Burp Sequencer is a statistical analysis tool that lets you collect a large amount of values, such as session IDs, and perform calculations on them to evaluate if they are being randomly generated, or maybe just obfuscated or encoded. This is useful when dealing with complex session cookies, as it gives you an idea of how the cookies are being generated and if there is some way of attacking or predicting them.
To use Burp Sequencer, you first need to find the response that sets the session cookie. It's usually the response to a successful login with a Set-Cookie header. In the following screenshot, you can see the response that sets a session cookie (WEAKID) for the WebGoat's session hijacking exercise (go to WebGoat | Session Management Flaws | Hijack a Session):
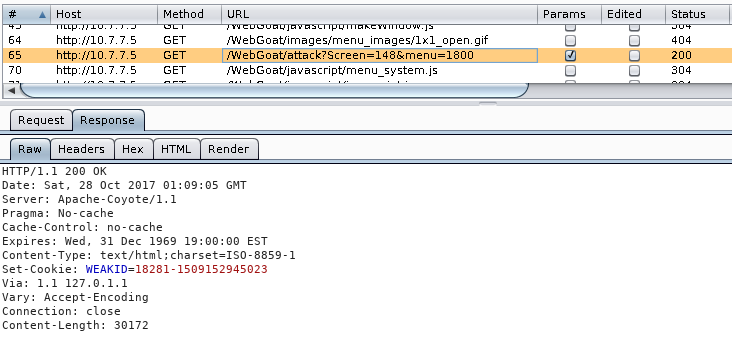
At first sight, the value of the response may seem unique and difficult enough to guess. The first part looks like an ID, and the second part appears to be a timestamp, maybe the expiration time in nanoseconds. It should be very difficult to guess at which precise nanosecond a session is ending, right? Well, as you'll see, it's not the best approach.
Find that response in the Burp Proxy's history, and right-click on it. You'll then see the Send to Sequencer option. Once in Sequencer, you need to choose which part of the response it is focused on:

You have the option to analyze a cookie, a form field, or a custom portion of the response. In this case, select the WEAKID cookie and click on Start live capture. It will start making requests to the server to capture as many different cookie values as possible. When finished, click on Analyze now to execute the analysis. In the result, Sequencer will indicate if the analyzed value is random enough and a good choice as a session ID. As you can see, WEAKID is weak and easily predictable:
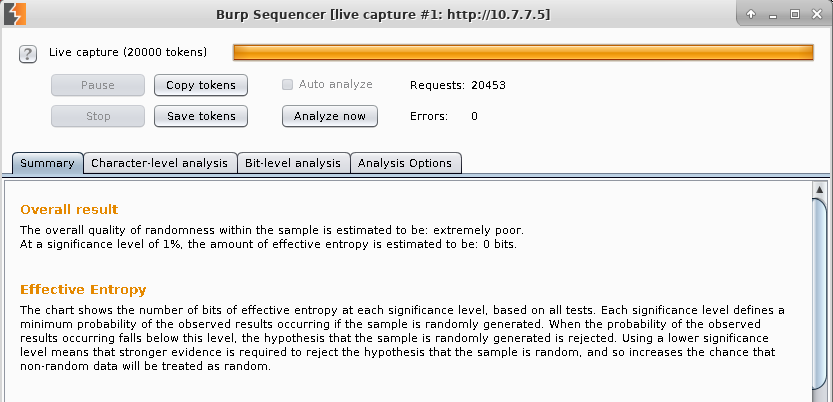
Entropy is a measure of the level of randomness in a piece of information. The result shows that WEAKID has zero randomness, which means that it's totally predictable and not a good option as a session ID. Sequencer also provides more detailed information about the distribution and significance of each byte and bit in the strings.
In the following screenshot, you'll see the character analysis chart. You can see that the characters in positions 3, 4, 15, 16, and 18 change much more than the characters in positions 0 or 5 to 13, which don't seem to change at all. Also, characters 0 to 4 suggest a counter or an increasing number, as the last character changes more than the previous one, and that character more than the one previous to it, and so on. We will verify this in the next section:
