Implementing identity management begins with a plan. An identity and access management (IAM) system in an organization is a complex, distributed system that touches systems, networks, and applications, and also controls access to assets. An IAM system also includes the business processes that work together with IAM technologies and personnel to get the job done.
An IAM system probably is the most important function that an organization will ever implement. Next to the network itself, the IAM system typically is the most critical in an environment, because the IAM system controls access to all systems and applications.
Single sign-on (SSO)
The concept of single sign-on (SSO) addresses a common problem for both users and security administrators. Every account that exists in a system, network, or application is a potential point of unauthorized access. Multiple accounts that belong to a single user represent an even greater risk:
- Users who need access to multiple systems or applications often must maintain numerous sets of credentials. Inevitably, this leads to shortcuts in creating and recalling passwords. Left to their own devices, users create weak passwords that have only slight variations, or worse yet, they’ll use the same passwords everywhere they can. When they have multiple sets of credentials to manage, users are more likely to write them down. It doesn’t stop at the organization’s boundary: Users often use the same passwords at work that they do for their personal accounts.
- Multiple accounts also affect user productivity (and sanity!) because the user must stop to log in to different systems. Someone must also create and maintain accounts, which involves unlocking accounts and supporting, removing, resetting, and disabling multiple sets of userids and passwords.
At first glance (alas), SSO seems the “perfect” solution that users and security administrators seek. SSO allows a user to present a single set of logon credentials, typically to an authentication server, which then transparently logs the user into all other enterprise systems and applications for which that user is authorized. Of course, SSO does have some disadvantages, which include
- Woo-hoo!: After you’re authenticated, you have the keys to the kingdom. Read that as access to all authorized resources! It’s the security professional’s nightmare. If login credentials for a user’s accounts are compromised, an intruder can access everything the end user was authorized to access.
- Complexity: Implementing SSO can be difficult and time-consuming. You have to address interoperability issues between different systems and applications. But, hey — that’s why you get paid (or should get paid) the big bucks!
SSO is commonly implemented by various protocols and solutions, including the following.
SECURITY ASSERTION MARKUP LANGUAGE (SAML)
The de facto protocol for authentication, SAML is used for facilitating user authentication across systems and among organizations, through the exchange of authentication and authorization information between organizations. SAML is the glue that is used to make most single sign-on (SSO) systems work.
As its full name suggests, SAML is an XML markup language. XML is becoming a standard method for exchanging information between dissimilar systems.
KERBEROS
Kerberos, commonly used in the Sun Network File System (NFS) and Microsoft Windows, is perhaps the most popular ticket-based symmetric key authentication protocol in use today.
 Kerberos is named for the fierce, three-headed dog that guards the gates of Hades in Greek mythology. (Not to be confused with Ker-beer-os, the fuzzy, six-headed dog sitting at the bar that keeps looking better and better!) Researchers at the Massachusetts Institute of Technology (MIT, also known as Millionaires in Training) developed this open-systems protocol in the mid-1980s.
Kerberos is named for the fierce, three-headed dog that guards the gates of Hades in Greek mythology. (Not to be confused with Ker-beer-os, the fuzzy, six-headed dog sitting at the bar that keeps looking better and better!) Researchers at the Massachusetts Institute of Technology (MIT, also known as Millionaires in Training) developed this open-systems protocol in the mid-1980s.
The CISSP exam requires a general understanding of Kerberos operation. Unfortunately, Kerberos is a complex protocol that has many different implementations and no simple explanation. The following step-by-step discussion is a basic description of Kerberos operation:
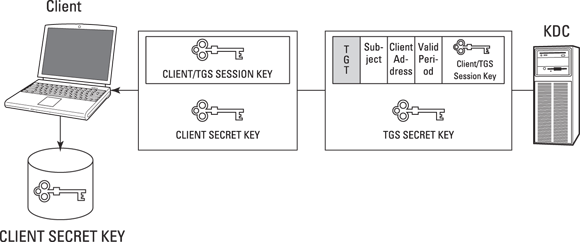
- The client prompts the subject (such as a user) for an identifier and a credential (for example, username and password). Using the authentication information (password), the client temporarily generates and stores a secret key for the subject by using a one-way hash function and then sends only the subject’s identification (username) to the Key Distribution Center’s (KDC) Authentication Server (AS). The password/secret key isn’t sent to the KDC. See Figure 7-1.
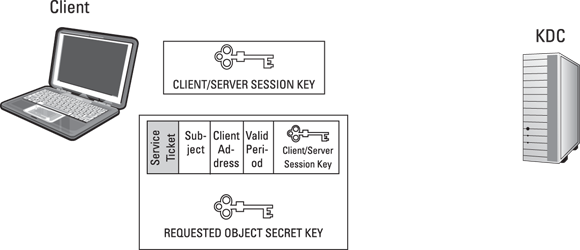
- The AS on the KDC verifies that the subject (known as a principal) exists in the KDC database. The KDC Ticket Granting Service (TGS) then generates a Client/TGS Session Key encrypted with the subject’s secret key, which only the TGS and the client know. The TGS also generates a Ticket Granting Ticket (TGT), consisting of the subject’s identification, the client network address, the valid period of the ticket, and the Client/TGS Session Key. The TGS encrypts the TGT by using its secret key, which only the TGS knows, then sends the Client/TGS Session Key and TGT back to the client. See Figure 7-2.
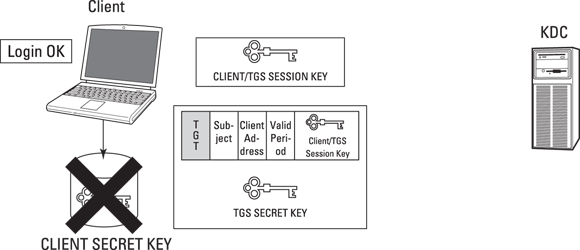
- The client decrypts the Client/TGS Session Key — using the stored secret key that it generated by using the subject’s password — authenticates the subject (user), and then erases the stored secret key to avoid possible compromise. The client can’t decrypt the TGT, which the TGS encrypted by using the TGS secret key. See Figure 7-3.
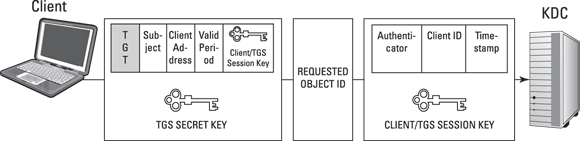
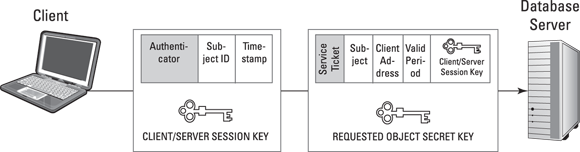
- When the subject requests access to a specific object (such as a server, also known as a principal), it sends the TGT, the object identifier (such as a server name), and an authenticator to the TGS on the KDC. (The authenticator is a separate message that contains the client ID and a timestamp, and uses the Client/TGS Session Key to encrypt itself.) See Figure 7-4.
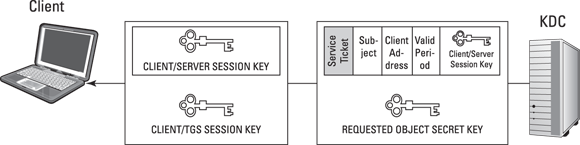
- The TGS on the KDC generates both a Client/Server Session Key (which it encrypts by using the Client/TGS Session Key) and a Service Ticket (which consists of the subject’s identification, the client network address, the valid period of the ticket, and the Client/Server Session Key). The TGS encrypts the Service Ticket by using the secret key of the requested object (server), which only the TGS and the object know. The TGS then sends the Client/Server Session Key and Service Ticket back to the client. See Figure 7-5.
- The client decrypts the Client/Server Session Key by using the Client/TGS Session Key. The client can’t decrypt the Service Ticket, which the TGS encrypted by using the secret key of the requested object. See Figure 7-6.
- The client can then communicate directly with the requested object (server). The client sends the Service Ticket and an authenticator to the requested object (server). The client encrypts the authenticator (comprising the subject’s identification and a timestamp) by using the Client/Server Session Key that the TGS generated. The object (server) decrypts the Service Ticket by using its secret key. The Service Ticket contains the Client/Server Session Key, which allows the object (server) to then decrypt the authenticator. If the subject identification and timestamp are valid (according to the subject identification, client network address, and valid period specified in the Service Ticket), then communication between the client and server is established. The Client/Server Session Key is then used for secure communications between the subject and object. See Figure 7-7.
See Chapter 5 for more information about symmetric key cryptography.
 In Kerberos, a session key is a dynamic key that is generated when needed, shared between two principals, then destroyed when it is no longer needed. A secret key is a static key that is used to encrypt a session key.
In Kerberos, a session key is a dynamic key that is generated when needed, shared between two principals, then destroyed when it is no longer needed. A secret key is a static key that is used to encrypt a session key.
LDAP
Lightweight Directory Access Protocol (LDAP) is both an IP protocol and a data model. LDAP (pronounced EL-dap) is used to support authentication and directory functions for both people and resources. Several vendors have implemented LDAP, including:
- Apache Directory Server
- CA eTrust Directory
- IBM SecureWay and Tivoli Directory Server
- Microsoft Active Directory
- Novell eDirectory
- Sun Directory Server
You can also find several open-source versions of LDAP available, including OpenLDAP and tinyldap.
RADIUS
The Remote Authentication Dial-In User Service (RADIUS) protocol is an open-source, client-server networking protocol — defined in more than 25 current IETF (Internet Engineering Task Force) RFCs (Request For Comments) — that provides authentication, authorization, and accounting (AAA) services. RADIUS is an Application Layer protocol that utilizes User Datagram Protocol (UDP) packets for transport. UDP is a connection-less protocol, which means it’s fast but not as reliable as other transport protocols.
RADIUS is commonly implemented in network service provider (NSP) networks, as well as corporate remote access service (RAS) and virtual private networks (VPNs). RADIUS is also becoming increasingly popular in corporate wireless networks. A user provides username/password information to a RADIUS client by using PAP or CHAP. The RADIUS client encrypts the password and sends the username and encrypted password to the RADIUS server for authentication.
Note: Passwords exchanged between the RADIUS client and RADIUS server are encrypted, but passwords exchanged between the workstation client and the RADIUS client are not necessarily encrypted — if using PAP authentication, for example. If the workstation client happens to also be a RADIUS client, all password exchanges are encrypted, regardless of the authentication protocol used.
RAS
Remote Access Service (RAS) servers utilize the Point-to-Point Protocol (PPP) to encapsulate IP packets and establish dial-in connections over serial and ISDN links. PPP incorporates the following three authentication protocols:
PAP: The Password Authentication Protocol (PAP) uses a two-way handshake to authenticate a peer to a server when a link is initially established. PAP transmits passwords in clear text and provides no protection from replay attacks (in which part of a session is captured or recorded, then played back to the system) or brute force attacks.
 A two-way handshake refers to a communications session in which the communicating devices, for example a remote workstation and a remote access server. The connection is established whereby one device sends an initial TCP SYN (Synchronize) packet to the other, and the other responds by sending an ACK (Acknowledgment) packet to indicate that the connection has been accepted.
A two-way handshake refers to a communications session in which the communicating devices, for example a remote workstation and a remote access server. The connection is established whereby one device sends an initial TCP SYN (Synchronize) packet to the other, and the other responds by sending an ACK (Acknowledgment) packet to indicate that the connection has been accepted.
- CHAP: The Challenge Handshake Authentication Protocol (CHAP) uses a three-way handshake to authenticate both a peer and server when a link is initially established and, optionally, at regular intervals throughout the session. CHAP requires both the peer and server to be preconfigured with a shared secret that must be stored in plain text. The peer uses the secret to calculate the response to a server challenge by using an MD5 one-way hash function. MS-CHAP, a Microsoft enhancement to CHAP, allows the shared secret to be stored in an encrypted form.
- EAP: The Extensible Authentication Protocol (EAP) adds flexibility to PPP authentication by implementing various authentication mechanisms, including MD5-challenge, S/Key, generic token card, digital certificates, and so on. Many wireless networks implement EAP.
TACACS
The Terminal Access Controller Access Control System (TACACS) is a remote authentication control protocol, originally developed for the MILNET (U.S. Military Network), which provides AAA services. The original TACACS protocol has been significantly enhanced, as XTACACS (no longer used) and TACACS+ (which is the most common implementation of TACACS). However, TACACS+ is a completely new protocol and therefore isn’t backward-compatible with either TACACS or XTACACS. TACACS+ is TCP based on (port 49) and supports practically any authentication mechanism (PAP, CHAP, MS-CHAP, EAP, token cards, Kerberos, and so on). The major advantages of TACACS+ are its wide support of various authentication mechanisms and granular control of authorization parameters. TACACS+ can also use dynamic passwords; TACACS uses static passwords only.
The original TACACS protocol is often used in organizations for simplifying administrative access to network devices such as firewalls and routers. TACACS facilitates the use of centralized authentication credentials that are managed centrally, so that organizations don’t need to manage user accounts on every device.
DIAMETER
This next-generation RADIUS protocol was developed to overcome some of RADIUS’s deficiencies, but it has yet to overcome RADIUS’s popularity, so it’s not yet widely implemented.
Like RADIUS, Diameter provides AAA services and is an open protocol standard defined in 11 current RFCs.
Unlike RADIUS, Diameter utilizes Transmission Control Protocol (TCP) and Stream Control Transmission Protocol (SCTP) packets to provide a more reliable, connection-oriented transport mechanism. Also, Diameter uses Internet Protocol Security (IPsec) or Transport Layer Security (TLS) to provide network security or transport layer security (respectively) — rather than PAP or CHAP (used in RADIUS) — to provide a more secure connection. See Chapter 6 for a complete discussion of TCP and SCTP, IPsec and TLS, and the OSI model.
Diameter isn’t fully backward-compatible with RADIUS, but it does provide an upgrade path for RADIUS-based environments. Diameter isn’t an acronym, but a pun on the term RADIUS. (In geometry, the diameter of a circle is twice its radius.)
SESAME
The Secure European System and Applications in a Multi-vendor Environment (SESAME) project, developed by the European Computer Manufacturers Association (ECMA), is a ticket-based system, like Kerberos, with some additional functionality. It uses both symmetric and asymmetric cryptography to distribute secret keys and securely transmit data. By using public key cryptography, SESAME can securely communicate between different organizations or security domains. It incorporates a trusted authentication server at each host (known as a Privileged Attribute Server, or PAS), employs MD5 and CRC-32 one-way hash functions, and uses two separate certificates (known as a Privileged Attribute Certificates, or PACs) to provide authentication and define access privileges. However, SESAME also has some serious security flaws in its basic implementation, including these:
- It uses an XOR function for encryption.
- It performs authentication based on a small segment of the message rather than on the entire message.
- Its key generation is not really very random.
- It’s vulnerable to password-guessing attacks. (Want to bet that somebody thought “open” was a pretty clever password?)
See Chapter 5 for more information on one-way hash functions, XOR functions, and key generation.
KryptoKnight
Developed by IBM, KryptoKnight is another example of a ticket-based SSO authentication and key distribution system that establishes peer-to-peer relationships between the Key Distribution Center (KDC) and its principals. In addition to user authentication with SSO, KryptoKnight provides two-party authentication, key distribution, and data integrity services. KryptoKnight is an extremely compact and flexible protocol that can be easily exported to other systems and applications, and it can function at any layer of the OSI model. Unlike Kerberos, KryptoKnight doesn’t require clock synchronization (it uses nonces instead).
A nonce is literally a number used once. Similar in concept to an initialization vector (see Chapter 5), a nonce is a randomly generated value (usually based on a timestamp) that can be used only once to authenticate a session.
 Kerberos, SESAME, and KryptoKnight are three examples of ticket-based authentication technologies that provide SSO services.
Kerberos, SESAME, and KryptoKnight are three examples of ticket-based authentication technologies that provide SSO services.
 LDAP, RAS (PAP and CHAP), RADIUS, Diameter, and TACACS are examples of centralized access control for remote access.
LDAP, RAS (PAP and CHAP), RADIUS, Diameter, and TACACS are examples of centralized access control for remote access.
 Controlling access to information, systems, devices, and facilities
Controlling access to information, systems, devices, and facilities Managing identification and authentication techniques
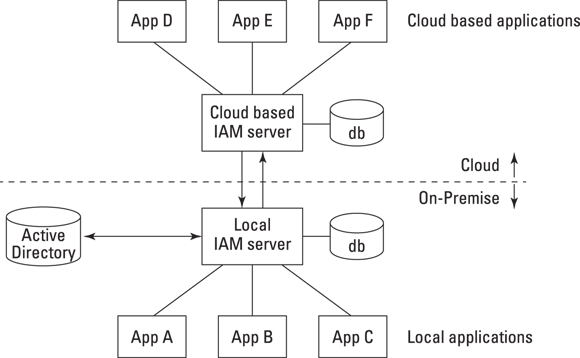
Managing identification and authentication techniques Integrating identity and access management in the cloud and on-premises
Integrating identity and access management in the cloud and on-premises Understanding data access control mechanisms
Understanding data access control mechanisms Defending against access control attacks
Defending against access control attacks Managing the identity and access provisioning lifecycle
Managing the identity and access provisioning lifecycle Kerberos is named for the fierce, three-headed dog that guards the gates of Hades in Greek mythology. (Not to be confused with Ker-beer-os, the fuzzy, six-headed dog sitting at the bar that keeps looking better and better!) Researchers at the Massachusetts Institute of Technology (MIT, also known as Millionaires in Training) developed this open-systems protocol in the mid-1980s.
Kerberos is named for the fierce, three-headed dog that guards the gates of Hades in Greek mythology. (Not to be confused with Ker-beer-os, the fuzzy, six-headed dog sitting at the bar that keeps looking better and better!) Researchers at the Massachusetts Institute of Technology (MIT, also known as Millionaires in Training) developed this open-systems protocol in the mid-1980s.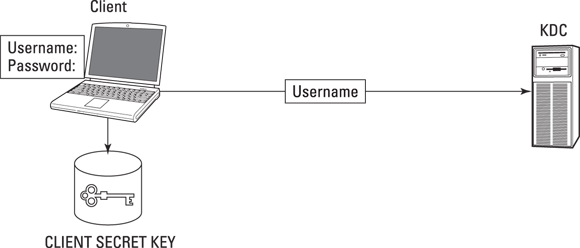
 In Kerberos, a session key is a dynamic key that is generated when needed, shared between two principals, then destroyed when it is no longer needed. A secret key is a static key that is used to encrypt a session key.
In Kerberos, a session key is a dynamic key that is generated when needed, shared between two principals, then destroyed when it is no longer needed. A secret key is a static key that is used to encrypt a session key. Because of the risks associated with text messages (such as mobile phone porting scams), the U.S. National Institute of Standards and Technology (NIST) has deprecated the use of text messages for multi-factor authentication.
Because of the risks associated with text messages (such as mobile phone porting scams), the U.S. National Institute of Standards and Technology (NIST) has deprecated the use of text messages for multi-factor authentication. You can use a software tool that helps users evaluate the quality of their passwords when they create them. These tools are commonly known as password/passphrase generators or password appraisers.
You can use a software tool that helps users evaluate the quality of their passwords when they create them. These tools are commonly known as password/passphrase generators or password appraisers.