CHAPTER 7
Security Tools and Technologies
In this chapter, you will be able to
• Understand how to use appropriate software tools to assess the security posture of an organization
• Given a scenario, analyze and interpret output from security technologies
Software tools and security technologies are the methods by which professionals can address vulnerabilities and risk in the enterprise. Tools enable a security analyst to assess the current security posture of a system. Various security technologies provide information that can be analyzed and interpreted by security analysts to determine risk profiles.
Certification Objective This chapter covers CompTIA Security+ exam objectives 2.2, Given a scenario, use appropriate software tools to assess the security posture of an organization, and 2.4, Given a scenario, analyze and interpret output from security technologies. These exam objectives are good candidates for performance-based questions, which means you should expect questions in which you must apply your knowledge of the topic to a scenario. The best answer to a question will depend upon specific details in the scenario preceding the question, not just the question. The questions may also involve tasks other than just picking the best answer from a list. Instead, they may involve actual simulations of steps to take to solve a problem.
Protocol Analyzer
A protocol analyzer is simply a tool (either hardware or software) that can be used to capture and analyze traffic passing over a communications channel, such as a network. Although protocol analyzers exist for many types of communication channels, such as telecommunications traffic and system buses, the most common use of a protocol analyzer is for the capture and examination of network traffic. In the networking world, this tool is commonly referred to by a variety of names such as packet sniffer, network analyzer, network sniffer, packet analyzer, or simply sniffer. Packet analyzers can be used to capture and analyze wired or wireless traffic and can be software based (most common) or a dedicated hardware/software platform. An effective packet analyzer must have the capability to place a network interface in promiscuous mode, which tells the interface to accept and process every packet it sees—not just packets destined for this specific system or sent to a broadcast, multicast, or unicast address. On a switched network, packet analyzers are typically plugged into a SPAN (discussed in the next section) or monitor ports that are configured to receive copies of packets passing through one or more interfaces on the same switch. Capabilities of packet analyzers vary greatly—some do nothing more than simple packet capture, whereas others attempt to reconstruct entire TCP/IP sessions with decoded packets and color-coded traffic streams.
From a security perspective, protocol analyzers are very useful and effective tools. Want to see if any system on your network is transmitting traffic on a specific port? Want to see if any packets are being sent to an address at a rival company? Want to see which employees spend all day surfing eBay? Want to find the system that’s flooding the local network with broadcast traffic? A protocol analyzer can help you address all these issues and more—if you have the analyzer plugged into the right location of your network and can “see” the traffic you are concerned about. Most organizations have multiple points in the network where traffic can be sniffed—in the core switch, between the user base and the server farm, between remote users and the core network, between the organization and any link to the Internet, and so on. Knowing how to ensure the packet analyzer can “see” the traffic you want to analyze, knowing where to place the analyzer, and knowing how to use the analyzer are all keys to getting the best results from a protocol analyzer. An example of a free and widely used protocol analyzer is Wireshark.
Switched Port Analyzer
The term Switched Port Analyzer (SPAN) is usually associated with Cisco switches—other vendors refer to the same capability as port mirroring or port monitoring. A SPAN has the ability to copy network traffic passing through one or more ports on a switch or one or more VLANs on a switch and forward that copied traffic to a port designated for traffic capture and analysis (as shown in Figure 7-1). A SPAN port or mirror port creates the collection point for traffic that will be fed into a protocol analyzer or IDS/IPS. SPAN or mirror ports can usually be configured to monitor traffic passing into interfaces, passing out of interfaces, or passing in both directions. When configuring port mirroring, you need to be aware of the capabilities of the switch you are working with. Can it handle the volume of traffic? Can it successfully mirror all the traffic, or will it end up dropping packets to the SPAN if traffic volume gets too high?
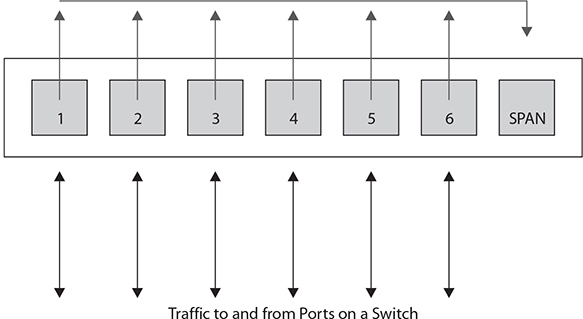
Figure 7-1 A SPAN port collects traffic from other ports on a switch.
Network Scanners
A network scanner is a tool designed to probe a network or systems for open ports, and hence machines that are on the network. Its job is to probe for open (or listening) ports and report back to the user which ports are closed, which are filtered, and which are open. Network scanners are capable of working on any IP network—including virtually every operating system and every popular mobile computing platform, from tablets to smartphones—because they operate by examining network connections. Having a good network scanning tool in your toolset and knowing how to use it properly can be very beneficial. The most commonly used scanner is the freeware tool Nmap (Network Mapper). Network scanners are also called port scanners and can be used to do the following:
• Search for “live” hosts on a network. Most network scanners enable you to perform a quick scan using ICMP, TCP, or UDP packets to search for active hosts on a given network or network segment. ICMP is still very popular for this task, but with the default blocking of ICMPv4 in many modern operating systems, such as Windows 7 and beyond, users are increasingly turning to TCP or UDP scans for these tasks.
• Search for any open ports on the network. Network scanners are most often used to identify any open ports on a host, group of hosts, or network. By scanning a large number of ports over a large number of hosts, a network scanner can provide you (or an attacker) with a very good picture of what services are running on which hosts on your network. Scans can be done for the “default” set of popular ports, a large range of ports, or every possible port (from 1 to 65535).
• Search for specific ports. Only looking for web servers? Mail servers? Network scanners can also be configured to just look for specific services.
• Identify services on ports. Some network scanners can help identify the services running on open ports based on information returned by the service or the port/service assigned (if standards have been followed). For example, a service running on port 80 is likely to be a web server.
• Look for TCP/UDP services. Most network scanners can perform scans for both TCP and UDP services, although some tools do not allow you to scan for both protocols at the same time.
As a security professional, you’ll use network scanners in much the same way an attacker would: to probe the systems in your network for open services. When you find open services, you’ll need to determine if those services should be running at all, if they should be running on the system(s) you found them on, and if you can do anything to limit what connections are allowed to those services. For example, you may want to scan your network for any system accepting connections on TCP port 1433 (Microsoft SQL Server). If you find a system accepting connections on TCP port 1433 in your Sales group, chances are someone has installed something they shouldn’t have (or someone installed something for them). It is important to note that network scanning activity can trigger an incident response activity when detected. Because of this, it is important that when using these types of tools inside a network that the security team is aware of the scope and timing of use to prevent unnecessary IR activity.
So how does a network scanner actually work? Much will depend on the options you select when configuring your scan, but for the sake of this example, assume you’re running a standard TCP connect scan against 192.168.1.20 for ports 1–1000. The scanner will attempt to create a TCP connection to each port in the range 1–1000 on 192.168.1.20. When the scanner sends out that SYN packet, it waits for the responding SYN/ACK. If a SYN/ACK is received, the scanner will attempt to complete the three-way handshake and mark the port as “open.” If the sent packet times out or an RST packet is received, the scanner will likely mark that port as “closed.” If an “administratively prohibited” message or something similar comes back, the scanner may mark that port as “filtered.” When the scan is complete, the scanner will present the results in a summary format—listing the ports that are open, closed, filtered, and so on. By examining the responses from each port, you can typically deduce a bit more information about the system(s) you are scanning, as detailed here:
• Open Open ports accept connections. If you can connect to these with a network scanner, the ports are not being filtered at the network level. However, there are instances where you may find a port that is marked as “open” by a network scanner that will immediately drop your connections if you attempt to connect to it in some other manner. For example, port 22 for SSH may appear “open” to a network scanner but will immediately drop your SSH connections. In such a case, the service is likely being filtered by a host-based firewall or a firewall capability within the service itself.
• Closed You will typically see this response when the scanned target returns an RST packet.
• Filtered You will typically see this response when an ICMP unreachable error is returned. This usually indicates that port is being filtered by a firewall or other device.
• Additional types Some network scanners will attempt to further classify responses, such as dropped, blocked, denied, timeout, and so on. These are fairly tool specific, and you should refer to any documentation or help file that accompanies that network scanner for additional information.
In general, you will want to run your scanning efforts multiple times using different options to ensure you get a better picture. A SYN scan may return different results than a NULL scan or FIN scan. You’ll want to run both TCP and UDP scans as well. You may need to alter your scanning approach to use multiple techniques at different times of the day/night to ensure complete coverage. The bad guys are doing this against your network right now, so you might as well use the same tools they do to see what they see. Network scanners can also be very useful for testing firewall configurations because the results of the port scans can show you exactly which ports are open, which ones you allow through, which ports are carrying services, and so on.
So how do you defend against port scans? Well, it’s tough. Port scans are pretty much a part of the Internet traffic landscape now. Although you can block IP addresses that scan you, most organizations don’t because you run the risk of an attacker spoofing source addresses as decoys for other scanning activity. The best defense is to carefully control what traffic you let in and out of your network, using firewalls, network filters, and host filters. Then carefully monitor any traffic that you do allow in.

EXAM TIP The previous two sections have described two of the most widely used and versatile tools, Wireshark and Nmap. Understanding what these tools can do and when and how they can be employed on your network covers a lot of testable areas of this objective.
Rogue System Detection
One of the challenges of network engineers is to determine if unauthorized equipment is attached to a network. Rogue systems are unauthorized systems and fall outside of the enterprise operations umbrella, adding risk to a system. This is why the first elements of the top 20 security controls consist of knowing the authorized software and hardware in your environment. You should do rogue system detection on a regular basis, which you can do in two ways with a network scanner. First, you can do active scans of the network to detect any devices not authorized. Second, you can do a passive scan via an examination of packets to see if anyone is communicating who is not authorized.
Network Mapping
Network mapping tools are another name for network scanners. Network mappers are designed to create network diagrams of how machines are connected. And then they stop there, while network scanners can do additional tasks, such as identify systems, services, and open ports. By definition, this makes network analyzers also mappers, albeit with more capabilities. The process of network mapping is the use of network mapping tools to identify the nodes of a network and characterize them as to OS, purpose, systems, etc.
Wireless Scanners/Cracker
You can use wireless scanners/crackers to perform network analysis of the wireless side of your networks. Who is connecting to them? What are they accessing? Is everything in conformance with your security plan? You need to actively pursue and answer these questions on a regular basis. There are a wide variety of wireless scanners that can assist in developing this form of monitoring.
Some common examples of wireless scanners are Kismet, NetStumbler, and Mini-
Stumbler. If you wish to add cracking ability, then AirSnort, AirCrack and CoWPAtty are common solutions.
Password Cracker
Password crackers are used by hackers to find weak passwords. Why would a system administrator use one? Same reason. Running your system’s password lists through a password cracker provides two things: an early warning of a crackable password, and peace of mind that your passwords are safe when you can’t crack any in a reasonable period of time.
Password crackers work using dictionary lists and brute force. On the dictionary lists, they make passwords by combining words with each other, with numbers, special symbols and test those against the system. They also can do brute force attacks. Password crackers can work on-line against a live system, but then they can be subject to timeouts after a limited number of false entries. But if they can steal the password file, they can operate a maximum speed until a match is found. On a modern Core I-7 machine, ten character passwords will fall in roughly a month of work.
Vulnerability Scanner
A vulnerability scanner is a program designed to probe a system for weaknesses, misconfigurations, old versions of software, and so on. There are essentially three main categories of vulnerability scanners: network, host, and application. A network vulnerability scanner probes a host or hosts for issues across their network connections. Typically, a network scanner will either contain or use a port scanner to perform an initial assessment of the network to determine which hosts are alive and which services are open on those hosts. It then probes each system and service. Network scanners are very broad tools that can run potentially thousands of checks, depending on the OS and services being examined. This makes them a very good “broad sweep” for network-visible vulnerabilities. Due to the number of checks they can perform, network scanners can generate a great deal of traffic and a large number of connections to the systems being examined, so you should take care to minimize the impact on production systems and production networks. Network scanners are essentially the equivalent of a Swiss army knife for assessments. They do lots of tasks and are extremely useful to have around—they may not be as good as a tool dedicated to examining one specific type of service, but if you can only run a single tool to examine your network for vulnerabilities, you’ll want that tool to be a network vulnerability scanner. Figure 7-2 shows a screenshot of Nessus from Tenable Network Security, a very popular network vulnerability scanner.
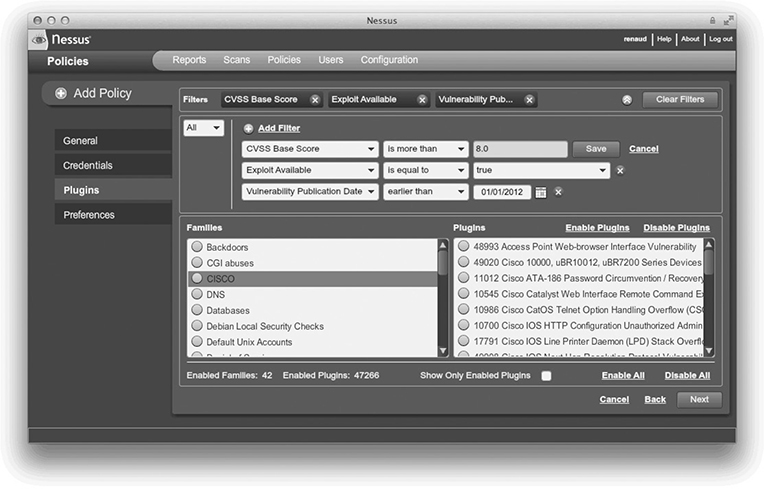
Figure 7-2 Nessus—a network vulnerability scanner
Bottom line: If you need to perform a broad sweep for vulnerabilities on one or more hosts across the network, a network vulnerability scanner is the right tool for the job.
Host vulnerability scanners are designed to run on a specific host and look for vulnerabilities and misconfigurations on that host. Host vulnerability scanners tend to be more specialized than network vulnerability scanners because they’re looking for issues associated with a specific operating system or set of operating systems. A good example of a host vulnerability scanner is the Microsoft Baseline Security Analyzer (MBSA), shown in Figure 7-3. MBSA is designed to examine the security state of a Windows host and offer guidance to address any vulnerabilities, misconfigurations, or missing patches. Although MBSA can be run against remote systems across the network, it is typically run on the host being examined and requires you to have access to that local host (at the Administrator level). The primary thing to remember about host vulnerability scanners is that they are typically looking for vulnerabilities on the system they are running on.
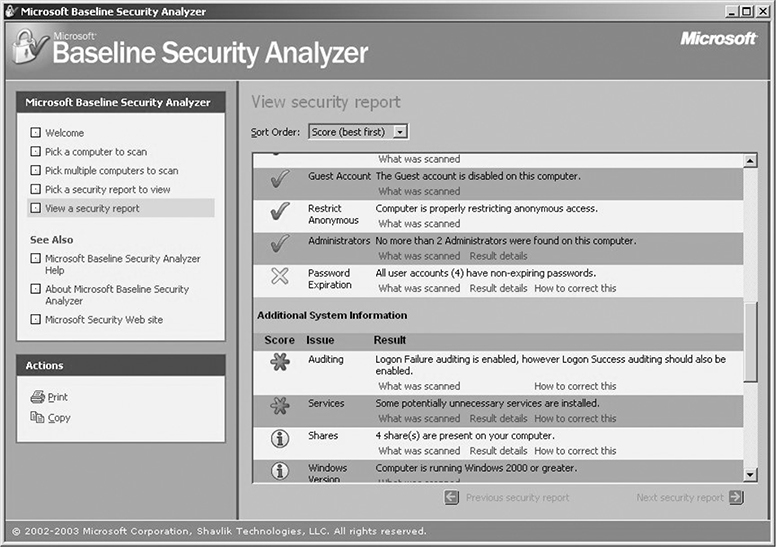
Figure 7-3 Microsoft Baseline Security Analyzer

EXAM TIP If you want to scan a specific host for vulnerabilities, weak password policies, or unchanged passwords, and you have direct access to the host, a host vulnerability scanner might be just the tool to use.
It’s worth nothing that some tools (such as Nessus) really cross the line between network-based and host-based vulnerability scanners. If you supply Nessus with host, login, and domain credentials, it can perform many checks that would be considered “host based.”
Selecting the right type of vulnerability scanner isn’t that difficult. Just focus on what types of vulnerabilities you need to scan for and how you will be accessing the host, services, or applications being scanned. It’s also worth noting that to do a thorough job, you will likely need both network-based and host-based scanners—particularly for critical assets. Host- and network-based scanners perform different tests and provide visibility into different types of vulnerabilities. If you want to ensure the best coverage, you’ll need to run both.
Application vulnerability scanners are designed to look for vulnerabilities in applications or certain types of applications. Application vulnerability scanners are some of the most specialized scanners—even though they contain hundreds or even thousands of checks, they only look for misconfigurations or vulnerabilities in a specific type of application. Different types of application vulnerability scanners operate against different types of applications. Some scanners are specific to an application, while others are specific to a type of application, as in web-based applications.
Arguably the most popular type of application vulnerability scanners are designed to test for weaknesses and vulnerabilities in web-based applications. Web applications are designed to be visible, interact with users, and accept and process user input—all things that make them attractive targets for attackers. As such, a relatively large number of web application scanners are available, ranging from open source to subscription fee basis. To be an effective web application scanner, the tool must be able to perform thousands of checks for vulnerabilities, misconfigurations, default content, settings, issues, and so on, with a variety of web technologies from IIS to Apache to PHP to ASP and everything else in between. Application vulnerability scanners are usually capable of performing advanced checks, such as SQL injection or JavaScript injection, that require interacting with the web application being examined and modifying requests and responses based on feedback from the application. Figure 7-4 shows a screenshot of Acunetix WVS (Web Vulnerability Scanner), an application vulnerability scanner specifically for web technologies.

Figure 7-4 Acunetix WVS

EXAM TIP If you want to examine a specific application or multiple instances of the same type of application (such as a website), an application vulnerability scanner is the tool of choice.
Configuration Compliance Scanner
The need to automate configuration checks has existed for years, and became important enough that a standard format was developed. SCAP, Security Content Automation Protocol, is a protocol to manage information related to security configurations and the automated validation of them. There is a wide variety of configuration compliance scanners that can perform this task, some SCAP compliant, some not, all with the intended purpose of informing system administrators whether or not their systems align with their defined requirements. The use of these tools requires that a baseline set of defined configurations is established and then the tools can track changes as the defined baseline changes. In most cases, the tool can be used to establish a baseline upon its first operation and set to measure deviations in future cycles.
Exploitation Frameworks
Exploitation frameworks are tool sets designed to assist hackers in the tasks associated with exploiting vulnerabilities in a system. These frameworks are important because the exploitation path typically involves multiple steps, all done in precise order on a system to gain meaningful effect. The most commonly used framework is Metasploit, a set of “tools” designed to assist a penetration tester in carrying out the steps needed to exploit a vulnerability on a system. These frameworks can be used by security personnel as well, specifically to test the exploitability of a system based on existing vulnerabilities and employed security controls.
Data Sanitization Tools
Data sanitization tools are tools used to destroy, purge, or otherwise identify for destruction specific types of data on systems. Before a system can be retired and disposed of, you need to sanitize the data needs. There are several approaches, the first being the whole disk approach. You can use a data sanitization tool to erase or wipe the entire storage of the system, making the data no longer recoverable. One method of doing this is to use self-encrypting disks, and the destruction of the key leaves the disk unrecoverable. A second, more targeted approach is to identify the sensitive data and deal with it specifically. Tools such as Identity Finder excel at this aspect of data sanitization. As with all tools, it is not the tool that provides the true value, but rather the processes and procedures that ensure the work is done and done correctly when required.
Steganography Tools
Steganography tools are designed to perform the act of steganography. Steganography is the science of hidden writing, or more specifically the hiding of messages in other content. Historically, this has been done by painting over messages, and later removing the cover paint, as well as other methods. Today, this is done within digital data streams. Because of the nature of digital images, videos, and audio files and the excess coding capacity in the stream, it is possible to embed additional content in the file. If this content is invisible to the typical user, then it is considered to be steganography. The same techniques are used to add visible (or invisible) watermarks to files so that their lineage can be traced. These watermarks can be used to trace documents, even serialize copies, so a firm can tell who leaks critical information, as each copy of a document is unique and traceable to a specific authorized user.
Honeypot
A honeypot is a server that is designed to act like the real server on a corporate network, but rather than having the real data, the data it possesses is fake. Honeypots serve as attractive targets to attackers. A honeypot acts as a trap for attackers, as traffic in the honeypot can be assumed to be malicious.
A honeynet is a network designed to look like a corporate network, but is made attractive to attackers. A honeynet is a collection of honeypots. It looks like the corporate network, but because it is known to be a false copy, all of the traffic is assumed to be illegitimate. This makes it easy to characterize the attacker’s traffic and also to understand where attacks are coming from.
Backup Utilities
Backup utilities are tools designed to perform one of the most important tasks in computer security, the backing up of data in case of loss. Backing up a single system isn’t that hard; a simple utility can manage it. Backing up an enterprise full of servers and workstations is a completely different problem with issues of segregating data, scale, and management of the actual backup files. This requires real tools to manage the process and scale it to enterprise class. Managing backups is a critical security task, for only by understanding the current backup posture does the security team know the status of this critical security function.
Banner Grabbing
Banner grabbing is a technique used to gather information from a service that publicizes information via a banner. Banners can be used for many things; for example, they can be used to identify services by type, version, and so forth, and they enable administrators to post information, including warnings, to users when they log in. Attackers can use banners to determine what services are running, and typically do for common banner-issuing services such as HTTP, FTP, SMTP, and Telnet. Figure 7-5 shows a couple of banner grabs being performed from a Telnet client against a web server. In this example, Telnet sends information to two different web servers and displays the responses (the banners). The top response is from an Apache instance (Apache/2.0.65) and the bottom is from Microsoft IIS (Microsoft-HTTPAPI/2.0).
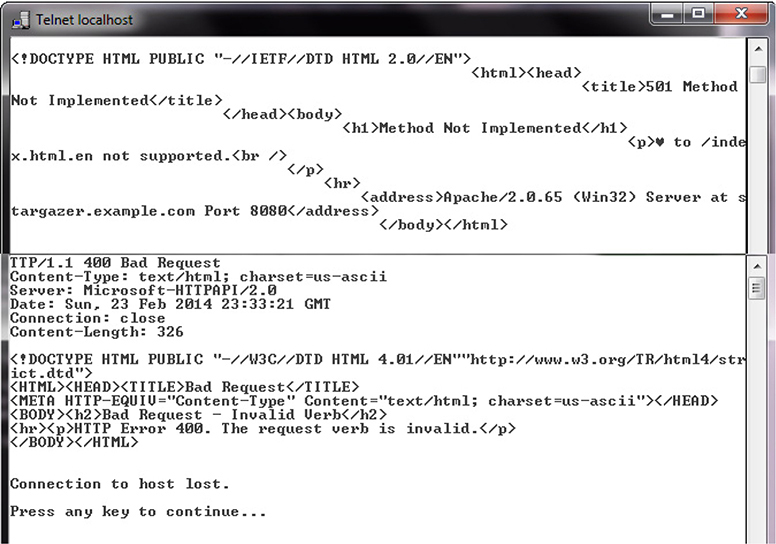
Figure 7-5 Banner grabbing using Telnet
If an organization wishes to raise the bar for attackers, they can change the banners to be less specific, masking the true revision and, in some cases, the actual type of service provider. This will only serve to slow down an adversary, but each element that forces more attempts, more time acts in the defenders interests, it provides time to catch an attacker.
Passive vs. Active
Tools can be classified as passive or active. Passive tools are those that do not interact with the system in a manner that would permit detection, as in sending packets or altering traffic. An example of a passive tool is Tripwire, which can detect changes to a file based on hash values. Another example of a passive tool is Wireshark, which, among other passive activities, performs OS mapping by analyzing TCP/IP traces. Passive sensors can use existing traffic to provide data for analysis.
Active tools interact with a target system in a fashion where their use can be detected. Scanning a network with Nmap is an active interaction that can be detected. In the case of Nmap, the tool itself may not be specifically detectable, but its use, the sending of packets, can be detected. When you need to map out your network or look for open services on one or more hosts, a network scanner is probably the most efficient tool for the job.
When determining whether to use a passive tool or an active tool, attackers may consider how much time they have available to carry out the attack. If an attacker has plenty of time, he likely will choose a passive scanner rather than a more invasive tool, such as Nmap, because he can collect the same information with less risk of detection. But the passive tool is subject to a couple of limitations; it can only detect systems based on their behavior on a network, and its collection point must be on the path between source and destination of conversations associated with the system being examined. An active tool can use the network to carry its interrogatory packets to a host and back, eliminating the location issue (to a degree), but also at the cost of alerting the system that it is being interrogated.

EXAM TIP Passive tools receive traffic only and do nothing to the traffic flow that would permit detection that they are interacting with the network. Active tools modify or send traffic and thus are discoverable by their traffic patterns.
Command-Line Tools
There are many command-line tools that provide a user direct information concerning a system. These are built into the operating system itself, or are common programs that are used by system administrators and security professionals on a regular basis.

EXAM TIP The fact that exam objective 2.2 enumerates a specific set of command-line tools means you should be prepared for performance-based questions targeting specific tools. You should know how and when to use each of these tools.
ping
The ping command sends echo requests to a designated machine to determine if communication is possible. The syntax is ping [options] targetname/address. The options include items such as name resolution, how many pings, data size, TTL counts, and more. Figure 7-6 shows a ping command on a Windows machine.
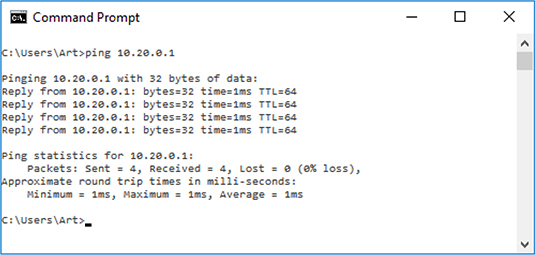
Figure 7-6 Ping command
netstat
The netstat command is used to monitor network connections to and from a system. The following are some examples of how you can use netstat:
• netstat –a Lists all active connections and listening ports
• netstat –at Lists all active TCP connections
• netstat –an Lists all active UDP connections
Many more options are available and useful. The netstat command is available on Windows and Linux, but availability of certain netstat command switches and other netstat command syntax may differ from operating system to operating system.
tracert
The tracert command is a Windows command for tracing the route that packets take over the network. The tracert command provides a list of the hosts, switches, and routers in the order that a packet passes by them, providing a trace of the network route from source to target. As tracert uses ICMP, if ICMP is blocked, tracert will fail to provide information. On Linux and macOS systems, the command with similar functionality is traceroute.
nslookup/dig
The DNS system is used to convert a name into an IP address. There is not a single DNS system, but rather a hierarchy of DNS servers, from root servers on the backbone of the Internet, to copies at your ISP, your home router, and your local machine, each in the form of a DNS cache. To examine a DNS query for a specific address, you can use the nslookup command. Figure 7-7 shows a series of DNS queries executed on a Windows machine. In the first request, the DNS server was with an ISP, while on the second request, the DNS server was from a VPN connection. Between the two requests, the network connections were changed, resulting in different DNS lookups.
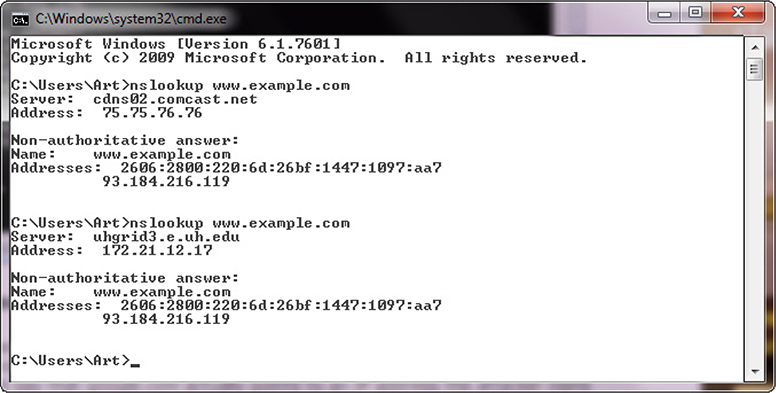
Figure 7-7 nslookup of a DNS query
At times, nslookup will return a nonauthoritative answer, as shown in Figure 7-8. This typically means the result is from a cache as opposed to a server that has an authoritative (that is, known to be current) answer, such as from a DNS server.
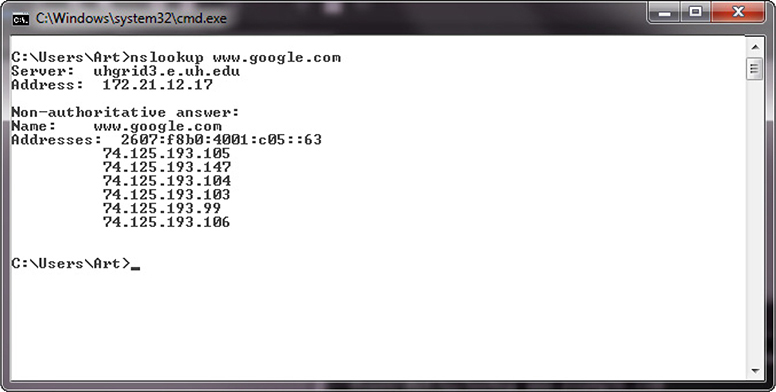
Figure 7-8 Cache response to a DNS query
While nslookup works on Windows systems, the command dig works on Linux systems. One difference is that dig is designed to return answers in a format that is easy to parse and include in scripts, a common trait of Linux command-line utilities.
arp
The arp command is designed to interface with the operating system’s Address Resolution Protocol (ARP) caches on a system. In moving packets between machines, a device sometimes needs to know where to send a packet using the MAC or layer 2 address. ARP handles this problem through four basic message types:
• ARP request “Who has this IP address?”
• ARP reply “I have that IP address; my MAC address is…”
• Reverse ARP (RARP) request “Who has this MAC address?”
• RARP reply “I have that MAC address; my IP address is…”
These messages are used in conjunction with a device’s ARP table, where a form of short-term memory associated with these data elements resides. The commands are used as a simple form of lookup. When a machine sends an ARP request to the network, the reply is received and entered into all devices that hear the reply. This facilitates efficient address lookups, but also makes the system subject to attack.
The arp command allows a system administrator the ability to see and manipulate the ARP cache on a system. This way they can see if entries have been spoofed or if other problems, such as errors, occur.
ipconfig/ip/ifconfig
Both ipconfig (for Windows) and ifconfig (for Linux) are command-line tools to manipulate the network interfaces on a system. They have the ability to list the interfaces and connection parameters, alter parameters, and refresh/renew connections. If you are having network connection issues, this is one of the first tools you should use, to verify the network setup of the operating system and its interfaces.
The ip command in Linux is used to show and manipulate routing, devices, policy routing, and tunnels.
tcpdump
The tcpdump utility is designed to analyze network packets either from a network connection or a recorded file. You also can use tcpdump to create files of packet captures, called pcap files, and perform filtering between input and output, making it a valuable tool to lessen data loads on other tools. For example, if you have a complete packet capture file that has hundreds of millions of records, but you are only interested in one server’s connections, you can make a copy of the pcap file containing only the packets associated with the server of interest. This file will be smaller and easier to analyze with other tools.
nmap
Nmap is a program developed by Gordon Lyon and has been the standard network mapping utility for Windows and Linux since 1999. The nmap command is the command-line command to launch and run the nmap utility.
netcat
Netcat is the network utility designed for Linux environments. It has been ported to Windows, but is not regularly used in windows environments. The actual command-line command to invoke netcat is nc –options –address.
The netcat utility is the tool of choice in Linux for reading from and writing to network connections using TCP or UDP. Like all Linux command-line utilities, it is designed for scripts and automation. Netcat has a wide range of functions. It acts as a connection to the network and can act as a transmitter, or a receiver, and with redirection it can turn virtually any running process into a server. It can listen on a port and pipe the input it receives to the process identified.

EXAM TIP You should know what each of these tools looks like when being used. If presented with output from one of the tools, you should be able to identify the tool that was used.
Security Technologies
There are several security technologies that you can employ to analyze security situations. The following technologies are presented to prepare you to answer performance-based exam questions related to CompTIA Security+ objective 2.4, Given a scenario, analyze and interpret output from security technologies. You should focus on understanding what information each of these technologies can provide and how to analyze and interpret that output to address a security problem.
HIDS/HIPS
Both a host-based intrusion detection system (HIDS) and a host-based intrusion prevention system (HIPS) alert on behaviors that match specified behavioral patterns. Unlike antivirus detection, where the likelihood of a false negative is low, a HIDS/HIPS can have significant false positive rates depending upon the specificity of the ruleset. For this reason, coupled with the basic purpose of these systems, they serve to act as an alerting mechanism to provide a signal to start incident response activities. The primary difference between a HIDS and a HIPS is that a HIPS is designed to provide automated responses to conditions to prevent intrusions. Rather than just alerting an operator, a HIPS can send a TCP reset signal to a device, breaking the communication path.
Antivirus
Antivirus (AV) applications check files for matches to known viruses and other forms of malware. Should your AV solution alert you, the only wise course of action is to either quarantine the file or erase it using the AV utility.
File Integrity Check
Whenever you download a file from an online source, even if from the vendor of the file, you should perform a file integrity check to ensure that the file has not been tampered with in any fashion. This will alert you to a changed binary, even if the hosting agent of the file doesn’t know about the specific issue. File integrity checks operate by taking a hash of the file and comparing this value to an offline store of correct values. If the hashes match, then the file is unaltered. On Microsoft Windows machines, a system file integrity check can be performed using the command line command sfc /scannow.
Host-Based Firewall
A host-based firewall is a firewall located on a host system. Because of the firewall’s proximity to a single system, you can tune it to the exact specifications of that machine, making it highly specific in its granularity of function. When you have high-value servers, a host-based firewall can provide specific connection specificity, allowing only permitted addresses and ports to access the machine. If properly tuned, a host-based firewall will have a very low false positive rate, and when it blocks connections, if there are repeated attempts, this is a sign of an active attack against the server.
Application Whitelisting
Application whitelisting is a technology that marks files as safe to run on a system based upon their hash values. This allows only specified binaries to be run on a system. For machines with a limited number of applications, this can be a powerful tool to combat many forms of malware. On Microsoft Windows machines using the Enterprise version of the OS, whitelisting can be done natively in the OS via a tool called applocker.
Removable Media Control
Removable media represents a potential data exfiltration pathway, as well as a pathway for malware into a system. Removable media controls are designed to prevent the transfer of data from a system to a removable media location, such as a flash drive or an external hard drive. There are multiple ways of doing this, but one of the most common is an encryption-based method, by which the files being transferred are encrypted to a key kept on the original system. This allows external media to be used to back up files, but they cannot be used to transfer data, as the key is on the original system and not accessible outside that machine.
Advanced Malware Tools
Advanced malware tools include tools such as Yara, a command-line pattern matcher that looks for indicators of compromise in a system. Yara assists security engineers in hunting down malware infections based on artifacts that the malware leaves behind in memory. Another type of advanced malware tool is a threat prevention platform that analyzes a system and its traffic in real time and alerts engineers to common malware artifacts such as callbacks to external devices.
Patch Management Tools
Patch management can be a daunting task. Administrators have to consider patches not only for the operating systems, but also for applications. In an enterprise with multiple machines that have different configurations, the task of maintaining software in a patched state is a significant chore. Patch management tools assist administrators by keeping lists of the software on a system and alerting users when patches become available. Some of these tools can even assist in the application of the patches. Having the tool alert users when patches are available is only part of the necessary solution; it is also necessary to ensure that the patches are installed, and there are tools to alert administrators when patches have not been updated in a timely fashion.
UTM
Unified threat management (UTM) is a marketing term used to describe all-in-one devices employed in network security. UTM devices typically provide a wide range of services, including switching, firewall, IDS/IPS, anti-malware, anti-spam, content filtering, and traffic shaping. These devices are designed to simplify security administration and are targeted for small and midsized networks. Because of the wide range of services UTMs provide, they are typically located at the edge of the network, managing traffic in and out of the network. When a UTM alerts, it is best to treat the alert like any other action that triggers an incident response and investigate the cause.
DLP
Data loss prevention (DLP) refers to technology employed to detect and prevent transfers of data across an enterprise. Employed at key locations, DLP technology can scan packets for specific data patterns. You can tune this technology to detect account numbers, secrets, specific markers, or files. When specific data elements are detected, the system can block the transfer. The primary challenge in employing DLP technologies is the placement of the sensor. The DLP sensor needs to be able to observe the data, so if the channel is encrypted, DLP technology can be thwarted. When a DLP system alerts that an issue has arisen with respect to blocking the potential exfiltration of protected information, this alarm should result in an investigation by an incident response team.
Data Execution Prevention
Data execution protection (DEP) is the protection of specific memory areas as nonexecutable in a Windows system. Implemented post Windows XP DEP combines with other technologies to prevent attackers from changing the operation of a program through code injection into a data storage location and then subsequently executing the code. Should a system detect a DEP violation, the OS will kill the program. Should this issue repeat, it is highly suspect that the program has been tampered with and needs to be reloaded.
Web Application Firewall
A web application firewall (WAF) is a device that performs restrictions based on rules associated with HTTP/HTTPS traffic. By definition, web application firewalls are a form of content filter, and their configuration capabilities allow them to provide significant capability and protections. The level of specificity in what can be allowed or blocked can be as precise as “allow Facebook but block Facebook games.” WAFs can detect and block disclosure of critical data, such as account numbers, credit card numbers, and so on. WAFs can also be used to protect websites from common attack vectors such as cross-site scripting, fuzzing, and buffer overflow attacks.
You can configure a web application firewall to examine inside an SSL session. This is important if an attacker is attempting to use an encrypted channel such as SSL to mask her activity. Because legitimate SSL channels are instantiated by the system, you can pass the appropriate credentials internally to the WAF to enable SSL inspection.

EXAM TIP This last section of the chapter has covered a bunch of different tools, each designed for a different purpose. Do not lose sight of the objective: Given a scenario, analyze and interpret output from security technologies. What can you do or not do with each of these technologies?
Chapter Review
In this chapter, you became acquainted with the appropriate software tools to assess the security posture of an organization. These tools include protocol analyzers, network scanners, rogue system detectors, network mapping tools, wireless scanners/crackers, password crackers, vulnerability scanners, configuration compliance scanners, exploitation frameworks, data sanitization tools, steganography tools, honeypots, backup utilities, and banner grabbing tools. You also learned the difference between passive and active tools. The chapter then explored a series of command-line tools and their application in security. The tools covered include ping, netstat, tracert, nslookup/dig, arp, ipconfig/ifconfig, tcpdump, nmap, and netcat.
The chapter closed with an overview of analyzing and interpreting the output from security technologies, including HIDS/HIPS, antivirus, file integrity checkers, host-based firewalls, application whitelisting, removable media controls, advanced malware tools, patch management tools, UTM, DLP, DEP, and web application firewalls. It is important to note that this chapter covers scenario-based performance objectives, and as such, you should be ready to demonstrate how you would employ the utilities described in the chapter.
Questions
To help you prepare further for the CompTIA Security+ exam, and to test your level of preparedness, answer the following questions and then check your answers against the correct answers at the end of the chapter.
1. What kind of tool is Wireshark?
A. Scanner
B. Steganography
C. Malware
D. Protocol analyzer
2. There are reports of a worm going through your company that communicates to other nodes on port TCP/1337. What tool would you use to find infected nodes on your network?
A. Protocol analyzer
B. Advanced malware tool
C. Network scanner
D. Password cracker
3. Why should you never use a network scanner on a network you are not authorized to scan?
A. A network scanner or port scanner is the same tool that an attacker would use.
B. It might crash the network switch.
C. Being too efficient at finding network information will cause you to get more work.
D. It will slow down your work machine with ancillary traffic.
4. Your manager comes to you with an audit finding that 85 percent of the machines on your network are vulnerable to a variety of different exploits. He wants you to verify the findings of the report. What would be the best tool for this?
A. Protocol analyzer
B. Network scanner
C. Vulnerability scanner
D. All of the above
5. What is the most common use of data sanitization tools?
A. Clearing web-form fields between user sessions
B. Erasing hard drives before computers are recycled
C. Removing PII from a database
D. Integrating with a data loss prevention system
6. Your organization has been hit with multiple targeted network attacks over the last few months resulting in two data breaches. To attempt to discover how the attackers are getting into your systems, you set up a few vulnerable virtual machines with fake data on them that look like the organization’s real machines. What defense mechanism have you built?
A. Passive sensors
B. Network-based intrusion detection system (NIDS)
C. DMZ
D. A honeynet
7. The tcpdump command-line tool is classified as which of the following?
A. Network scanner
B. Password cracker
C. Protocol analyzer
D. Data sanitization tool
8. Why should you compare hashes of the files you download from the Internet to a library of known hash values?
A. It prevents the spread of malware by checking a file’s integrity.
B. It prevents you from running the incorrect application.
C. It protects the data stored in the file.
D. The hash is needed to decrypt the file.
9. What two things can removable media control do to improve security?
A. Prevent data sharing and prevent executables from running
B. Prevent infiltration of malware and prevent exfiltration of data
C. Provide secure log storage and provide portable encryption
D. Provide a sandbox location for malware and provide network access control
10. Which of the following describes most network tools that are designed to detect an attack?
A. Active
B. Passive
C. Linux based
D. Windows based
11. List at least three ways host vulnerability scanners are different from network vulnerability scanners: _______________ ____________ _______________.
12. A network scanner will usually list a port on a remote machine as one of which three classifications? ___________ _____________ ____________
Answers
1. D. Wireshark is a protocol analyzer that can make visual displays of IP traffic.
2. C. A network scanner that searches for particular ports can help detect infected machines.
3. A. Because a network scanner operates the same way that an attacker would operate a port scanner against your network to search for vulnerable machines, many companies prohibit the use of a network scanner on any corporate machines.
4. C. A vulnerability scanner is the best tool for the task. A protocol analyzer allows you to examine packets, not systems for vulnerabilities. A network scanner maps systems, but has limited vulnerability scanning capability.
5. B. The most common use of a data sanitization tool is to erase hard drives of any potential sensitive data before they are recycled.
6. D. A honeynet is composed of several vulnerable machines deployed to purposely be attacked.
7. C. The tcpdump command-line tool is a protocol analyzer that allows you to filter and display all the network traffic going to a machine, or save it in files for later viewing.
8. A. Comparing the file’s hash ensures that the file has not been altered from the known good file, which prevents the spread of malware because most changes are due to a virus being implanted in the file.
9. B. Removable media control can prevent a path for malware to enter the organization, and can prevent the exfiltration of sensitive data from the organization.
10. B. The majority of detection tools are passive, in that they wait for something in the environment to change as an indicator of an attack. Most tools have equivalents for both Windows and Linux, since the detection is not dependent upon the host system being attacked.
11. Host vulnerability scanners are different from network vulnerability scanners by:
• Being more specialized
• Requiring high-level access to the local host, typically Administrative access
• Scanning for vulnerabilities on a specific operating system
• Generally only running against a single host
• Being able to find more in-depth issues such as missing patches and unchanged passwords
12. Network scanners will typically return a port’s status as either open, closed, or filtered.