CHAPTER 20
Identity and Access Management Controls
In this chapter, you will
• Learn how to implement identity management controls
• Learn how to implement access management controls
One of the core tenets of computer security is the concept that all actions will be controlled via a system of approvals; accessing a resource, operating on a resource, and storing of an item all can only be performed by authorized parties. Identity and access management systems are the mechanisms by which this is accomplished. Identity systems establish a link between users and accounts in the system which represent the user during system operations. Access management controls work to manage what users can do with resources, which actions are allowed, which actions are denied. This chapter examines the specifics of these systems.
Certification Objective This chapter covers CompTIA Security+ exam objective 4.3, Given a scenario, implement identity and access management controls. This objective is a good candidate for performance-based questions, which means you should expect questions in which you must apply your knowledge of the topic to a scenario. The best answer to a question will depend upon specific details in the scenario preceding the question, not just the question. The questions may also involve tasks other than just picking the best answer from a list. Instead, they may involve actual simulations of steps to take to solve a problem.
Access Control Models
The term access control describes a variety of protection schemes. It sometimes refers to all security features used to prevent unauthorized access to a computer system or network. In this sense, it may be confused with authentication. More properly, access is the ability of a subject (such as an individual or a process running on a computer system) to interact with an object (such as a file or hardware device). Authentication, on the other hand, deals with verifying the identity of a subject.
To understand the difference, consider the example of an individual attempting to log in to a computer system or network. Authentication is the process used to verify to the computer system or network that the individual is who he claims to be. The most common method to do this is through the use of a user ID and password. Once the individual has verified his identity, access controls regulate what the individual can actually do on the system—just because a person is granted entry to the system does not mean that he should have access to all data the system contains.
Consider another example. When you go to your bank to make a withdrawal, the teller at the window will verify that you are indeed who you claim to be by asking you to provide some form of identification with your picture on it, such as your driver’s license. You might also have to provide your bank account number. Once the teller verifies your identity, you will have proved that you are a valid (authorized) customer of this bank. This does not, however, mean that you have the ability to view all information that the bank protects—such as your neighbor’s account balance. The teller will control what information, and funds, you can access and will grant you access only to the information that you are authorized to see. In this example, your identification and bank account number serve as your method of authentication and the teller serves as the access control mechanism.
In computer systems and networks, access controls can be implemented in several ways. An access control matrix provides the simplest framework for illustrating the process and is shown in Table 20-1. In this matrix, the system is keeping track of two processes, two files, and one hardware device. Process 1 can read both File 1 and File 2 but can write only to File 1. Process 1 cannot access Process 2, but Process 2 can execute Process 1. Both processes have the ability to write to the printer.
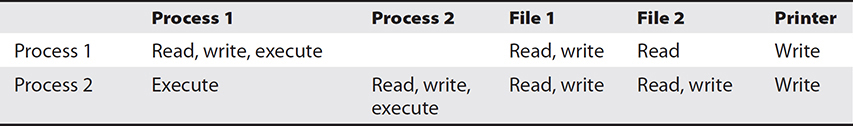
Table 20-1 An Access Control Matrix
While simple to understand, the access control matrix is seldom used in computer systems because it is extremely costly in terms of storage space and processing. Imagine the size of an access control matrix for a large network with hundreds of users and thousands of files. The actual mechanics of how access controls are implemented in a system varies, though access control lists (ACLs) are common. An ACL is nothing more than a list that contains the subjects that have access rights to a particular object. The list identifies not only the subject but the specific access granted to the subject for the object. Typical types of access include read, write, and execute, as indicated in the example access control matrix.
No matter what specific mechanism is used to implement access controls in a computer system or network, the controls should be based on a specific model of access. Several different models are discussed in security literature and listed under exam objective 4.3, including mandatory access control (MAC), discretionary access control (DAC), attribute-based access control (ABAC), role-based access control (RBAC), and rule-based access control (also RBAC).
MAC
A less frequently employed system for restricting access is mandatory access control (MAC). This system, generally used only in environments in which different levels of security classifications exist, is much more restrictive regarding what a user is allowed to do. Referring to the “Orange Book,” a mandatory access control is “a means of restricting access to objects based on the sensitivity (as represented by a label) of the information contained in the objects and the formal authorization (i.e., clearance) of subjects to access information of such sensitivity.” In this case, the owner or subject can’t determine whether access is to be granted to another subject; it is the job of the operating system to decide.

EXAM TIP Common information classifications include High, Medium, Low, Confidential, Private, and Public.
In MAC, the security mechanism controls access to all objects, and individual subjects cannot change that access. The key here is the label attached to every subject and object. The label will identify the level of classification for that object and the level to which the subject is entitled. Think of military security classifications such as Secret and Top Secret. A file that has been identified as Top Secret (has a label indicating that it is Top Secret) may be viewed only by individuals with a Top Secret clearance. It is up to the access control mechanism to ensure that an individual with only a Secret clearance never gains access to a file labeled as Top Secret. Similarly, a user cleared for Top Secret access will not be allowed by the access control mechanism to change the classification of a file labeled as Top Secret to Secret or to send that Top Secret file to a user cleared only for Secret information. The complexity of such a mechanism can be further understood when you consider today’s windowing environment. The access control mechanism will not allow a user to cut a portion of a Top Secret document and paste it into a window containing a document with only a Secret label. It is this separation of differing levels of classified information that results in this sort of mechanism being referred to as multilevel security.
Finally, just because a subject has the appropriate level of clearance to view a document does not mean that she will be allowed to do so. The concept of least privilege, or sometimes called “need to know,” which is a DAC concept (discussed next), also exists in MAC mechanisms. Least privilege means that a person is given access only to information that she needs in order to accomplish her job or mission.
DAC
Both discretionary access control (DAC) and mandatory access control are terms originally used by the military to describe two different approaches to controlling an individual’s access to a system. As defined by the “Orange Book,” a Department of Defense (DoD) document that at one time was the standard for describing what constituted a trusted computing system, DACs are “a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject.” While this might appear to be confusing “government-speak,” the principle is rather simple. In systems that employ DACs, the owner of an object can decide which other subjects can have access to the object and what specific access they can have. One common method to accomplish this is the permission bits used in Linux-based systems. The owner of a file can specify what permissions (read/write/execute) members in the same group can have and also what permissions all others can have. ACLs are also a common mechanism used to implement DAC.

EXAM TIP If you are trying to remember the difference between MAC and DAC, just remember that MAC is associated with multilevel security labels such as Top Secret and Secret, while DAC uses ACLs.
ABAC
Attribute-based access control (ABAC) is a form of access control based on attributes. These attributes can be in a wide variety of forms, such as user attributes, resource or object attributes, and environmental attributes. For instance, a doctor can access medical records, but only for patients to which she is assigned, or only when she is on shift. The major difference between ABAC and role-based access control is the ability to include Boolean logic in the access control decision.
Role-Based Access Control
ACLs can be cumbersome and can take time to administer properly. Another access control mechanism that has been attracting increased attention is role-based access control (RBAC). In this scheme, instead of each user being assigned specific access permissions for the objects associated with the computer system or network, each user is assigned a set of roles that he or she may perform. The roles are in turn assigned the access permissions necessary to perform the tasks associated with the role. Users will thus be granted permissions to objects in terms of the specific duties they must perform—not according to a security classification associated with individual objects.
Rule-Based Access Control
The first thing that you might notice is the ambiguity that is introduced with this access control method also using the acronym RBAC. Rule-based access control again uses objects such as ACLs to help determine whether access should be granted or not. In this case, a series of rules are contained in the ACL and the determination of whether to grant access will be made based on these rules. An example of such a rule is one that states that no employee may have access to the payroll file after hours or on weekends. As with MAC, users are not allowed to change the access rules, and administrators are relied on for this. Rule-based access control can actually be used in addition to or as a method of implementing other access control methods. For example, MAC methods can utilize a rule-based approach for implementation.

EXAM TIP Do not become confused between rule-based and role-based access controls, even though they both have the same acronym. The name of each is descriptive of what it entails and will help you distinguish between them.
Physical Access Control
Physical access control is the process of defining and enforcing who can have physical access to a system. Physical access control lists work in the physical world in the same way they work in the electronic world. Access lists define the group of individuals who are authorized to utilize a resource. Entry into a server room, access to equipment rooms, and keys for locks protecting sensitive areas are all examples of elements that require access control.
Many organizations use electronic access control systems to control the opening of doors. The use of proximity readers and contactless access cards provides user information to the control panel. Doorways are electronically controlled via electronic door strikes and magnetic locks. These devices rely on an electronic signal from the control panel to release the mechanism that keeps the door closed. These devices are integrated into an access control system that controls and logs entry into all the doors connected to it, typically through the use of access tokens. Security is improved by having a centralized system that can instantly grant or refuse access based upon access lists and the reading of a token that is given to the user. This kind of system also logs user access, providing nonrepudiation of a specific user’s presence in a controlled environment. The system will allow logging of personnel entry, auditing of personnel movements, and real-time monitoring of the access controls.
Proximity Cards
One method of electronic door control is through the use of proximity cards, or contactless access cards (such as the example shown in Figure 20-1). A keypad, a combination of the card and a separate PIN code, may also be required to open the door to a secure space.

Figure 20-1 Contactless access cards act as modern keys to a building.
Many organizations use electronic access control systems to control the opening of doors. The use of proximity readers and contactless access cards provides user information to the control panel. Doorways are electronically controlled via electronic door strikes and magnetic locks. These devices rely on an electronic signal from the control panel to release the mechanism that keeps the door closed. These devices are integrated into an access control system that controls and logs entry into all the doors connected to it, typically through the use of access tokens. Security is improved by having a centralized system that can instantly grant or refuse access based upon access lists and the reading of a token that is given to the user. This kind of system also logs user access, providing nonrepudiation of a specific user’s presence in a controlled environment. The system will allow logging of personnel entry, auditing of personnel movements, and real-time monitoring of the access controls.
Smart Cards
A smart card (also known as an integrated circuit card [ICC] or chip card) is a credit card-sized card with embedded integrated circuits that is used to provide identification security authentication. Smart cards can increase the physical security because they can carry long cryptographic tokens, too long to remember and too large a space to guess. Because of the manner in which they are employed and used, copying the number is not a practical option as well. Smart cards can find use in a variety of situations where you want to combine something you know (a pin or password) together with something you have (and can’t be duplicated, a smart card). Many standard corporate-type laptops come with smart card readers installed and their use is integrated into the Windows user access system.
Biometric Factors
Biometric factors are measurements of certain biological factors to identify one specific person from others. These factors are based on parts of the human body that are unique. The most well-known of these unique biological factors is the fingerprint. Fingerprint readers have been available for several years in laptops and other mobile devices, on keyboards, and as stand-alone USB devices.
However, many other biological factors can be used, such as the retina or iris of the eye, the geometry of the hand, and the geometry of the face. When these are used for authentication, there is a two-part process: enrollment and then authentication. During enrollment, a computer takes the image of the biological factor and translates it to a numeric value, called a template. When the user attempts to authenticate, the biometric feature is scanned by the reader, and the computer computes a value in the same fashion as the template, and then compares the numeric value being read to the one stored in the database. If they match, access is allowed. Since these physical factors are unique, theoretically only the actual authorized person would be allowed access.
In the real world, however, the theory behind biometrics breaks down. Tokens that have a digital code work very well because everything remains in the digital realm. A computer checks your code, such as 123, against the database; if the computer finds 123 and that number has access, the computer opens the door. Biometrics, however, take an analog signal, such as a fingerprint or a face, and attempt to digitize it, and it is then matched against the digits in the database. The problem with an analog signal is that it might not encode the exact same way twice. For example, if you came to work with a bandage on your chin, would the face-based biometrics grant you access or deny it? Because of this, the templates are more complex in a manner where there can be a probability of match, or closeness measurement.
Fingerprint Scanner
A fingerprint scanner measures the unique pattern of a person’s fingerprint and translates that pattern into a numerical value, or template, as discussed in the previous section. Fingerprint readers can be enhanced to assure that the pattern is a live pattern, one with circulating blood or other detectable biological activity, to prevent simple spoofing with a Play-Doh mold of the print. Fingerprint scanners are cheap to produce and have widespread use in mobile devices. One of the challenges of fingerprint scanners is that they don’t function if the user is wearing gloves (e.g., medical gloves) or has worn off their fingerprints through manual labor, as many involved in the sheetrock trade do through normal work.
Retinal Scanner
A retinal scanner examines blood vessel patterns in the back of the eye. Believed to be unique and unchanging, the retina is a readily detectable biometric. Retinal scanning does suffer from lack of user acceptance, as it involves a laser scanning the inside of the user’s eyeball, which raises some psychological issues for some users who are wary of letting a laser scan the inside of their eye. This detection requires the user to be right in front of the device for it to work. It is also more expensive because of the precision of the detector and the involvement of lasers and users’ vision.
Iris Scanner
An iris scanner works in a means similar to a retinal scanner in that it uses an image of a unique biological measurement, in this case the pigmentation associated with the iris of the eye. This can be photographed and measured from a distance, removing the psychological impediment of placing one’s eye up close to a scanner. The downside to being able to capture an iris scan at a distance is that it’s easy to do without a person’s knowledge, and even construct contact lenses that mimic a pattern. There are also some other issues associated with medical conditions such as pregnancy, and some diseases, which can be detected by changes in a person’s iris and if revealed would be a privacy violation.
Voice Recognition
Voice recognition is the use of unique tonal qualities and speech patterns to identify a person. Long the subject of sci-fi movies, this biometric has been one of the hardest to develop into a reliable mechanism, primarily because of problems with false acceptance and rejection rates, which will be discussed a bit later in the chapter.
Facial Recognition
Facial recognition was also mostly the stuff of sci-fi until it was integrated into various mobile phones. A sensor that recognizes when you move the phone in a position to see your face, coupled with a state of not logged in, turns on the forward-facing camera and the system looks for its enrolled owner. This system has proven to have fairly high discrimination, and works fairly well, with only one drawback. Another person can move the phone in front of the registered user and it can unlock; in essence, another user can activate the unlocking mechanism even when the user is unaware. The other minor drawback is that for certain transactions, such as positive identification for financial transactions, the position of the phone on an NFC location, together with the user’s face needing to be in a certain orientation with respect to the phone leads to awkward positions. Having to put your face in a proper position on the phone to identify you, while holding it against the counter height NFC credit card reader, can be awkward.
False Positives and False Negatives
Engineers who design biometric systems understand that if a system were set to exact checking, an encoded biometric might never grant access since the system might never scan the biometric exactly the same way twice. Therefore, most systems are designed to allow a certain amount of error in the scan, while not allowing too much. This leads to the concepts of false positives and false negatives. A false positive occurs when a biometric is scanned and allows access to someone who is not authorized—for example, two people who have very similar fingerprints might be recognized as the same person by the computer, which grants access to the wrong person. A false negative occurs when the system denies access to someone who is actually authorized—for example, a user at the hand geometry scanner forgot to wear a ring he usually wears and the computer doesn’t recognize his hand and denies him access.
What is desired is for the system to be able to differentiate the two signals, one being the stored value and the other being the observed value, in such a way that the two curves do not overlap. Figure 20-2 illustrates two probability distributions that do not overlap.
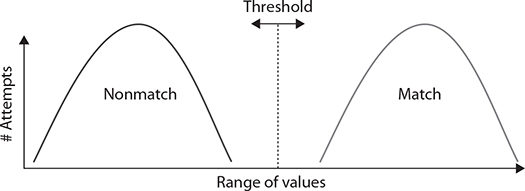
Figure 20-2 Ideal probabilities
For biometric authentication to work properly, and also be trusted, it must minimize the existence of both false positives and false negatives. But biometric systems are seldom that discriminating, and the curves tend to overlap, as shown in Figure 20-3. For detection to work, a balance between exacting and error must be created so that the machines allow a little physical variance—but not too much.
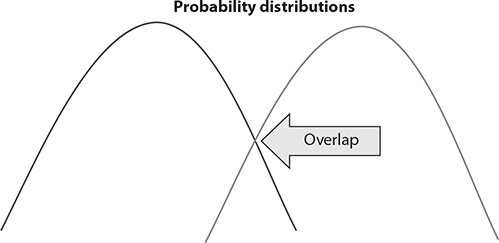
Figure 20-3 Overlapping probabilities
This leads us to acceptance and rejection rates.
False Acceptance Rate
The false acceptance rate (FAR) is just that, what level of false positives are going to be allowed in the system. A false acceptance/positive is demonstrated by the grayed-out area in Figure 20-4. In this area, the two curves overlap, and the decision has been set that at the threshold or better an accept signal will be given. Thus, if you are not a match, but your measured value falls on the upper end of the nonmatch curve, in the gray area, you will be considered a match, and hence become a false positive. Expressed as probabilities, the false acceptance rate is the probability that the system incorrectly identifies a match between the biometric input and the stored template value.

Figure 20-4 False acceptance rate
When selecting the threshold value, the designer must be cognizant of two factors: one is the rejection of a legitimate biometric, the area on the match curve below the threshold value. The second consideration is the acceptance of false positives. The more the curves overlap, the larger the problem for once a threshold is chosen, that number defines the FAR. Setting the threshold higher will decrease false positives but increase false negatives or rejections. This would increase the false rejection rate, discussed in the next section.
False Rejection Rate
The false rejection rate (FRR) is just that, what level of false negatives, or rejections, are going to be allowed in the system. A false rejection is demonstrated by the grayed-out area in Figure 20-5. In this section, the curves overlap, and the decision has been set that at the threshold or lower a reject signal will be given. Thus, if you are on the lower end of the match curve, in the gray area, you will be rejected, even if you should be a match. Expressed as probabilities, the false rejection rate is the probability that the system incorrectly rejects a legitimate match between the biometric input and the stored template value.

Figure 20-5 False rejection rate
When comparing the FAR and the FRR, one realizes that, in most cases, whenever the curves overlap, they are related. This brings up the issue of the crossover error rate. Both the FAR and the FRR are set by choosing the threshold value. This is done when the system is set up and reflects the choice of which error rate is more important. If you want to make it harder for a false positive, you will cause many failed authorizations of legitimate users as they will be seen by the system as on the other curve. If you want to make sure all legitimate users do not experience troubles during scans, then some unauthorized users will get accepted (false positives) as they will be interpreted by the system as being on the wrong curve based on where the threshold is set.
Crossover Error Rate
The crossover error rate (CER) is the rate where both accept and reject error rates are equal. This is the desired state for most efficient operation, and it can be managed by manipulating the threshold value used for matching. In practice, the values may not be exactly the same, but they will typically be close to each other. Figure 20-6 demonstrates the relationship between the FAR, FRR, and CER.
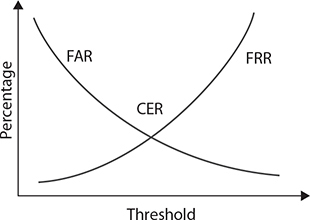
Figure 20-6 FRR, FAR, and CER compared
Biometrics Calculation Example
Assume we are using a fingerprint biometric system, and we have 1000 users. During the enrollment stage, 5 users were unable to enroll (the system could not establish a fingerprint signature/template for them). This means the system has a failure to enroll rate (FER) = 0.5 percent. This means only 995 users can use the system, and an alternative means needs to be in place for the users who cannot use the system.
During the testing of the 995 users, 50 users were rejected when the system matched their fingerprint against their enrollment fingerprint template. This makes the FRR = 5.02 percent.
Also, 25 users out of the 995 users were accepted by the system when the system matched their fingerprint against another user’s fingerprint template. This means the FAR = 2.51 percent
The lower the FAR and FRR, the better the system, and the ideal situation is setting the thresholds where the FAR and FRR are equal, the crossover error rate.

EXAM TIP Understand how to calculate FAR and FRR given data. Remember to include those that fail enrollment.
Tokens
An access token is a physical object that identifies specific access rights, and in authentication falls into the “something you have” factor. Your house key, for example, is a basic physical access token that allows you access into your home. Although keys have been used to unlock devices for centuries, they do have several limitations. Keys are paired exclusively with a lock or a set of locks, and they are not easily changed. It is easy to add an authorized user by giving the user a copy of the key, but it is far more difficult to give that user selective access unless that specified area is already set up as a separate key. It is also difficult to take access away from a single key or key holder, which usually requires a rekey of the whole system.
In many businesses, physical access authentication has moved to contactless radio frequency cards and proximity readers. When passed near a card reader, the card sends out a code using radio waves. The reader picks up this code and transmits it to the control panel. The control panel checks the code against the reader from which it is being read and the type of access the card has in its database. The advantages of this kind of token-based system include the fact that any card can be deleted from the system without affecting any other card or the rest of the system. In addition, all doors connected to the system can be segmented in any form or fashion to create multiple access areas, with different permissions for each one. The tokens themselves can also be grouped in multiple ways to provide different access levels to different groups of people. All of the access levels or segmentation of doors can be modified quickly and easily if building space is re-tasked. Newer technologies are adding capabilities to the standard token-based systems. Smart cards can also be used to carry identification tokens. The primary drawback of token-based authentication is that only the token is being authenticated. Therefore, the theft of the token could grant anyone who possesses the token access to what the system protects.
The risk of theft of the token can be offset by the use of multifactor authentication (described in Chapter 18). One of the ways that people have tried to achieve multifactor authentication is to add a biometric factor to the system. A less expensive alternative is to use hardware tokens in a challenge/response authentication process. In this way, the token functions as both a something-you-have and something-you-know authentication mechanism. Several variations on this type of device exist, but they all work on the same basic principles. The device has an LCD screen and may or may not have a numeric keypad. Devices without a keypad will display a password (often just a sequence of numbers) that changes at a constant interval, usually about every 60 seconds. When an individual attempts to log in to a system, he enters his own user ID number and then the number that is displayed on the LCD. These two numbers are either entered separately or concatenated. The user’s own ID number is secret, and this prevents someone from using a lost device. The system knows which device the user has and is synchronized with it so that it will know the number that should have been displayed. Since this number is constantly changing, a potential attacker who is able to see the sequence will not be able to use it later, since the code will have changed. Devices with a keypad work in a similar fashion (and may also be designed to function as a simple calculator). The individual who wants to log in to the system will first type his personal identification number into the calculator. He will then attempt to log in. The system will then provide a challenge; the user must enter that challenge into the calculator and press a special function key. The calculator will then determine the correct response and display it. The user provides the response to the system he is attempting to log in to, and the system verifies that this is the correct response. Since each user has a different PIN, two individuals receiving the same challenge will have different responses. The device can also use the date or time as a variable for the response calculation so that the same challenge at different times will yield different responses, even for the same individual.
Hardware
There are several forms of hardware tokens, from proximity cards and smart cards discussed earlier to Common Access Cards (CACs), USB tokens, and key fobs with RFID chips. These hardware components act as a token, being an authentication factor that typically takes the form of a physical or logical entity that the user must be in possession of to access their account or certain resources.
Most of these tokens are physical tokens that display a series of numbers that changes every 30 to 90 seconds, such as the token pictured in Figure 20-7 from Blizzard Entertainment. These act as one-time password generators, making them impossible to copy as the sequence is tied to each device independently. The displayed sequence of numbers must be entered when the user is attempting to log in or access certain resources. The ever-changing sequence of numbers is synchronized to a remote server such that when the user enters the correct username, password, and matching sequence of numbers, she is allowed to log in. Even if an attacker obtains the username and password, the attacker cannot log in without the matching sequence of numbers.

Figure 20-7 Token authenticator from Blizzard Entertainment
Software
Access tokens may also be implemented in software. Software tokens still provide two-factor authentication but don’t require the user to have a separate physical device on hand. Some tokens require software clients that store a symmetric key (sometimes called a seed record) in a secured location on the user’s device (laptop, desktop, tablet, and so on). Other software tokens use public key cryptography. Asymmetric cryptography solutions, such as public key cryptography, often associate a PIN with a specific user’s token. To log in or access critical resources, the user must supply the correct PIN. The PIN is stored on a remote server and is used during the authentication process so that if a user presents the right token, but not the right PIN, the user’s access can be denied. This helps prevent an attacker from gaining access if he gets a copy of or gains access to the software token. The most common form of software tokens is in identifying a specific device in addition to a user, in that the software token is on the device and the user supplies the rest of the details needed to demonstrate authenticity.
HOTP/TOTP
HMAC-based One-Time Password (HOTP) is an algorithm that can be used to authenticate a user in a system by using an authentication server. (HMAC stands for Hash-based Message Authentication Code.) It is defined in RFC 4226, dated December 2005. The Time-based One-Time Password (TOTP) algorithm is a specific implementation of an HOTP that uses a secret key with a current timestamp to generate a one-time password. It is described in RFC 6238, dated May 2011.

EXAM TIP Tokens represent 1) something you have with respect to authentication as well as 2) a device that can store more information than a user can memorize, which makes them very valuable for access control. The details in the scenario preceding a question will provide the necessary criteria to pick the best token method for the question.
Certificate-Based Authentication
Certificate-based authentication is a means of proving identity via the presentation of a certificate. Certificates offer a method of establishing authenticity of specific objects such as an individual’s public key or downloaded software. A digital certificate is a digital file that is sent as an attachment to a message and is used to verify that the message did indeed come from the entity it claims to have come from. Using a digital certificate is a verifiable means of establishing possession of an item, specifically the certificate. When the certificate is held within a store that prevents tampering or extraction, then this becomes a reliable means of identification, especially when combined with an additional factor such as something you know or a biometric.
PIV/CAC/Smart Card
The U.S. federal government has several smart card solutions for identification of personnel. The Personal Identity Verification (PIV) card is a U.S. government smart card that contains the cardholder’s credential data used to determine access to federal facilities and information systems. The Common Access Card (CAC) is a smart card used by the U.S. Department of Defense (DoD) for active-duty military, Selected Reserve members, DoD civilians, and eligible contractors. Like the PIV card, it is used for carrying the cardholder’s credential data, in the form of a certificate, used to determine access to federal facilities and information systems.
IEEE 802.1x
IEEE 802.1X is an authentication standard that supports port-based authentication services between a user and an authorization device, such as an edge router. IEEE 802.1X is used by all types of networks, including Ethernet, Token Ring, and wireless. This standard describes methods used to authenticate a user prior to granting access to a network and the authentication server, such as a RADIUS server. 802.1X acts through an intermediate device, such as an edge switch, enabling ports to carry normal traffic if the connection is properly authenticated. This prevents unauthorized clients from accessing the publicly available ports on a switch, keeping unauthorized users out of a LAN. Until a client has successfully authenticated itself to the device, only Extensible Authentication Protocol over LAN (EAPoL) traffic is passed by the switch.

CAUTION One security issue associated with 802.1X is that the authentication occurs only upon initial connection, and that another user can insert themselves into the connection by changing packets or using a hub. The secure solution is to pair 802.1X, which authenticates the initial connection, with a VPN or IPsec, which provides persistent security.

EXAM TIP Understanding how public key cryptography is used to establish trust for identities is covered partly in this chapter and partly in Chapter 29. But to answer questions regarding objective 4.3, you need to understand both chapters, as Chapter 29 covers the limitations of certificates.
File System Security
File systems need a method of applying security, to prevent unauthorized access and unauthorized alterations. File system security is the set of mechanisms and processes employed to ensure this critical function. Using a combination of file storage mechanisms, along with access control lists and access control models, provides a means by which you can secure your file systems. You need a file system capable of supporting user-level access differentiation, something NTFS does, but FAT32 does not. Next, you need to have a functioning access control model, such as MAC, DAC, or ABAC, as previously described in this chapter. Then you need a system to grant users permissions to access and modify the files, which can be handled by the OS, although administering and maintaining this can be a challenge. Modern OSs that are employed in enterprise settings, specifically NTFS for Windows, are designed to enable file system security. This is done through the inner workings of the file system and is invisible to the user as users will not even see files they cannot access.
Database Security
Database security is the application of security functions, who can access what, inside a database system. Data security is a significant concern for many enterprises, as the data in the databases represents valuable information assets. Major database engines have built-in access control provisions and encryption capabilities. Access control is managed by named users and defined permissions, all managed inside the database system. The results are enforced via encryption, which also provides protection should the datafiles be copied or released. This can provide the desired levels of confidentiality and integrity to the contents of the database. The advantage to these encryption schemes is that they can be tailored to the data structure, protecting the essential columns while not impacting columns that are not sensitive. Properly employing database encryption requires that the data schema and its security requirements be designed into the database implementation. The advantage is in better protection against any database compromise, and the performance hit is typically negligible with respect to other alternatives.
Chapter Review
In this chapter, you became acquainted with access control methods for securing information in the enterprise. The chapter opened with an examination of the major access control models, including MAC, DAC, ABAC, role-based, and rule-based access control. It next addressed physical access control through the use of proximity cards and smart cards.
The discussion of biometric factors included both factors and usage. You learned about several different biometric technologies: fingerprint scanning, retinal scanning, iris scanning, voice recognition, and facial recognition. The methods and analytics covered included false positive and false negatives, false acceptance rate, false rejection rate, and the crossover error rate, and you were given an example showing how these factors are interrelated.
The chapter continued with an examination of various tokens used in access control, including hardware and software options, as well as HOTP/TOTP forms of one-time password generators. Certificate-based authentication, including its use in PIV/CAC and smart cards as well as 802.1x, was presented. The chapter concluded with an examination of file system security and database security.
Questions
To help you prepare further for the CompTIA Security+ exam, and to test your level of preparedness, answer the following questions and then check your answers against the correct answers at the end of the chapter.
1. During a visit to a hosting center where your organization keeps some offsite servers, you see a door with an odd-looking panel next to it. You see people approaching the panel and placing their eyes into a hooded viewer. A few seconds after they’ve done this, the door unlocks. What type of biometric scanner might this be?
A. Voice recognition scanner
B. Retinal scanner
C. Fingerprint scanner
D. Facial recognition scanner
2. You’ve spent the last week tweaking a fingerprint scanning solution for your organization. Despite your best efforts, roughly 1 in 50 attempts will fail even if the user is using the correct finger and their fingerprint is in the system. Your supervisor says 1 in 50 is “good enough” and tells you to move onto the next project. Your supervisor just defined which of the following for your fingerprint scanning system?
A. False rejection rate
B. False acceptance rate
C. Critical threshold
D. Failure acceptance criteria
3. Which of the following algorithms uses a secret key with a current timestamp to generate a one-time password?
A. Hash-based Message Authentication Code
B. Date-hashed Message Authorization Password
C. Time-based One-Time Password
D. Single sign-on
4. Your organization needs a system for restricting access to files based on the sensitivity of the information in those files. You might suggest which of the following access control systems?
A. Discretionary access control
B. Mandatory access control
C. Confidential access control
D. File-based access control
5. Which of the following describes a major difference between NTFS and FAT32 file systems?
A. NTFS supports user-level access differentiation.
B. FAT32 supports group-level access differentiation.
C. FAT32 natively encrypts files and directories.
D. NTFS logs all file access using secure tokens.
6. Your organization has grown too large to support assigning permissions to users individually. Within your organization, you have large groups of users who perform the same duties and need the same type and level of access to the same files. Rather than assigning individual permissions, your organization may wish to consider using which of the following access control methods?
A. Group-based access control
B. Shift-based access control
C. Role-based access control
D. File-based access control
7. With regard to authentication, an access token falls into which factor category?
A. Something you are
B. Something you have
C. Something you know
D. Something you see
8. Which of the following is NOT a common form of hardware token?
A. Proximity card
B. Common Access Card
C. USB token
D. Iris scan
9. A client of yours wants a system that will allow them to verify that messages came from specific individuals. In other words, they want to make sure that if a message purports to come from Sally, it really came from Sally. What method of establishing authenticity might you suggest they use?
A. Digital certificates
B. One-time passwords
C. Software tokens
D. Fingerprint scans
10. The hospital client you are working with needs to do a better job restricting access to patient records. They want doctors to have access only to records for their patients and only when the doctors are in the hospital. What type of access control method might work well in this situation?
A. Role-based access control
B. Mandatory access control
C. Discretionary access control
D. Attribute-based access control
11. While depositing cash from a charity fundraiser at a local bank, you notice bank employees are holding up cards next to a panel near a door. A light on the panel turns green and the employees are able to open the door. The light on the panel is normally red. What type of electronic door control is this bank using?
A. Iris scanner
B. Hardware tokens
C. Proximity cards
D. Symmetric key tokens
12. Your colleague is telling you a story she heard about a way to trick fingerprint scanners using gummy bears. She heard that if you press a gummy bear against an authorized user’s finger, you can then use that gummy bear as their fingerprint to fool a fingerprint scanner. If this works, the result is an example of which of the following?
A. False negative
B. False positive
C. Crossover positive
D. Crossover negative
13. The HR department in your organization wants to restrict access to the payroll file such that no one can access the payroll file outside of normal business hours (M–F, 7 A.M. to 6 P.M.). What type of access control method are they asking for?
A. Rule-based access control
B. Mandatory access control
C. Physical access control
D. Restrictive access control
14. When designing and tweaking biometric systems, the point where both the accept and reject error rates are equal is known as which of the following?
A. Crossover acceptance rate
B. Accept-reject overlap rate
C. Crossover error rate
D. Overlap acceptance rate
15. Which of the following is a smart card identification typically used by the U.S. Department of Defense?
A. Personal Identity Verification card
B. Common Access Card
C. Symmetric Token Card
D. Proximity Verification Card
Answers
1. B. This is most likely a retinal scanner. Retinal scanners examine blood vessel patterns in the back of the eye. Retinal scanning must be done at short distances; the user has to be right at the device for it to work.
2. A. Your supervisor just defined the false rejection rate (FRR) for your system. The FRR is the level of false negatives, or rejections, that are going to be allowed in the system. In this case your supervisor is willing to accept 1 false rejection for every 50 attempts.
3. C. The Time-based One-Time Password (TOTP) algorithm is a specific implementation of an HOTP that uses a secret key with a current timestamp to generate a one-time password.
4. B. Mandatory access control (MAC) is a system used in environments with different levels of security classifications. Access to objects (like files) is based on the sensitivity of the information contained in those objects and the authorization of the user to access information with that level of sensitivity.
5. A. NTFS supports user-level access differentiation and allows you to assign user permissions to files and directories.
6. C. Your organization could consider role-based access control. In role-based access control, instead of each user being assigned specific access permissions for the objects associated with the computer system or network, each user is assigned a set of roles that he or she may perform. The roles are in turn assigned the access permissions necessary to perform the tasks associated with the role. Users will thus be granted permissions to objects in terms of the specific duties they must perform—not according to a security classification associated with individual objects.
7. B. An access token is a physical object that identifies specific access rights, and in authentication falls into the “something you have” factor category.
8. D. An iris scan would be considered a biometric technique and is not a hardware token. A hardware token is a physical item the user must be in possession of to access their account or certain resources.
9. A. You might suggest they consider digital certificates. A digital certificate is a digital file that is sent as an attachment to a message and is used to verify that the message did indeed come from the entity it claims to have come from.
10. D. The hospital should consider using attribute-based access control (ABAC), a form of access control based on attributes. These attributes can be in a wide variety of forms, such as user attributes, resource or object attributes, and environmental attributes. For instance, a doctor can access medical records, but only for patients to which he is assigned, or only when he is on shift. The major difference between ABAC and role-based access control is the ability to include Boolean logic in the access control decision.
11. C. The bank employees are using proximity cards, contactless access cards that provide information to the electronic door control system. Proximity cards just need to be close enough to the scanner to work—they do not need to actually touch the scanner.
12. B. This is an example of a false positive. A false positive occurs when a biometric is scanned and allows access to someone who is not authorized.
13. A. The HR department is looking for rule-based access control, which uses objects such as ACLs to help determine whether access should be granted or not. In this case, a series of rules are contained in the ACL and the determination of whether to grant access will be made based on these rules.
14. C. The crossover error rate (CER) is the rate where both accept and reject error rates are equal. This is the desired state for most efficient operation of a biometric system, and it can be managed by manipulating the threshold value used for matching.
15. B. The Common Access Card (CAC) is a smart card identification used by the U.S. Department of Defense (DoD) for active-duty military, Selected Reserve members, DoD civilians, and eligible contractors.