2
The World of Secret U.S. Government R&D
At the federal level the U.S. government’s budget for R&D supports a broad range of scientific and engineering activities with purposes including securing the national defense, advancing knowledge generally, developing the workforce, and strengthening U.S. innovation and competitiveness in the global economy.1 The U.S. government categorizes its R&D activities into three categories: basic research (known in the government as “6.1”), applied research (“6.2”), and development (“6.3”).2 The government also stipulates the measure of the maturity of a technology based on technology readiness level (TRL). TRL is a scale from one to nine, with one being the least mature technology and nine being a fielded system, shown in figure 8. These levels correspond to the phases of technology development from basic technology research through development to operations and support. In general a low TRL of one or two corresponds to 6.1 R&D; a TRL of three or four corresponds to 6.2 R&D, and so on. Figure 8 shows how R&D funds in the 6.1, 6.2, and 6.3 categories map to TRLs.
The U.S. government’s acquisition process is unique and complex, and it involves several steps: identifying priorities and needs, soliciting proposals, establishing contracts with defense contractors, and advancing technology through the phases of technology development.3 Because of this complexity, the government has dedicated acquisition agencies that are paired with agencies and military branches.4 The “milestone decisions,” shown in figure 8 as triangles labeled A, B, and C, are formal reviews and decision points in the acquisition process. For example, a technology must be developed and demonstrated to have achieved TRL 6 as a prerequisite to Milestone B. A defense “program” is considered to have officially started once it passes Milestone B.
Fig. 8. Technology readiness levels and types of R&D mapped to phases of technology development. Source: Adapted from Jacobsen, “Technology Readiness Levels Introduction,” and NASA and U.S. Army Medical Department Medical Research and Materiel Command, Army Technology Objectives (ATOS).
To define the scale of U.S. government R&D, it is important to understand the size of the federal budget, which is proposed by the executive branch and then must be approved by Congress. Congress defines the R&D priorities for the country and determines the “aggregate, agency, and programmatic R&D funding.”5 President Trump’s 2018 proposed R&D budget was $151 billion, a little more than half of which—$84 billion—was for defense.6 This was on a similar scale to spending levels for the last few years.7
The landscape of U.S. government R&D consists of many players, agencies, and organizations. Figure 9 maps the key players, including federal and state governments and nongovernmental players. The figure shows funding channels within government agencies, as well as funding for those working on U.S. government R&D contracts. Organizations outside of the U.S. government that provide funding to these contractors are also shown. In essence the figure depicts a stakeholder value network and uses arrows to show flows, covering the key categories of stakeholders relevant to U.S. government R&D environments. Each category includes a few example stakeholders.
There are three “flows” in the figure: political flows, which include approving budgets, lobbying representatives, ensuring compliance with regulations, creating or establishing courts, and providing oversight—such as that for security clearances; financial flows, which include equity investments, grants, contracts, and interdepartmental fund transfers; and the flow of technology or technology innovation.8
Note that many U.S. government agencies relevant here fall within federal executive branch departments headed by Cabinet members. There are also independent agencies that, while still part of the executive branch, are (or at least have traditionally been) insulated from short-term political pressure because the president’s power to replace the head of such an agency is limited through congressional statutes; these include agencies such as the Central Intelligence Agency (CIA) and National Science Foundation.
Certain programs cut across the landscape in figure 9. For example, Congress established the SBIR program as part of legislation that mandates eleven federal agencies to reserve a portion of their R&D funds for small businesses (defined as having fewer than five hundred employees).9 The Small Business Administration serves as the coordinating agency for the eleven agencies, reviews SBIR program implementation, and reports annually to Congress.10
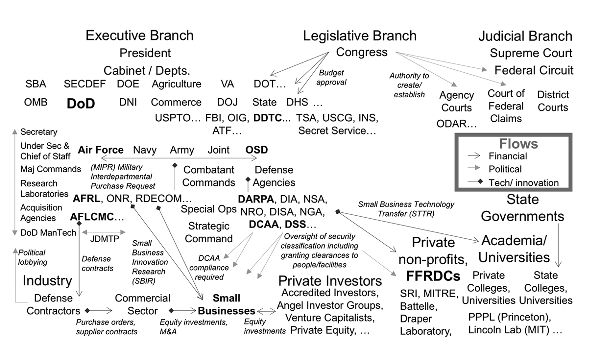
Fig. 9. Stakeholder value network: landscape of U.S. government R&D. Created by the author.
To illustrate how all of this works, a hypothetical electronic warfare program is discussed below, and key stakeholders are identified in bold in figure 9. This hypothetical program is led by the Air Force Materiel Command (AFMC), a major command in the U.S. Air Force (USAF) that focuses on weapon systems, receives congressional budget approval for its programs, and is overseen by the secretaries of the air force and defense, as well as—ultimately—the president. The Air Force Life Cycle Management Center (AFLCMC), an acquisition agency, oversees the identification and selection of defense contractors; this work is managed by a program executive officer (PEO).
Organizations within the Office of the Secretary of Defense (OSD) oversee various program functions, including those with a significant impact on innovation. The Defense Contract Audit Agency (DCAA) conducts financial audits and supports contract negotiations and administration for defense agencies. The Defense Security Service (DSS) provides oversight of security classification, including the granting of clearances to individuals and facilities, while the State Department’s Directorate of Defense Trade Controls (DDTC) oversees adherence to International Traffic in Arms Regulations (ITAR).
There are ways for defense agencies to acquire technology from each other simply and relatively quickly without putting new contracts in place. For instance, if the hypothetical USAF electronic warfare program seeks to leverage technology being developed at DARPA, the USAF can use a military interdepartmental purchase request (MIPR) to transfer money to DARPA. DARPA, in turn, can use the funding for programs that involve small businesses, universities, and Federally Funded Research & Development Centers (FFRDCs).
The hypothetical electronic warfare program may leverage technology developed through SBIR contracts. The USAF SBIR program is led out of the Air Force Research Laboratory (AFRL). Small businesses receive SBIR contracts from AFRL, and these are also overseen by organizations such as DCAA. Small businesses also receive funding from private investors.
Secure U.S. Government R&D
Secure U.S. government R&D is a subset of U.S. government R&D that specifically addresses national security. It tends to occur in a unique environment that restricts the disclosure of information, based on the assumption that secrecy is required to maintain national security. It probably comes as no surprise that secrecy is considered part and parcel of the United States’ most advanced technology for national security. Even the CIA website’s career page (shown in fig. 10) implies that “advanced technology” and “classified” are synonymous. To its credit, the CIA does have a sense of humor about its level of secrecy (see fig. 11).
In 2010 the Washington Post published “Top Secret America,” a series of articles by Dana Priest and William M. Arkin based on a two-year investigation. Some of the key statistics reported in the articles speak to the size and characteristics of overall secure U.S. government R&D:

Fig. 10. CIA website careers page. Source: U.S. Central Intelligence Agency, “Careers and Internships.”
The top-secret world the government created in response to the terrorist attacks of Sept. 11, 2001, has become so large, so unwieldy and so secretive that no one knows how much money it costs, how many people it employs, how many programs exist within it or exactly how many agencies do the same work. . . .
Some 1,271 government organizations and 1,931 private companies work on programs related to counterterrorism, homeland security and intelligence in about 10,000 locations across the United States. . . .
Every day across the United States, 854,000 civil servants, military personnel and private contractors with top-secret security clearances are scanned into offices protected by electromagnetic locks, retinal cameras and fortified walls that eavesdropping equipment cannot penetrate. . . .
Every one of these buildings has at least one of these rooms, known as a SCIF, for sensitive compartmented information facility. Some are as small as a closet; others are four times the size of a football field.
SCIF size has become a measure of status in Top Secret America, or at least in the Washington region of it. “In D.C., everyone talks SCIF, SCIF, SCIF,” said Bruce Paquin, who moved to Florida from the Washington region several years ago to start a SCIF construction business.11

Fig. 11. CIA’s first official tweet, June 2014. Source: CIA through @CIA Twitter handle.
It turns out that these numbers represent only a fraction of secure U.S. government settings. “The Post’s online database of government organizations and private companies was built entirely on public records. The investigation focused on top-secret work because the amount classified at the secret level is too large to accurately track.”12 The secure U.S. government R&D environment may be largely invisible to the general public, but it is vast and widespread.
Security Classification
What gets classified in the United States? Who decides what is classified? And who owns classified information? Since 1940 presidents have issued executive orders establishing U.S. government–wide classification standards and procedures.13 As of this writing, the current order in effect is President Obama’s Executive Order 13526; as in prior orders issued by other presidents, it defines three levels of classification: “Top Secret” is “applied to information, the unauthorized disclosure of which reasonably could be expected to cause exceptionally grave damage to the national security”; “Secret” applies to information whose disclosure could cause “serious damage” to national security; and “Confidential” is information whose disclosure could cause “damage” to national security.
Additional terms are used for certain classified information that gets special handling. Particularly sensitive information, designated as “Special Access Programs” (SAP) and “Sensitive Compartmented Information” (SCI), is not shared with individuals not working on that particular SAP or SCI program, even if those individuals have secret or top secret security clearances. A determination must be made that an individual has a “need to know” to gain access to information in a SAP or SCI program, and additional background checks or polygraph tests may be required. Some SAP and SCI programs are so sensitive that even top personnel in the U.S. government may be unaware of their existence; these programs are “unacknowledged,” and no reference is made to them in the published federal budget.
Transmitting and handling information at the three classification levels can be cumbersome. The information must be stored in locked safes, cannot be emailed or posted online, and usually cannot even be carried by hand from one location to another without advance notice, filled-out paperwork, and the involvement of security and document control personnel at both locations. Sometimes classified information can be communicated via special fax machines and secure phones, but the lengthy process required to get approval for such technologies means that they are often outdated and cumbersome to use once they’ve been installed. Even more restrictions apply for SAP and SCI environments.
Only a limited number of individuals who have what is called “original classification authority” (OCA) are empowered to decide whether information should be classified and at what level: the president, vice president, agency heads, and other officials designated by the president. In specific instances other U.S. government officials are delegated OCA pursuant to very specific restrictions. OCA is used to create security classification guides (SCGs), which define what specific information is classified and at what level. Derivative classification authority (DCA) is a much broader power and is widely used—for example, by employees of defense contractors to generate classified technical documents and mark them with the appropriate classification as per the relevant SCG. Individuals exercising DCA must be trained according to procedures defined by agencies in response to executive orders. For example, a defense contractor employee working on a classified project is required to read and undergo training on the SCG; then, when generating a technical document, he or she must mark the document according to the SCG. Security personnel of both the defense contractor and the U.S. government often review these markings.
Even though SCGs include directives to classify certain information at the highest level, the SCGs may themselves be unclassified. For example, the AFRL published an SCG for electronic warfare technology in 2005 specifying that certain information was unclassified—including “acknowledgement of the use of laser jamming or sensor damage techniques” in “technical operating concepts”—but classifying at the “secret” level the “details/techniques (such as waveforms, power/fluence, etc.) used against visual or IR imaging systems.”14 The 2005 SCG specifies additional information, such as declassification instructions and the reasons for classification. The three reasons for classification cited in this SCG are the following:
- Category 1.4a: Military plans, weapons, or operations.
- Category 1.4e: Scientific, technological, or economic matters relating to the national security, which includes defense against transnational terrorism.
- Category 1.4g: Vulnerabilities or capabilities of systems, installations, projects, plans, or protective services relating to the national security, which includes defense against transnational terrorism.15
The categories refer to the executive order on classification, which specifies the categories of information that can be classified.
Secrecy Orders
The U.S. Patent and Trademark Office (USPTO) also plays a role in classifying information by screening patent applications to determine whether disclosure of their subject matter would have a detrimental impact on national security. This practice began during World War I, when Congress legislated that the president could withhold a patent from being issued for national security reasons during wartime.16 The wartime restriction has since been removed. Also it is not just the president who can decide to withhold a patent; if in the opinion of an agency official the disclosure of an invention would be detrimental to national security, the commissioner of patents must enact a so-called “secrecy order.” Such an order not only forbids issuance of the patent, but also forbids the inventor from publishing or disclosing any material related to the invention. Congress stipulates the actions by the USPTO in the law.17
There are three types of secrecy orders. The first applies to patent applications that contain unclassified subject matter but whose distribution outside the United States is restricted.18 The second applies to patent applications that contain classified subject matter and for which appropriate controls have been identified (using DD Form 441). The third applies to patent applications that contain classified subject matter but for which appropriate controls have not yet been identified; in such cases the USPTO itself is responsible for prohibiting or approving disclosure of the invention. Sometimes when a secrecy order is imposed on a private inventor, it is referred to as a “John Doe” secrecy order.
The commissioner of patents reviews secrecy orders annually to determine whether they can be lifted; this review is waived during wartime and national emergencies. As figure 12 shows, the number of secrecy orders has increased over time. Thus the rate at which new secrecy orders are being imposed exceeds the rate at which secrecy orders are being lifted. The largest increase in secrecy orders in the last few years has come from the U.S. Navy (fig. 13).
Access to Classified Information
The U.S. government owns classified information and reserves the right to revoke access to it at any time. “A security clearance is a privilege, not a right,”19 and the law stipulates punishments for improperly disclosing classified information or otherwise violating the obligation to protect it.20
For an individual to have access to classified information, he or she must at a minimum have a security clearance. In most cases security clearances are given only to U.S. citizens who are sponsored for clearance by a U.S. government agency and who undergo a security investigation to determine whether they are “of unquestioned allegiance to the United States.”21 Before individuals gain access to classified information, they are required to sign nondisclosure agreements with the U.S. government that are lifelong obligations to protect classified information—even after their security clearances are no longer active. Security clearances must be renewed every five years, a procedure that typically requires a justification statement from a U.S. government agency for continued access and another security investigation.22

Fig. 12. Increase in total U.S. secrecy orders over time. Created by the author using data from Aftergood, “Invention Secrecy Statistics.”
When U.S. government agencies award a contract to a company that has not previously done business with the U.S. government, they can recommend that employees of the company be given security clearances—even if such clearances extend only to gaining access to secure government facilities and not to the handling or safeguarding of classified material at the company offices. The recommending agency becomes the sponsoring agency necessary for DSS to begin the process of investigating and granting security clearances.23
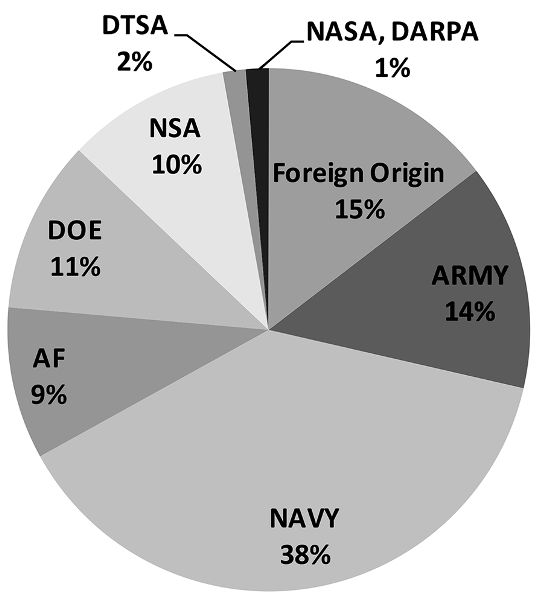
Fig. 13. New secrecy orders by U.S. government agency imposing the order. Created by the author using data from Aftergood, “Invention Secrecy Statistics.”
How, one might reasonably wonder, could innovation ever prosper in a classified world so restricted, so siloed, and so different from the open, collaborative world we imagine, say in Silicon Valley, where high-tech innovation seems to be a daily occurrence? In fact the secrecy and restrictions do kill innovation some of the time, but there are also occasions when innovation not only survives, but also thrives.
