism takes the form of verbal persuasion. Besides language and rhetoric, activists make creative use of images and sounds for emotional effect.58 The creative use of symbolic resources in transnational advocacy networks has been called “symbolic politics.”59 Such symbolic politics is also an essential element in Chinese online activism. Few cases happen without the marshalling of symbols. Narratives produced during protests stress the innocence of the victims and the injustices they suffer. In contrast, the perpetrators are often described as heinous and ruthless. These narratives present the archetypal contrast between good and evil. For example, one of the most widely circulated posts in the protests surrounding the death of Qiu Qingfeng was a poem describing the victim’s youthful beauty and innocence. Titled “Maple Flying: For the Soul of the Dead,” it laments the passing away of a beautiful young life and begins with the following lines:
On an ordinary day of the week,
Like any other day crammed with classes
Having confidently finished an exam, with no shuttle bus to take
A girl student walked alone in the afternoon, until
She reached the end of some unknown night.60
Narratives about Sun Zhigang’s death in 2003 similarly contrasted his youthful innocence and intelligence with the brutality of the police. Disseminating graphic images of the victims is an important feature of symbolic politics. The Internet is ideal for this purpose. Like narratives, these images highlight the victims’ innocence and beauty and the injustices inflicted on them. In the campaign to stop dam building on the Nu River, a group of environmentalists traveled from Beijing to the distant Nu River valley on an investigative field trip. Then they organized a photo exhibit in Beijing to showcase the primordial beauty of the river in order to mobilize public opposition. Selected items of the exhibit were published on the campaign Web site. The welcome page of the Web site shows two innocent little girls bathing in the river. The image highlights the young girls’ vulnerability, beauty, and innocence, as if to exhort the viewer to help stop the dam-building project that will destroy the river and thereby the beauty of young lives. In the Shanxi kiln case, the person who posted the open letter crying out for help to save the children accompanied the letter with photographs showing the horrific conditions in the kilns.
Digital Hidden Transcripts
Besides rightful and artful contention, another digital form may be identified. I will call this the “hidden transcripts of the information age,” or digital hidden transcripts. James Scott considers “hidden transcripts” as “a critique of power spoken behind the back of the dominant.”61 He notes that “it does not contain only speech acts but a whole range of practices…. For many peasants, activities such as poaching, pilfering, clandestine tax evasion, and intentionally shabby work for landlords are part and parcel of the hidden transcript.”62
Digital hidden transcripts are ways of resisting power through digital forms. Four forms may be identified. The first involves technical means, which basically entails using code to break code. Examples are proxy servers, antiblocking software, and, for more savvy computer users, rewriting computer programs to disarm their filtering functions. Technical and computer-discussion forums in Chinese cyberspace are full of practical advice and comments about how to evade firewalls.
The second form of digital hidden transcripts resembles an online guerilla war. If a Web site is shut down, people open another, now that the technology makes this easy. The owner of an anticorruption Web site who exposed a corrupt mayor in Shandong province in 2004 constantly faced the shutdown of his Web site. He was eventually forced to host his Web site on an overseas server. He also created numerous blogs, writing, “I created about 80 blogs. For some time, there were people who tried to block and close my blogs. More than thirty of them were ‘killed’ one after another. But I still have about fifty of them running. They have realized that there is no use trying to close my blogs. They are no longer so aggressively at it now.”63
The third form of digital hidden transcript is linguistic. Internet filters block preassigned values such as characters for Falun Gong, but language users are infinitely more creative than computer programs. Through practice, Chinese Internet users have developed an entire repertoire of symbolic devices to beat filters. For example, in May 2000, in the online protest surrounding the murder of a Beijing University student, SNF users found that posts containing the characters for Beida (Beijing University) were blocked. They beat the filters by inserting punctuation and other symbols between the two Chinese characters for Beida, posting messages with phrases like Bei.Da and Bei2Da. The use of these small creative devices has attracted journalists’ attention. A news story in the Chinese-language newspaper Asia Weekly describes such linguistic creativity: “In dealing with the filtering of sensitive words, netizens have come up with many ways of beating filters through test and trial. These include character separation, homophony, word separation, Romanization, and using images and pictures. Because one single method may not be effective, several methods are often used in combination to cheat the computer system.”64 Such linguistic creativity has become so common that one individual posted a message arguing that filtering will be doomed to failure and that the worst-case scenario, barring the complete shutdown of the Internet, would be the appearance of an entirely new “Martian” language with signs like “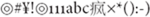 .”65
.”65
The fourth digital hidden transcript is a form of organizational creativity. Online activism takes different forms, such as online petitions, verbal protests, and hosting rights-defense Web sites. Most forms are public. But activists have also invented more hidden forms. One effective but little known tactic is secret online meetings. Internet dissident Liu Di, known by her Internet ID Stainless Steel Mouse, was taken into police custody in 2002. After her release on December 25, 2003, she wrote a long story about her experience of online political participation. She made special mention of the secret meetings she had with others in an online forum: “We opened a secret forum in Xici and gave it an inconspicuous name, ‘Good friends come and play.’ Because the forum serial number is 71138, we also called it Forum 71138. Our purpose was to discuss what we could do for the progress of China. We decided to meet at 8pm every Friday in the chatroom of the secret forum.”66
Because formal organizations are vulnerable to repression, she believed in the power of the Internet more than in formal organizations. When some members of her meeting group wanted to start offline organizations, she demurred:
Some friends thought that online communities are too virtual and too loose. They hoped to have a tighter organization … I opposed the idea in the past. I still believe I am correct. From the point of view of economics, all forms of organization, including government, businesses, and NGOs, exist to reduce transaction costs and speed up economic and social development. A necessary condition for cost reduction is information exchange. This is the function of newspapers, radio, television, the Internet, and other media. Can organization really be more effective than media and the Internet in information exchange and cost reduction? Not necessarily. My own case proves it: Only yesterday, January 15, 2004, did the police station in my neighborhood learn from me that I had been released on bail. In contrast, last year on December 25, the same day when I was released on bail, I was already receiving media interviews.67
Digital hidden transcripts thus reflect both political conditions and human creativity under such conditions. They are used both for direct expression of dissent and for organization.
Conclusion
This chapter argues that over the past decade, an Internet-control regime that combines legal, administrative, and technological means to limit online free speech has formed in China. An architecture of control built on code was born alongside a new architecture of political institutions. This control regime, however, is torn by the internal contradictions between the priorities of economic development and ideological control. In addition, popular demands for government transparency, accountability, and citizens’ rights to know act as countercurrents against control. Finally, Chinese Internet users and activists are skilled social actors. They have developed creative ways of negotiating and fighting Internet control.
This analysis indicates neither the triumph of total control nor of resistance. Perhaps the most important outcome so far is that information and communication technologies have become central means, stakes, and arenas of political struggle. Writing in 1997, Manuel Castells observes, regarding the role of new technologies in Western nations, that “electronic media have become the privileged space of politics.”68 The same could be said of China at the beginning of the new millennium. The encounters between control and resistance have given rise to an informational politics in China. The main features of this new informational politics include, first, the formation of a regulatory regime consisting of government agencies, administrative and technical personnel, rules and laws, and a cyber police force. This regime combines traditional forms of repression with newer, more subtle methods of control and governmentality. It relies increasingly on technological means of control and surveillance. At the same time, however, aware of the complexity and scope of control, the regime takes a selective approach to the exercise of control. Hence the selective targeting of cyberdissidents, blocking of foreign Web sites, and closing of domestic sites. Hence also the different priorities put on different issues, some of which are controlled more closely than others, or more closely at some times than at others.
For citizens, the new politics means a new field of struggle. In recent years, there have appeared in Chinese public discourse more and more demands for information access, information disclosure, rights to know, and communication rights. This new discourse is tied to citizens’ use of new information and communication technologies. It reflects citizens’ frustrations in using these new information tools as well as an understanding of their importance. Despite continuities, these citizen struggles against Internet control have a different character than earlier struggles. The new struggles are diffuse, fluid, guerilla-like, both organized and unorganized, and networked both internally and externally, online with offline. Students of Chinese politics have long recognized the cellular feature of resistance in modern Chinese history, where activities of resistance and protest tend to be isolated. This cellular feature remains today,69 but my analysis of Internet protests reveals new possibilities of alliance, networking, and connection. Pockets of resistance are turning into activist networks.