In this chapter you will
• Describe wireless network architecture and terminology
• Identify wireless network types and forms of authentication
• Describe wireless encryption algorithms
• Identify wireless hacking methods and tools
• Describe mobile platform attacks
• Identify Mobile Device Management
Some people like love stories, some like mysteries, and some prefer watching explosions and gunfire in action movies. As for me, I am a certified horror movie nut. I love watching movies about monsters, ghosts, spooks, blood, and gore—just plain-old scarefests. One that got to me quite a bit when I was younger—even though it’s not really thought of as a true horror movie, I guess—was Poltergeist. And it even had some wireless hacking in it.
If you haven’t seen it, the story revolves around a young girl who is ghost-napped into another dimension. After moving into a new house, she starts talking to the “TV people” and, after a few shenanigans and some interesting furniture stacking by the ghosts, gets sucked into the “other side.” Some wranglings with ghost hunters and a really weird, melodramatic little woman finally lead to the return of the little girl, along with the best vacuum-cleaning a house has ever seen.
Oh, the wireless hacking? Well, at one point in the movie—before everything goes haywire—the dad is having a football party at the house. Several guys are sitting around a TV, hollering and yelling during a big play, when suddenly the picture changes...to a kid’s show. It seems the next-door neighbor had the same TV set and accompanying remote and was setting things up for his kid while the football party was going on. The neighbors argued and battled for some time with the remotes until, I can only guess, someone realized it was perfectly okay to just walk up and change the channel manually.
Hopefully your wireless hacking won’t result in attacks from the other side (insert deep, ominous laughter here) or even arguments with your next-door neighbor, but at least you understand what wireless hacking is nowadays. Back in the early 80s it didn’t even exist, and the idea was nearly as far-fetched as the still-cool Star Trek communicators we watched on reruns. Wireless hacking back then was nothing more than crossing a signal or two, talking over someone (or listening in to them) on a telephone, or playing with CB or scanner frequencies. Today, though, we’ve got worlds of wireless to discover and play with.
Look at virtually any study on wireless usage statistics in the United States and you’ll find we simply can’t live without wireless anymore. We use it at home, with wireless routers and access points becoming just as ubiquitous as refrigerators and toasters. We expect it when we travel, using hotspot access at airports, hotels, and coffee shops. We use wireless keyboards, mice, and virtually anything else we can point at and click (ceiling fan remote controls are all the rage now, don’t you know). We have our vehicles tied to cell phones, our cell phones tied to Bluetooth ear receivers, and satellites beaming television to our homes. Heck, we’re sometimes even beaming GPS information from our dogs. And I’d bet your network at home is still chirping away, even though you’re not there to use it, right? Surely you didn’t shut it all down before you left for the day.
Not to mention our devices are now more mobile than ever, and getting progressively smaller...and smarter. Where once mobile security concerns centered on data-at-rest encryption and pre-shared keys for wireless connectivity on the laptop, the smartphone is unquestionably the ruler of the airwaves today. People are using smartphones more and more as their primary networked interaction devices, and we need to focus attention appropriately.
Wireless and mobile computing is here to stay, and what a benefit it is to the world. The freedom and ease of use it offers are wonderful and, truly, are changing our society day by day. However, along with that we have to use a little caution. If data is sent over the airwaves, it can be received over the airwaves—by anyone (maybe not in clear text, and maybe not easily discernable, but it can be received). Therefore, we need to explore the means of securing our data and preventing accidental spillage. And that, Dear Reader, is what this chapter is all about.
Although it’s important to remember that any discussion on wireless should include all wireless mediums (phones, keyboards, and so on), this section is going to focus primarily on wireless data networking. I’m not saying you should forget the rest of the wireless world—far from it. In the real world you’ll find as many, if not more, hacking opportunities outside the actual wireless world network. What we do want to spend the vast majority of our time on, however, are those that are testable issues. And, because EC-Council has defined the objectives this way, we will follow suit.
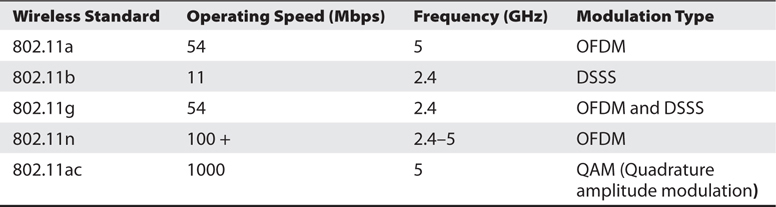
A wireless network is built with the same concerns as any other media you decide to use. You have to figure out the physical makeup of the transmitter and receiver (NIC) and how they talk to one another. There has to be some order imposed on how clients communicate to avoid collisions and useless chatter. There also must be rules for authentication, data transfer, size of packets, and so on. In the wireless data world, these are all defined with standards, known as the 802.11 series. Although you probably won’t get more than a couple of questions on your exam referencing the standards, you still need to know what they are and basic details about them. Table 7-1 summarize these standards.
Table 7-1 Wireless Standards
One other note of interest when it comes to the standards we’re chatting about here is the method wireless networks use to encode messages onto the media in use—the airwaves. In the wired world, we can encode using various properties of the electrical signal itself (or, if using fiber, the light wave); however, in wireless there’s nothing physical for the machine to “touch.” Modulation—the practice of manipulating properties of a waveform—then becomes the encoding method of choice. There are nearly endless methods of modulating a waveform to carry a signal, but the two you’ll need to know in wireless are OFDM and DSSS (QAM is very new and isn’t touched on your exam).
Both orthogonal frequency-division multiplexing (OFDM) and direct-sequence spread spectrum (DSSS) use various pieces of a waveform to carry a signal, but they go about it in different ways, and the best way I can think to explain it comes in the form of a discussion about your cable television set. See, the cable plugged into the back of your TV is capable of carrying several different frequencies of waveforms, and all of them are plowing into the back of your TV right now. You watch one of these waveforms by tuning your TV specifically to that channel.
In this oversimplified case, the cable is split into various channels, with each one carrying a specific waveform. OFDM works in this same manner, with several waveforms simultaneously carrying messages back and forth. In other words, the transmission media is divided into a series of frequency bands that don’t overlap each other, and each of them can then be used to carry a separate signal. DSSS works differently by combining all the available waveforms into a single purpose. The entire frequency bandwidth can be used at once for the delivery of a message. Both technologies accomplish the same goal, just in different ways.
As for a basic wireless network setup, you’re probably already well aware of how it’s done. There are two main modes a wireless network can operate in. The first is ad hoc, which is much like the old point-to-point networks in the good old days. In ad hoc mode, your system connects directly to another system, as if a cable were strung between the two. Generally speaking, you shouldn’t see ad hoc networks appearing very often, but park yourself in any open arena (such as an airport or bus station) and see how many pop up.
Infrastructure mode is the one most networks are set up as and the one you’ll most likely be hacking. Whereas ad hoc connects each system one to another, infrastructure makes use of an access point (AP) to funnel all wireless connections through. A wireless access point is set up to connect with a link to the outside world (usually some kind of broadband router). This is an important consideration when you think about it—wireless devices are usually on completely different subnets than their wired cousins. If you remember our discussion on broadcast and collision domains, you’ll see quickly why this is important to know up front.
Clients connect to the access point using wireless NICs; if the access point is within range and the device understands what it takes to connect, it is allowed access to the network. Wireless networks can consist of a single access point or multiple ones, thus creating overlapping “cells” and allowing a user to roam freely without losing connectivity. This is also an important consideration when we get to generating wireless packets later in this chapter. The client needs to “associate” with an access point first and then “disassociate” when it moves to the next one. This dropping and reconnecting will prove vital later, trust me.
We should probably pause here for a brief introduction to a couple of terms. Keep in mind these may not necessarily be testable items as far as EC-Council is concerned, but I think they’re important nonetheless. When you have a single access point, its “footprint” is called a basic service area (BSA). Communication between this single AP and its clients is known as a basic service set (BSS). Suppose, though, you want to extend the range of your network by adding multiple access points. You’ll need to make sure the channels are set right, and after they’re set up, you will have created an extended service set (ESS). As a client moves from one AP in your subnet to another, so long as you’ve configured everything correctly, the client will disassociate from one AP and (re)associate with another seamlessly. This movement across multiple APs within a single ESS is known as roaming. Okay, enough vocabulary. It’s time to move on.
Another consideration to bring up here deals with the access points and the antennas they use. It may seem like a weird (and crazy) thing to discuss physical security concerns with wireless networks because by design they’re accessible from anywhere in the coverage area. However, that’s exactly the point: many people don’t consider it, and it winds up costing them dearly. Most standard APs use an omnidirectional antenna, which means the signal emanates from the antenna in equal strength 360 degrees from the source. Well, it’s at least close to 360 degrees anyway, since the farther away you get vertically from the signal, the exponentially worse the signal reception gets. But if you were to, say, install your AP in the corner of a building, three-quarters of your signal strength is lost to the parking lot. And the guy sitting out in the car hacking your network will be very pleased by this.
A better option may be to use a directional antenna, also sometimes known as a Yagi antenna.
Unidirectional antennas allow you to focus the signal in a specific direction, which greatly increases signal strength and distance. The benefit is obvious in protecting against the guy in the parking lot. However, keep in mind this signal is now greatly increased in strength and distance, so you may find that the guy will simply drive from his corner parking spot close to the AP to the other side of the building, where you’re blasting wireless out the windows. The point is, wireless network design needs to take into account not only the type of antenna used but where it is placed and what is set up to contain or corral the signal. The last thing you want is for some kid with a Pringles can a block away tapping into your network. The so-called cantenna is very real and can boost signals amazingly. Check out Figure 7-1 for some antenna examples.
Figure 7-1 Wireless antennas
Other antennas you can use are dipole and parabolic grid. Dipole antennas have, quite obviously, two signal “towers” and work omnidirectionally. Parabolic grid antennas are one type of directional antenna and work a lot like satellite dishes. They can have phenomenal range (up to 10 miles due to their power output) but aren’t in use much. Another directional antenna type is the loop antenna, which looks like a circle. And, in case you were wondering, a Pringles can will work as a directional antenna. Google it and you’ll see what I mean.
So, you’ve installed a wireless access point and created a network for clients to connect to. To identify this network to clients who may be interested in joining, you’ll need to assign a service set identifier (SSID). The SSID is not a password and provides no security at all for your network. It is simply a text word (32 characters or less) that identifies your wireless network. SSIDs are broadcast by default and are easily obtainable even if you try to turn off the broadcast (in an effort dubbed “SSID cloaking”). The SSID is part of the header on every packet, so its discovery by a determined attacker is a given, and securing it is virtually a moot point.
Once the AP is up and a client comes wandering by, it’s time to authenticate so an IP address can be pulled. Wireless authentication can happen in more than a few ways, from the simplistic to the complicated. A client can simply send an 802.11 authentication frame with the appropriate SSID to an AP and have it answer with a verification frame. Or, the client might participate in a challenge/request scenario, with the AP verifying a decrypted “key” for authentication. Whether Open System Authentication Process or Shared Key Authentication Process, respectively, the idea is to prove you belong.
If you want to get really crazy, you may even tie the whole thing together with an authentication server (RADIUS), forcing the client into an even more complicated authentication scenario. The key here is to remember there is a difference between association and authentication. Association is the action of a client connecting to an AP, whereas authentication actually identifies the client before it can access anything on the network.
Lastly, after everything is set up and engineered appropriately, you’ll want to take some steps toward security. This may seem like a laughable concept because the media is open and accessible to anyone within range of the AP, but there are some alternatives available for security. Some are better than others, but as the old saying goes, some security is better than none at all.
There are a host of wireless encryption topics and definitions to cover. I briefly toyed with an exhaustive romp through all of them but decided against it after thinking about what you really need to know for the exam. Therefore, I’ll leave some of the “in-the-weeds” stuff for another discussion, and many of the definitions to the glossary, and just stick with the big three here: WEP, WPA, and WPA-2.
WEP stands for Wired Equivalent Privacy and, in effect, doesn’t effectively encrypt anything. Now I know you purists are jumping up and down screaming about WEP’s 40- to 232-bit keys, yelling that RC4 is an encryption algorithm, and questioning whether a guy from Alabama should even be writing a book at all. But trust me, it’s not what WEP was intended for. Yes, “encryption” is part of the deal, but WEP was never intended to fully protect your data. It was designed to give people using a wireless network the same level of protection someone surfing over an Ethernet wired hub would expect: if I were on a hub, I wouldn’t expect that the guy in the parking lot could read what I send and receive because he wouldn’t have physical access to the wire.
Now think about that for a moment—wired equivalent privacy. No minimally educated security person walking upright and capable of picking glazed doughnuts over cake ones would ever consider a hub secure. Granted, it’s harder than sitting out in the hallway with an antenna and picking up signals without even entering the room, but does it really provide anything other than a discouragement to casual browsers? Of course not, and so long as it’s implemented that way, no one can be upset about it.
WEP uses something called an initialization vector (IV) and, per its definition, provides for confidentiality and integrity. It calculates a 32-bit integrity check value (ICV) and appends it to the end of the data payload and then provides a 24-bit IV, which is combined with a key to be input into an RC4 algorithm. The “keystream” created by the algorithm is encrypted by an XOR operation and combined with the ICV to produce “encrypted” data. Although this all sounds well and good, it has one giant glaring flaw: it’s ridiculously easy to crack.
WEP’s initialization vectors are relatively small and, for the most part, get reused pretty frequently. Additionally, they’re sent in clear text as part of the header. When you add this to the fact that we all know the cipher used (RC4) and that it wasn’t ever really designed for more than one-time usage, cracking becomes a matter of time and patience. An attacker simply needs to generate enough packets in order to analyze the IVs and come up with the key used. This allows him to decrypt the WEP shared key on the fly, in real time, and renders the encryption useless.
Does this mean WEP is entirely useless and should never be used? As far as your exam goes, that answer may as well be yes, but how about in the real world? Is a WEP-protected connection in a hotel better than the wired outlet provided to you in the room? That’s probably something you need to think about. You may prefer the protection the WEP connection gives you over the complete absence of anything on the wired connection. Not to mention, you don’t really know what’s on the other end of that port. The point is that while WEP shouldn’t be considered a secured network standard for your organization, and it will be roundly destroyed on the exam as being worthless, there are still plenty of uses for it, and it may turn out to be the best choice for specific situations in your adventures.
A better choice in encryption technology is Wi-Fi Protected Access (WPA) or WPA2. WPA makes use of something called Temporal Key Integrity Protocol (TKIP), a 128-bit key, and the client’s MAC address to accomplish much stronger encryption. The short of it is, WPA changes the key out (hence the “temporal” part of the name) every 10,000 packets or so, instead of sticking with one and reusing it, as WEP does. Additionally, the keys are transferred back and forth during an Extensible Authentication Protocol (EAP) authentication session, which makes use of a four-step handshake process to prove the client belongs to the AP, and vice versa.
WPA2 is much the same process; however, it was designed with the government and the enterprise in mind. In something called WPA-2 Enterprise, you can tie EAP or a RADIUS server into the authentication side of WPA2, allowing you to make use of Kerberos tickets and all sorts of additional goodies. But what if you just want to use it at home or on your small network and don’t want to bother with all those additional, and costly, authentication measures? No worries, WPA2 Personal is your bag, baby. Much like other encryption offerings, you simply set up a pre-shared key and give it only to those people you trust on your network.
A couple final notes on WPA2 include encryption and integrity. Whether enterprise or personal, it uses AES for encryption, ensuring FIPS 140-2 compliance—not to mention AES is just plain better. As for integrity, believe it or not, TKIP had some irregularities originally. WPA2 addresses these by using something called Cipher Block Chaining Message Authentication Code Protocol (CCMP), which sounds really technical and awesome. What CCMP really does is something everyone has been doing forever to ensure integrity—it simply uses something to show the message hasn’t been altered during transit. The rest of us call them hashes, but CCMP calls them message integrity codes (MICs), and the whole thing is done through a process called cipher block chaining message authentication code (CBC-MAC).
I’m sure you’ve seen your share of mathematical tomfoolery that appears to be “magic” or some Jedi mind trick. These usually start with something like “Pick a number between 1 and 10. Add 13. Divide by 2,” and so on, until the number you picked is arrived at. Magic, right? Well, I have one here for you that is actually relevant to our discussion on WEP cracking.
In the world of probability, there is a principle known as the “birthday problem.” The idea is that if you have a group of at least 23 random people, the odds are that two of them will share the same birthday. There’s a lot of math here, but the short of it is if you have 366 people, the probability is very near 100 percent. However, drop the number of people down to just 57 and the probability drops only 1 percentage point. Therefore, the next time you’re in a big group of people, you can probably win a bet that at least two of them share the same day as a birthday.
So, just how is this relevant to hacking? Well, the mathematics for this little anomaly led to a cryptographic attack called the birthday attack (also known as the birthday paradox). The same principles of probability that’ll win you a drink at the bar apply to cracking hash functions. Or, in this case, WEP keys.
So, there you have it. WEP, WPA, and WPA-2 are your wireless encryption measures. WEP is relatively easy to crack and according to your exam probably should never be used. However, on your home network you may be okay—especially if you take other, common sense, (dare I say it) defense-in-depth measures to protect yourself. WPA and WPA2 are much better choices from an overall security standpoint. The answer to the question “how do you crack WPA2?” is, unfortunately, not very easily. In fact, if the password in use is long or overly complex, it’s improbable you can get it done in any reasonable timeframe at all since the key has absolutely nothing to do with the password. It’s not completely impossible; it’s just really tough with AES. The only real way to accomplish this is to use a tool that creates the crypto key based on the password (which of course you don’t have). You must capture the authentication handshake used in WPA2 and attempt to crack the pair master key (PMK) from inside (tools such as Aircrack and KicMAC, a Mac OS X tool, can help with this), but it’s just not that easy to do. A comparison of WEP, WPA, and WPA2 is shown in Table 7-2.
Table 7-2 Wireless Encryption Comparison
When it comes to hacking wireless networks, the truly great news is you may not have much of it to do. Many networks have no security configured at all, and even those that do have security enabled don’t have it configured correctly. According to studies recently published by the likes of the International Telecommunications Union (ITU) and other equally impressive organizations, more than half of all wireless networks don’t have any security configured at all, and of the remainder, nearly half could be hacked within a matter of seconds. Granted, a large number of those are home networks that do not represent much of a valued target for hackers; however, the numbers for organization and business use are equally as eye-popping. If you think that’s good news for hackers, the follow-up news is even more exciting: wireless communication is expected to grow tenfold within the next few years. Gentlemen, and ladies, start your engines.
In versions past, ECC has spent a lot of time concentrating on finding wireless networks to hack. Thankfully, at least on this one thing, they’ve recognized reality and pulled back the reigns. Spending a lot of time talking about finding wireless networks makes as much sense as talking about how to find air. So we’re not talking about finding any wireless network—that’s too easy. What we are hoping to cover here is how you can find the wireless network you’re looking for—the one that’s going to get your team inside the target and provide you with access to all the goodies. The rest of this is just good-to-know information.
First up in our discussion of wireless network discovery are the “war” options. No matter which technique we’re talking about, the overall action is the same: an attacker travels around with a Wi-Fi-enabled laptop looking for open wireless access points/networks. In war driving, the attacker is in a car. War walking has the attacker on foot. War flying? I’m betting you could guess it involves airplanes.
Another option in wireless network discovery is the use of a wide array of tools created for that very purpose. However, before we cover the tools you’ll see mentioned on your exam, it’s relevant at this point to talk about the wireless adapter. No matter how great the tool is, if the wireless adapter can’t pull the frames out of the air in the correct manner, all is lost. Some tools are built this way and work only with certain chipset adapters, which can be frustrating at times.
The answer for many in wireless hacking is to invest in an AirPcap dongle (www.cacetech.com)—a USB wireless adapter that offers all sorts of advantages and software support (see Figure 7-2). Sure, it’s expensive, but it’s worth it. In addition to working with Aircrack-ng and other sniffing/injection wireless hacking applications, it provides a useful software distribution. AirPcapReplay is included in this and offers the ability to replay traffic from a captured file across the wireless network.
Figure 7-2 AirPcap USB
Barring this, you may need to research and download new and different drivers for your particular card. The madwifi project may be an answer for you (http://madwifi-project.org). At any rate, just keep in mind that, much like the ability of wired adapters to use promiscuous mode for your sniffing efforts, discussed earlier in this book, not all wireless adapters are created equal, and not all will work with your favorite tool. Be sure to check the user guides and man pages for lists and tips on correctly configuring your adapters for use.
I’ve already made mention of WIGLE (http://wigle.net) and how teams of miscreant hackers have mapped out wireless network locations using GPS and a tool called NetStumbler (see Figure 7-3). NetStumbler (www.netstumbler.com), the tool employed in this endeavor, can be used for identifying poor coverage locations within an ESS, detecting interference causes, and finding any rogue access points in the network (we’ll talk about these later). It’s Windows based, easy to use, and compatible with 802.11a, b, and g.
Figure 7-3 NetStumbler
Although it’s usually more of a wireless packet analyzer/sniffer, Kismet is another wireless discovery option. It works on Linux-based systems and, unlike NetStumbler, works passively, meaning it detects access points and clients without actually sending any packets. It can detect access points that have not been configured (and would then be susceptible to the default out-of-the-box admin password) and will determine which type of encryption you might be up against. You might also see two other interesting notables about Kismet on your exam: First, it works by “channel hopping,” to discover as many networks as possible. Second, it has the ability to sniff packets and save them to a log file, readable by Wireshark or tcpdump.
Another great network discovery tool is NetSurveyor (see Figure 7-4). This free Windows-based tool provides many of the same features as NetStumbler and Kismet. Additionally, it supports almost all wireless adapters without any significant additional configuration, which is of great benefit to hackers who can’t afford, or don’t have, an AirPcap card. NetSurveyor acts as a great tool for troubleshooting and verifying proper installation of wireless networks. To try it, simply download and install the tool and then run it. It will automatically find your wireless adapter and begin scanning. Click through the different menu options and check out all the information it finds without you needing to configure a thing!
Figure 7-4 NetSurveyor
First things first: wireless hacking does not need to be a complicated matter. Some simple attacks can be carried out with a minimum of technical knowledge and ability. Sure, there are some really groovy and, dare I say, elegant wireless hacks to be had, but don’t discount the easy ones. They will probably pay as many dividends as the ones that take hours to set up.
For example, take the concept of a rogue access point. The idea here is to place an access point of your own somewhere—heck, you can even put it outside in the bushes—and have legitimate users connect to your network instead of the original. Just consider the possibilities! If someone were to look at his wireless networks and connect to yours, because the signal strength is better or yours is free whereas the others are not, he’s basically signing over control to you. You could configure completely new DNS servers and have your AP configure them with the DHCP address offering. That would then route users to fake websites you create, providing opportunities to steal authentication information. Not to mention, you could funnel everything through a packet capture.
Sometimes referred to as “evil twin” (assuming the SSID on the rogue box is set similar to the legitimate one), an attack like this is incredibly easy to pull off. The only drawback is they’re sometimes really easy to see, and you run a pretty substantial risk of discovery. You’ll just have to watch out for true security-minded professionals because they’ll be on the lookout for rogue APs on a continual basis and (should) have plenty of tools available to help them do the job.
Another truly ridiculous attack is called the ad hoc connection attack. To be honest, it shouldn’t ever be successful, but after years in the security management business, I’ve seen users do some pretty wild things, so almost nothing surprises me anymore. An ad hoc connection attack occurs when an attacker simply sits down with a laptop somewhere in your building and advertises an ad hoc network from his laptop. Believe it or not, people will, eventually, connect to it. Yes, I know it’s tantamount to walking up to a user with a crossover cable in hand and asking, “Excuse me, would you please plug this in to your system’s NIC? The other end is in my computer and I’d like easy access to you.” But what can you do?
Another attack on the relatively easy side of the spectrum is the denial-of-service effort. This can be done in a couple of ways, neither of which is particularly difficult. First, you can use any number of tools to craft and send de-authenticate (disassociate) packets to clients of an AP, which will force them to drop their connections. Granted, they may try to immediately climb back aboard, but there’s nothing stopping you from performing the same action again. Or you can employ a rogue AP to have legitimate users connect, thereby removing their access to legitimate networked resources (in ECC lingo, an unauthorized association).
The other easy DoS wireless attack is to jam the wireless signal altogether, using some type of jamming device and, usually, a high-gain antenna/amplifier. All wireless devices are susceptible to some form of jamming and/or interference—it’s simply a matter of placing enough signals out in the airwaves that the NICs can’t keep up. Tons of jammer options are available (a quick Google search on wireless jammers will show you around 450,000 pages on the subject), ranging from 802.11 networks to Bluetooth and other wireless networking technologies. No, the giant jar of jam used in the movie Spaceballs won’t work, but anything generating enough signals in the 2.4GHz range would definitely put a crimp in an 802.11b network.
One of the goals for many illegitimate hackers is the plain old denial-of-service (DoS) attack. Whether it’s a resource, machine, segment, or entire network, sometimes shutting down communication is just as valuable to the bad guys as leaving it up and stealing things (especially in the military world). In wired communications we have all sorts of detection and defense options set up to help prevent against DoS attacks, but have you given any thought to the wireless world?
FCC rules and the Communication Act of 1934 make the marketing, selling, and/or using a jammer a federal offense and can result in seriously nasty punishment. Check almost any electronic device in your house right now: there will be an FCC warning saying that it will not create interference and that it will accept all interference. However, that doesn’t mean you can’t get a hold of these jammers. For example, the MGT P6 Wifi (www.magnumtelecom.com/Pages/gb/jammers.htm) is a small device about the size of a cell phone that can effectively shut down all Wi-Fi communication within a 20-meter radius. That may not sound like much, but if you’ve ever seen what happens in a board room when communications go down, you’d be nodding in agreement with me now that it’s something to be concerned about.
What if you increased the power output of that little device? Better yet, what if you have four or five of them to disperse around particularly important networked areas in an organization? Do you think that maybe causing a communications blackout for certain people in an organization might have an impact on their mission? How about its effect on social engineering opportunities? I can guarantee you if the 4th floor (or whatever floor your specific company’s executives sit on) starts having communications problems, reverse social engineering opportunities abound.
Even scarier, what if the objective weren’t a simple Wi-Fi network but, instead, an entire 4G network within a city? Don’t shake your head and discount it as black-helicopter conspiracy theory—it could really happen. A recent study at Virginia Tech proposed that a high-speed LTE network could be brought down across city blocks via a briefcase-sized device costing around $650. Because the delivery of the LTE signal depends on a small portion of the overall signal (the control instructions make up less than 1 percent), blocking those instructions effectively destroys the entire signal. After all, if your phone can’t sync, it can’t send or receive anything.
The good news in all of this is the availability of these types of devices is somewhat limited. The bad news is, they’re not very well controlled or regulated, and money talks. If Lone Star comes after you with his technological jar of raspberry jam (anyone who has seen the movie Spaceballs understands this reference quite well, and if you haven’t seen it, go watch it now), there’s not a whole lot you can do about it.
One defense wireless network administrators attempt to use is to enforce a MAC filter. Basically it’s a list of MAC addresses that are allowed to associate to the AP; if your wireless NIC’s address isn’t on the list, you’re denied access. The easy way around this is to monitor the network to figure out which MAC addresses are in use on the AP and simply spoof one of them. On a Unix/Linux machine, all you need do is log in as root, disable the interface, enter a new MAC, and reenable the device:
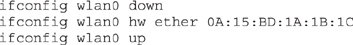
Tons of tools are also available for MAC spoofing. A couple of the more easy-to-use ones are SMAC and TMAC. Both allow you to change the MAC address with just a couple of clicks and, once you’re done, to return things to normal with a click of the mouse.
Cracking WEP is ridiculously easy and can be done with any number of tools. The idea revolves around generating enough packets to effectively guess the encryption key. The weak initialization vectors discussed already are the key—specifically, the fact that they’re reused and sent in clear text. Regardless of the tool, the standard WEP attack follows the same basic series of steps:
1. Start a compatible wireless adapter on your attack machine and ensure it can both inject and sniff packets.
2. Start a sniffer to capture packets.
3. Use some method to force the creation of thousands and thousands of packets (generally by using “de-auth” packets).
4. Analyze these captured packets (either in real time or on the side) with a cracking tool.
I thought about putting step-by-step examples of the process in here, using specific tools, but they wouldn’t serve any point. Each situation is unique, and any steps using a specific tool I put in here may not work for you at your location. This tends to lead to confusion and angst. The best advice I can give you is set up a lab and practice yourself. Don’t have an extra wireless access point to play with? Try hacking your own WAP (just make very sure you own it; otherwise, unless you have permission to do so, leave it alone). If you get lost along the way or something doesn’t seem to make sense, just check out any of the online videos you can find on WEP cracking. There are bajillions of them out there.
WEP is easy to crack, and more than a few tools are available for doing so. The Aircrack-ng suite of tools is probably one of the more “famous” ones, and will definitely show up on your exam somewhere. Aircrack-ng holds all sorts of goodies inside (a sniffer, a wireless network detector, a password cracker, and even a traffic analysis tool) and can run on both Windows and Linux. If you really want to dig into the toolset, Aircrack uses different techniques for cracking different encryption standards. On WEP, for instance, it can use a dictionary technique or a variety of weirdly named algorithmic processes called PTW, FMS, and the Korek technique.
Cain and Abel will do it easily, just sniffing packets and cracking as stated earlier, although it may take a little longer than some other tools. KisMAC (an OS X Mac application) can be used to brute-force WEP or WPA passwords. Other tools include, but are not limited to WEPAttack (wepattack.sourceforge.com), WEPCrack (wepcrack.sourceforge.com), Portable Penetrator (a mobile tool of all things, www.secpoint.com), and Elcomsoft’s Wireless Security Auditor tool.
WPA and WPA2 are exponentially more difficult. Both rely on and use a pre-shared, user-defined password alongside a constantly changed temporal key to provide protection. In WPA, the process of cracking this is really, really hard and basically comes down to one thing: brute force. Much like WEP, force a bunch of packets to be sent and store them, then run them through an offline cracker (like Aircrack) to brute-force against those packets until you’re successful. It will take a lot longer than cracking WEP, but just remain patient. WPA2 is even worse, as you’ll have to deal with the additional authentication mechanism (RADIUS and such). If the AES key stinks in the first place, your job will be much easier, but if half an effort is given to making it good in the first place, then…well, good luck with that.
Much about sniffing a wireless network is the same as sniffing its wired counterpart. The same protocols and authentication standard weaknesses you looked for with Wireshark off that switch port are just as weak and vulnerable on wireless. Authentication information, passwords, and all sorts of information can be gleaned just from watching the air, and although you are certainly welcome to use Wireshark, a couple of tools can help you get the job done.
Just a few of the tools specifically made for wireless sniffing include some we’ve already talked about, such as NetStumbler and Kismet, and some that we haven’t seen yet, including OmniPeek, AirMagnet WiFi Analyzer Pro, and WiFi Pilot. Assuming you have a wireless adapter that is compatible and can watch things in promiscuous mode, OmniPeek is a fairly well-known and respected wireless sniffer. In addition to the same type of traffic analysis you would see in Wireshark, OmniPeek provides network activity status and monitoring in a nice dashboard for up-to-the-minute viewing.
AirMagnet WiFi Analyzer, from Fluke Networks, is an incredibly powerful sniffer, traffic analyzer, and all-around wireless network-auditing software suite. It can be used to resolve performance problems and automatically detect security threats and vulnerabilities. Per the company website (www.airmagnet.com/products/wifi_analyzer/), AirMagnet includes the “only suite of active WLAN diagnostic tools, enabling network managers to easily test and diagnose dozens of common wireless network performance issues including throughput issues, connectivity issues, device conflicts and signal multipath problems.” And for you compliance paperwork junkies out there, AirMagnet includes a compliance reporting engine that maps network information to requirements for compliance with policy and industry regulations.
The point here isn’t to rehash everything we’ve already talked about regarding sniffing. What you need to get out of this is the knowledge that sniffing is beneficial to wired and wireless network attacks, and you need to be able to recognize the tools mentioned here. Again, I recommend you go out and download these tools. Most, if not all, are either free or have a great trial version for your use. Read the usage guides and determine your adapter compatibility; then fire them up and see what you can capture. You won’t necessarily gain much, exam-wise, by running them, but you will gain valuable experience for your “real” work.
Forget the coming zombie apocalypse—we’re already there. If you’ve been outside anywhere in the United States over the past couple of years, you can’t help but notice it just as I have: most people are stumbling around, with vacant expressions on their faces, and only half-heartedly engaging the world around them. Why? Because they spend most of their waking hours staring down into a smartphone or tablet. And if you’re a parent reading this book and your teenagers can make it through an entire meal without picking up a phone to text, take of picture of what they’re eating, or post an update of their exciting life (“Johnny is eating spaghetti—FOR BREAKFAST!”), you probably should be nominated for some sort of award.
But come on, admit it, you’re probably one of them too. We’ve allowed mobile computing to become so much a part of our lives it’s here to stay. We chat over our mobile devices, play games with them, do our banking over them, and use them for all sorts of business activities. Mobile networking is the future, and the future is now. According to Google Analytics, from 2014 to the end of 2015, smartphone usage went up 394 percent. Tablet usage exploded, with a 1,721 percent gain, and mobile digital usage stats showed fully 60 percent of online time was spent on mobile devices. OWASP even has Top Ten vulnerabilities specifically for the mobile world, and the Google search I just performed for “hacking mobile devices” returned a whopping 94 million results. The laptop may not be dead as far as a target, but the mobile army is certainly closing in. Because of all this, EC-Council changed their official courseware this go-round and expanded a whole new chapter on mobile platforms. While most of us groaned at yet another facet of memorization needed for an exam, it was probably overdue.
Companies the world over are struggling with implementing policy to contain all this growth. BYOD (Bring Your Own Device) offers some exciting opportunities in potential cost savings and increased productivity, but at what risk? If Bob uses his own tablet and keeps company secrets on it, what happens if/when it gets stolen? Even if the tablet or smartphone in question isn’t owned by the company, and even if it’s not allowed access to super-secret-squirrel areas, is it possible Jane could store information on it that puts all that information at risk? While digging through the dumpster for useful information is still a good idea for the ethical hacker, a little focus on mobile may definitely be worth your while. A bunch of users possibly storing sensitive organization information on devices that aren’t centrally controlled and have little to no security built into them? That sounds like a target rich environment to me.
Yes, attacking mobile platforms should be mentioned in any hacking endeavor and should become part of your arsenal. The bad news is, this stuff will tested and, as always, some of it is weird and off the rails. The good news is, though, despite ECC devoting an entire chapter to the subject, a lot of this is stuff you already know—or should, assuming you don’t live under a rock and can read. For example, were you aware there are multiple operating systems available for mobile (GASP! You don’t say?!?), that Android and iOS devices can be rooted (SHOCKING!), and that applications not specifically written by Google or Apple engineers can be put on smartphones and tablets (SAY IT AIN’T SO!!)? In this convenience versus security realm, I’ll cover what you need and, as always, dump the fluff.
When it comes to mobile platforms, there are two major players in the field—Android and iOS—and a couple others we have to mention. Android was created by Google specifically for mobile devices, and it contains an OS, middleware, and a suite of built-in applications for the mobile user. It offers a framework that allows reuse and replacement of components, media support for virtually everything you can imagine, a development environment to beat the band, and really cool names for each release (like Ice Cream Sandwich, Jelly Bean, and KitKat). Head on over to www.android.com and you’ll find more than you ever wanted to know about it.
iOS, on the other hand, is Apple’s operating system for mobile devices—that is, the iPhone and iPad (you will also find iOS on Apple TV and iPods). Apple made its mark in the desktop world, targeting entertainment and education, and its mobile OS is no different. iOS was designed from the get-go for mobile devices, using direct manipulation (touch gestures) to interface with the OS. Built-in applications include everything from entertainment to a woman’s voice that answers questions for you (Siri). A good review of everything on the current release can be found at http://www.apple.com/ios/.
As for the others out there, Windows and Blackberry are the only ones even mentioned by EC-Council. You should be aware there’s such a thing as a Windows phone (https://www.microsoft.com/en-us/windows/phones), with its own OS and features (like the 128-bit BitLocker data-at-rest option and Internet Explorer 10 built in). Blackberry is almost the same (in regard to the amount of effort you should spend on it), but there may be a little bit of a bigger payoff when it comes to this mobile platform. Although Blackberry has been largely phased out in the real world, those still using it are usually prime targets.
Outside of the occasional target opportunity they might present, I’m not sure it’s worth the neurons to devote much time to either. Mainly because their market share is virtually nonexistent, but also because EC-Council doesn’t devote much time to them either. Not to mention Blackberry is ditching its proprietary OS for Android, so the whole thing will be irrelevant before the end of this year. Almost all the same attack thoughts and steps to secure the phones are the same across platforms, so just be aware what they are.
Whether Android or iOS, one thing you will get asked about is rooting or jailbreaking the device. Both mean the same thing: perform some action that grants you administrative (root) access to the device so you can do whatever you want with it. There are multiple tools to help you root an Android. One such groovy tool (that ECC included in the courseware) is called SuperOneClick, which makes the whole process ridiculously easy. Others include, but of course are not limited to, Superboot, OneClickRoot, Kingo, unrevoked, RescueRoot, and UnlockRootPro.
As far as jailbreaking an iOS (which invalidates every warranty you can think of), there are three types and three basic techniques. Types of jailbreaking include Userland (user-level access but not admin), iBoot, and Bootrom (both granting admin-level privileges). The techniques for pulling this off include the following:
• Untethered jailbreaking The kernel will remain patched (that is, jailbroken) after reboot, with or without a system connection.
• Semi-tethered jailbreaking A reboot no longer retains the patched kernel; however, the software has already been added to the device. Therefore, if admin privileges are required, the installed jailbreaking tool can be used.
• Tethered jailbreaking A reboot removes all jailbreaking patches, and the phone may get stuck in a perpetual loop on startup, requiring a system connection (USB) to repair.
Jailbreaking tools include, but are not limited to, evasi0n7, GeekSn0w, Pangu, Redsn0w, Absinthe, and Cydia
When it comes to mobile vulnerabilities, no matter the platform, it’s almost laughable to ask about them. These are devices owned and operated mainly by users who can roam at will and can install virtually anything at all on them at will, for any reason. Security concerns? You betcha. Mobile platforms have gobs of vulnerable attack points warranting your attention: OWASP posts a Top Ten vulnerabilities for mobile that includes everything from server-side controls to client injection, and there are tons more. A hacker can take advantage not only of data on the device but also the camera and microphone—how neat would it be to listen in on or even watch a board meeting, hmm?
Many of the vulnerabilities and attack vectors we talked about on everything else also apply to mobile. Just as with web hosts, perhaps the most obvious attack vector comes from the apps themselves. App stores may not have any vetting of apps at all when entering the marketplace and are often used to distribute all sorts of malicious stuff. From iPhones to Android devices, users download and install applications for everything from working on documents to faking a Star Wars light saber (Obi-Wan’s is my personal favorite) for impromptu interoffice Jedi battles. Most users don’t even think about it—they just click the link, install the app, and start playing—and many don’t even bother to read or care about what the app is asking for, permissions-wise, on the device. Got an app for hacking? You bet we do, and if it’s tied to a fun-looking application, all the better.
How about social engineering, phishing, and (gulp!) physical security? Mobile users are as, if not more so, susceptible to all of it as their desktop peers. There’s not really a community standard mechanism for dealing with spam and phishing, and because mobile users are always on, it works quite well as an attack vector. What about theft or loss of the devices themselves? It’s one thing to black widow a website and peruse it on your own or to grab a SAM file and spend time pounding away on it, but what if you could just steal the whole dang server? In effect, that’s what’s going on with these things. In addition to any files or data the user has on the phone, a smartphone has all the data, contacts, phone numbers, and e-mails you’d need to set up social engineering attacks in the future.
Believe me, it’s not just teenagers anymore. The popularity of mobile platform applications for business use and the supposed productivity boost they’re capable of providing for organizations has greatly increased the number of workplace mobile devices in use today. It’s not surprising that organizations would want to look at mobile computing as a way to increase productivity. What may be surprising to some of them, though, is what their users are actually doing with those devices.
According to a recent study by Harvard Business Review, consumers of smartphones spend only a fraction of their time either planning for, or accomplishing, work activities on their smart devices. An incredible 77 percent of their time, though, is spent either shopping, socializing, or in the pursuit of “me time” entertainment—whether they’re at work or not. Want more? How about the fact the fastest-growing demographic in new Twitter accounts is older than 55? Or that nearly half of all Facebook use is mobile platform only? Taken together with the fact that many studies now show social media overtaking porn as the #1 Internet activity, it’s a miracle we get anything done anymore.
The very devices and open business thought processes we’re putting into place to spur productivity and increase output are, instead, giving people more time to play, interact, and shop. This probably doesn’t come as much of a surprise to anyone who’s spent any time monitoring network activity of business users in a large organization (some of the stuff the guy in the next cubicle is looking at during work hours would really amaze you), but it’s all interesting and noteworthy to me, especially when you think about the lack of security involved in all this playtime.
Want more? Consider the connectivity these devices provide for users. Most folks hate security and turn off everything they can to make life easier for themselves, and that goes for Wi-Fi connectivity on phones too. There are tons of open Wi-Fi spots all over the place that people use with their smartphones and tablets, and sniffing these types of connections is ridiculously easy. Throw in location awareness and spyware apps, and the stuff gets pretty scary pretty quickly.
Frightened yet? Heck, we’re not even done with the platform spectrum. Any real discussion on wireless standards and architecture must at least mention 3G, 4G, and Bluetooth. 3G and 4G refer to third- and fourth-generation mobile telecommunications, respectively, and offer broadband-type speeds for data usage on mobile devices (cell phones and such). The actual technology behind these transmission standards is tweaked from mobile carrier to mobile carrier, so unlike a wireless NIC complying with 802.11g working with any manufacturer’s access point with the same standard, one company’s devices may not work with another’s on 3G or 4G.
Bluetooth refers to a very open wireless technology for data exchange over a relatively short range (10 meters or less). It was designed originally as a means to reduce cabling but has become a veritable necessity for cell phones and other mobile devices. Part of what makes Bluetooth so susceptible to hacking is the thing that makes it so ubiquitous—its ease of use. Bluetooth devices are easy to connect one to another and can even be set to look for other devices for you automatically. Bluetooth devices have two modes: a discovery mode and a pairing mode. Discovery mode determines how the device reacts to inquiries from other devices looking to connect, and it has three actions. The discoverable action obviously has the device answer to all inquiries, limited discoverable restricts that action, and nondiscoverable tells the device to ignore all inquiries.
Whereas discovery mode details how the device lets others know it’s available, pairing mode details how the device will react when another Bluetooth system asks to pair with it. There are basically only two versions: yes, I will pair with you, and no, I will not. Nonpairable rejects every connection request, whereas pairable accepts all of them. Between discovery and pairing modes, you can see how Bluetooth was designed to make connection easy.
So in addition to the, roughly, billion or so new smartphones that will be sold this year, a growing populace (in and out of the business world) carrying, adjusting, manipulating, and rooting these devices at will, and the ease with which data can be stored on the device with little to no oversight or security control, you have to be aware of short-reach wireless connectivity that may offer virtual control over the device. We also have virtually nowhere to hide with them, since 3G and 4G reach nearly everywhere. Sleep well tonight, security folks. Sleep well.
Attacks on these devices abound. First and foremost, phishing attacks and social engineering are merciless when it comes to mobile devices. I’m sure you’re all familiar with good-old SMS (text) messaging, but have you ever thought about SMS phishing? While our users at least think about whether or not they should click a link in e-mail, a text message is another thing altogether. Almost every vendor from airlines to UPS packaging gives you an option to get your updates via text, and the practice is growing quickly. How easy would it be to just send User Joe a text message telling him, “You have a package coming. Click Here to track”? Definitely something to think about.
The list of Trojans available for all sorts of hilarity is almost without end. Notable Android Trojans include Obad, Fakedefender, TRAMP.A, and ZitMo. Spyware stuff is really scary, and tools like Mobile Spy and Spyera make it really easy to listen in on or even watch what the target is doing. And if that’s not enough, the tools we use to manage our own devices can be used against us. Ever heard of Google Voice? How about Remote Wipe from Google? One loose password and mobile device hacking becomes a nightmare. How about tracking where I’m at all the time? Tools like AndroidLost, Find My Phone, and Where’s My Droid were designed to help me find my lost phone, but they (and many, many others) can be used to track where I happen to be at. Wouldn’t it be helpful to know where folks are at during a social engineering visit to the site?
And how about using your mobile device as an attack platform? Tools like Network Spoofer allow you to control how websites appear on a desktop/laptop. DroidSheep allows you to perform sidejacking by listening to wireless packets and pulling session IDs. Nmap works great on a mobile device, and sniffers are a dime a dozen. Heck, you can even install Kali Linux on the thing and turn it into a full-featured hacking machine.
Finally, we can’t finish any wireless attack section without visiting our friendly little Bluetooth devices. After all, think about what Bluetooth is for: connecting devices, usually mobile (phones), wirelessly over a short distance. And since we keep everything on our devices (e-mail, calendar appointments, documents, and just about everything else you might find on a business computer), it should seem fairly obvious, then, that hacking that signal could pay huge dividends.
Bluetooth definitely falls into the wireless category and has just a few things you’ll need to consider for your exam and for your career. Although hundreds of tools and options are available for Bluetooth hacking, the good news is their coverage on the exam is fairly light, and most of it comes in the form of identifying terms and definitions. The major Bluetooth attacks are listed here:
• Bluesmacking A simple denial-of-service attack against the device.
• Bluejacking Consists of sending unsolicited messages to, and from, mobile devices.
• Bluesniffing An effort to discover Bluetooth-enabled devices—much like war driving in wireless hacking.
• Bluebugging Successfully accessing a Bluetooth-enabled device and remotely using its features.
• Bluesnarfing The actual theft of data from a mobile device.
• Blueprinting Think of this as footprinting for Bluetooth: Blueprinting involves collecting device information over Bluetooth.
Although they’re not covered in depth on your exam, you should know some of the more common Bluetooth tools available. Of course, your first action should be to find the Bluetooth devices. BlueScanner (from SourceForge) does a great job of finding devices around you, but it will also try to extract and display as much information as possible. BT Browser is another great, and well-known, tool for finding and enumerating nearby devices. Bluesniff and btCrawler are other options, providing nice GUI formats for your use. As far as attacks go, Blooover is a good choice for bluebugging, and PhoneSnoop is good for spyware on a Blackberry.
In a step up from that, you can start taking advantage of and hacking the devices nearby. Super Bluetooth Hack is an all-in-one software package that allows you to do almost anything you want to a device you’re lucky enough to connect to. If the device is a smartphone, you could read all messages and contacts, change profiles, restart the device, and even make calls as if they’re coming from the phone itself.
In the wireless world, the 802.11 series of standards is very important. 802.11a can attain speeds up to 54 Mbps and uses the 5GHz range. 802.11b has speeds of 11 Mbps at 2.4 GHz, and 802.11g is 54 Mbps at 2.4 GHz. 802.11n has speeds over 100 Mbps and uses a variety of ranges in MIMO format between 2.4 GHz and 5 GHz. Two other standards of note are 802.11i (an amendment to the original 802.11 series standard that specifies security mechanisms for use on the WLAN) and 802.16 (global development of broadband wireless metropolitan area networks, WiMax). 802.11ac is the newest standard in practice.
Modulation—the practice of manipulating properties of a waveform—is the encoding method of choice in wireless networks. Both orthogonal frequency-division multiplexing (OFDM) and direct-sequence spread spectrum (DSSS) use various pieces of a waveform to carry a signal. OFDM works with several waveforms simultaneously carrying messages back and forth: the transmission media is divided into a series of frequency bands that don’t overlap each other, and each of them can then be used to carry a separate signal. DSSS works differently by combining all the available waveforms into a single purpose; the entire frequency bandwidth can be used at once for the delivery of a message.
In ad hoc mode, wireless systems connect directly to other systems, as if a cable were strung between the two. Infrastructure mode uses an access point (AP) to funnel all wireless connections through, and clients associate and authenticate to it. Wireless networks can consist of a single access point or multiple ones, thus creating overlapping cells and allowing a user to roam freely without losing connectivity. The client needs to associate with an access point first and then disassociate when it moves to the next one.
When there is a single access point, its footprint is called a basic service area (BSA). Communication between this single AP and its clients is known as a basic service set (BSS). If you extend the range of your network by adding multiple access points, the setup is known as an extended service set (ESS). As a client moves from one AP in your subnet to another, so long as everything is configured correctly, it’ll disassociate from one AP and (re)associate with another seamlessly. This movement across multiple APs within a single ESS is known as roaming.
Wireless network design needs to take into account not only the type of antenna used but where it is placed and what is set up to contain or corral the signal. Physical installation of access points is a major concern because you will want to avoid spillage of the signal and loss of power. Most standard APs use an omnidirectional antenna, which means the signal emanates from the antenna in equal strength 360 degrees from the source. Directional antennas allow you to focus the signal in a specific direction, which greatly increases signal strength and distance. Other antennas you can use are dipole and parabolic grid. Dipole antennas have, quite obviously, two signal “towers” and work omnidirectionally. Parabolic grid antennas work a lot like satellite dishes and can have phenomenal range (up to 10 miles) but aren’t in use much.
To identify a wireless network to clients who may be interested in joining, a service set identifier (SSID) must be assigned. The SSID is not a password and provides no security at all for your network. It is a text word (32 characters or less) that only distinguishes your wireless network from others. SSIDs are broadcast by default and are easily obtainable even if you try to turn off the broadcast (in an effort dubbed SSID cloaking). The SSID is part of the header on every packet, so its discovery by a determined attacker is a given, and securing it is virtually a moot point.
Wireless authentication can happen in more than a few ways, from the simplistic to the complicated. In Open System Authentication Process, a client sends an 802.11 authentication frame with the appropriate SSID to an AP to have it answer with a verification frame. In Shared Key Authentication Process, the client will participate in a challenge/request scenario, with the AP verifying a decrypted “key” for authentication. Association is the action of a client connecting to an AP, whereas authentication actually identifies the client before it can access anything on the network.
WEP stands for Wired Equivalent Privacy and provides weak security for the wireless network. Using 40-bit to 232-bit keys in an RC4 encryption algorithm, WEP’s primary weakness lies in its reuse of initialization vectors (IVs)—an attacker can simply collect enough packets to decode the WEP shared key. WEP was never intended to fully protect your data; it was designed to give people using a wireless network the same level of protection that someone surfing over an Ethernet wired hub would expect. WEP’s initialization vectors are relatively small and, for the most part, get reused pretty frequently. Additionally, they’re sent in clear text as part of the header. An attacker simply needs to generate enough packets in order to analyze the IVs and come up with the key used.
A better choice in encryption technology is Wi-Fi Protected Access (WPA) or WPA-2. WPA makes use of Temporal Key Integrity Protocol (TKIP), a 128-bit key, and the client’s MAC address to accomplish much stronger encryption. The short of it is, WPA changes the key out (hence the “temporal” part of the name) every 10,000 packets or so, instead of sticking with one and reusing it. Additionally, the keys are transferred back and forth during an Extensible Authentication Protocol (EAP) authentication session, which makes use of a four-step handshake process in proving the client belongs to the AP, and vice versa.
WPA2 is much the same process; however, it was designed with the government and the enterprise in mind. In something called WPA-2 Enterprise, you can tie EAP or a Radius server into the authentication side of WPA2, allowing you to make use of Kerberos tickets and all sorts of additional goodies. Whether enterprise or personal, it uses AES for encryption, ensuring FIPS 140-2 compliance. As for integrity, WPA2 addresses this by using Cipher Block Chaining Message Authentication Code Protocol (CCMP), with message integrity codes (MICs), in a process called cipher block chaining message authentication code (CBC-MAC).
An AirPcap dongle is a USB wireless adapter that offers all sorts of advantages and software support. WIGLE (http://wigle.net) helps in identifying geographic locations of wireless networks; teams of hackers have mapped out wireless network locations using GPS and a tool called NetStumbler. NetStumbler (www.netstumbler.com) can be used for identifying poor coverage locations within an ESS, detecting interference causes, and finding any rogue access points in the network. It’s Windows based, easy to use, and compatible with 802.11a, b, and g.
Kismet is another wireless discovery option. It works on Linux-based systems and, unlike NetStumbler, works passively, meaning it detects access points and clients without actually sending any packets. It can detect access points that have not been configured (and would then be susceptible to the default out-of-the-box admin password) and will determine which type of encryption you might be up against. It works by “channel hopping” to discover as many networks as possible and has the ability to sniff packets and save them to a log file, readable by Wireshark or tcpdump.
Another great network discovery tool is NetSurveyor. This free Windows-based tool provides many of the same features as NetStumbler and Kismet. Additionally, it supports almost all wireless adapters without any significant additional configuration—which is of great benefit to hackers who can’t afford, or don’t have, an AirPcap card. NetSurveyor acts as a great tool for troubleshooting and verifying optimal installation of wireless networks. A few of the tools specifically made for wireless sniffing include NetStumbler, Kismet, OmniPeek, AirMagnet WiFi Analyzer Pro, and WiFi Pilot.
The rogue access point is an easy attack on a wireless network whereby an attacker sets up an access point near legitimate APs and tricks users into associating and authenticating with it. Sometimes referred to as an “evil twin,” an attack like this is easy to attempt. The use of rogue APs (evil twins) may also be referenced as a mis-association attack. Additionally, faking a well-known hotspot on a rogue AP (that is, McDonald’s or Starbucks free Wi-Fi spots) is referred to as a honeyspot attack
Denial-of-service efforts are also easy attacks to attempt. In addition to other attacks, you can jam the wireless signal altogether, using some type of jamming device and, usually, a high-gain antenna/amplifier. All wireless devices are susceptible to some form of jamming and/or interference—it’s simply a matter of placing enough signal out in the airwaves that the NICs can’t keep up.
Cracking WEP is ridiculously easy and can be done with any number of tools. The idea revolves around generating enough packets to effectively guess the encryption key. The weak initialization vectors we discussed already are the key; that is, they’re reused and sent in clear text. Tools for cracking WEP include Cain and Abel and Aircrack (both use Korek, but Aircrack is faster) as well as KisMAC, WEPCrack, chopchop, and Elcomsoft’s Wireless Security Auditor tool. KisMAC runs on Mac OS X and can be used to brute-force WEP or WPA. On WEP, Aircrack can use a dictionary technique, or a variety of weirdly named algorithmic processes called PTW, FMS, and the Korek technique, while only dictionary can be used against WPA and WPA2.
Mobile platform attacks come from a variety of attack vectors. BYOD is a ubiquitous business policy called Bring Your Own Device, allowing workers to bring and use their own personal mobile devices in the office. These devices have many vulnerable attack points, such as the apps themselves, malware, loss and theft, and unprotected Wi-Fi access and sniffing.
When it comes to mobile platforms, there are two major players in the field—Android and iOS. Whether Android or iOS, one thing you will get asked about is rooting or jailbreaking (respectively) the device. Both mean the same thing: perform some action that grants you administrative (root) access to the device so you can do whatever you want with it. Tools for rooting an Android include SuperOneClick, OneClickRoot, Kingo, unrevoked, RescueRoot, and UnlockRootPro.
Types of jailbreaking include Userland (user-level access but not admin), iBoot, and Bootrom (both granting admin-level privileges). The techniques for pulling this off include untethered jailbreaking, semi-tethered jailbreaking, and tethered jailbreaking. Jailbreaking tools include, but are not limited to, evasi0n7, GeekSn0w, Pangu, Redsn0w, Absinthe, and Cydia
Just as with web hosts, perhaps the most obvious attack vector comes from the apps themselves. App stores may not have any vetting of apps at all when entering the marketplace and are often used to distribute all sorts of malicious stuff. Social engineering, phishing, and physical security attacks also work in the mobile world.
Mobile Device Management (MDM) is an effort to add some control to enterprise mobile devices. Much like group policy and such in the Microsoft Windows world, MDM helps in pushing security policies, application deployment, and monitoring of mobile devices. Solutions include, but are not limited to, XenMobile, MaaS360, AirWatch, and MobiControl.
Bluetooth refers to a very open wireless technology for data exchange over a relatively short range (10 meters or less). Bluetooth devices have two modes: a discovery mode and a pairing mode. Discovery mode determines how the device reacts to inquiries from other devices looking to connect, and it has three actions. The discoverable action obviously has the device answer to all inquiries, limited discoverable restricts that action, and nondiscoverable tells the device to ignore all inquiries. Pairing mode details how the device will react when another Bluetooth system asks to pair with it. There are basically only two versions: yes, I will pair with you, and no, I will not. Nonpairable rejects every connection request, whereas pairable accepts all of them.
SMS phishing is a wireless attack using text messaging to deliver malicious links. Notable Android Trojans include Obad, Fakedefender, TRAMP.A, and ZitMo. Tools like Network Spoofer allow you to control how websites appear on a desktop/laptop. DroidSheep allows you to perform sidejacking by listening to wireless packets and pulling session IDs. The major Bluetooth attacks include the following:
• Bluesmacking A simple denial-of-service attack against the device.
• Bluejacking Consists of sending unsolicited messages to, and from, mobile devices.
• Bluesniffing An effort to discover Bluetooth-enabled devices—much like war driving in wireless hacking.
• Bluebugging Successfully accessing a Bluetooth-enabled device and remotely using its features.
• Bluesnarfing The actual theft of data from a mobile device.
• Blueprinting Think of this as footprinting for Bluetooth: This attack involves collecting device information over Bluetooth.
BlueScanner (from SourceForge) does a great job of finding devices around you, but it will also try to extract and display as much information as possible. BT Browser is another great, and well-known, tool for finding and enumerating nearby devices. Bluesniff and btCrawler are other options, providing nice GUI formats for your use.
1. A WPA2 wireless network is discovered during a pen test. Which of the following methods is the best way to crack the network key?
A. Capture the WPA2 authentication traffic and crack the key.
B. Capture a large amount of initialization vectors and crack the key inside.
C. Use a sniffer to capture the SSID.
D. WPA2 cannot be cracked.
2. You are discussing wireless security with your client. He tells you he feels safe with his network because he has turned off SSID broadcasting. Which of the following is a true statement regarding his attempt at security?
A. Unauthorized users will not be able to associate because they must know the SSID in order to connect.
B. Unauthorized users will not be able to connect because DHCP is tied to SSID broadcast.
C. Unauthorized users will still be able to connect because nonbroadcast SSID puts the AP in ad hoc mode.
D. Unauthorized users will still be able to connect because the SSID is still sent in all packets, and a sniffer can easily discern the string.
3. You are discussing wireless security with your client. He tells you he feels safe with his network as he has implemented MAC filtering on all access points, allowing only MAC addresses from clients he personally configures in each list. You explain this step will not prevent a determined attacker from connecting to his network. Which of the following explains why the APs are still vulnerable?
A. WEP keys are easier to crack when MAC filtering is in place.
B. MAC addresses are dynamic and can be sent via DHCP.
C. An attacker could sniff an existing MAC address and spoof it.
D. An attacker could send a MAC flood, effectively turning the AP into a hub.
4. What information is required in order to attempt to crack a WEP AP? (Choose two.)
A. Network SSID
B. MAC address of the AP
C. IP address of the AP
D. Starting sequence number in the first initialization vector
5. Which of the following protects against man-in-the-middle attacks in WPA?
A. MIC
B. CCMP
C. EAP
D. AES
6. Which of the following is the best choice for performing a bluebugging attack?
A. PhoneSnoop
B. BBProxy
C. btCrawler
D. Blooover
7. Operations promotes the use of mobile devices in the enterprise. Security disagrees, noting multiple risks involved in adding mobile devices to the network. Which of the following provides some protections against the risks security is concerned about?
A. Implement WPA.
B. Add MAC filtering to all WAPs.
C. Implement MDM.
D. Ensure all WAPs are from a single vendor.
8. Which of the following provides for integrity in WPA2?
A. AES
B. CCMP
C. TKIP
D. RADIUS
9. Which of the following is a true statement?
A. Configuring a strong SSID is a vital step in securing your network.
B. An SSID should always be more than eight characters in length.
C. An SSID should never be a dictionary word or anything easily guessed.
D. SSIDs are important for identifying networks but do little to nothing for security.
10. Which wireless encryption technology makes use of temporal keys?
A. WAP
B. WPA
C. WEP
D. EAP
11. Which wireless technology uses RC4 for encryption?
A. WAP
B. WPA
C. WEP
D. WPA2
E. All of the above
12. You wish to gain administrative privileges over your Android device. Which of the following tools is the best option for rooting the device?
A. Pangu
B. SuperOneClick
C. Cydia
D. evasi0n7
13. Which of the following jailbreaking techniques will leave the phone in a jailbroken state even after a reboot?
A. Tethered
B. Untethered
C. Semi-tethered
D. Rooted
1. A. WPA2 is a strong encryption method, but almost everything can be hacked given time. Capturing the password pairwise master key (PMK) during the handshake is the only way to do it, and even then it’s virtually impossible if it’s a complicated password.
2. D. Turning off the broadcast of an SSID is a good step, but SSIDs do nothing in regard to security. The SSID is included in every packet, regardless of whether it’s broadcast from the AP.
3. C. MAC filtering is easily hacked by sniffing the network for a valid MAC and then spoofing it, using any number of options available.
4. A, B. The MAC address of the AP and the SSID are required for attempting a WEP crack.
5. A. MIC provides integrity checking in WPA, verifying frames are authentic and have not been tampered with. Part of how it accomplishes this is a sequence number—if any arrive out of sequence, the whole session is dropped.
6. D. Blooover is designed for bluebugging. BBProxy and PhoneSnoop are both Blackberry tools, and btCrawler is a discovery option.
7. C. Mobile Device Management won’t mitigate all the risks associated with unending use of mobile devices on your network—but at least it’s something.
8. B. Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (say that three times fast) uses Message Integrity Codes (MICs) for integrity purposes.
9. D. An SSID is used for nothing more than identifying the network. It is not designed as a security measure.
10. B. WPA uses temporal keys, making it a much stronger encryption choice than WEP.
11. C. WEP uses RC4, which is part of the reason it’s so easily hacked and not considered a secure option.
12. B. SuperOneClick is designed for rooting Android. The others are jailbreaking iOS options.
13. B. If untethered jailbreaking has been performed, the device is in a jailbroken state forever, with or without connection to another device.