CHAPTER 3
Threat Actors
In this chapter, you will
• Explain threat actor types
• Explain threat actor attributes
• Explore open source threat intelligence
This chapter examines the types and attributes of threat actors. Threat actors can take many forms and represent different levels of threats, so understanding the type and motivation of an actor can be critical for proper defensive measures. The chapter also explores open source intelligence as used to understand the current threat environment, and to lead the proper resource deployment of cyber defenses.
Certification Objective This chapter covers CompTIA Security+ exam objective 1.3, Explain threat actor types and attributes.
Types of Actors
The act of deliberately accessing computer systems and networks without authorization is generally referred to as hacking, with individuals who conduct this activity being referred to as hackers. The term “hacking” also applies to the act of exceeding one’s authority in a system. This would include authorized users who attempt to gain access to files they aren’t permitted to access or who attempt to obtain permissions that they have not been granted. While the act of breaking into computer systems and networks has been glorified in the media and movies, the physical act does not live up to the Hollywood hype. Intruders are, if nothing else, extremely patient, since the process to gain access to a system takes persistence and dogged determination. The attacker will conduct many pre-attack activities in order to obtain the information needed to determine which attack will most likely be successful. Typically, by the time an attack is launched, the attacker will have gathered enough information to be very confident that the attack will succeed.
Generally, attacks by an individual or even a small group of attackers fall into the unstructured threat category. Attacks at this level generally are conducted over short periods of time (lasting at most a few months), do not involve a large number of individuals, have little financial backing, and are accomplished by insiders or outsiders who do not seek collusion with insiders. Intruders, or those who are attempting to conduct an intrusion, definitely come in many different varieties and have varying degrees of sophistication (see Figure 3-1).
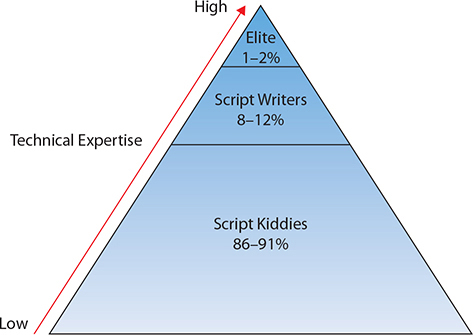
Figure 3-1 Distribution of attacker skill levels
Script Kiddies
At the low end of the spectrum technically are what are generally referred to as script kiddies, individuals who do not have the technical expertise to develop scripts or discover new vulnerabilities in software but who have just enough understanding of computer systems to be able to download and run scripts that others have developed. These individuals generally are not interested in attacking specific targets, but instead simply want to find any organization that may not have patched a newly discovered vulnerability for which the script kiddie has located a script to exploit the vulnerability. It is hard to estimate how many of the individuals performing activities such as probing networks or scanning individual systems are part of this group, but it is undoubtedly the fastest growing group and the vast majority of the “unfriendly” activity occurring on the Internet is probably carried out by these individuals.
Hacktivists
As shown in Figure 3-1, at the next level above script kiddies are those people who are capable of writing scripts to exploit known vulnerabilities. These individuals are much more technically competent than script kiddies and account for an estimated 8 to 12 percent of malicious Internet activity. When hackers work together for a collectivist effort, typically on behalf of some cause, they are referred to as hacktivists. Hacktivist groups may include script kiddies, but in general script kiddies do not have the skills to participate in a meaningful manner in advancing a hacktivist cause, although they may be enlisted as ground troops to add volume to an attack.
Organized Crime
As businesses became increasingly reliant upon computer systems and networks, and as the amount of financial transactions conducted via the Internet increased, it was inevitable that organized crime would eventually turn to the electronic world as a new target to exploit. One of the major changes over the past decade in cybersecurity has been the ability for hackers to monetize their efforts. Part of this is due to the rise in cryptocurrency, such as bitcoin, but an entire marketplace on the dark web for stolen identities, financial data, and intellectual property has created a criminal cybersecurity marketplace that, in terms of dollars, is larger than the international drug trade. This has led to a whole new class of organized crime figure, cybersecurity criminals, who can lurk in the shadows of anonymity and create malware and other attacks, as well as perform attacks, all with an eye on making money.
Criminal activity on the Internet at its most basic is no different from criminal activity in the physical world. Fraud, extortion, theft, embezzlement, and forgery all take place in the electronic environment.
One difference between criminal groups and the “average” hacker is the level of organization that criminal elements employ in their attack. Criminal groups typically have more money to spend on accomplishing the criminal activity and are willing to spend extra time accomplishing the task, provided the level of reward at the conclusion is great enough. With the tremendous amount of money that is exchanged via the Internet on a daily basis, the level of reward for a successful attack is high enough to interest criminal elements. Attacks by criminal organizations usually fall into the structured threat category, which is characterized by a greater amount of planning, a longer period of time to conduct the activity, more financial backing to accomplish it, and possibly corruption of, or collusion with, insiders.
Nation States/APT
At the top end of this spectrum shown in Figure 3-1 are those highly technical individuals, often referred to as elite hackers, who not only have the ability to write scripts that exploit vulnerabilities but also are capable of discovering new vulnerabilities. This group is the smallest of the lot, however, and is responsible for, at most, only 1 to 2 percent of intrusive activity. Many of these elite hackers are employed by major cybersecurity firms in an effort to combat criminal activity. Others are employed by nation states and other international organizations, to train and run large groups of skilled hackers to conduct nation-state attacks against a wide range of adversaries. In the United States, government rules and regulations prevent government workers from attacking companies for reasons of economic warfare. Not all countries live by this principle, and many have organized hacking efforts designed to gather information from international companies, stealing intellectual property for the express purpose of advancing their own country’s national companies.
As nations have increasingly become dependent on computer systems and networks, the possibility that these essential elements of society might be targeted by organizations or nations determined to adversely affect another nation has become a reality. Many nations today have developed to some extent the capability to conduct information warfare. There are several definitions for information warfare, but a simple one is that it is warfare conducted against the information and information processing equipment used by an adversary. In practice, this is a much more complicated subject, because information not only may be the target of an adversary, but also may be used as a weapon. Whatever definition you use, information warfare falls into the highly structured threat category. This type of threat is characterized by a much longer period of preparation (years is not uncommon), tremendous financial backing, and a large and organized group of attackers. The threat may include attempts not only to subvert insiders but also to plant individuals inside of a potential target in advance of a planned attack.
An interesting aspect of information warfare is the list of possible targets available. We have grown accustomed to the idea that, during war, military forces will target opposing military forces but will generally attempt to destroy as little civilian infrastructure as possible. In information warfare, military forces are certainly still a key target, but much has been written about other targets, such as the various infrastructures that a nation relies on for its daily existence. Water, electricity, oil and gas refineries and distribution, banking and finance, telecommunications—all fall into the category of critical infrastructures for a nation. Critical infrastructures are those whose loss would have severe repercussions on the nation. With countries relying so heavily on these infrastructures, it is inevitable that they will be viewed as valid targets during conflict. Given how dependent these infrastructures are on computer systems and networks, it is also inevitable that these same computer systems and networks will be targeted for a cyberattack in an information war.
Another major advance in cyberattacks is the development of the advanced persistent threat (APT). APT attacks are characterized by using toolkits to achieve a presence on a target network and then, instead of just moving to steal information, focusing on the long game, maintaining a persistence on the target network. The tactics, tools, and procedures of APTs are focused on maintaining administrative access to the target network and avoiding detection. Then, over the long haul, the attacker can remove intellectual property and more from the organization, typically undetected.
Operation Night Dragon is the name given to an intellectual property attack executed against oil, gas, and petrochemical companies in the United States in 2006. Using a set of global servers, attackers from China raided global energy companies for proprietary and highly confidential information such as bidding data for leases. The attack shed new light on what constitute critical data and associated risks. Further, as demonstrated by the Stuxnet attacks against Iranian uranium plants, the cyberattacks in Estonia, and the attacks on electricity distribution in the Ukraine, the risk of nation-state attacks is real. There have been numerous accusations of intellectual property theft being sponsored by, and in some cases even performed by, nation-state actors. In a world where information dominates government, business, and economies, the collection of information is the key to success, and with large rewards, the list of characters willing to spend significant resources is high.
Insiders
It is generally acknowledged by security professionals that insiders are more dangerous in many respects than outside intruders. The reason for this is simple—insiders have the access and knowledge necessary to cause immediate damage to an organization. Most security is designed to protect against outside intruders and thus lies at the boundary between the organization and the rest of the world. Insiders may actually already have all the access they need to perpetrate criminal activity such as fraud. In addition to unprecedented access, insiders also frequently have knowledge of the security systems in place and are better able to avoid detection. Attacks by insiders are often the result of employees who have become disgruntled with their organization and are looking for ways to disrupt operations. It is also possible that an “attack” by an insider may be an accident and not intended as an attack at all. An example of this might be an employee who deletes a critical file without understanding its critical nature.

EXAM TIP One of the hardest threats that security professionals will have to address is that of the insider. Since employees already have access to the organization and its assets, additional mechanisms need to be in place to detect attacks by insiders and to lessen the ability of these attacks to succeed.
Employees are not the only insiders that organizations need to be concerned about. Often, numerous other individuals have physical access to company facilities. Custodial crews frequently have unescorted access throughout the facility, often when nobody else is around. Other individuals, such as contractors or partners, may have not only physical access to the organization’s facilities but also access to computer systems and networks. A contractor involved in U.S. intelligence computing, Edward Snowden, was charged with espionage in 2013 after he released a wide range of data illustrating the technical capabilities of U.S. intelligence surveillance systems. He is the ultimate insider, with his name becoming synonymous with the insider threat issue.
Competitors
In today’s world of global economic activity, much of it enabled by the interconnected nature of businesses, many businesses have an information component. And this information component is easier to copy, steal, or disrupt than older, more physical assets, making it an alluring target for competitors. There have been cases of people moving from competitor to competitor, taking insider information with them for years, even decades, before the Internet was developed. The interconnectedness and digital nature of modern business has enabled this sort of corporate crime to be committed to an even greater degree. Where, in decades past, it would take significant risk to copy the detailed engineering specifications of a major process for a firm, today the same might be accomplished with a few clicks and a USB drive.

EXAM TIP Being able to differentiate the different types of threat actors based on their characteristics is important for the exam. What differentiates an insider from a nation state from a competitor when examining a potential attack?
Attributes of Actors
Threat actors can be divided into groups based on abilities, as shown previously in the chapter. There are other ways to differentiate the threat actors, by location, internal or external, by level of sophistication, level of resources, and intent. These attributes are described below.
Internal/External
Internal threat actors have one significant advantage over external actors. Internal actors have access to the system, and although it may be limited to user access, access provides the threat actor the ability to pursue their attack. External actors have an additional step, the establishment of access to the system under attack.
Level of Sophistication
As shown earlier in Figure 3-1, attacker skill or sophistication can be divided into several categories. When examining a group of threat actors and considering the individual skills of members of the group, there may well be a mix, with a few highly skilled individuals acting to move larger numbers of less skilled participants. The greater the skill level the more an individual will be expected to lead and design the attacks. When it comes to the sophistication level of the attack itself, one notable trend is that as the skill level goes up, so too does the use of minimal methods. Although zero day attacks are widely covered in the news, true zero day vulnerabilities are rarely used; they are reserved for the few cases where there are no other options, because once used they will be patched. Even with highly sophisticated and resourced nation-state teams employing APT methods, a surprising number of attacks are being performed using old attacks, old vulnerabilities, and simple methods that take advantage of “low-hanging fruit.” This is not to say that newer, more advanced methods are not used, but rather there is an economy of mechanism in the attacks themselves, using just what is needed at each step. There is also a lot of missing data to this picture, as we do not know of the methods that have been used successfully if the threat actor remains undetected.
Resources/Funding
As mentioned earlier, criminal organizations and nation states have larger budgets, bigger teams, and the ability to pursue campaigns for longer periods of time. Cybersecurity is challenging for attackers as well as defenders, and there are expenses associated with maintaining teams and tools used as threat actors against a system. APTs, with their penchant for long-term attacks, some lasting for years, require significant resources to engage in this type of activity, so there is a need for long-term resources that only major organizations or governments can manage over time.
Intent/Motivation
The intent or motivation behind an attack can be simple or multifold in nature. A script kiddie is just trying to make a technique work. A more skilled threat actor is usually pursuing a specific objective, such as trying to make a point as a hacktivist. At the top of the intent pyramid is the APT threat actor, whose intent or motivation is at least threefold. First is the drive to persist access mechanisms so that the threat actor has continued access. Second is the drive to remain undetected. In most APTs that are discovered, the length of intrusion is greater than a year and in many cases determining the original date of infection is not possible, as it is limited by length of logs. Third is the goal of stealing something of value on the network. APTs do not go to all the trouble of maintaining access and remaining invisible just to crash a system or force a rebuild.

EXAM TIP When taking the Security+ exam, threat actors will be described in terms of attributes: resources, level of sophistication, location, and motivation. Be sure to understand how these differences matter with respect to types of attacks.
Use of Open Source Intelligence
Open source intelligence, sometimes called open source threat intelligence, refers to intelligence data collected from public sources. There is a wide range of public sources of information concerning current cybersecurity activity. From news articles, to blogs, to government reports, there seems to be a never-ending stream of news concerning what is happening, to whom, and how. This leads to the overall topic of information sharing and the greater topic of threat intelligence (not just open source).
Cybersecurity is a game of resource management. No firm has the resources to protect everything against all threats, and even attempting to do so would add complexity that would open up other threat avenues. One of the important decisions is where to apply one’s resources in the complex landscape of cybersecurity defense. Threat intelligence is the gathering of information from a variety of sources, including non-public sources, to allow an entity to properly focus their defenses against the most likely threat actors.
There are several major sources besides the wide range of open source feeds. Examples include Information Sharing and Analysis Organizations (ISAOs) and Information Sharing Analysis Centers (ISACs). ISAOs vary greatly in capability but essentially include any organization, whether an industry sector or geographic region, that is sharing cyber-related information for the purpose of enhancing their members’ cybersecurity posture. ISACs are a special category of ISAO consisting of privately run, but government approved, industry-based cybersecurity. ISACs may be considered fusion centers where real-time information can be shared between members. ISAOs and ISACs work on a very simple premise: share what is happening to you, and together learn what is happening in your industry. The sharing is anonymized, the analysis is performed by highly skilled workers in a security operations center, and the resulting information is fed back to members as close to real time as possible. Highly skilled analysts are expensive, and this mechanism shares the costs across all of the member institutions. A U.S. government program, InfraGard, is run by the FBI and also acts as a means of sharing, although timeliness and level of analysis are nowhere near that of an ISAC, but the price is right (free).
At the end of the day, a combination of open source information, ISAC information (if available—not everyone can join), and InfraGard information provides a picture of what the current threat landscape looks like and what the most effective options for defense are against each threat. Using this information is critical in the deployment of proper cybersecurity defenses.
Chapter Review
The chapter opened with an examination of the types of threat actors. From script kiddies, to hacktivists, to organized crime and nation states, the primary differentiation is level of resources. The threat actors of insiders and competitors were also covered. Switching to the attributes of threat actors, they can be internal or external, and possess varying levels of skill, resources, and motivation. The chapter closed with an examination of open source intelligence.
Questions
To help you prepare further for the CompTIA Security+ exam, and to test your level of preparedness, answer the following questions and then check your answers against the correct answers at the end of the chapter.
1. Which of the following is the term generally used to refer to the act of deliberately accessing computer systems and networks without authorization?
A. Phishing
B. Threat
C. Vulnerability
D. Attack
2. Attacks by an individual or even a small group of attackers fall into which threat category?
A. Unorganized threat
B. APT
C. Singular threat
D. Hactivist
3. Which of the following is the term used to refer to individuals who do not have the technical expertise to develop scripts or discover new vulnerabilities in software but who have just enough understanding of computer systems to be able to download and run scripts that others have developed?
A. Script kiddies
B. Hackers
C. Simple intruders
D. Intermittent attackers
4. What is the name given to a group of hackers who work together for a collectivist effort, typically on behalf of some cause?
A. Script kiddies
B. Hacktivists
C. Motivated hackers
D. Organized intruders
5. Attacks by individuals from organized crime are generally considered to fall into which threat category?
A. Highly structure threats
B. Unstructured threat
C. Structured threat
D. Advanced persistent threat
6. What is the name given to the group of individuals who not only have the ability to write scripts that exploit vulnerabilities but also are capable of discovering new vulnerabilities?
A. Elite hackers
B. Hacktivists
C. Uber hackers
D. Advanced persistent threat actors
7. Criminal activity on the Internet can include which of the following? (Choose all that apply.)
A. Fraud
B. Extortion
C. Theft
D. Embezzlement
E. Forgery
8. Warfare conducted against the information and information processing equipment used by an adversary is known as which of the following?
A. Information warfare
B. Cyber warfare
C. Offensive cyber operations
D. Computer espionage
9. What term is used to describe the type of threat that is characterized by a much longer period of preparation (years is not uncommon), tremendous financial backing, and a large and organized group of attackers?
A. Advanced capability threat
B. Structured threat
C. Nation-state threat
D. Highly structured threat
10. What is the term used to define attacks that are characterized by using toolkits to achieve a presence on a target network, with a focus on the long game—maintaining a persistence on the target network?
A. Covert network threat
B. Advanced persistent threat
C. Covert channel attack
D. Concealed network presence
11. Which of the following are reasons that the insider threat is considered so dangerous? (Choose all that apply.)
A. Insiders have the access and knowledge necessary to cause immediate damage to an organization.
B. Insiders may actually already have all the access they need to perpetrate criminal activity such as fraud.
C. Insiders generally do not have knowledge of the security systems in place, so system monitoring will allow for any inappropriate activity to be detected.
D. Attacks by insiders are often the result of employees who have become disgruntled with their organization and are looking for ways to disrupt operations.
12. When discussing threat concerns regarding competitors, which of the following is true?
A. There are no known cases of criminal activity involving people moving from competitor to competitor, taking insider information with them for years.
B. Where in the past it would take significant risk to copy the detailed engineering specifications of a major process for a firm, today it can be accomplished with a few clicks and a USB drive.
C. Modern search engines make it less likely that a competitor could steal intellectual property without being detected.
D. With increases in digital forensics, it is now more difficult to copy and steal proprietary digital information or disrupt operations.
13. Which of the following are true concerning attacker skill and sophistication? (Choose all that apply.)
A. The level of complexity for modern networks and operating systems has grown so that it is nearly impossible for anyone but the most skilled of hackers to gain unauthorized access to computer systems and networks.
B. Attackers do not have magic skills, but rather the persistence and skill to keep attacking weaknesses.
C. With the introduction of cloud computing during the last decade, attackers now primarily focus on the cloud, thus reducing the level of sophistication required to conduct attacks since they can focus on a more limited environment.
D. There is a surprising number of attacks being performed using old attacks, old vulnerabilities, and simple methods that take advantage of “low-hanging fruit.”
14. Which of the following is the term used to describe the processes used in the collection of information from public sources?
A. Media exploitation
B. Open source intelligence
C. Social media intelligence
D. Social engineering
15. What term is used to describe the gathering of information from a variety of sources, including non-public sources, to allow an entity to properly focus their defenses against the most likely threat actors?
A. Infosec analysis
B. Data intelligence
C. Threat intelligence
D. Information warfare
Answers
1. D. Attack is the term that is now generally accepted when referring to the act of gaining unauthorized access to computer systems and networks. The terms phishing, threat, vulnerability all relate to attacks, but are not the act of attacking.
2. D. Attacks by an individual or even a small group of attackers fall into the hactivist threat category. Attacks by criminal organizations usually fall into the structured threat category. The other two answers are not categories of threats used by the security community.
3. A. Script kiddies is the label used to refer to individuals who do not have the technical expertise to develop scripts or discover new vulnerabilities in software but who have just enough understanding of computer systems to be able to download and run scripts that others have developed. Hackers is the more general term used to refer to individuals at all levels who attempt to gain unauthorized access to computer systems and networks. The other two answers are not terms used in the security community.
4. B. When hackers work together for a collectivist effort, typically on behalf of some cause, they are referred to as hacktivists. Hacktivist groups may include script kiddies, but in general script kiddies do not have the skills to participate in a meaningful manner in advancing a hacktivist cause, although they may be enlisted as ground troops to add volume to an attack. The other two terms are not generally used in the security community.
5. C. Attacks by criminal organizations usually fall into the structured threat category characterized by a greater amount of planning, a longer period of time to conduct the activity, more financial backing to accomplish it, and possibly corruption of, or collusion with, insiders. Highly structured threats require greater planning, while unstructured threats require less, and APT attacks are typically nation state in origin, not organized criminals.
6. A. Elite hackers is the name given to those who not only have the ability to write scripts that exploit vulnerabilities but also are capable of discovering new vulnerabilities.
7. A, B, C, D, and E. Criminal activity on the Internet at its most basic is no different from criminal activity in the physical world. Fraud, extortion, theft, embezzlement, and forgery all take place in the electronic environment.
8. A. Information warfare is warfare conducted against the information and information processing equipment used by an adversary. Cyber warfare and offensive cyber operations are terms that you may encounter, but the more generally accepted term for this type of activity is information warfare. Computer espionage is generally associated with intelligence gathering and not general computer warfare.
9. D. A highly structured threat is characterized by a much longer period of preparation (years is not uncommon), tremendous financial backing, and a large and organized group of attackers. The threat may include attempts not only to subvert insiders but also to plant individuals inside of a potential target in advance of a planned attack. This type of threat generally is much more involved and extensive than a structured threat. The other terms are not commonly used in the security industry.
10. B. Advanced persistent threats (APTs) are attacks characterized by using toolkits to achieve a presence on a target network and then, instead of just moving to steal information, focusing on the long game, maintaining a persistence on the target network. Their tactics, tools, and procedures are focused on maintaining administrative access to the target network and avoiding detection. Covert channels are indeed a concern in security but are a special category of attack. The other terms are not generally used in the security community.
11. A, B, and D. Insiders frequently do have knowledge of the security systems in place and are thus better able to avoid detection.
12. B. In today’s world of global economic activity, much of it is enabled by the interconnected nature of businesses. Many businesses have an information component that is easier to copy, steal, or disrupt than older, more physical assets. Additionally, there have been cases of people moving from competitor to competitor, taking insider information with them for years, even decades, before the Internet was developed.
13. B and D. While the complexity of systems is indeed increasing, there still exists a large number of computers and networks that have not been adequately protected, making it possible for less sophisticated attackers to gain unauthorized access. Additionally, while cloud computing has added another focus for attackers, it has not eliminated computer systems and networks in general as potential targets.
14. B. Open source intelligence is the term used to describe the processes used in the collection of intelligence from public sources. Human intelligence (HUMINT) is a specific category of intelligence gathering focused on obtaining information directly from individuals. The other terms are not generally used by security professionals.
15. C. Threat intelligence is the gathering of information from a variety of sources, including non-public sources, to allow an entity to properly focus their defenses against the most likely threat actors. Information warfare is conducted against the information and information processing equipment used by an adversary and consists of a larger range of activities. The other two terms are not generally used by security professionals.