One of the first direct requests to a web server during a web penetration test should be to identify what methods are supported by the web server. You can use Netcat to open a connection to the web server and query the web server with the OPTIONS method. You can also use Nmap to determine the supported methods.
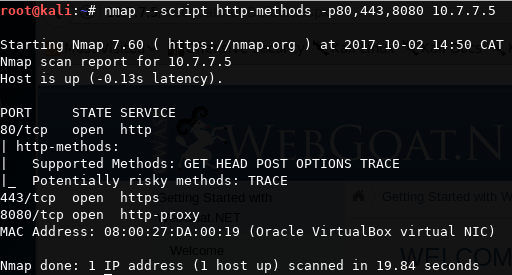
In the ever-increasing repository of Nmap scripts, you can find a script named http-methods.nse. When you run the script using the --script option along with the target, it will list the allowed HTTP methods on the target, and it will also point out the dangerous methods. In the following screenshot, you can see this in action where it detects several enabled methods and also points out TRACE as a risky method: