 10 MINUTES
10 MINUTESWorking with networks today, you will encounter a number of advanced and specialized network devices. You will still be responsible for troubleshooting clients, servers, and cables, but you will also deal with the detailed configuration of switches and routers.
In this chapter you will explore basic network terms, configure and work with VPNs and VLANs, and examine the properties of intrusion detection systems, intrusion prevention systems, and proxy servers.
 10 MINUTES
10 MINUTES
As with any discipline, developing an understanding of the terminology of the discipline is almost as important as being able to work with the technology. Network technicians must be very comfortable with their terminology, so that they can talk properly with peers, management, and customers about network-related problems and solutions.
In this lab exercise you will develop clear definitions of popular network terms and network technologies.
At the completion of this lab, you will be able to
 Identify advanced networking terms
Identify advanced networking terms
The materials you’ll need for this lab are
 The Mike Meyers’ CompTIA Network+ Guide to Managing and Troubleshooting Networks textbook
The Mike Meyers’ CompTIA Network+ Guide to Managing and Troubleshooting Networks textbook
 Pencil or pen
Pencil or pen
 Paper
Paper
Now that you have been with the company for some time, there actually are some techs who have less experience than you do. One of the junior network technicians is having some trouble understanding terms such as VLANs and VPNs, to name a couple. He asks if you would sit with him and help him identify the purpose of each of the mentioned technologies. You decide to help out by creating definitions of each and asking him to associate the terms with the definitions.
Match the following terms to the appropriate definitions:

 30 MINUTES
30 MINUTES
One of ITCF’s new clients is a small insurance firm with a number of agents who work from their homes. CJ and Maggie ask you to use the machines in the Network Lab to configure and test a virtual private network (VPN) solution using the built-in Routing and Remote Access Services (RRAS) role in Windows Server 2012/2012 R2. You will first create the VPN server, and then you will configure the client systems to access that server using VPN. Good luck!
For additional information on VPN technologies, check out the “VPN” section in Chapter 12 of the Mike Meyers’ CompTIA Network+ Guide to Managing and Troubleshooting Networks textbook.
In this lab, you’ll configure a Windows VPN server and a Windows VPN client. At the end of this lab, you will be able to
 Configure the RRAS VPN on a Windows Server 2012/2012 R2 system
Configure the RRAS VPN on a Windows Server 2012/2012 R2 system
 Implement and test a Windows VPN
Implement and test a Windows VPN
The materials you’ll need for this lab are
 Windows 7/8/8.1 client machine
Windows 7/8/8.1 client machine
 Windows Server 2012/2012 R2 machine
Windows Server 2012/2012 R2 machine
 A switch and appropriate cabling to connect the small network
A switch and appropriate cabling to connect the small network
 Pencil or pen
Pencil or pen
 Paper
Paper
You have really become quite efficient at managing the resources in the Network Lab and are very skilled at reconfiguring the machines and the network to test different scenarios. Maggie explains that you will need to install and configure the RRAS role on the Server 2012/2012 R2 machine.
Every time you configure these lab exercises, you learn a little more about networking technologies and reinforce the concepts you have been studying. In this lab exercise you will actually build an RRAS server to host your VPN server.
 Tech Tip
Tech Tip
Microsoft allows you to create a VPN server with Windows Server 2012/2012 R2 using RRAS. The RRAS role is installed from the Network Policy and Access Services under Server Roles.
Step 1 To configure the RRAS server for this lab exercise, complete the following substeps:
a. Boot up the Windows Server 2012/2012 R2 machine. The Server Manager window should have popped up by default when you got to the desktop. If you closed this window, reopen it by clicking the Server Manager icon in the bottom-left corner of the taskbar.
b. In the top-right corner, click Manage and then click Add roles and features, and then click the Next button.
c. Click Next through the next couple of screens (Installation Type and Server Selection). The next screen should be the Server Roles selection.
d. Select Remote Access and click Next (see Figure 12-1).
e. Click Next for the next three screens.
f. At the Role Services page, put a check mark in the box next to DirectAccess and VPN (RAS). Click the Add Features button in the new window that pops up. Click Next.
g. On the Confirmation screen, put a check in the box next to Restart the destination server automatically if required, click the Yes button in the new window that pops up, and then click the Install button. When the installation concludes, click the Close button.
h. Click the yellow Notifications triangle at the top of the Server Manager window. In the Post-deployment Configuration section, click Open the Getting Started Wizard.
i. In the Configure Remote Access window that pops up, select the Deploy VPN only option (see Figure 12-2).
j. In the Routing and Remote Access window that pops up, right-click the server and select Configure and Enable Routing and Remote Access. Click the Next button on the following screen. On the next screen, select Custom configuration and click Next. On the following screen, put a check mark in the box next to VPN access (see Figure 12-3) and click Next. Then, click Finish and, finally, click Start service.
FIGURE 12-1 Selecting the Remote Access role
FIGURE 12-2 Selecting the Deploy VPN only option
FIGURE 12-3 Enabling VPN access
Step 2 Now follow the substeps to create and authorize a user for the VPN:
a. Press the WINDOWS key and type Computer Management.
b. Under Local Users and Groups, select Users, right-click in the middle pane, and select New User.
c. Create a new user with a user name and password.
d. Right-click the user you created and select Properties.
e. Click the Dial-in tab and, under Network Access Permission, select Allow Access.
Step 3 Now follow the substeps to send client traffic through the VPN:
a. Before connecting to the VPN, open Wireshark and start a capture on the client machine. From the client machine, go to www.totalsem.com. You should see the HTTP traffic in Wireshark.
b. On your Windows 7/8/8.1 client, open Network and Sharing Center and select Set up a new connection or network to open the Set Up a Connection or Network wizard (see Figure 12-4).
c. Select Connect to a workplace and click Next.
d. When asked how you want to connect, select your Internet connection.
e. Enter the IP address of your server and then click Next.
f. Enter the user name and password of the user you created in the previous step and click Connect.
FIGURE 12-4 Connect to a workplace
Now that you are connected to the VPN, start a packet capture using Wireshark on the client and on the server. Go to www.totalsem.com again. After the page loads, stop the capture. How is this capture different?


 30 MINUTES
30 MINUTES
Virtual local area networks (VLANs) offer the capability of providing security on your network because systems in one VLAN cannot communicate with systems in other VLANs unless the administrator allows routing between the VLANs.
VLANs also offer the capabilities of creating broadcast domains within the switch. When a system in a VLAN broadcasts a message, that broadcast message does not go beyond the VLAN.
In this lab, you will create two VLANs on a Cisco multilayer switch. You will then verify that two systems connected to the switch and placed in different VLANs cannot communicate with one another until you enable interVLAN routing. By the end of this lab you should be able to
 Define the function of a VLAN
Define the function of a VLAN
 Configure VLANs
Configure VLANs
 Configure interVLAN routing
Configure interVLAN routing
The materials you’ll need for this lab are
 A Cisco 3560 switch (or similar) or a Cisco simulator
A Cisco 3560 switch (or similar) or a Cisco simulator
 A console (Yost) cable
A console (Yost) cable
 Two client systems
Two client systems
 Pencil or pen
Pencil or pen
 Paper
Paper
The Cisco 3560 switch is a multilayer switch providing the capability to create VLANs as well as implement interVLAN routing. There are many manufacturers and models of multilayer switches (sometimes called Layer 3 switches). If you have access to different model switches or only have access to a Layer 2 switch, you may still follow the steps to create two VLANs; however, you will not be able to configure interVLAN routing without a separate external router.
You will also be working with the Cisco command-line interface (CLI) in the Cisco IOS software. Only the commands needed to complete the lab exercise will be introduced. If you would like to explore the Cisco IOS software CLI further, please visit Cisco at www.cisco.com/en/US/docs/ios/preface/usingios.html.
Many of the commands you will use in this lab exercise will be run from the privileged EXEC mode (Switch#). This mode is normally password protected, and if the password is lost or forgotten, it can be difficult to reset the password. To perform a password recovery on a Cisco switch, navigate to the following Web site: www.cisco.com/c/en/us/support/docs/ios-nx-os-software/ios-software-releases-121-mainline/6130-index.html. Scroll down to the Index. Here you will find hyperlinks to the Password Recovery Procedure for many Cisco routers and switches. Follow the hyperlink for your Cisco switch to get the specific password recovery procedure.
Cathy, one of the network technicians at ITCF, is talking with Maggie and learns that you are working on your CompTIA Network+ certification. Cathy is working with a customer who is implementing VLANs and would like to know if you would like to learn how to configure VLANs. As usual, you jump at the chance to work with a mentor, and you invite Cathy to use a switch and two computers in the Network Lab.
Step 1 To set up the small network, power on the switch and then plug the first computer into port number 2. Connect the second computer to port number 8 on the switch.
Step 2 On both systems, disable the Windows Firewall. Configure the first computer (System1) with an IP address of 10.0.0.1/8 and the second computer (System2) with an IP address of 10.0.0.2/8.
Step 3 After configuring the IP addresses, open a command prompt and verify that you can ping from one computer to the other (see Figure 12-5). Can you successfully ping from computer 1 to computer 2?

FIGURE 12-5 Results of successfully configured network: System 1 can successfully ping System 2.
Step 4 Connect the console cable to the console port on your switch and then to the serial port on System 1. On System 1, launch PuTTY (download from www.chiark.greenend.org.uk/~sgtatham/putty/download.html). In the Basic options for your PuTTY session, verify that the Serial button is selected. Under the Category: pane, click the Serial menu item. Under the Options controlling local serial lines verify the following settings as shown in Figure 12-6:
FIGURE 12-6 PuTTY configuration window with serial settings to manage the Cisco 3560 switch

Click the Open button. You may have to press ENTER in the PuTTY command-line window before you see a prompt, allowing you to type commands.
Step 5 To display a list of VLANs that currently exist, type show vlan. You should see that there are a few default VLANs for different network architectures—notice that VLAN 1 is named the default VLAN (see Figure 12-7). The far right column shows you which ports are part of the VLAN. Record the ports that are part of the default VLAN:
FIGURE 12-7 Looking at the default VLANs on a Cisco switch


If you are using a switch that has been in the lab environment, it may already be in some state of configuration as opposed to the default out-of-box state. If you had any trouble pinging between the computers, or there seem to be some VLANs already configured, use the following steps to reset the switch:
a. Press and hold the Mode button for approximately 15 seconds (until the four LEDs turn solid green), then release the Mode button. The SYST LED should then blink and the terminal should indicate Reload Requested.
b. Press ENTER and when prompted Would you like to terminate autoinstall? [Yes/No], type Yes and press ENTER.
c. When prompted Would you like to enter the initial configuration dialog? [Yes/No], type No and press ENTER.
d. You should now be at the Switch> prompt.
e. Type enable and press ENTER. You should now be at the Switch# prompt. Type delete vlan.dat and press ENTER. Type reload, and then press enter. Press y, press ENTER, and boot back into the switch.
Step 6 To create a VLAN named Acct and one called Marketing, type the following commands, pressing ENTER after each command. You’ll start at the Switch> prompt:
enable
You should now be at the Switch# prompt. Keep going:
conf t
Now the prompt looks like this: Switch(config)#. Keep going:
vlan 2
Now the prompt looks like this: Switch(config-vlan)#. Keep going:
name Acct
You will return to the Switch(config-vlan)# prompt. If you did this correctly, you won’t get any feedback. Keep going:
exit
Now the prompt again looks like this: Switch(config)#. Keep going:
vlan 3
The prompt will change to Switch(config-vlan)#. Keep going:
name Marketing
You will return to the Switch(config-vlan)# prompt. If you did this correctly, you won’t get any feedback. Keep going:
End
Step 7 At this point, you should be at the prompt Switch#. You might see a log entry appear, saying that the switch configuration has changed. If so, press ENTER to get back to the prompt.
To view the newly created VLANs, type the following commands. Figure 12-8 shows the results.
FIGURE 12-8 Looking at the newly created VLANs
Switch# show vlan
Step 8 To place port 2 in the Acct VLAN, type the following commands, and press ENTER after each one. Note that the prompt dialog will change as you move through the commands.

Step 9 To place port 8 in the Marketing VLAN, type the following commands:

Step 10 To verify that the ports are placed in the appropriate VLANs, use the following command to display VLANs. Figure 12-9 shows the results.
FIGURE 12-9 Verifying that ports are assigned to the correct VLANs
Switch# show vlan
Step 11 Now that you have the ports that each system is connected to in different VLANs, the two systems should not be able to ping one another (see Figure 12-10). The reason is that VLANs are security boundaries and broadcast domains. Unless a Layer 3 device is used, only systems within a single VLAN and IP subnet will be able to communicate with one another, and not with systems in other VLANs or subnets. Furthermore, if two systems in the same IP subnet are configured for different VLANs, they will never be able to communicate under any circumstance, since Layer 3 devices only take traffic off a subnet.
FIGURE 12-10 Once the two systems are in different VLANs, they can no longer communicate.
Can you ping from System 1 to System 2? _____________________
Can you ping from System 2 to System 1? _____________________
Step 12 Now you will implement interVLAN routing to allow the two separate VLANs to communicate with each other. To enable interVLAN routing, you will assign a router address to each VLAN, and enable routing using the following commands, pressing ENTER after each command. Note that the prompt will change as you move through the commands. Start in privileged EXEC mode (Switch#).
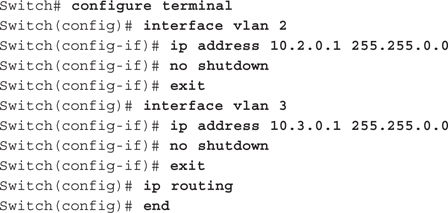
Step 13 To verify that the IP addresses have been assigned to the appropriate VLANs, use the following command to display VLANs and IP addresses. Figure 12-11 shows the results.
FIGURE 12-11 Verifying the VLANs and assigned IP addresses
show ip interface
Step 14 Now you must place the computer systems in the correct networks. Configure the first computer (System 1) with an IP address of 10.2.0.11/16 and a default gateway of 10.2.0.1. Configure the second computer (System 2) with an IP address of 10.3.0.11/16 and a default gateway of 10.3.0.1.
Step 15 Now that you have the VLANs routed, the two systems should be able to ping one another (see Figure 12-12). The Acct VLAN is network 10.2.0.0/16 and the Marketing VLAN is network 10.3.0.0/16.
FIGURE 12-12 Successful ping from System 1 (10.2.0.11/16) with a reply from System 2 (10.3.0.11/16)
Can you ping from System 1 to System 2? _____________________
Can you ping from System 2 to System 1? _____________________
To learn more about advanced switching topics such as VLANs, VLAN Trunking Protocol (VTP), and interVLAN routing, refer to Chapter 12 of the Mike Meyers’ CompTIA Network+ Guide to Managing and Troubleshooting Networks textbook.
 45 MINUTES
45 MINUTES
You have installed and configured a VPN and implemented VLANs. Now, to finish your exploration of advanced networking devices, you will explore what Mike terms network protection. There are four areas that you will examine:
 Intrusion detection system/intrusion protection system (IDS/IPS)
Intrusion detection system/intrusion protection system (IDS/IPS)
 Port mirroring
Port mirroring
 Proxy serving
Proxy serving
 Port authentication
Port authentication
Just as there are manufacturers that provide multilayer switches that are capable of providing VPNs and VLANs, there are manufacturers, developers, and methods that provide network protection. You’re going to explore some of these manufacturers, developers, and methods.
In this lab, you’ll explore a few of the manufacturers, developers, and methods that offer various network protection solutions. By the end of this lab, you will be able to
 Define IDS/IPS and profile one or two of the manufacturers
Define IDS/IPS and profile one or two of the manufacturers
 Define port mirroring
Define port mirroring
 Contrast the two types of proxy serving
Contrast the two types of proxy serving
 Detail port authentication
Detail port authentication
The materials you need for this lab are
 Internet access
Internet access
 Pencil or pen
Pencil or pen
 Paper
Paper
As with any network consulting firm, the staff at ITCF work hard to stay informed on the latest networking technologies, especially where network security and protection are concerned! After talking with one of your co-workers about IDS/IPS, you are intrigued and decide to do some further investigation.
Step 1 Beginning with IDS/IPS devices, provide a brief description of each device. Then conduct a Web search to profile one or two manufacturers that offer devices fitting those descriptions.


Step 2 See what you can find out about port mirroring. Record your findings in the following space.


Step 3 You have already read about proxy servers in the textbook. Now compare the features of a physical proxy server (such as the Blue Coat ProxySG 510) and a public proxy server.


Step 4 Finish with a short discussion about port authentication.


1. Sara knows that using a VPN allows you to safely connect to computers over the Internet using an encrypted channel. She would like to know the difference between an SSL VPN and an IPsec VPN. Briefly describe the difference for her.


2. Marc is about to purchase five new switches that he will be using in a VLAN configuration. What is the benefit of a multilayer switch?


3. Robert would like to implement the strongest protection available to prevent unwanted access to the corporate network. What is the difference between an IDS and an IPS? Which device would be considered the strongest protection?


4. ITCF already implements a robust firewall on their office Internet connection. Why might they want to install a proxy server as well?


Use the vocabulary terms from the list below to complete the sentences that follow.
intrusion detection system (IDS)
port mirroring
Routing and Remote Access Services (RRAS)
tunnel
1. A VPN is used to create an encrypted _______________ between the VPN client and the VPN server.
2. The _______________ role allows for the capability of a VPN on a server.
3. A(n) _______________ will monitor network traffic for suspicious activity.
4. In order to monitor network traffic on your switch, you will need to configure _______________ on the switch.