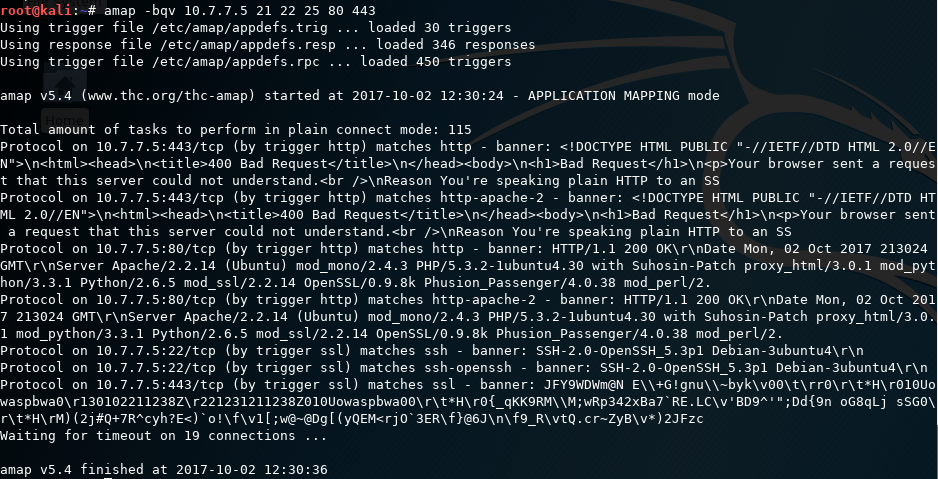
Kali Linux also comes with a tool called Amap, which was created by the The Hacker's Choice (THC) group and works like Nmap. It probes the open ports by sending a number of packets, and then it analyzes the response to determine the service listening on that port.
The probe to be sent to the target port is defined in a file called appdefs.trig, and the response that is received is analyzed against the signatures in the appdefs.resp file.
During a penetration test, it is important to probe the port using multiple tools to rule out any false positives or negatives. Relying on the signatures of one tool could prove to be fatal during a test, as your future exploits would depend on the service and its version identified during this phase.
You can invoke Amap using the -bqv option, which will only report the open ports and print the response received in ASCII and some detailed information related to it: