In this chapter:
Computer systems are used for many different purposes in business today. These range from keeping personal to-do lists to developing business-critical applications in banks. Applications are often categorized by their purpose. For example:
- Personal productivity and groupware
The use of Personal Computers (PCs) for word processing, electronic mail (email), and document sharing using a Local Area Network (LAN).
- Design and development
Computer-aided design and software development.
- Manufacturing and production
Monitoring and control applications in factories.
- Business intelligence
Data warehousing applications used to aid decision-making, arising from powerful, large-scale databases.
- Business operations
Business operations applications (sometimes called line of business applications) that “transact the business” of a company—in other words, they perform business transactions on behalf of the company. This is not limited to cash-for-goods transactions. It can include any buyer/supplier transaction that can be translated into a digital format, as well as internal business processes dealing with company resources. For example:
Credit card transactions
Cash transactions from a bank’s Automatic Teller Machine (ATM) or supermarket cash dispenser
Stock market transactions for a stock exchange or brokerage
Information transactions for collecting, collating, and distributing news—such as the results and medal tables for the Olympic Games
Payroll transactions (essential for the smooth operation of any corporation)
Logistics transactions, such as the scheduling of vehicles in a transportation company
Voice application transactions (“Press 1 to enter your meter reading….”) for a computer integrated telephony system
Sales transactions for companies doing business through the Internet
Business applications are crucial to many large and medium-sized companies. For such companies, doing business without these applications would be unthinkable; a bank that lost its computerized account records would cease trading. Many, if not most, of the largest business applications around the world run on CICS.
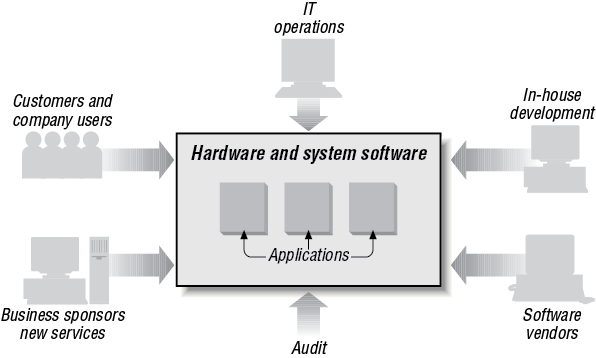
Even though the computer is at its center, a business application is focused on people. It is a human system as much as a computer system. The purpose of a business application is to keep accurate, up-to-date, and secure operational business information and deliver it rapidly to the users of the application. There are a number of key features that any business application needs. They have to be fast, accurate, secure, and auditable. In addition, the information has to be up to date and available to multiple users across a company, its suppliers, customers, and business partners. A model of the relationship between computers and people is shown in Figure 1-1.
Accuracy (in the sense of adhering to the intent of the business) depends on the computer system being controlled appropriately; that is, having clear lines of responsibility and division of responsibilities. It is essential to have organizational responsibilities that the system itself monitors and enforces. To this end, business applications broadly separate system development, system operations, and system use with checks and balances. These may be as official as a system audit. There are, of course, many subdivisions of these roles; for example, system development may be subdivided into architecture, design, programming, and testing.
Division of responsibility ensures that different groups of people involved with an application are unable to take advantage of their situations. Consider a payroll application, it should be impossible for payroll clerks to update their own salaries without being monitored; programmers would have built into the program an audit log that is checked by the audit department. Similarly, the program should include a log of all software updates to ensure that system administrators are unable to make fraudulent changes to the program without trace.
Business applications define the business rules that control the delivery and update of critical data; therefore, they require support throughout their lifecycle. The stages of a lifecycle include:
- Design
Design user interfaces that meet users’ needs; design for growth and extension; design to build complex applications with many features and capabilities.
- Develop
Develop efficiently, using modern tools and techniques.
- Test
Test thoroughly and efficiently to find problems and track down causes of problems.
- Update
Update in such a way as not to disrupt the existing version when upgrading to a new version.
In addition to lifecycle requirements, business applications must also meet a set of general technical requirements:
- Accessibility
The application can be used from any appropriate place on the network.
- Availability
The application is available for use by authorized persons at all designated times; it does not need to be shut down for routine maintenance and can be upgraded without interruption.
- Communication
Rapid communication is possible between distributed parts of the application.
- Manageability
Systems administrators can monitor the application to detect problems, and can take corrective action before users complain.
- Prioritized use of the hardware
A management capability should be in place to determine how much the machines are used, so that the workload can be distributed evenly.
- Rapid response
The response time for end users is appropriate (which usually means short!).
- Reliability
The application is not expected to fail, but if it does, it provides diagnostic information to help identify the cause of the failure.
- Recoverability
The application restarts quickly after a failure, without loss of information or of data integrity.
- Scaleability
The application can support as many users as needed without slowing down excessively or requiring excessive resources.
- Security
The application includes the ability to control who can use it, and which actions the users can perform.
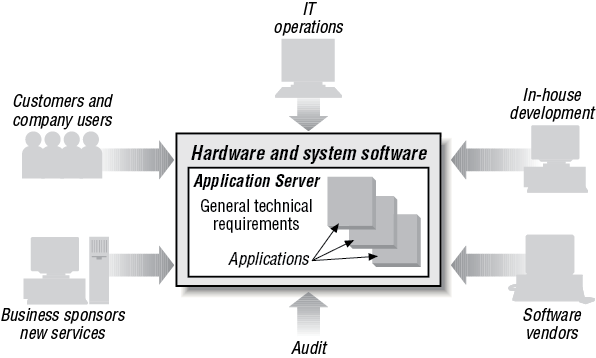
CICS was originally seen as a transaction processing system. Indeed behind the scenes this is a lot of what it is doing. But, like a lot of middleware, CICS comes to life by virtue of the many applications and operating systems that it supports. It not only provides an extensive Application Programming Interface (API), but it also controls the resources behind the applications; for example, security, databases, files, programs, transactions and so on, that the applications use. Hence, as CICS has evolved, describing it as an application server gives a much truer picture of its role today. In Figure 1-1 we see a loose arrangement of applications, which largely function independently of each other. Figure 1-2, on the other hand, draws those applications together so that there can be, for example, shared resources distributed across a computer network. To support the division of responsibilities, lifecycle requirements, and general technical requirements, an application server is required to manage the business applications. This is where CICS fits in. IBM’s product CICS is an application server.
If you have key applications that run 24 hours a day for 7 days a week and if your business requires that applications can be recovered completely after failure, you have good reason to move to CICS. If your business already uses CICS, extending your CICS system provides an integrated solution for your ever-increasing business requirements.