CHAPTER 23
Incident Response, Disaster Recovery, and Continuity of Operations
In this chapter, you will
• Understand the incident response process
• Learn the incident response procedures
• Explore disaster recovery preparation
• Examine the process of continuity of operations
Normal operations in an IT enterprise include preparing for when things go wrong. One aspect of things going wrong is when things are not operating correctly, for reasons unknown, and the incident response process is used to determine the what, why, and where of the problem. A bigger problem is a disaster, where disaster recovery is the pressing issue, as well as continuity of operations. Each of these situations is one that requires preparation and readiness for the enterprise to navigate all of the complexities of these types of operations. This chapter looks at the concepts and procedures behind these specialized operations.
Certification Objective This chapter covers CompTIA Security+ exam objectives 5.4, Given a scenario, follow incident response procedures, and 5.6, Explain disaster recovery and continuity of operation concepts.
Objective 5.6 is a good candidate for performance-based questions, which means you should expect questions in which you must apply your knowledge of the topic to a scenario. The best answer to a question will depend upon specific details in the scenario preceding the question, not just the question. The questions may also involve tasks other than just picking the best answer from a list. Instead, you may be instructed to order things on a diagram, put options in rank order, match two columns of items, or perform a similar task.
Incident Response Plan
An incident response plan describes the steps an organization performs in response to any situation determined to be abnormal in the operation of a computer system. The causes of incidents are many, from the environment (storms), to errors on the part of users, to unauthorized actions by unauthorized users, to name a few. Although the causes may be many, the results can be classified into classes. A low-impact incident may not result in any significant risk exposure, so no action other than repairing the broken system is needed. A moderate-risk incident will require greater scrutiny and response efforts, and a high-level risk exposure incident will require the greatest scrutiny and response efforts. To manage incidents when they occur, an IT team needs to create an incident response plan that includes a table of guidelines to assist in determining the level of response.
Two major elements play a role in determining the level of response. Information criticality is the primary determinant, and this comes from the data classification and the quantity of data involved. The loss of one administrator password is less serious than the loss of all of them and thus requires a lower level of response. The second factor is how the incident potentially affects the organization’s operations. A series of breaches, whether minor or not, indicates a pattern that can have public relations and regulatory issues.
The incident response plan will cover a wide range of items, which are covered in the next several sections. Although an incident response plan may cover more items in a given enterprise, the Security+ objectives examine incident types and category definitions, roles and responsibilities of personnel, reporting and escalation requirements, cyber-incident response teams, and exercising of the plan.
Documented Incident Types/Category Definitions
To assist in the planning of incident responses and to group the myriad of possible incidents into a manageable set of categories, one step of the incident response planning process is the documentation of incident types/category definitions. Documented incident types/category definitions provide planners and responders with a set number of preplanned scripts that can be applied quickly, minimizing repetitive approvals and process flows. Examples of how categories are defined include items such as interruption of service, malicious communication, data exfiltration, malware delivery, phishing attack, and so on, although this list will be customized to meet the IT needs of each organization.
As this is customized to meet the IT needs of the organization, their onus is on the security group to develop the details for the different types of incident response categories and the materials and procedures to be used in each type. Doing this work before an incident is easy, as there is no time crunch of the actual incident pushing you at every step. The amount of work scales with the size of the IT organization and the services they are providing to the enterprise, but in all cases it is a doable task.
Roles and Responsibilities
A critical step in the incident response planning process is to define the roles and responsibilities of the incident response team members. These roles and responsibilities may vary slightly based on the identified categories of incident, but defining them before an incident occurs empowers the team to perform the necessary tasks during the time-sensitive aspects of an incident. Permissions to cut connections, change servers, and start/stop services are common examples of actions that are best defined in advance to prevent time-consuming approvals during an actual incident.
There are several specific roles that are unique to all IR teams, the team leader, the team communicator, and an appropriate bevvy of SMEs. The team leader manages the overall IR process, so they need to be a member of management so they can navigate the corporate chain of command. The team communicator is the spokesperson for the team to all other groups, inside and outside the company. IR team members are typically SMEs, and their time is valuable and should be spent on task. The team communicator shields these members from the time-consuming press interview portion as much as possible.
Reporting Requirements/Escalation
Planning the desired reporting requirements including escalation steps is an important part of the operational plan for an incident. Who will talk for the incident and to whom, and what will they say? How does the information flow? Who needs to be involved? When does the issue escalate to higher levels of management? These are all questions best handled in the calm of a pre-incident planning meeting where the procedures are crafted rather than on the fly as an incident is occurring.
Reporting requirements can refer to industry, regulatory, and statutory requirements in addition to internal communications. Understanding the reporting requirements to external entities is part of the responsibility of the communications lead on the team. Having the correct information in the hands of the correct people at the correct time is an essential part of reporting, and a prime responsibility of the communications’ lead on the team.
Cyber-Incident Response Teams
The cyber-incident response team is composed of the personnel who are designated to respond to an incident. The incident response plan should identify the membership and backup members, prior to an incident occurring. Once an incidence response begins, trying to find personnel to do tasks only slows down the function, and in many cases would make it unmanageable. Whether a dedicated team or a group of situational volunteers, the planning aspect of incident response needs to address the topic of who is on the team and what are their duties.
Management needs to appoint the team members and ensure that they have time to be prepared for service. The team leader is typically a member of management who fully understands both the enterprise IT environment and IR process, for their job is to lead the team with respect to the process. Subject matter experts on the various systems that are involved provide the actual working portion of the team, often in concert with operational IT personnel for each system. The team is responsible for all phases of the incident response process, which is covered in the next section of this chapter.
Exercise
One really doesn’t know how well a plan is crafted until it is tested. Exercises come in many forms and functions, and doing a tabletop exercise where planning and preparation steps are tested is an important final step in the planning process. Having a process and a team is not enough unless the team has practiced the process on the systems of the enterprise.

EXAM TIP If given a scenario, the details of the scenario will point to the appropriate part of the planning process. Pay attention to the details for the best answer.
Incident Response Process
The incident response process is the set of actions security personnel perform in response to a wide range of triggering events. These actions are wide and varied, as they have to deal with a wide range of causes and consequences. Incident response activities at times are closely related to other IT activities involving IT operations. Incident response activities can be similar to disaster recovery and business continuity operations. Incident response activities are not performed in a vacuum, but rather are intimately connected to many operational procedures, and this connection is key to overall system efficiency.

EXAM TIP Know the six phases of the incident response process and the order in which they are performed: preparation, identification, containment, eradication, recovery, and lessons learned.
Preparation
Preparation is the phase of incident response that occurs before a specific incident. Preparation includes all the tasks needed to be organized and ready to respond to an incident. Through the use of a structured framework coupled with properly prepared processes, incident response becomes a manageable task. Without proper preparation, this task can quickly become impossible or intractably expensive. Successful handling of an incident is a direct result of proper preparation. Items done in preparation are things like ensuring the correct data events are being logged, that reporting of potential incidents is happening, that people are trained with respect to IR process and their personal responsibilities.
Identification
Identification is the process where a team member suspects that a problem is bigger than an isolated incident and notifies the incident response team for further investigation. An incident is defined as a situation that departs from normal, routine operations. Whether an incident is important or not is the first point of decision as part of an incident response process. A single failed login is technically an incident, but if it is followed by a correct login, then it is not of any consequence. In fact, this could even be considered as normal. But 10,000 failed attempts on a system, or failures across a large number of accounts, are distinctly different and may be worthy of further investigation. The act of identification is coming to a decision that the information related to the incident is worthy of further investigation by the IR team.
Identification can be done by many on the IT team, from the help desk, to admins, to database personnel, in essence anyone who finds something out of the ordinary that may be a real problem. Some training is required to prevent false alarms, a single failed file access for instance, or a server that resets unexpectedly, these things happen and probably are not a cause for IR alarm. But when the single incidents become multiple incidents, then an investigation may be warranted and the conditions should be identified as a possible IR issue.
A key first step is in the processing of information and the determination of whether or not to invoke incident response processes. Incident information can come from a wide range of sources, including logs, employees, help desk calls, system monitoring, security devices, and more. The challenge is to detect that something other than simple common errors that are routine is occurring. When evidence accumulates, or in some cases specific items such as security device logs indicate a potential incident, the next step is to escalate the situation to the incident response team.
The IR team examines the information, gathering additional information if necessary to determine the cause of the incident. If it meets the defined thresholds of the organization, an incident will be logged and fully investigated. Whatever the root cause, if it is truly more than a random error, the next step is containment.
Containment
Once the IR team has determined that an incident has in fact occurred and requires a response, their first step is to contain the incident and prevent its spread. For example, if the incident involves a virus or worm that is attacking database servers, then protecting uninfected servers is paramount. Containment is the set of actions taken to constrain the incident to the minimal number of machines. This preserves as much of production as possible and ultimately makes handling the incident easier. This can be complex, for in many cases, containing the problem requires fully understanding the problem, its root cause, and the vulnerabilities involved.
Eradication
Once the IR team has contained a problem to a set footprint, the next step is to eradicate the problem. Eradication involves removing the problem, and in today’s complex system environment, this may mean rebuilding a clean machine. A key part of operational eradication is the prevention of reinfection. Presumably, the system that existed before the problem occurred would be prone to a repeat infection, and thus this needs to be specifically guarded against. One of the strongest value propositions for virtual machines is the ability to rebuild quickly, making the eradication step relatively easy.
Recovery
After the issue has been eradicated, the recovery process begins. At this point, the investigation is complete and documented. Recovery is the process of returning the asset into the business function and restoration of normal business operations. Eradication, the previous step, removed the problem, but in most cases the eradicated system will be isolated. The recovery process includes the steps necessary to return the systems and applications to operational status. After recovery, the team moves to document the lessons learned from the incident.
Lessons Learned
A post-mortem session should collect lessons learned and assign action items to correct weaknesses and to suggest ways to improve. To paraphrase a famous quote, those who fail to learn from history are destined to repeat it. The lessons learned phase serves two distinct purposes. First is to document what went wrong and allowed the incident to occur in the first place. Failure to correct this means a sure repeat. Second is to examine the incident response process itself. Where did it go well, where were the problems, and how can it be improved? Continuous improvement of the actual incident response process is an important task.

EXAM TIP Two main elements have been covered and they have overlap. Incident response planning and the actual incident response process are multistep items that can easily generate questions. Be sure to pay attention to what aspect, planning or process, the question belongs to, and then what aspect of that topic. Step one, determine if the question is concerning the planning or IR process. Then pick the correct phase.
Disaster Recovery
Many types of disasters, whether natural or caused by people, can stop your organization’s operations for some length of time. Such disasters are unlike the threats to your computer systems and networks, because the events that cause the disruption are not specifically aimed at your organization. This is not to say that those other threats won’t disrupt operations—they can, and industrial espionage, hacking, disgruntled employees, and insider threats all must be considered. The purpose of this section is to point out additional events that you may not have previously considered.
The amount of time your organization’s operations are disrupted depends in part on how prepared it is for a disaster and what plans are in place to mitigate the effects of a disaster. Disaster recovery is the process that the organization uses to recover from events that disrupt normal operations. Any of the events in Table 23-1 could cause a disruption in operations.
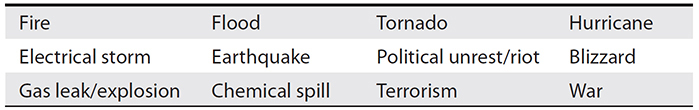
Table 23-1 Common Causes of Disasters
Fortunately, these types of events do not happen very often. It is more likely that business operations will be interrupted due to employee error (such as accidental corruption of a database, or unplugging a system to plug in a vacuum cleaner—an event that has occurred at more than one organization). A good disaster recovery plan will prepare your organization for any type of organizational disruption.
When disaster occurs, it is typically too late to begin the planning of a response. The following sections, “Recovery Sites,” “Hot Sites,” “Warm Sites,” and “Cold Sites,” provides details needed to make appropriate preparations.
Recovery Sites
Related to the location of backup storage is where the restoration services will be located. If the organization has suffered physical damage to its facility, having offsite data storage is only part of the solution. This data will need to be processed somewhere, which means that computing facilities similar to those used in normal operations are required. These sites are referred to as recovery sites. The recovery problem can be approached in a number of ways, including hot sites, warm sites, and cold sites.
Hot Sites
A hot site is a fully configured environment, similar to the normal operating environment that can be operational immediately or within a few hours depending on its configuration and the needs of the organization.
Warm Sites
A warm site is partially configured, usually having the peripherals and software but perhaps not the more expensive main processing computer. It is designed to be operational within a few days.
Cold Sites
A cold site will have the basic environmental controls necessary to operate but few of the computing components necessary for processing. Getting a cold site operational may take weeks.

EXAM TIP Alternate sites are highly tested on the CompTIA Security+ exam. It is also important to know whether the data is available or not at each location. For example, a hot site has duplicate data or a near-ready backup of the original site. A cold site has no current or backup copies of the original site data. A warm site has backups, but they are typically several days or weeks old.
Order of Restoration
Part of the planning for a disaster is to decide the order of restoration, which systems should be restored first, second, and ultimately last. There are a couple of distinct factors to consider. First are dependencies. Any system that is dependent upon another for proper operation might as well wait in line to be restored until the prerequisite services are up and running. The second factor is criticality to the enterprise. The most critical service should be brought back up first.
Backup Concepts
A key element in business continuity/disaster recovery (BC/DR) plans is the availability of backups. This is true not only because of the possibility of a disaster but also because hardware and storage media will periodically fail, resulting in loss or corruption of critical data. An organization might also find backups critical when security measures have failed and an individual has gained access to important information that may have become corrupted or at the very least can’t be trusted. Data backup is thus a critical element in these plans, as well as in normal operation. There are several factors to consider in an organization’s data backup strategy:
• How frequently should backups be conducted?
• How extensive do the backups need to be?
• What is the process for conducting backups?
• Who is responsible for ensuring backups are created?
• Where will the backups be stored?
• How long will backups be kept?
• How many copies will be maintained?
Keep in mind that the purpose of a backup is to provide valid, uncorrupted data in the event of corruption or loss of the original file or the media where the data was stored. Depending on the type of organization, legal requirements for maintaining backups can also affect how it is accomplished.
There are four main forms of backups: full, incremental, differential, and snapshots. Each of these has advantages and disadvantages in terms of time to back up and restore as well as complexity. These are described in the coming sections.
Understanding the purpose of the archive bit is important when you read about the backup types. The archive bit is used to indicate whether a file has (1) or has not (0) changed since the last backup. The bit is set (changed to a 1) if the file is modified, or in some cases, if the file is copied, the new copy of the file has its archive bit set. The bit is reset (changed to a 0) when the file is backed up. The archive bit can be used to determine which files need to be backed up when using methods such as the differential backup method.

EXAM TIP When learning the following backup types, be sure to pay attention to details as to how many backups are needed to restore. A typical exam question “With this type of backup (differential or incremental) and a seven-day backup scheme, how many backup tapes are needed for a restore?” is not a simple memorization, for you need the details from the scenario to answer. Also know the “order of restoration” of the backups.
Differential
In a differential backup, only the files that have changed since the last full backup was completed are backed up. This also implies that periodically a full backup needs to be accomplished. The frequency of the full backup versus the interim differential backups depends on your organization and needs to be part of your defined strategy. Restoration from a differential backup requires two steps: the last full backup first needs to be loaded, and then the last differential backup performed can be applied to update the files that have been changed since the full backup was conducted. Again, this is not a difficult process, but it does take some time. The amount of time to accomplish the periodic differential backup, however, is much less than that for a full backup, and this is one of the advantages of this method. Obviously, if a lot of time has passed between differential backups, or if most files in your environment change frequently, then the differential backup does not differ much from a full backup. It should also be obvious that to accomplish the differential backup, the system has to have a method to determine which files have been changed since some given point in time. The archive bit is not cleared in a differential backup since the key for a differential is to back up all files that have changed since the last full backup.
Incremental
The incremental backup is a variation on a differential backup, with the difference being that instead of copying all files that have changed since the last full backup, the incremental backup backs up only files that have changed since the last full or incremental backup occurred, thus requiring fewer files to be backed up. With incremental backups, even less information will be stored in each backup. Just as in the case of the differential backup, the incremental backup relies on the occasional full backup being accomplished. After that, you back up only files that have changed since the last backup of any sort was conducted. To restore a system using this type of backup method requires quite a bit more work. You first need to go back to the last full backup and reload the system with this data. Then you have to update the system with every incremental backup that has occurred since the full backup. The advantage of this type of backup is that it requires less storage and time to accomplish. The disadvantage is that the restoration process is more involved. Assuming that you don’t frequently have to conduct a complete restoration of your system, however, the incremental backup is a valid technique. An incremental backup will clear the archive bit.
Snapshots
A snapshot is a copy of a virtual machines at a specific point in time. A snapshot is a created by copying the files that store the virtual machine. One of the advantages of a virtual machine over a physical machine is the ease with which the virtual machine can be backed up and restored—the ability to revert to an earlier snapshot is as easy as clicking a button and waiting for the machine to be restored via a change of the files.
Full
The easiest type of backup to understand is the full backup. In a full backup, all files and software are copied onto the storage media. Restoration from a full backup is similarly straightforward—you must copy all the files back onto the system. This process can take a considerable amount of time. Consider the size of even the average home PC today, for which storage is measured in tens and hundreds of gigabytes. Copying this amount of data takes time. In a full backup, the archive bit is cleared.

EXAM TIP The amount of data that will be backed up, and the time it takes to accomplish this, has a direct bearing on the type of backup that should be performed. The table outlines the three basic types of backups that can be conducted, the amount of space required for each, and the ease of restoration using each strategy.

Geographic Considerations
An important element to factor into the cost of the backup strategy is the expense of storing the backups. A simple strategy might be to store all your backups together for quick and easy recovery actions. This is not, however, a good idea. Suppose the catastrophic event that necessitated the restoration of backed-up data was a fire that destroyed the computer system the data was processed on. In this case, any backups that were stored in the same facility might also be lost in the same fire.
The solution is to keep copies of backups in separate locations. The most recent copy can be stored locally, as it is the most likely to be needed, while other copies can be kept at other locations. Depending on the level of security your organization desires, the storage facility itself could be reinforced against possible threats in your area (such as tornados or floods). A more recent advance is online backup services. A number of third-party companies offer high-speed connections for storing data in a separate facility. Transmitting the backup data via network connections alleviates some other issues with physical movement of more traditional storage media, such as the care during transportation (tapes do not fare well in direct sunlight, for example) or the time that it takes to transport the tapes.
Off-Site Backups
Off-site backups are just that, backups that are stored in a separate location from the system being backed up. This can be important in the realm of problems that can affect larger areas than a single room. A building fire, a hurricane, a tornado … these are all disasters that occur frequently and typically affect a larger area than a single room or building. Having backups off-site alleviates the risk of losing the backup to the same problem. In today’s high-speed network world with cloud services, storing backups in the cloud is an option that can resolve many of the risk issues associated with backup availability.
Distance
The distance associated with an off-site backup is a logistics problem. If you need to restore a system and the backup is stored hours away by car, that increases the recovery time. The delay resulting from physical movement of backup tapes has been alleviated in many systems through networks that move the data at the speed of the network. Distance is also critical when examining the reach of a disaster. It is important that the off-site location is far enough away that it is not affected by the same incident. This includes the physical location of a cloud storage provider’s servers. If your business is in Puerto Rico and so is your cloud provider’s servers, for example, Hurricane Maria likely made your data unavailable for a long time.
Location Selection
Picking a storage location for backups has several key elements. First is physical safety of the backup media. Because of the importance to maintain a proper environmental condition safe from outside harm, this can limit locations. HVAC can be a consideration, as well as issues such as potential flooding and theft. Protecting the backup media is important as damage to it may not be discovered until the media is needed and then the loss becomes potentially catastrophic. Ability to move the backups in and out of storage is also a concern. Again, the cloud and networks come to the rescue. With today’s high-speed networks, reasonably priced storage, and the ability to store backups in a redundant array across multiple sites, all while protecting the information via encryption, cloud storage is the ideal solution.
Legal Implications
With regard to location selection, if you are considering cloud storage for your backups, you must take into consideration the legal implications of where the data would actually be stored. Different jurisdictions have different laws, rules, and regulations concerning core tools such as encryption. Understanding how these affect data backup storage plans is critical to prevent downstream problems. Some countries require storage of data concerning their citizens to be done within their borders, under their legal jurisdiction. Other countries may have different government regulations concerning privacy that would impact the security of the data. In the end, without proper contracting and review, one may not have any idea where their data is actually stored, for what might be a cloud in Atlanta this week, could be Albania next week.
Data Sovereignty
Data sovereignty is a relatively new type of legislation several countries have enacted recently that mandates data stored within their borders is subject to their laws, and in some cases that data originating within their borders must be stored there. In today’s multinational economy, with the Internet’s lack of borders, this has become a problem. Several high-tech firms have changed their business strategies and offerings in order to comply with data sovereignty rules and regulations. For example, LinkedIn, a business social network site, recently was told by Russian authorities that it needed to store all of its data on Russian citizens on servers in Russia. LinkedIn took the business decision that the cost was not worth the benefit and has since abandoned the Russian market.

EXAM TIP Using the information in the given scenario, you should be able to differentiate which geographic consideration is most important. This can change based on how the scenario is worded, so answer per the given criteria.
Continuity of Operation Planning
Ensuring continuity of operations is a business imperative, as it has been shown that businesses that cannot quickly recover from a disruption have a real chance of never recovering and going out of business. The overall goal of continuity of operation planning is to determine which subset of normal operations needs to be continued during periods of disruption. Continuity of operations planning involves developing a comprehensive plan to enact during a situation where normal operations are interrupted. This includes identifying critical assets (including key personnel), critical systems, and interdependencies, and ensuring their availability during a disruption.
Developing a continuity of operations plan is a joint effort between the business and the IT team. The business understands which functions are critical for continuity of operations, and which functions can be suspended. The IT team understands how this translates into equipment, data and services and can establish the correct IT functions. Senior management will have to make the major decisions as to the risk balance versus cost versus criticality when examining hot, warm, or cold site strategies.
Exercises/Tabletop
Once a continuity of operations plan is in place, a tabletop exercise should be performed to walk through all of the steps and ensure all elements are covered and that the plan does not forget a key dataset or person. This tabletop exercise is a critical final step, for it is this step that validates the planning covered the needed elements. The steps in the exercise should be performed by the principal leaders of the business and IT functions to ensure that all steps are correct. This will take time from senior members, but given the criticality of this business process, as this is being done for operations determined to be critical to the business, this hardly seems like overkill.
This exercise aspect is not a onetime thing, it should be repeated after major changes to systems that impact the continuity of operations plan or other major change such as personnel. As such, major corporations regularly exercise these types of systems on a calendar-based schedule, rotating through day and night shifts, primary and backup people and different systems.
After-Action Reports
Just as identifying and documenting lessons learned is a key element of the incident response process, after-action reports should be prepared after invoking the continuity of operations plan. Similar to lessons learned, after-action reports serve two functions. First, they document the level of operations upon transfer to the backup system. Is all of the capability necessary to continue operations up and running? The second question set addresses how the actual change from normal operations to those supported by continuity systems occurred, including documenting what went right and what went wrong?
Failover
Failover is the process for moving from a normal operational capability to the continuity-of-operations version of the business. The required speed and flexibility of the failover depends on the business type, from seamless for most financial sites, to a slightly delayed process where A is turned off and someone goes and turns B on with some period of no service between. Simple transparent failovers can be achieved through architecture and technology choices, but they must be designed into the system. Simpler, slightly delayed failovers cost less but result in less continuity for those connected to the system.
Failover can be a technology driven thing where one system fails and a redundant system takes its place without notice by the rest of the process. Failover can also be an interruption to service, switch to business continuity of operations mode type event that involves technology, people and shifting business processes. In both extremes, and all cases in between, the term failover refers to the shift from primary or original processing to a redundant or secondary form.
Separate from failover, which occurs whenever a problem occurs, is the switch back to the original system. Once a system is fixed, resolving whatever caused the outage, there is a need to move back to the original production system. This “failback” mechanism, by definition, is harder to perform, as primary keys and indices are not easily transferred back. The return to operations is a more complicated process, but the good news is that it can be performed at a time of the organization’s choosing, unlike the problem that initiated the initial shift of operations to continuity procedures.
Alternate Processing Sites
One of the key aspects of planning a solid, cost-effective continuity of operations plan is to consider alternate processing sites. In the worst case, the action that triggered the shift to the continuity system could also have rendered the physical location of the original business system unusable. Another consideration is the scale and volume of transactions to be processed while in continuity mode of operations. Typically, the volume is smaller, meaning that smaller sites can handle the continuity operations. It is also important to consider the operators, as continuity systems will require people to operate specific aspects of their function and location of the sites where they are physically accessible by the correct personnel is important. If you choose an alternate processing site that is 500 miles away in another major city and you do not have staff or personnel there, you need to have a plan to temporarily move the required personnel, including temporary lodging, etc. In a company with multiple sites, it is not uncommon to use a different geographic office to cover the one that is lost, using local people to run the business continuity processes.
Alternate Business Practices
Because continuity of operations involves maintaining only key systems, the business practices that are appropriate for continuity of operations will most likely be different than those used in normal operations. This leads to alternate business practices, an element of continuity of operation that must be planned and tested. These alternate business practices need to meet the objectives of the continuity of operations objectives. There are many operations that are performed in business that may be suspended during alternative operations. For instance, assuming you use an internal clocking system to record employee time, one where they log into an application when they start and stop working. This operation may not be deemed important enough to continue during alternative processing, so an alternative means of logging employee time and paying them is needed.

EXAM TIP Continuity of operation planning is an important concept with several parts, all of which are easily tested. Do not confuse incident response steps, backups, and continuity of operations. They have items in common, so watch for specific details in a question scenario to select the best answer.
Chapter Review
In this chapter, you became acquainted with incident response procedures as well as concepts related to disaster recovery and continuity of operations. The chapter opened with incident response planning, including documented incident types/categories, defining the roles and responsibilities or responders, the reporting requirements and escalation plans, the composition of the cyber-incident response team, and the necessity of exercising the plans. The chapter then described the six phases of the incident response process: preparation, identification, containment, eradication, recovery, and lessons learned.
The chapter then moved to disaster recovery concepts, beginning with recovery sites, which include hot, warm, and cold sites. The concept of order of restoration was presented next, explaining the importance of identifying the order in which systems should be restored. Backup concepts included the various types of backups: differential backups, incremental backups, snapshots, and full backups. Geographic considerations included off-site backups, distance, location selection, legal implications, and data sovereignty.
The chapter concluded with an examination of continuity of operations planning, including exercises/tabletop, after-action reports, failover, alternate processing sites, and alternate business practices.
Questions
To help you prepare further for the CompTIA Security+ exam, and to test your level of preparedness, answer the following questions and then check your answers against the correct answers at the end of the chapter.
1. What is the term used to describe the steps an organization performs after any situation determined to be abnormal in the operation of a computer system?
A. Computer/network penetration incident plan
B. Incident response plan
C. Backup restoration and reconfiguration
D. Cyber event response
2. Two major elements play a role in determining the level of response to an incident. Information criticality is the primary determinant. What is the other?
A. Information sensitivity or the classification of the data
B. The value of any data lost in the incident
C. How the incident potentially affects the organization’s operations
D. Whether the organization wishes to pursue a legal settlement against the attacker(s)
3. The designated group of personnel who will respond to an incident is called which of the following?
A. Incident response red team
B. Incident action group
C. Cyber-emergency response group
D. Cyber-incident response team
4. Which phase of the incident response process occurs before an actual incident?
A. Preparation
B. Identification
C. Containment
D. Prevention
5. Which phase of the incident response process involves removing the problem?
A. Identification
B. Eradication
C. Recovery
D. Mitigation
6. In which phase of the incident response process are actions taken to constrain the incident to the minimal number of machines?
A. Eradication
B. Identification
C. Containment
D. Recovery
7. Which of the following is a fully configured environment similar to the normal operating environment that can be operational immediately or within a few hours depending on its configuration and the needs of the organization?
A. Cold site
B. Warm site
C. Hot site
D. Recovery site
8. Which of the following is a partially configured location, usually having the peripherals and software but perhaps not a more expensive main processing computer?
A. Cold site
B. Warm site
C. Hot site
D. Recovery site
9. Which of the following are considerations for an organization’s data backup strategy? (Choose all that apply.)
A. How frequently backups should be conducted
B. How extensive backups need to be
C. Where the backups will be stored
D. How long the backups will be kept
10. Which backup strategy includes only the files and software that have changed since the last full backup?
A. Incremental
B. Full
C. Snapshot
D. Differential
11. Which backup strategy focuses on copies of virtual machines?
A. Incremental
B. Full
C. Snapshot
D. Differential
12. When discussing location for storage of backups, which of the following is true? (Choose all that apply.)
A. The most recent copy should be stored off-site, as it is the one that is most current and is thus the most valuable one.
B. Off-site storage is generally not necessary except in cases where the possibility of a break-in at the main facility is high.
C. Off-site storage is a good idea so that you don’t lose your backup to the same event that caused you to lose your operational data and thus need the backup.
D. The most recent copy can be stored locally, as it is the most likely to be needed, while other copies can be kept at other locations.
13. What is the term used to describe the requirement where some countries have enacted laws stating that certain types of data must be stored within their boundaries?
A. Data sovereignty
B. International intellectual property
C. International privacy rights
D. National data protection rights
14. What is the term for the set of steps needed to develop a comprehensive plan to enact during a situation where normal operations are interrupted?
A. Disaster recovery
B. Continuity of operations planning
C. Incident response planning
D. Restoration of business functions planning
15. What is the name of the process for moving from a normal operational capability to the continuity-of-operations version of the business?
A. Disaster recovery
B. Alternate business practices
C. Failover
D. Continuity of business functions
Answers
1. B. Incident response plan is the term used to describe the steps an organization performs in response to any situation determined to be abnormal in the operation of a computer system.
2. C. The second factor involves a business decision on how this incident plays into current business operations. A series of breaches, whether minor or not, indicates a pattern that can have public relations and regulatory issues.
3. D. The designated group of personnel who will respond to an incident is known as the cyber-incident response team.
4. A. Preparation is the phase of incident response that occurs before a specific incident. Preparation includes all the tasks needed to be organized and ready to respond to an incident. The act of identification is coming to a decision that the information related to the incident is worthy of further investigation by the IR team. Containment is the set of actions taken to constrain the incident to the minimal number of machines. Prevention is not a phase of the incident response process.
5. B. Eradication involves removing the problem, and in today’s complex system environment, this may mean rebuilding a clean machine. The act of identification is coming to a decision that the information related to the incident is worthy of further investigation by the IR team. The recovery process includes the steps necessary to return the systems and applications to operational status. Mitigation is not a phase in the incident response process.
6. C. Containment is the set of actions taken to constrain the incident to the minimal number of machines. Eradication involves removing the problem, and in today’s complex system environment, this may mean rebuilding a clean machine. The act of identification is coming to a decision that the information related to the incident is worthy of further investigation by the IR team. The recovery process includes the steps necessary to return the systems and applications to operational status.
7. C. A hot site is a fully configured environment similar to the normal operating environment that can be operational immediately or within a few hours depending on its configuration and the needs of the organization. A cold site will have the basic environmental controls necessary to operate but few of the computing components necessary for processing. A warm site is partially configured, usually having the peripherals and software but perhaps not the more expensive main processing computer. A recovery site is any location where restoration of services would take place, whether cold, warm, or hot.
8. B. A warm site is partially configured, usually having the peripherals and software but perhaps not the more expensive main processing computer. A cold site will have the basic environmental controls necessary to operate but few of the computing components necessary for processing. A hot site is a fully configured environment similar to the normal operating environment that can be operational immediately or within a few hours depending on its configuration and the needs of the organization. A recovery site is any location where restoration of services would take place, whether cold, warm, or hot.
9. A, B, C, and D. All of these are considerations for an organization’s data backup strategy.
10. D. In a differential backup, only the files and software that have changed since the last full backup was completed are backed up. The incremental backup is a variation on a differential backup, with the difference being that instead of copying all files that have changed since the last full backup, the incremental backup backs up only files that have changed since the last full or incremental backup occurred, thus requiring fewer files to be backed up. In a full backup, all files and software are copied onto the storage media. Snapshots refer to copies of virtual machines.
11. C. Snapshots refer to copies of virtual machines. The incremental backup is a variation on a differential backup, with the difference being that instead of copying all files that have changed since the last full backup, the incremental backup backs up only files that have changed since the last full or incremental backup occurred, thus requiring fewer files to be backed up. In a full backup, all files and software are copied onto the storage media. In a differential backup, only the files and software that have changed since the last full backup was completed are backed up.
12. C and D. Off-site storage is a good idea so that you don’t lose your backup to the same event that caused you to lose your operational data and thus need the backup. Additionally, the most recent copy can be stored locally, as it is the most likely to be needed, while other copies can be kept at other locations.
13. A. Data sovereignty is a relatively new phenomena, but in the past couple of years several countries have enacted laws stating the certain types of data must be stored within their boundaries. The other terms do not describe any actual situation.
14. B. Continuity of operations planning is the set of steps needed to develop a comprehensive plan to enact during a situation where normal operations are interrupted. Disaster recovery is the process that an organization uses to recover from events that disrupt normal operations. An incident response plan describes the steps an organization performs in response to any situation determined to be abnormal in the operation of a computer system. Restoration of business functions planning is not a standard term used in recovery planning.
15. C. Failover is the process for moving from a normal operational capability to the continuity-of-operations version of the business. Disaster recovery is the process that an organization uses to recover from events that disrupt normal operations. Alternate business practices are developed in recognition that processes may need to be different in a continuity of operations situation since the focus is only on maintaining key systems. Continuity of business functions is not a term used in industry.