We now need to go through the process of enabling user accounts in the directory to log in to the AWS management console.
- Point your browser to the AWS Directory Service Console and edit the configuration of your Simple AD directory. Enter the access URL you've chosen:
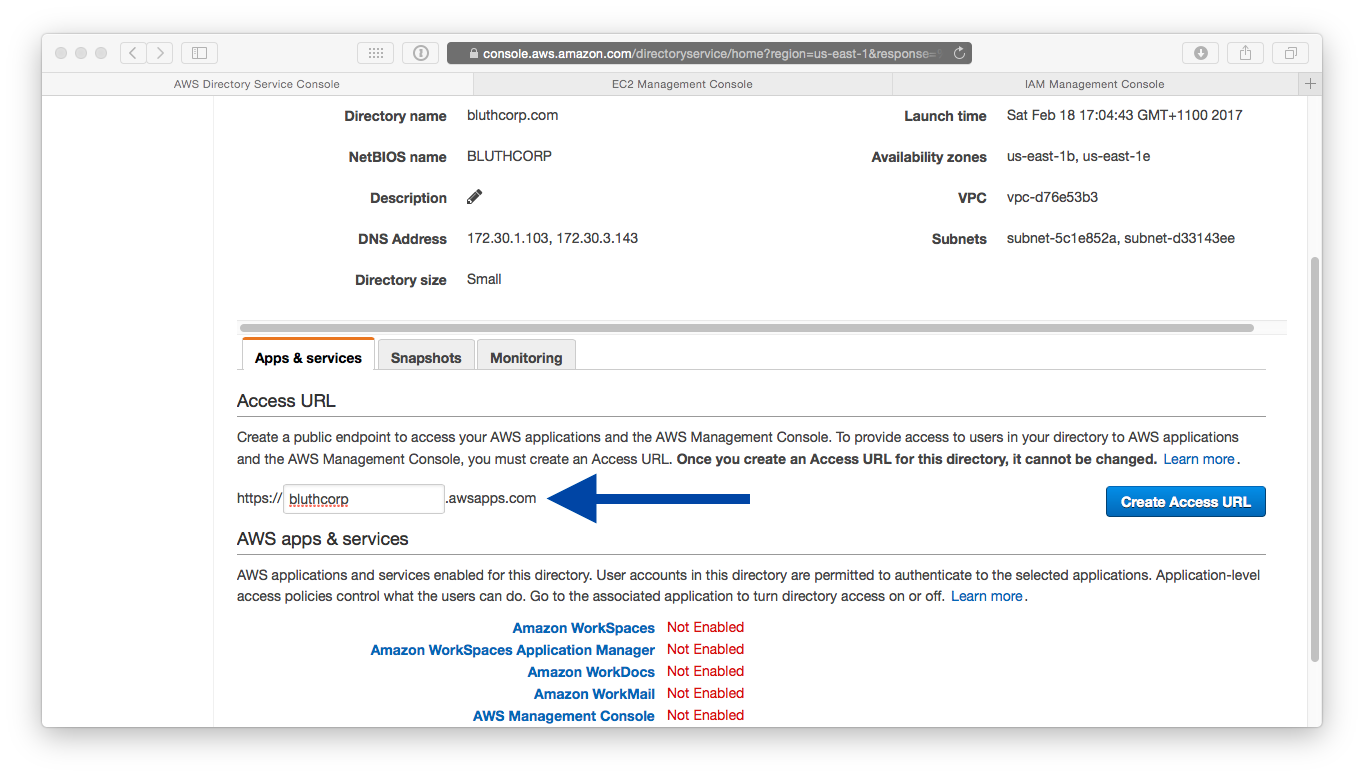
- We now want to enable the AWS Management Console for this service. Click on it to proceed to the next step:
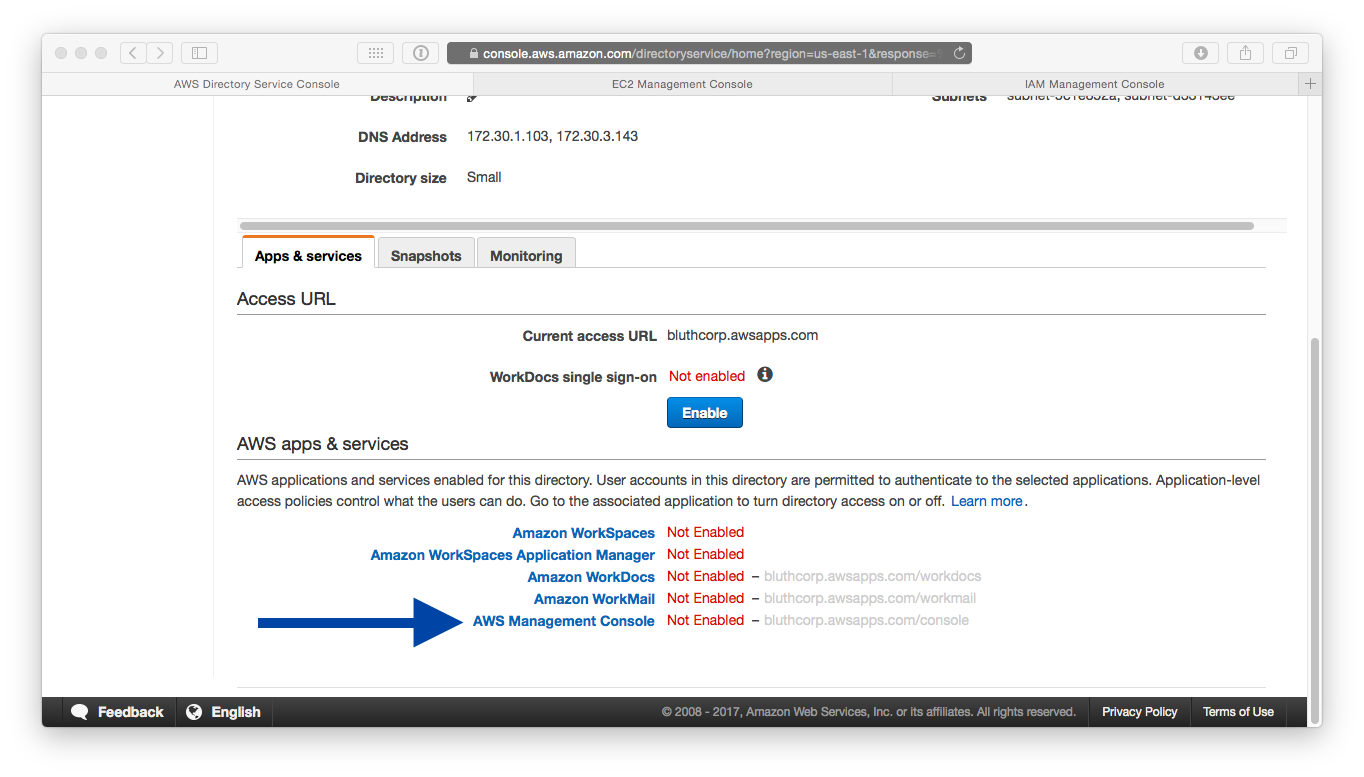
- We've already created roles and assigned a policy to them. So select Use Existing Role, as shown in the following screenshot:
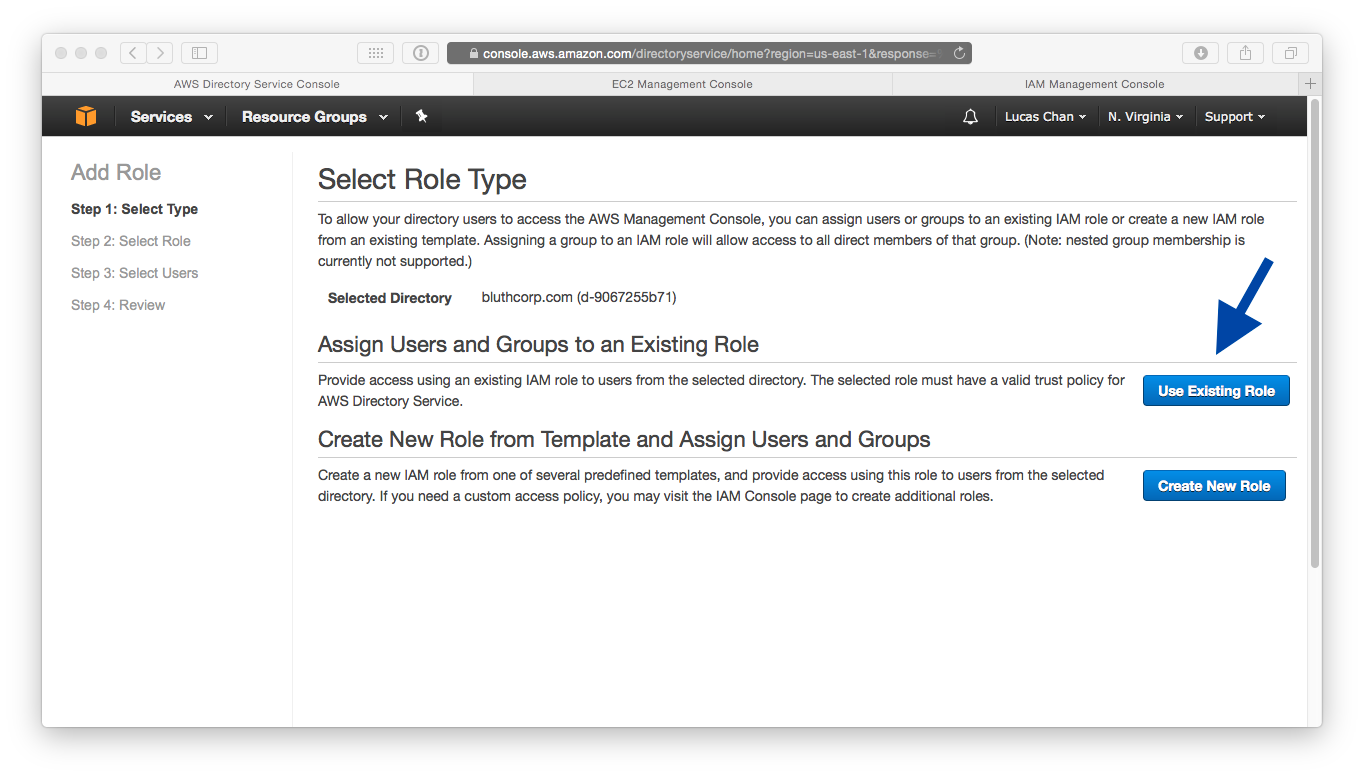
- Start with the CanAssumePowerUser role. We need to map it to the AWSPowerUser group we created in AD (the one Lucille resides in):

- Search for AWSPowerUser and then proceed to the next step:
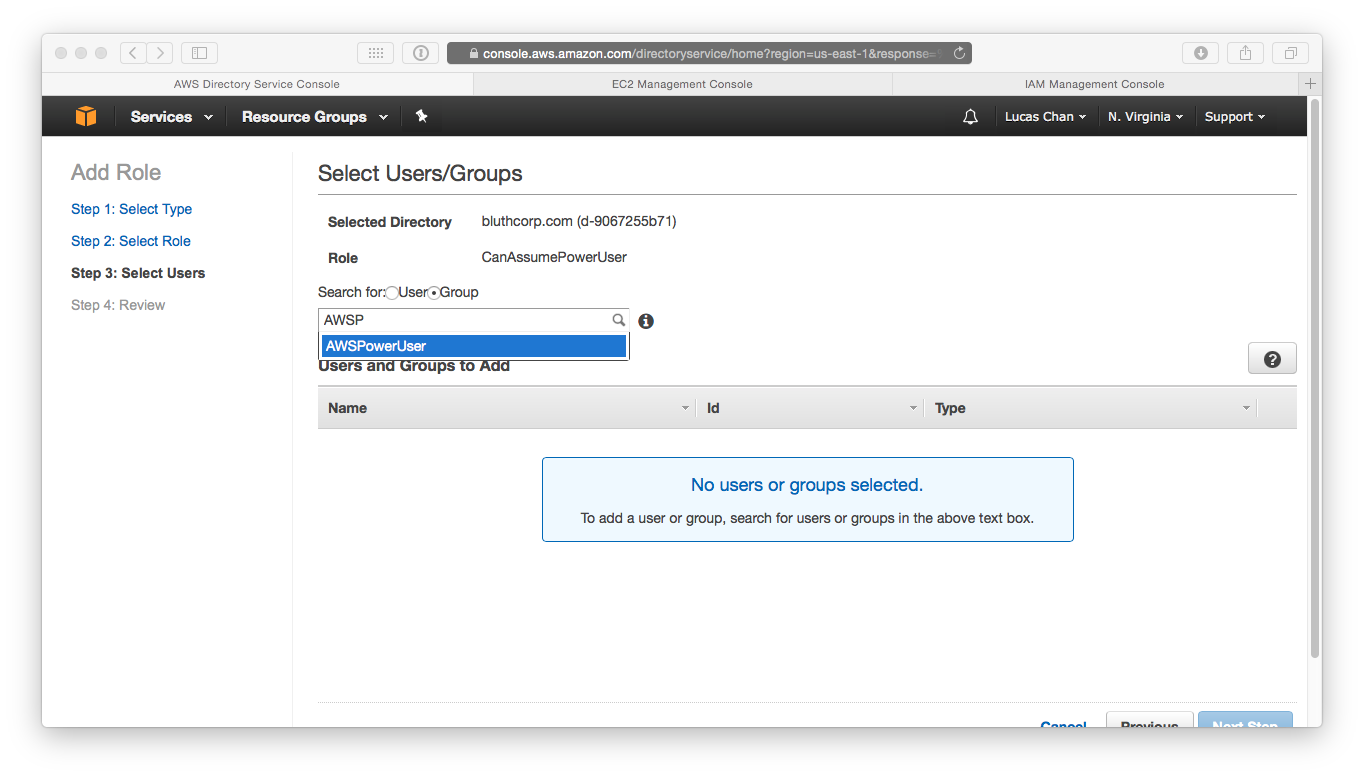
- You now need to repeat these steps for the CanAssumeReadOnly role. Map it to the AWSReadOnly role we created in AD:
