Introduction
Howdy, my name is Marcus, and I’m a hacker. You probably picked up this book to learn from the best in red teams. I’m going to start off with one of my favorite sayings: “We have two ears and one mouth so that we can listen twice as much as we speak.” This quote is attributed to the Greek Stoic philosopher Epictetus. Trying to live out that wisdom is something I may never master.
When I was young, I was a know-it-all. I’d argue just to be right even when confronted with facts that definitively showed I was wrong. I was that kid in class who would raise my hand at every question, practically jumping out of the seat when a question was asked.
At some point, my parents bought an encyclopedia set, which I read from cover to cover. I read dictionaries to learn new words. I wanted to be like Einstein and Martin Luther King, Jr., rolled up into one. This behavior of wanting to know everything and believing I was the smartest person on Earth was crushed when I joined the military.
I was pretty smart and an excellent test taker, so I got into the U.S. Navy’s cryptologic program. After I left basic training and arrived at my technical training command, I noticed it was swamped with nothing but really smart people.
When I arrived in Scotland for my first duty station, it was more of the same. I worked with senior noncommissioned officers and civilians who absolutely blew my mind. The old me was still there, but I eventually put my pride away and started asking more questions. I started taking the saying “There is no such thing as a dumb question” seriously.
From then on, I asked the most questions. Asking questions, and more importantly, listening to what others had to say, changed my life and learning. I still read everything I could get my hands on and kept close to the people who knew their stuff.
All my question-asking led me to a successful career in cybersecurity. My question-asking and listening was great when dealing with prospects and customers on the sales side of things. When people ask me how I got here, I tell them, “I ask more questions than anyone else.”
Last year, when I started working on the original Tribe of Hackers, we asked more than 70 individuals in cybersecurity questions about how they started and found success. In this book, I’ve brought along a merry bunch of hacker friends who specialize in offensive security (aka red teaming).
Before we get started, let me quickly lay out what a red team is. A red team is a cybersecurity function that tests networks, applications, and systems to find vulnerabilities that may lead to compromise. Sometimes, red teams are allowed to exploit systems to validate that the vulnerability is real. Red teams also can perform physical assessments and social engineering engagements.
On the opposite side of the house, a blue team is responsible for monitoring networks, systems, and applications for intrusions and for making sure that the confidentiality, integrity, and availability of all assets are not affected. Nowadays, organizations are combining red and blue teams and sometimes use the term purple team.
To formulate questions, I reached out the cybersecurity community on Twitter to hear what they wanted to know about the most.

Originally, I planned on using five questions from the book, but on second thought, I decided to take more than five questions from the community. The following are the questions inspired by the response from the community, plus a few more from me.
- How did you get your start on a red team?

- What is the best way to get a red team job?
- How can someone gain red team skills without getting in trouble with the law?
- Why can’t we agree on what a red team is?
- What is one thing the rest of information security doesn’t understand about being on a red team? What is the most toxic falsehood you have heard related to red, blue, or purple teams?

- When should you introduce a formal red team into an organization’s security program?
- How do you explain the value of red teaming to a reluctant or nontechnical client or organization?
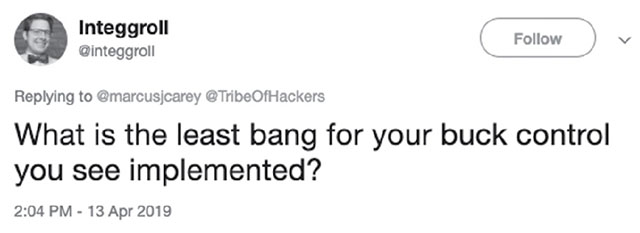
- What is the least bang-for-your-buck security control that you see implemented?
- Have you ever recommended not doing a red team engagement?

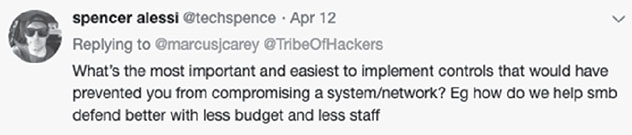
- What’s the most important or easiest-to-implement control that can prevent you from compromising a system or network?
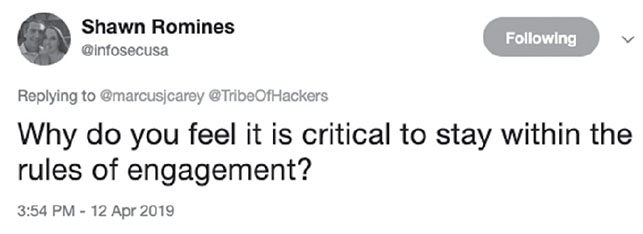
- Why do you feel it is critical to stay within the rules of engagement?
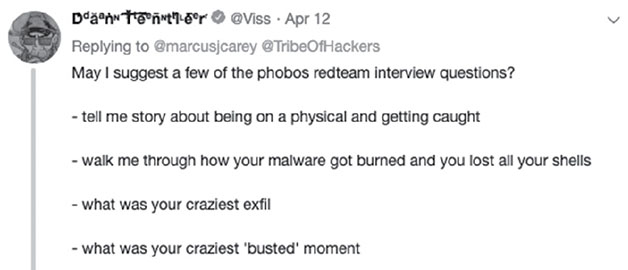
- If you were ever busted on a penetration test or other engagement, how did you handle it?
- What is the biggest ethical quandary you experienced while on an assigned objective?
- How does the red team work together to get the job done?
- What is your approach to debriefing and supporting blue teams after an operation is completed?
- If you were to switch to the blue team, what would be your first step to better defend against attacks?
- What is some practical advice on writing a good report?
- How do you ensure your program results are valuable to people who need a full narrative and context?
- How do you recommend security improvements other than pointing out where it’s insufficient?

- What nontechnical skills or attitudes do you look for when recruiting and interviewing red team members?
- What differentiates good red teamers from the pack as far as approaching a problem differently?
So, those are the 21 questions we asked 47 experts, including myself. I thought I’d chime in with my opinions to set the stage before getting to the 46 others. Hope you enjoy!
Marcus J. Carey
April 12, 2019