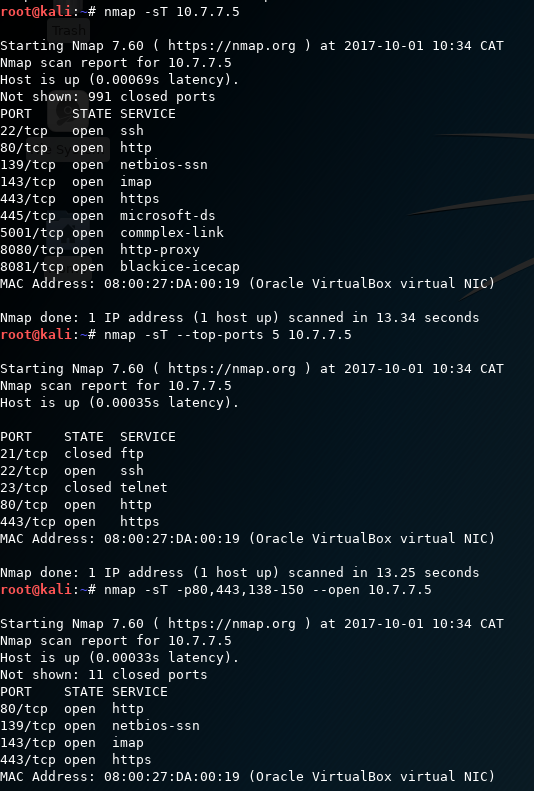
The straightforward way of running an Nmap port scan is called the TCP connect scan. This option is used to scan for open TCP ports, and it is invoked using the -sT option. The connect scan performs a full three-way TCP handshake (SYN-SYN / ACK-ACK). It provides a more accurate state of the port, but it is more likely to be logged at the target machine and slower than the alternative SYN scan. A SYN scan, using the -sS option, does not complete the handshake with the target, and it is therefore not logged on that target machine. However, the packets generated by the SYN scan can alert firewalls and IPS devices, and they are sometimes blocked by default by such appliances.
Nmap, when invoked with the -F flag, will scan for the top 100 ports instead of the top 1,000 ports. Additionally, it also provides you with the option to customize your scan with the --top-ports [N] flag to scan for N most popular ports from the nmap-services file. Many organizations might have applications that will be listening on a port that is not part of the nmap-services file. For such instances, you can use the -p flag to define a port, port list, or a port range for Nmap to scan.
There are 65535 TCP and UDP ports and applications that could use any of the ports. If you want, you can test all of the ports using the -p 1-65535 or -p- option.
The following screenshot shows the output of the preceding commands: