CHAPTER 17
Physical Security Controls
In this chapter, you will
• Explore the importance of physical security controls
• Learn about important environment controls
Physical security is an important topic for businesses dealing with the security of networks and information systems. Businesses are responsible for managing their risk exposure, which requires securing a combination of assets: employees, product inventory, trade secrets, and strategy information. These and other important assets affect the profitability of a company and its future survival. Companies therefore perform many activities to attempt to provide physical security—locking doors, installing alarm systems, using safes, posting security guards, setting access controls, and more.
Environmental controls play an important role in the protection of the systems used to process information. Most companies today have invested a large amount of time, money, and effort in both network security and information systems security. In this chapter, you will learn about how the strategies for securing the network and for securing information systems are linked, and you’ll learn several methods by which companies can minimize their exposure to physical security events that can diminish their network security.
Certification Objective This chapter covers CompTIA Security+ exam objective 3.9, Explain the importance of physical security controls.
Lighting
Proper lighting is essential for physical security. Unlit or dimly lit areas allow intruders to lurk and conduct unauthorized activities without a significant risk of observation by guards or other personnel. External building lighting is important to ensure that unauthorized activities cannot occur without being observed and responded to. Internal lighting is equally important, for it enables more people to observe activities and see conditions that are not correct. As described later, in the “Barricades/Bollards” section, windows can play an important role in assisting the observation of the premises. Having sensitive areas well lit and open to observation through windows prevents activities that would otherwise take place in secret. Unauthorized parties in server rooms are more likely to be detected if the servers are centrally located, surrounded in windows, and well lit.
Signs
Signs act as informational devices and can be used in a variety of ways to assist in physical security. Signs can provide information as to areas that are restricted, or indicate where specific precautions, such as keeping doors locked, are required. A common use of signs in high-security facilities is to delineate where visitors are allowed versus secured areas where escorts are required. Visual security clues can assist in alerting users to the need for specific security precautions. Visual clues as to the types of protection required can take the form of different-color name badges that dictate the level of access, visual lanyards that indicate visitors, colored folders, and so forth.
Fencing/Gate/Cage
Fencing serves as a physical barrier around property. It can serve to keep people out and in, preventing the free movement across unauthorized areas. Fencing can be an important part of a physical security plan. Properly employed, it can help secure areas from unauthorized visitors. Outside of the building’s walls, many organizations prefer to have a perimeter fence as a physical first layer of defense. Chain-link-type fencing is most commonly used, and it can be enhanced with barbed wire along the top. Anti-scale fencing, which looks like very tall vertical poles placed close together to form a fence, is used for high-security implementations that require additional scale and tamper resistance.
Inside a building fencing can be used to provide a means of restricting entry into areas where separate physical security policies apply. Material storage, servers, networking gear, and other sensitive items can be separated from unauthorized access with simple chain link fences. These areas are typically called a cage, and entry/exit to the caged areas is via a gate. The gate allows controlled access and makes it easier to monitor who and what enters and leaves the controlled area. Gates are used for external fencing as well. Gates offer a monitoring point for ingress and egress from a controlled area.
Security Guards
Security guards provide an excellent security measure, because guards are a visible presence with direct responsibility for security. Other employees expect security guards to behave a certain way with regard to securing the facility. Guards typically monitor entrances and exits and can maintain access logs of who has entered and departed the building. In many organizations, everyone who passes through security as a visitor must sign the log, which can be useful in tracing who was at what location and why.
Security personnel are helpful in physically securing the machines on which information assets reside, but to get the most benefit from their presence, they must be trained to take a holistic approach to security. The value of data typically can be many times that of the machines on which the data is stored. Security guards typically are not computer security experts, so they need to be educated about the value of the data and be trained in network security as well as physical security involving users. They are the company’s eyes and ears for suspicious activity, so the network security department needs to train them to notice suspicious network activity as well. Multiple extensions ringing in sequence during the night, computers rebooting all at once, or strangers parked in the parking lot with laptop computers or other mobile computing devices are all indicators of a network attack that might be missed without proper training.
Alarms
Alarms serve to alert operators to abnormal conditions. Physical security can involve numerous sensors, intrusion alarms, motion detectors, switches that alert to doors being opened, video and audio surveillance, and more. Each of these systems can gather useful information, but it is only truly useful if it is acted upon. When one of these systems has information that can be of use to operational personnel, an alarm is the easiest method of alerting personnel to the condition. Alarms are not simple; if a company has too many alarm conditions, especially false alarms, then the operators will not react to the conditions as desired. Tuning alarms so that they provide useful, accurate, and actionable information is important if you want them to be effective.

EXAM TIP Lighting, signs, fencing, and alarms are all items readily associated with physical security. The proper answer to an exam question will be based on the specific details of the question—watch for the clues and pick the best answer based on the context of the question.
Safe
Safes are physical storage devices that are intended to impede unauthorized access to their protected contents. Safes come in a wide variety of shapes, sizes, and cost. The higher the level of protection from the physical environment, the better the level of protection against unauthorized access. Safes are not perfect; in fact, they are rated in terms of how long they can be expected to protect the contents from theft or fire. The better the rating, the more expensive the safe.
Secure Cabinets/Enclosures
There are times when a safe is overkill, providing a higher level of security than is really needed. A simpler solution is secure cabinets and enclosures. Secure cabinets and enclosures provide system owners a place to park an asset until its use. Most secure cabinets/enclosures do not offer all of the levels of protection that one gets with a safe, but they can be useful, especially when the volume of secure storage is large.
Secure enclosures can provide security against some forms of physical access, as in users, yet still provide the proper environmental controls and setting necessary for operation. Safes cannot typically provide these levels of controls.
Protected Distribution/Protected Cabling
Cable runs between systems need to be protected from physical damage to the cables and subsequent communication failures. This is accomplished by protected distribution/protected cabling during the cable installation. This may be something as simple as metal tubes, or as complex a concrete pipes to run buried cables. The objective is to prevent any physical damage to the physical layer portion of the system. Protected distribution/protected cabling provides physical safeguards to the cabling between systems, from all physical hazards including interception and tapping. The protection of entire systems is covered later in the section “Faraday Cages.”
Airgap
An airgap is a term used to describe the physical and logical separation of a network from all other networks. This separation is designed to prevent unauthorized data transfers to and from the network. The flaw in this logic is that users will move data by other means, such as a USB drive, to get their work done. Frequently called “sneaker net,” this unauthorized bypassing of the airgap, although ostensibly for the purpose of mission accomplishment, increases system risk because it also bypasses checks, logging, and other processes important in development and deployment.
Mantrap
The implementation of a mantrap is one way to combat tailgating. A mantrap comprises two doors closely spaced that require the user to card through one and then the other sequentially. Mantraps make it nearly impossible to trail through a doorway undetected—if an intruder happens to catch the first door before it closes, he will be trapped in by the second door as the second door remains locked until the first one closes and locks.

EXAM TIP A mantrap door arrangement can prevent unauthorized people from following authorized users through an access-controlled door, which is also known as tailgating.
Faraday Cages
Electromagnetic interference (EMI) is an electrical disturbance that affects an electrical circuit. EMI is due to either electromagnetic induction or radiation emitted from an external source, either of which can induce currents into the small circuits that make up computer systems and cause logic upsets, and is covered in Chapter 12. EMI can plague any type of electronics, but the density of circuitry in the typical data center can make it a haven for EMI. EMI is defined as the disturbance on an electrical circuit caused by that circuit’s reception of electromagnetic radiation. Magnetic radiation enters the circuit by induction, where magnetic waves create a charge on the circuit. The amount of sensitivity to this magnetic field depends on a number of factors, including the length of the circuit, which can act like an antenna. EMI is grouped into two general types: narrowband and broadband. Narrowband is, by its nature, electromagnetic energy with a small frequency band and, therefore, typically sourced from a device that is purposefully transmitting in the specified band. Broadband covers a wider array of frequencies and is typically caused by some type of general electrical power use such as power lines or electric motors.
In the United States, the Federal Communications Commission (FCC) has responsibility for regulating products that produce EMI and has developed a program for equipment manufacturers to adhere to standards for EMI immunity. Modern circuitry is designed to resist EMI. Cabling is a good example; the twists in unshielded twisted pair (UTP), or Category 5e, 6, 6a, or 7, cable are there to prevent EMI. EMI is also controlled by metal computer cases that are grounded; by providing an easy path to ground, the case acts as an EMI shield. Shielding can be important for network cabling. It is important not to run lengths of network cabling in parallel with power cables. Twisted pair offers some degree of protection, but in electrically noisy environments such as industrial facilities, shielded twisted pair (STP) may be necessary.
A bigger example of shielding would be a Faraday cage or Faraday shield, which is an enclosure of conductive material that is grounded. These can be room-sized or built into a building’s construction; the critical element is that there is no significant gap in the enclosure material. These measures can help shield EMI, especially in high radio frequency environments.
While we have talked about the shielding necessary to keep EMI radiation out of your circuitry, there is also technology to try and help keep it in. Known by some as TEMPEST, it is a DoD program designed to block Van Eck emissions. A computer’s monitor or LCD display produces electromagnetic radiation that can be remotely observed with the correct equipment, called Van Eck emissions. TEMPEST was the code word for a National Security Agency (NSA) program to secure equipment from this type of eavesdropping. While some of the information about TEMPEST is still classified, there are guides on the Internet that describe protective measures, such as shielding and electromagnetic-resistant enclosures. A company has even developed a commercial paint that offers radio frequency shielding. All of these protections are designed to stop electromagnetic energy from carrying a signal beyond a specific physical boundary, either the Faraday cage or paint or other EM barrier. This prevents outside signals from getting in and prevents those outside from monitoring what is happening on the inside.

EXAM TIP When it comes to shielding, understand the difference between a Faraday cage (large open space) and EMI shielding on cables (very specific shielding) and which is appropriate based on what is being protected from EMI.
Lock Types
Locks are a common security measure that are used with near ubiquity. Everyone is familiar with using a lock to secure something. Many different lock types are used in and around the computer security arena. There are types for laptops, for desktops, even servers. Just as locks can keep your car or bike from being stolen, they can secure computers as well. Laptops are popular targets for thieves and should be locked inside a desk when not in use, or secured with special computer lockdown cables. Laptop thefts from cars can occur in seconds, and thieves have been caught taking laptops from security screening areas at airports while the owner was distracted in screening. If an organization uses desktop towers, it should use computer desks that provide a space in which to lock the computer. In some cases, valuable media are stored in a safe designed for that purpose. All of these measures can improve the physical security of the computers themselves, but most of them can be defeated by attackers if users are not knowledgeable about the security program and do not follow it.
Although locks have been used for hundreds of years, their design has not changed much: a metal “token” is used to align pins in a mechanical device. Because all mechanical devices have tolerances, it is possible to sneak through these tolerances by “picking” the lock. Most locks can be easily picked with simple tools, some of which are shown in Figure 17-1.

Figure 17-1 Lock-picking tools
Humans are always trying to build a better mousetrap, and that applies to locks as well. High-security locks have been designed to defeat attacks, such as the one shown in Figure 17-2; these locks are more sophisticated than a standard home deadbolt system. Typically found in commercial applications that require high security, these locks are made to resist picking and drilling, as well as other common attacks such as simply pounding the lock through the door. Another common feature of high-security locks is key control, which refers to the restrictions placed on making a copy of the key. For most residential locks, a trip to the hardware store will allow you to make a copy of the key. Key control locks use patented keyways that can only be copied by a locksmith, who will keep records on authorized users of a particular key.

Figure 17-2 A high-security lock and its key
High-end lock security is more important now that attacks such as “bump keys” are well known and widely available. A bump key is a key cut with all notches to the maximum depth, also known as “all nines.” This key uses a technique that has be around a long time, but has recently gained a lot of popularity. The key is inserted into the lock and then sharply struck, bouncing the lock pins up above the shear line and allowing the lock to open. High-security locks attempt to prevent this type of attack through various mechanical means such as nontraditional pin layout, sidebars, and even magnetic keys.
Biometrics
Biometrics is the measurement of biological attributes or processes with the goal of identification of a party possessing the measures. The most well-known biometric factor is the fingerprint. Fingerprint readers have been available for several years in laptops and other mobile devices, such as shown in Figure 17-3, and as stand-alone USB devices.

Figure 17-3 Newer laptop computers often include a fingerprint reader.
Other biometric measurements that can be used for physical security purposes include the retina or iris of the eye, the geometry of the hand, and the geometry of the face. When any of these are used for authentication, there is a two-part process: enrollment and then authentication. During enrollment, a computer takes the image of the biological factor and reduces it to a numeric value. When the user attempts to authenticate, his or her feature is scanned by the reader, and the computer compares the numeric value being read to the one stored in the database. If they match, access is allowed. Since these physical factors are unique, theoretically, only the actual authorized person would be allowed access.
Biometrics are frequently used in physical security, and are becoming nearly ubiquitous for controlling access to mobile devices, such as phones and tablets. For many physical security situations, the true question for access is, are you the correct person who should have access? Using biometrics to confirm the identity of the person being presented for access as the same person who went through the identification phase at enrollment is a good way to answer this question. You can’t loan your fingerprints, iris, or retina for a scan, or your hand for its geometry. Biometrics bind the identification token to the person.
Biometrics are not foolproof. Some biometric measures can be duplicated to fool a sensor, and in many cases, the actual biometric is converted to a number that can also be intercepted and used in a software attack. Safeguards exist for most biometric bypass mechanisms, making them a usable security technology.
Barricades/Bollards
The primary defense against a majority of physical attacks are the barricades between the assets and a potential attacker—walls, fences, gates, and doors. Barricades provide the foundation upon which all other security initiatives are based, but the security must be designed carefully, as an attacker has to find only a single gap to gain access. Barricades can also be used to control vehicular access to and near a building or structure. The simple post-type barricade that prevents a vehicle from passing but allows people to walk past is called a bollard.

EXAM TIP All entry points to server rooms and wiring closets should be closely controlled, and, if possible, access should be logged through an access control system.
Walls may have been one of the first inventions of humans. Once they learned to use natural obstacles such as mountains to separate them from their enemy, they next learned to build their own mountain for the same purpose. Hadrian’s Wall in England, the Great Wall of China, and the Berlin Wall are all famous examples of such basic physical defenses. The walls of any building serve the same purpose, but on a smaller scale: they provide barriers to physical access to company assets. In the case of information assets, as a general rule, the most valuable assets are contained on company servers. To protect the physical servers, you must look in all directions. Doors and windows should be safeguarded, and a minimum number of each should be used in a server room when they are all that separate the servers from the personnel allowed to access them. It is very important that any transparent windows or doors do not allow shoulder surfing from outside the server room. It is good to see people in the room, just not what they type on their screens. Less obvious entry points should also be considered: Is a drop ceiling used in the server room? Do the interior walls extend to the actual roof, raised floors, or crawlspaces? Access to the server room should be limited to the people who need access, not to all employees of the organization. If you are going to use a wall to protect an asset, make sure no obvious holes appear in that wall.
NOTE Windows or no windows? Windows provide visibility, allowing people to observe activities in the server room. This can provide security if those doing the observing have authority to see the activity in the server room. If those outside do not have this authority, then windows should be avoided.
Another method of preventing surreptitious access is through the use of windows. Many high-security areas have a significant number of windows so that people’s activities within the area can’t be hidden. A closed server room with no windows makes for a quiet place for someone to achieve physical access to a device without worry of being seen. Windows remove this privacy element that many criminals depend upon to achieve their entry and illicit activities.
Tokens/Cards
Controlling physical access to a small facility can be achieved through door locks and physical keys, but that solution is unwieldy for larger facilities with numerous people coming and going. Many organizations rely on a badging system using either tokens or cards that can be tied to automated ID checks and logging of entry/exit. This can provide much greater detail in tracking who is in a facility and when they have come and gone. Tokens and cards can embed a serialized ID for each user, enabling user-specific logging. Originally designed to augment payroll time cards, these electronic IDs have improved security through the logging of employees’ in and out times. Tokens and cards offer the same function as keys, but the system can be remotely updated to manage access in real time, and users can have privilege revoked without having to recover the token or card.
Environmental Controls
While the confidentiality of information is important, so is its availability. Sophisticated environmental controls are needed for current data centers. Heating and cooling is important for computer systems as well as users. Server rooms require very specific cooling, usually provided by a series of hot and cold aisles. Fire suppression is an important consideration when dealing with information systems.

EXAM TIP Be sure you understand the principles behind environmental control systems such as HVAC and fire suppression, as well as environmental monitoring.
HVAC
Controlling a data center’s temperature and humidity is important to keeping servers running. Heating, ventilating, and air conditioning (HVAC) systems are critical for keeping data centers cool, because typical servers put out between 1000 and 2000 BTUs of heat (1 BTU equals the amount of energy required to raise the temperature of one pound of liquid water one degree Fahrenheit).
Multiple servers in a confined area can create conditions too hot for the machines to continue to operate. This problem is made worse with the advent of blade-style computing systems and with many other devices shrinking in size. While physically smaller, they tend to still expel the same amount of heat.
Temperature is not the only concern. Humidity needs to be controlled to prevent static issues (too low humidity) or condensation issues (too high humidity). Typically, air pressure in controlled spaces is kept slightly higher than surrounding areas, to ensure air flows out of the controlled space, not in.
Hot and Cold Aisles
The trend toward smaller, denser servers means more servers and devices per rack, putting a greater load on the cooling systems. This encourages the use of a hot aisle/cold aisle layout. A data center that is arranged into hot and cold aisles dictates that all the intake fans on all equipment face the cold aisle, and the exhaust fans all face the opposite aisle. The HVAC system is then designed to push cool air underneath the raised floor and up through perforated tiles on the cold aisle. Hot air from the hot aisle is captured by return air ducts for the HVAC system. The use of this layout is designed to control airflow, with the purpose being never to mix the hot and cold air. This requires the use of blocking plates and side plates to close open rack slots. The benefits of this arrangement are that cooling is more efficient and can handle higher density.
Fire Suppression
According to the Fire Suppression Systems Association (www.fssa.net), 43 percent of businesses that close as a result of a significant fire never reopen. An additional 29 percent fail within three years of the event. The ability to respond to a fire quickly and effectively is thus critical to the long-term success of any organization. Addressing potential fire hazards and vulnerabilities has long been a concern of organizations in their risk analysis process. The goal obviously should be never to have a fire, but in the event that one does occur, it is important to have mechanisms in place to limit the damage the fire can cause. Fire suppression systems are designed to provide protection against the damage from a fire that spreads in a facility. Because they are suppression systems, they don’t prevent the fire from occurring per se, but they do stop it once it begins.
Water-Based Fire Suppression Systems
Water-based fire suppression systems have long been, and still are today, the primary tool to address and control structural fires. Considering the amount of electrical equipment found in today’s office environment and the fact that, for obvious reasons, this equipment does not react well to large applications of water, it is important to know what to do with equipment if it does become subjected to a water-based sprinkler system. The 2017 NFPA 75: Standard for the Protection of Information Technology Equipment outlines measures that can be taken to minimize the damage to electronic equipment exposed to water. This guidance includes these suggestions:
• Open cabinet doors, remove side panels and covers, and pull out chassis drawers to allow water to run out of equipment.
• Set up fans to move room-temperature air through the equipment for general drying. Move portable equipment to dry, air-conditioned areas.
• Use compressed air at no higher than 50 psi to blow out trapped water.
• Use handheld dryers on the lowest setting to dry connectors, backplane wirewraps, and printed circuit cards.
• Use cotton-tipped swabs for hard-to-reach places. Lightly dab the surfaces to remove residual moisture. Do not use cotton-tipped swabs on wirewrap terminals.
• Use water-displacement aerosol sprays containing Freon-alcohol mixtures as an effective first step in drying critical components. Follow up with professional restoration as soon as possible.
Even if these guidelines are followed, damage to the systems may have already occurred. Since water is so destructive to electronic equipment, not only because of the immediate problems of electronic shorts to the system but also because of longer-term corrosive damage water can cause, alternative fire suppression methods have been sought. One of the more common alternative methods used was halon-based systems. Halon systems have been phased out because of environmental concerns surrounding the release of halon into the atmosphere, as it is a potent greenhouse gas.
Clean-Agent Fire Suppression Systems
Carbon dioxide (CO2) has been used as a fire suppression agent for a long time. The Bell Telephone Company used portable CO2 extinguishers in the early part of the 20th century. Carbon dioxide extinguishers attack all three necessary elements for a fire to occur. CO2 displaces oxygen so that the amount of oxygen remaining is insufficient to sustain the fire. It also provides some cooling in the fire zone and reduces the concentration of “gasified” fuel.
Argon extinguishes fire by lowering the oxygen concentration below the 15 percent level required for combustible items to burn. Argon systems are designed to reduce the oxygen content to about 12.5 percent, which is below the 15 percent needed for the fire but is still above the 10 percent required by the EPA for human safety.
Inergen, a product of Ansul Corporation, is composed of three gases: 52 percent nitrogen, 40 percent argon, and 8 percent carbon dioxide. In a manner similar to pure argon systems, Inergen systems reduce the level of oxygen to about 12.5 percent, which is sufficient for human safety but not sufficient to sustain a fire.
Another chemical used to phase out halon is FE-13, or trifluoromethane. This chemical was originally developed as a chemical refrigerant and works to suppress fires by inhibiting the combustion chain reaction. FE-13 is gaseous, leaves behind no residue that would harm equipment, and is considered safe to use in occupied areas. Other halocarbons are also approved for use in replacing halon systems, including FM-200 (heptafluoropropane), a chemical used as a propellant for asthma medication dispensers.

EXAM TIP The specific chemicals used for fire suppression are not testable; they are included here to provide you with the complete story for the workplace.
Handheld Fire Extinguishers
Although computer security professionals typically do not have much influence over the type of fire suppression system that their office includes, they do need to be aware of what type has been installed, what they should do in case of an emergency, and what they need to do to recover after the release of the system. One area that they can influence, however, is the type of handheld fire extinguisher that is located in their area.
Automatic fire suppression systems designed to discharge when a fire is detected are not the only systems you should be aware of. If a fire can be caught and contained before the automatic systems discharge, it can mean significant savings to the organization in terms of both time and equipment costs (including the recharging of the automatic system). Handheld extinguishers are common in offices, but the correct use of them must be understood or disaster can occur.
There are four different classes of fire, as shown in Table 17-1. Each class of fire has its own fuel source and method for extinguishing it. Class A systems, for example, are designed to extinguish fires with normal combustible material as the fire’s source. Water can be used in an extinguisher of this sort, since it is effective against fires of this type. Water, as we’ve discussed, is not appropriate for fires involving wiring or electrical equipment. Using a Class A extinguisher against an electrical fire not only will be ineffective but can result in additional damage. Some extinguishers are designed to be effective against more than one class of fire, such as the common ABC fire extinguishers. This is probably the best type of system to have in a data processing facility. All fire extinguishers should be easily accessible and should be clearly marked. Before anybody uses an extinguisher, they should know what type of extinguisher it is and what the source of the fire is. When in doubt, evacuate and let the fire department handle the situation.

Table 17-1 Types of Fire and Suppression Methods

EXAM TIP The type of fire distinguishes the type of extinguisher that should be used to suppress it. Remember that the most common type is the ABC fire extinguisher, which is designed to handle all types of fires except flammable-metal fires, which are rare.
Fire Detection Devices
An essential complement to fire suppression systems and devices are fire detection devices (fire detectors). Detectors may be able to detect a fire in its very early stages, before a fire suppression system is activated, and sound a warning that potentially enables employees to address the fire before it becomes serious enough for the fire suppression equipment to kick in.
There are several different types of fire detectors. One type, of which there are two varieties, is activated by smoke. The two varieties of smoke detector are ionization and photoelectric. A photoelectric detector is good for potentially providing advance warning of a smoldering fire. This type of device monitors an internal beam of light. If something degrades the light, for example by obstructing it, the detector assumes it is something like smoke and the alarm sounds. An ionization style of detector uses an ionization chamber and a small radioactive source to detect fast-burning fires. Shown in Figure 17-4, the chamber consists of two plates, one with a positive charge and one with a negative charge. Oxygen and nitrogen particles in the air become “ionized” (an ion is freed from the molecule). The freed ion, which has a negative charge, is attracted to the positive plate, and the remaining part of the molecule, now with a positive charge, is attracted to the negative plate. This movement of particles creates a very small electric current that the device measures. Smoke inhibits this process, and the detector will detect the resulting drop in current and sound an alarm.
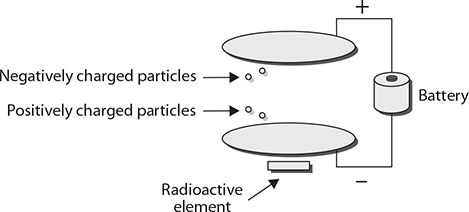
Figure 17-4 An ionization chamber for an ionization type of smoke detector
Both of these devices are often referred to generically as smoke detectors, and combinations of both varieties are possible. For more information on smoke detectors, see http://home.howstuffworks.com/home-improvement/household-safety/fire/smoke2.htm. As both of these devices are triggered by the interruption of a signal, without regard to why, they can give false alarms. They are unable to distinguish the difference between the smoke from a kitchen fire and burned toast.
Another type of fire detector is activated by heat. These devices also come in two varieties. Fixed-temperature or fixed-point devices activate if the temperature in the area ever exceeds some predefined level. Rate-of-rise or rate-of-increase temperature devices activate when there is a sudden increase in local temperature that may indicate the beginning stages of a fire. Rate-of-rise sensors can provide an earlier warning but are also responsible for more false warnings.
A third type of detector is flame activated. This type of device relies on the flames from the fire to provide a change in the infrared energy that can be detected. Flame-activated devices are generally more expensive than the other two types but can frequently detect a fire sooner.
Cable Locks
Portable equipment has a principal feature of being portable. This can also be a problem, as portable equipment—laptops, projectors, and the like—can be easily removed or stolen. Cable locks provide a simple means of securing portable equipment to furniture or another fixture in the room where the equipment resides. Cable locks can be used by road warriors to secure laptops from casual theft. They also can be used in open areas such as conference centers or rooms where portable equipment is exposed to a wide range of visitors.
Screen Filters
As discussed in Chapter 2, shoulder surfing involves the attacker directly observing an individual entering information on a form, keypad, or keyboard, usually to read passwords or other sensitive information. Given the close physical spacing on today’s aircraft and other public conveyances, if you are going to use a laptop, others are going to have access to see the screen. Screen filters are optical filters that limit the angle of viewability to a very narrow range, making it difficult for others to visually eavesdrop. Screen filters have a wide range of uses, from road warrior laptops, to kiosks, to receptionists’ computers, or places where sensitive data is displayed (medical data in medical environments).

EXAM TIP Some physical security equipment is used to secure aspects of mobile devices. Screen filters secure screens from observation, while cable locks prevent equipment theft. These are both preventative agents, and you should be ready to match them on the exam to specific threats, such as shoulder surfing or device theft.
Cameras
Video surveillance is typically done through closed-circuit television (CCTV). The use of CCTV cameras for surveillance purposes dates back to at least 1961, when cameras were installed in the London Transport train station. The development of smaller camera components and lower costs has caused a boon in the CCTV industry since then.
CCTV cameras are used to monitor a workplace for security purposes. These systems are commonplace in banks and jewelry stores, places with high-value merchandise that is attractive to thieves. As the expense of these systems dropped, they became practical for many more industry segments.
Traditional cameras are analog based and require a video multiplexer to combine all the signals and make multiple views appear on a monitor. IP-based cameras are changing that, as most of them are stand-alone units that are viewable through a web browser, such as the camera shown in Figure 17-5.

Figure 17-5 IP-based cameras leverage existing IP networks instead of needing a proprietary CCTV cable.
These IP-based systems add useful functionality, such as the ability to check on the building from the Internet. This network functionality, however, makes the cameras subject to normal IP-based network attacks. A DoS attack launched at the CCTV system just as a break-in is occurring is the last thing that anyone would want (other than the criminals). For this reason, IP-based CCTV cameras should be placed on their own separate network that can be accessed only by security personnel. The same physical separation applies to any IP-based camera infrastructure. Older time-lapse tape recorders are slowly being replaced with digital video recorders. While the advance in technology is significant, be careful if and when these devices become IP-enabled, since they will become a security issue, just like everything else that touches the network.
If you depend on the CCTV system to protect your organization’s assets, carefully consider camera placement and the type of cameras used. Different iris types, focal lengths, and color or infrared capabilities are all options that make one camera superior to another in a specific location.
Motion Detection
When monitoring an area for unauthorized activity, one potentially useful tool is a motion detector. In areas where there is little or no expected traffic, a motion detector can alert an operator to activity in an area. Motion detectors come in a variety of types, but most are based on infrared (heat) radiation and can detect the changes of a warm body moving. They can be tuned for size, ignoring smaller movement such as small animals in outdoor settings. Although not useful in busy office buildings during normal daily use, motion detectors can be useful during off-hours, when traffic is minimal. Motion detectors can be used to trigger video systems, so they do not record large amounts of “empty” activity. Video monitoring of the loading dock area in the back of the building can be triggered in this fashion, using the motion detector to turn on cameras whenever activity is occurring.
Logs
Physical security logs provide the same utility as computer logs do for a security investigation. They act as a record of what was observed at specific points in time. Having roving guards check in at various places across a shift via a log entry provides a record of the actual surveillance. Logs of visitors arriving and departing, equipment received and shipped out, and so forth all serve as a record of the physical happenings in a facility.
Remote sensing of badges and equipment utilizing RFID tags can create equipment move logs that include when, where, what, and who—all automatically. Advanced capabilities such as this make inventory of movable equipment easier as its location is tracked and it can be scanned remotely.

EXAM TIP Cameras, IR detection, motion detection, and logs are all methods associated with detection, and frequently after-the-fact detection at that. These devises and methods provide valuable attribution fact patterns, even when it is after the actual event.
Infrared Detection
Infrared (IR) radiation is not visible to the human eye, but can be used just like a light source to detect a range of things. Motion from living creatures can be seen because of the heat signatures of their bodies. Infrared detection is a technical means of looking for things that otherwise may not be noticed. At night, when it is dark, someone can hide in the shadows, but infrared light can point them out to IR-sensing cameras. Infrared detectors can sense differences in temperature, which can be from a person entering a room, even if not visible due to darkness. IR alarms are used extensively to monitor people movement in areas where there should be none.
Key Management
Physical locks have physical keys, and keeping track of who has what keys can be a chore. Add in master keys and maintaining a list of who has physical access to each space, and such tracking can quickly become a task requiring a software solution. Key management is the process of keeping track of where the keys are and who has access to what. A physical security environment that does not have a means of key management is not verifiably secure. Key management will be essential when, say, a server in a locked room goes missing and management wants to know “Who has keys that can give them access to that room?”
Chapter Review
In this chapter, you became acquainted with the principles of physical security controls, including environmental controls. The chapter began with lighting, signs, fencing, gates, and cages, all items designed to restrict or guide physical movement. From there the chapter moved into security guards, alarms, safes, secure cabinets, and protected distribution for cables. These elements further refine restrictions on movement and the ability for access to system components. The chapter then examined airgaps, mantraps, and Faraday cages.
Physical lock types, tokens/cards, and biometrics were discussed. Barricades and bollards closed up the core physical protection area. The chapter then moved into environmental controls, HVAC, hot and cold aisles, and fire suppression. The chapter closed with an examination of cable locks, screen filters, cameras, motion detectors, logs, infrared detection, and key management.
Questions
To help you prepare further for the CompTIA Security+ exam, and to test your level of preparedness, answer the following questions and then check your answers against the correct answers at the end of the chapter.
1. Why is physical security important to protecting data?
A. Physical access to data will negate the security advantages of the cloud.
B. Information resides on physical assets, linking physical and information security.
C. Social engineering can negate any information security controls.
D. None of the above.
2. Proper interior and exterior lighting is important because:
A. It can detect people who are where they don’t belong.
B. It shows who is in a restricted space.
C. It allows more people and activities to be observed.
D. It is needed for the use of closed-circuit television cameras.
3. Your organization has experienced multiple incidents of graffiti tagging and people loitering in the parking lot despite the chain-link fence surrounding it. What is the best solution to the issue?
A. No Trespassing signage
B. More guard stations
C. Additional external lighting
D. Change the chain-link fencing to anti-scale fencing
4. The supervisor in charge of the security guards wants to increase the guards’ awareness of information security and has asked you to provide a training session. List two things that would be included in your curriculum?
A. __________________
B. __________________
5. After a physical security incident, what critical data can security guards commonly provide?
A. Employee ID information
B. Access logs of who has entered and exited the building
C. Alarm codes
D. Blueprints showing unmonitored areas of the building
6. Alarms are effective only if which of the following is true?
A. They alert on abnormal conditions.
B. Every entrance is monitored with a sensor.
C. They are not tied to the information systems.
D. They are tuned to provide accurate and useful alerts.
7. You are implementing a test lab at your organization for early alpha software development. To prevent any of the development code from inadvertently getting put on production computers, what should you implement?
A. Airgap
B. Strict firewalls
C. Protected distribution
D. Patch management
8. What is the security benefit of a Faraday cage?
A. Prevents attack by EMP
B. Prevents illicit monitoring of Van Eck emissions
C. Works better than anti-scale fencing
D. Prevents stack overflows by EMI
9. The CSO is starting a project to revamp all physical security at the organization. Of particular interest to him are high-security locks on critical infrastructure, and he has asked you to create a PowerPoint presentation to justify the expense to management. What three features would you highlight in your presentation about high-security locks?
A. ______________
B. ______________
C. ______________
10. Biometrics are based upon which of the following?
A. The original fingerprint studies of the 1880s
B. Parts of the human body that are unique
C. The ability to rapidly scan biological markers
D. Advances in retinal scanning
11. What is a primary problem with biometrics?
A. Technically biometrics are difficult to implement
B. The human body changing over time
C. The ease with which biometrics are faked
D. Biometrics can’t be loaned or delegated
12. The token’s primary security advantage over metallic keys is ________________.
A. Tokens are revocable
B. Tokens can be copied for faster distribution
C. Tokens are bigger, and thus easier to find than a key
D. Tokens can be issued to all employees
13. Clean-agent fire suppression systems are designed to replace this traditional fire suppression element: ________________.
14. A fire involving which of the following is not covered by the traditional ABC handheld fire extinguisher?
A. Flammable liquids
B. Flammable metals
C. Cloth soaked in accelerant
D. A computer on fire
15. What should you do to protect your IP-based CCTV system from a DDoS attack?
A. Reconfigure your firewalls
B. Connect it to an intrusion detection system
C. Require multifactor authentication to access the CCTV system
D. Place all CCTV components on a separate network
Answers
1. B. Information resides on physical assets, linking physical security with the security of information.
2. C. Proper lighting allows more people and activities to be observed.
3. D. A change from chain-link fencing to anti-scale fencing to prevent intruders from climbing the fence is the best solution.
4. There are several things that you can discuss to assist guards’ information security knowledge, such as indicators of a network attack being all computers rebooting at once, several phones ringing at once, and strangers with laptops or other equipment sitting in a vehicle in the parking lot.
5. B. Guards commonly have logs of who has entered and exited a building.
6. D. Alarms are effective only if they are tuned to provide accurate and useful alerting information.
7. A. A lab environment can be airgapped from the rest of the network to prevent software from being accidentally copied to production machines.
8. B. A Faraday cage can prevent illicit monitoring of computer systems through Van Eck emissions.
9. High-security locks have many anti-intrusion features, so your presentation should highlight any three of the following: pick resistance, drill resistance, resistance to pounding it through the door, bump resistance, sidebars, magnetic keys, nontraditional pins, and key control.
10. B. Biometrics are based upon parts of the body that are unique, such as fingerprints, iris, retina, and others.
11. B. Some biometric features can change over time, or with medical conditions making them less reliable and forcing a re-identification phase to resync a user and their biometric.
12. The primary security advantage tokens have over metallic keys is the ability to revoke a key remotely.
13. The most traditional fire suppression agent is water, but that cannot be used on all fires and can cause damage to electrical equipment.
14. B. A fire involving flammable metals is not covered by a typical ABC fire extinguisher.
15. D. The CCTV system should be on a completely separate network, airgapped if possible, with only security personnel having access.