CHAPTER 8
Security in Cloud Computing
In this chapter you will
• Identify cloud computing concepts
• Understand basic elements of cloud security
• Identify cloud security tools
If you haven’t seen the movie The Princess Bride, stop what you’re doing and go watch it right now. Trust me, the 2 hours or so you’ll waste in this escape fiction will be more than worthwhile for the innumerable pop culture references you’ll gain. Not to mention the laughs you’ll get along the way.
One particularly funny line from the movie comes from the repeated use of the word inconceivable. Sicilian boss Vizzini (portrayed by Wallace Shawn) uses it over and over again, for things that truly are…conceivable. Finally, in one scene he’s standing at the top of a cliff with his two henchmen, watching the good guy climbing up a rope hanging over the edge. Vizzini thinks he’s finally rid of the good guy and cuts the rope, hoping to see him splat at the bottom. When he peers over and sees the guy has not fallen, but has caught a hold of a branch and is dangling from the cliffside, he yells “Inconceivable!” Swordsman Inigo Montoya, played brilliantly by a young Mandy Patinkin, looks at him and says, “You keep using that word. I do not think it means what you think it means.”
I’m unsure if there are statistics kept on memes, but the sheer number that have exploded from this phrase has got to be close to the top. Do a quick image search for it and you’ll see what I mean—but be forewarned, some of them are brutal. If you’re in an online conversation and misuse a word or a phrase, I can almost guarantee you’ll hear (or see) Inigo Montoya’s phrase.
All of this serves to introduce our next, very short, but packed with good information chapter on cloud computing. Since the word cloud is about as fully understood by most people as nuclear fusion or anything Ozzy Osbourne says, it’s naturally an area we should focus some attention on. EC-Council devoted an entire new chapter to “Cloud Computing,” and we’ll do our best to get it translated to common sense throughout the rest of the chapter. And nobody even think of quoting Inigo back to ECC. I’m sure they know what both words mean. Maybe.
Cloud Computing
I have a couple friends who are really involved in cloud computing for a major enterprise network, so I asked them, “What’s the biggest misconception surrounding cloud computing?” Both, in one fashion or another, answered the same way: “Just which type and which model of cloud computing are you asking about?” This really hit the nail on the head, since a lot of us simply don’t have a clue what cloud computing really is. We think we know, because we’re smart. And we’ve seen Visio diagrams for decades showing that groovy little cloud to signify a network we had no insight into (like the Internet). Not to mention we’ve all uploaded music, videos, and documents to “the cloud.” Ask most people to define cloud and that’s exactly what pops into their head—an unknown group of network resources sitting somewhere that we can send stuff to, pull stuff from, and play around in if we need to. And that’s sort of true; there’s just a lot more to the story.
The entire idea behind cloud computing started almost as soon as the idea for the Internet was birthed. A guy named J.C.R. Licklider, who was very prominent in the creation of ARPANET, postulated the concept of “an intergalactic computer network,” storing data and providing services to organizations and, eventually, individuals. He may have been off on scope just a bit (maybe in 1960 the idea we’d be spread throughout the galaxy seemed plausible), but the concept was dead-on. Others continued the thought process—with some even branching it out to artificial intelligence–type ideas—alongside a brand new idea called virtualization (starting back in the 1960s by companies like General Electric, Bell Labs, and IBM).
Virtualization was a neat concept springing from the mainframe line of thinking: let’s find a way to run more than one operating systems simultaneously on the same physical box. The 1990s saw gobs of research and action on this, with several VM (virtual machine) companies crawling out into the open to work on it and, in some cases, even offering virtualized private networking services to customers.
With abundant virtualization opportunities, the concept of cloud computing exploded. There are arguments over who the first real cloud computing provider was, and while it’s not very important for your exam, a little history never hurt. Salesforce hit in 1999, and although it wasn’t really a cloud, it did offer a one-stop shop for applications via a web portal, and broke the ice for the concept. In 2002, Amazon Web Services opened for business, providing cloud-based storage and data computation services. They continued expansion of cloud services and have become one of the biggest cloud services provider on the planet.
This is not to say AWS is the only or the best provider available. In many cases, they’re nowhere near the top. HPE offers cloud services, as does AT&T, IBM, Century Link, Cisco, Microsoft, and the list goes on and on. Which service provider is best for your needs? Well, you need to know more about what type of cloud you’re looking for first.
So just what is modern cloud computing? While a firm, absolute definition is hard to run down, you could do worse than this one: cloud computing provides user and enterprise subscribers on-demand delivery of various IT services as a metered service over a network. Cloud computing offers everything from on-demand self-service, storage, and resource pooling to elasticity, automation in management, and broad network access. To further define what exactly it is, we need to consider the three major types of cloud computing—IaaS, PaaS, and SaaS.
Infrastructure as a Service (IaaS) basically provides virtualized computing resources over the Internet. A third-party provider hosts infrastructure components, applications and services on behalf of its subscribers, with a hypervisor (such as VMware, Oracle VirtualBox, Xen, or KVM) running the virtual machines as guests. Collections of hypervisors within the cloud provider exponentially increase the virtualized resources available and provide scalability of service to subscribers. As a result, IaaS is a good choice not just for day-to-day infrastructure service, but also for temporary or experimental workloads that may change unexpectedly. IaaS subscribers typically pay on a per-use basis (within a certain timeframe, for instance, or sometimes by the amount of virtual machine space used).
Platform as a Service (PaaS) is geared toward software development, as it provides a development platform that allows subscribers to develop applications without building the infrastructure it would normally take to develop and launch software. Hardware and software is hosted by the provider on its own infrastructure so customers do not have to install or build homegrown hardware and software for development work. PaaS doesn’t usually replace an organization’s actual infrastructure—instead it just offers key services the organization may not have onsite.
Lastly, Software as a Service (SaaS) is probably the simplest and easiest to think about. SaaS is simply a software distribution model—the provider offers on-demand applications to subscribers over the Internet. And why would anyone do this? Well, remember that entire section on web applications from the previous chapter, and all the headaches of patch management and security your admins have to worry about? SaaS may be able to take that workload off your plate. Sass benefits include easier administration, automated patch management, compatibility, and version control. For comparison purposes of all models, check out Figure 8-1.
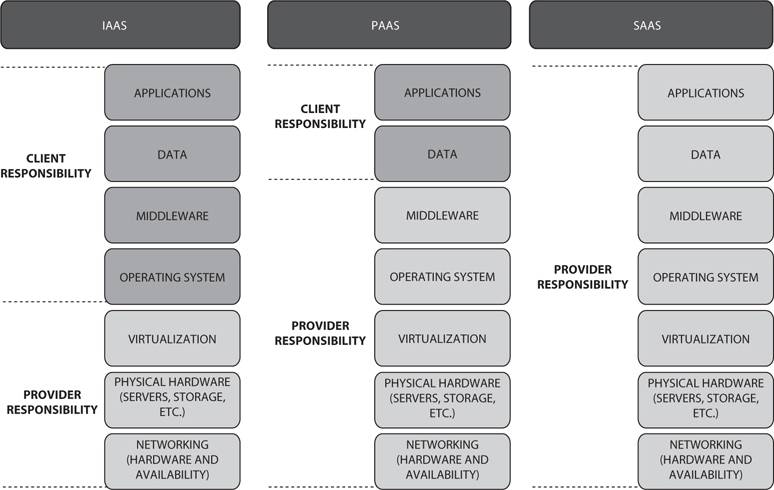
Figure 8-1 Cloud security alliance models
Along with the types of cloud, there are four main deployment models: public, private, community, and hybrid. A public cloud model is one where services are provided over a network that is open for public use (like the Internet). Public cloud is generally used when security and compliance requirements found in large organizations isn’t a major issue. A private cloud model is, not surprisingly, private in nature. The cloud is operated solely for a single organization (a.k.a. single-tenant environment) and is usually not a pay-as-you-go operation. Private clouds are usually preferred by larger organizations, because the hardware is dedicated and security and compliance requirements can be more easily met.
The last two models are a little bit different. A community cloud model is one where the infrastructure is shared by several organizations, usually with the same policy and compliance considerations. For example, multiple different state-level organizations may get together and take advantage of a community cloud for services they require. The hybrid cloud model, last on our list, is exactly what it sounds like—a composition of two or more cloud deployment models.
Lastly, and as always with these types of things, we need to spend just a little bit of time talking about U.S. Government rules and regulations regarding the cloud. In September of 2011, faced with more and more government organizations looking to the cloud as a means to save money, NIST (National Institutes of Standards and Technology) released Special Publication 500-292: NIST Cloud Computing Reference Architecture (http://www.nist.gov/customcf/get_pdf.cfm?pub_id=909505) to provide a “fundamental reference point to describe an overall framework that can be used government wide.” This publication defined five major roles within a cloud architecture, shown in Figure 8-2:
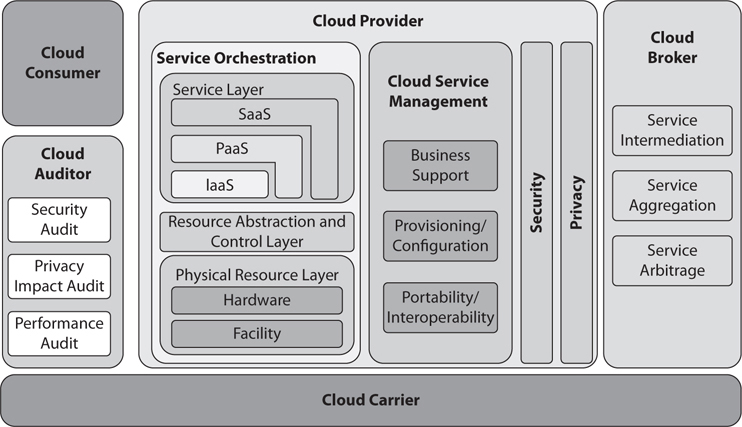
Figure 8-2 NIST Cloud Computing Reference Architecture
• Cloud carrier The organization that has the responsibility of transferring the data; akin to the power distributor for the electric grid. The cloud carrier is the intermediary for connectivity and transport between subscriber and provider.
• Cloud consumer The individual or organization that acquires and uses cloud products and services.
• Cloud provider The purveyor of products and services.
• Cloud broker Acts to manage use, performance, and delivery of cloud services, as well as the relationships between providers and subscribers. The broker “acts as the intermediate between consumer and provider and will help consumers through the complexity of cloud service offerings and may also create value added cloud services as well.”
• Cloud auditor Independent assessor of cloud service and security controls. The auditor “provides a valuable inherent function for the government by conducting the independent performance and security monitoring of cloud services.”
In addition to the NIST reference architecture, there are a few regulatory bodies and efforts surrounding cloud computing. But what’s really very interesting about them is ECC doesn’t even mention them in the official courseware. Not one regulatory effort—FedRAMP, PCI, FIPS—is mentioned at all. Does this mean they’re not important, that we shouldn’t devote space to them, or that you shouldn’t be aware of them? Heck no. It’s my opinion these will be part of the exam sooner rather than later, so you should at least be able to identify them. ECC has a habit of springing these things on you after release of new material, so at a minimum be aware these things exist.
FedRAMP is probably the most recognized and referenced regulatory effort regarding cloud computing. Per FedRAMP’s site (http://www.fedramp.gov/), the Federal Risk and Authorization Management Program (FedRAMP) “is a government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services.” This not only provides an auditable framework for ensuring basic security controls for any government cloud effort, but FedRAMP also offers weekly tips for security and configuration (https://www.fedramp.gov/fedramp-weekly-tips-cues-11/ for example) and even has free training available on the site (http://www.fedramp.gov/resources/training/).
Want more? How about the Cloud Security Alliance (CSA)? They’re the leading professional organization devoted to promoting cloud security best practices and organizing cloud security professionals. In addition to providing a certification on cloud security and offering all sorts of cloud-centric training, they published a general cloud enterprise architecture model to help professionals conceptualize the components of a successful cloud implementation. They also publish gobs of documentation on everything from privacy concerns to security controls focus and implementation (https://cloudsecurityalliance.org).
There’s more regarding cloud—lots more. I could’ve written an entire book on the subject, but that’s not what I’m here for. You’ll need to know cloud basics, which we’ve covered, I think, pretty well so far. There are some security goodies still left to talk about, though, so hang on.
Cloud Security
What may be one of the most confusing aspects of cloud computing security comes back to what we started this chapter with—it’s hard to defend something when you don’t really know what that something is. Instead of building hardware (like servers, network devices, and cabling) and setting up a classic data center to fit your needs, you simply purchase services to handle the resources, automation, and support to get the job done. The services purchased, though, run in a data center somewhere, filled with servers, network devices, and cabling. The only real difference is the physical devices belong to someone else.
Which all serves to bring up questions regarding a very fuzzy line in security testing. Let’s say you wish to test all your resources, data, and services to get an idea of your overall security because, well, you’re supposed to. Where does your testing start and end? I mean, considering your entire system relies on Amazon (for example) to remain up and secure, can you test all of Amazon? And what happens if your resources are comingled somewhere inside all that cloud secret sauce? Can you really trust they’re on top of things, security wise? Should you? Can you? As you can tell, security in the cloud is…weird.
Storm Clouds
Oh, the cloud. Doesn’t it instantly bring to mind pictures of serenity, calm, and beauty? Look at the little cherubs over there are handling the cabling for us. Oh, isn’t it so cute how they bat down intrusion attempts at the barrier over there? Just adorable. But I got to thinking when I started writing this chapter that there has to be a dark side. Maybe the cloud isn’t always brightly lit and fluffy with little cherubs handling everything. Maybe it’s dark and harsh, with thunder and lightning rumbling about. More, you know, like a horror show.
I did a Google search on “Cloud horror stories” and came up with some fascinating articles. Seems moving things to the cloud doesn’t suddenly make your world a better place where security and protection isn’t a concern anymore. No, it’s filled with dark alleyways and nefarious folks roaming around looking for the right lightning bolt to toss—or to grab hold of.
In a CIO.com article on this subject, author John Brandon noted some nightmare scenarios a cloud service subscriber might want to think about. Suppose your provider just suddenly decides they’re done paying bills and declares bankruptcy? Now you’re in a real pickle, with your data and services locked away in the red tape of financial bureaucracy and a nightmare world of lawyers and time you can ill-afford to use in getting things back up and running. And it’s actually happened—a provider named Nirvanix did declare bankruptcy. But no worries—they gave all subscribers 30 days to move all data out to new locales. No problem, right? I mean, surely we can move our entire operation with no downtime or loss in 30 days. Right?
And speaking of being in a bad mood, what happens if you and your cloud provider just don’t get along? Suppose, for instance, you decide you want to move service and data X from your current provider to another and your current provider decides they don’t want to assist you with that. Is it possible they could make things difficult on you? Or suppose your virtualized servers and data actually get hacked and destroyed and your provider simply throws up their hands and says, “Not our fault—we don’t provide any disaster recovery options for you. Should’ve paid attention when you signed the contract.” Providers are very touchy when it comes to their internal workings, and if you’re on their bad side, things can go south in a hurry.
And who can forget money in all this? You probably have financial and contracting sections within the organization to keep this cloud provision paid for. So what happens when they get into a dispute? If the provider thinks you haven’t paid but your contracting/finance office thinks you have, what happens to the actual IT services? Does everyone let things keep running smoothly while they work it out over beignets and coffee? Somehow I think not.
No, dear reader, the cloud isn’t always nice and fluffy. Sometimes there are things flying around up here you need to be ready for. When you come up here to play, just remember, here be dragons—and the stuff of nightmares.
So does that mean cloud security is different? In some aspects, yes. For instance, cloud security is really talking about two sides of the same coin—you must be concerned with the security of the provider as well as that of the subscriber, and both are responsible for it. And what about additional target points introduced as a part of cloud? For example, using virtualization introduces a hypervisor layer between physical hardware and subscribed servers. Therefore, if you comprise the hypervisor, you compromise them all. Add to it that most cloud providers simply will not allow subscribers the monitoring and access even approximating what they’d have in a traditional architecture (I’ve personally heard the phrase “that’s part of the secret sauce, so don’t worry about it” more times than I care to remember), and things can get really hairy.
However, in most aspects, the answer is definitely no. You’re still faced with the same issues you have everywhere else: computing resources are public-facing or otherwise available, and bad guys are trying to get into them. There are security policies to be hammered out and adhered to, authentication methods to figure out, web application security concerns, intrusion detection issues, malware prevention efforts, and the list goes on and on. In short, once again you must ask yourself, “What are my vulnerabilities and threats, and what can I do to mitigate against them?” Both CSA and ECC have a nice reference chart for security control layers, which you can see in Figure 8-3.
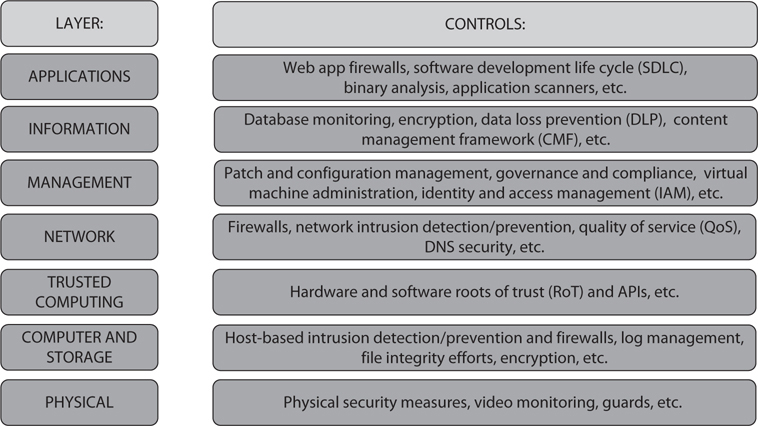
Figure 8-3 Cloud control layers
As far as tools to assist you in cloud security, not surprisingly the list is long. Depending on the model chosen and what you’re trying to get out of your cloud architecture (or keep in it), tools can be a varied as your traditional data centers. A couple mentioned specifically by EC-Council are CloudInspect and CloudPassage Halo. Core’s CloudInspect is “a tool that profits from the Core Impact & Core Insight technologies to offer penetration-testing as a service from Amazon Web Services for EC2 users” (http://www.coresecurity.com/corelabs-research/projects/core-cloudinspect). It’s obviously designed for AWS cloud subscribers and runs as an automated, all-in-one testing suite specifically for your cloud subscription. CloudPassage’s Halo “provides instant visibility and continuous protection for servers in any combination of data centers, private clouds and public clouds. The Halo platform is delivered as a service, so it deploys in minutes and scales on-demand. Halo uses minimal system resources, so layered security can be deployed where it counts, right at every workload—servers, instances and containers” (https://www.cloudpassage.com/products/).
Other cloud-specific tools and toolsets mentioned include Dell Cloud Manager, Qualys Cloud Suite, Trend Micro’s “Instant On” Cloud Security, and Panda Cloud Office Protection.
Threats and Attacks
Depending on who you talk to, there are various “top threats” to cloud computing. The Cloud Security Alliance released a publication titled “The Notorious Nine: Cloud Computing Top Threats in 2013,” while Infoworld and others list at least 12. And EC-Council? They seem to believe it’s important to list every single threat imaginable, and devote slide after slide to cloud computing threats. The more salient ones are listed on everyone’s offering, though, so we’ll concentrate on those.
In virtually every list you look at, data breach or loss is listed at the top. Data breach or loss, of course, refers to the malicious theft, erasure, or modification of almost anything in the cloud you can think of. Due to the nature of cloud computing, the sheer amount of data available makes this a prime target—not to mention that data is sensitive in nature. You might think financial information is the big target, but data breaches involving health information and intellectual property may turn out to be more even more damaging to an organization (not just in fines and lawsuits, but in brand damage and loss of business). It’s important to note that while cloud providers deploy their own tools, methods, and controls to protect their overall environment, it’s generally and ultimately up to the subscribers themselves to protect their own data in the cloud. No matter what implementation of cloud, data breach threats apply to all models. On their site, CSA recommends multifactor authentication and encryption as protection against data breaches.
Abuse of cloud resources is another threat high on everyone’s list. If an attacker can create anonymous access to cloud services, he could then leverage the tremendous resources to pull off all sorts of things. Need to crack a password or encryption key and don’t have a 25-GPU cluster at home? Why not use the cloud’s virtual servers to do it for you? An attacker may also leverage resources to build rainbow tables, create and control botnets, and even host exploits and malicious sites. Typically this threat isn’t necessarily a specific concern of cloud subscribers (other than maybe some degradation of services or whatnot), but it’s a very valid concern for the provider. The provider should perform active monitoring to detect any abuse instances as well as have a means to protect/recover from them. Generally speaking, abuse of cloud services threat applies to the IaaS and PaaS models.
Ground Floor Opportunity
I can promise there’s no pun intended with this sidebar talking about the “ground floor” right in the middle of a chapter about the cloud. I’m simply not that clever, and I would never stoop to that level. So get your head out of the clouds and come back to Earth. I’m cirrus.
As with every other segment of IT, the cloud has its own world of certifications and acronyms you get to put in your e-mail signature. The biggest splash on the market right now comes from ISC2 and CSA—the Certified Cloud Security Professional. CCSP (https://www.isc2.org/ccsp/default.aspx) certifies professionals with “deep-seated knowledge and competency derived from hands-on experience with cyber, information, software and cloud computing infrastructure security.” The certification path is much like others in differing areas of IT expertise—you need years of experience in the field (5, per the website, including 3 years of information security and at least 1 year of cloud security experience) verified by jobs held and qualified individuals vouching for you, an ability to memorize a lot of terms and take tests, and a pretty decent sum of money. The CCSP credential is suitable for mid-level to advanced professionals involved with IT architecture, web and cloud security engineering, information security, governance, risk and compliance, and even IT auditing
If this certification seems a little much like a jumping-off spot, a smaller-step beginning can be found in the Certificate of Cloud Security Knowledge (CCSK, https://cloudsecurityalliance.org/education/ccsk/#_info-video1), also offered by CSA. For the low, low fee of $345, anyone can attempt the examination twice and gain the certificate. This counts for a year of experience in cloud security, and can be looked at as almost a prerequisite for the CCSP.
Although there is official training for the certification, may I humbly suggest CCSP Certified Cloud Security Professional All-in-One Exam Guide (ISBN 1259835464) from McGraw Hill Professional? I happen to know the author—Mr. Daniel Carter—and can attest to his knowledge and experience in this particular arena. Even if you don’t want to take the examination, the CCSP book will be good reading—you obviously don’t need the CCSP to be an ethical hacker, but learning what you need for this certification will make you a better ethical hacker.
Next on our list is insecure interfaces and APIs. Cloud services rely heavily on APIs and web services to function and operate, and without them, functions like auto-scaling, authentication, authorization, and sometimes the operations of cloud applications themselves will fail. Insecure interfaces and APIs can circumvent user-defined policies and really mess around with input data verification efforts. Both provider and subscriber should ensure strong security controls are in place, such as strong encryption and authorization access to APIs and connectivity. This threat applies to all models of cloud.
Other threats mentioned that warrant inclusion in our discussion are insufficient due diligence (for example, moving an application from one cloud environment to another and not knowing the security differences between the two), shared technology issues (multitenant environments may not provide proper isolation between systems and applications), and unknown risk profiles (subscribers simply do not know exactly what security provisions are made in the background of and by the provider). Many others, such as malicious insiders, inadequate design, and DDoS are valid for both cloud services and traditional data centers.
Attacks against cloud computing are as varied and crazed as those against anything else. Social engineering, for instance, is a good attack vector no matter what the environment—why bother with technology-specific attacks when you can just ask people for credentials or get them to click a link in an e-mail? SQL injection and cross-site scripting? Of course—they work just as well when the apps and databases are hosted on somebody else’s servers. Other attacks that work everywhere else are also apropos for cloud systems—DNS poisoning and session hijacking all work just as well here as they would anywhere else.
A couple of interesting cloud-based ones are out there, though. Two that ECC mention explicitly are session riding and side channel attacks. Session riding is, in effect, simply CSRF under a different name and deals with cloud services instead of traditional data centers. A side channel attack, also known as a cross-guest VM breach, deals with the virtualization itself. If an attacker can somehow gain control of an existing VM (or place his own) on the same physical host as the target, he may be able to pull off lots of naughty activities.
Is there more to know about the cloud? Of course there is, and I could have expanded this to include a lot more of it. However, the subject material is so vast, broad, and varied, I didn’t think getting too far down in the weeds would be relevant at this point. Should you decide to concentrate in the cloud arena, there are other certifications and study efforts you should definitely check into. For most of us, the cloud is simply one more attack vector; one more area of focus that provides its own interesting security and attack thoughts. This chapter should give you what you need for the exam, which is what you bought this book for in the first place. My suggestion, though, is to definitely keep your head in the cloud. A lot of computing is headed there, so why not immerse now?
Chapter Review
Virtualization (started back in the 1960s by companies like General Electric, Bell Labs, and IBM) is a practice whereby the physical aspects of the hardware are virtually presented to operating systems in a way that allows more than one virtual machines (with their own operating systems) to run simultaneously on the same physical box. Cloud computing provides user and enterprise subscribers on-demand delivery of various IT services as a metered service over a network. Cloud computing offers everything from on-demand self-service, storage, and resource pooling to elasticity, automation in management, and broad network access. To further define what exactly it is, we need to consider the three major types of cloud computing—IaaS, PaaS, and SaaS. Cloud computing can be thought of as the ultimate in separation of duties. It moves system services that would otherwise be hosted internally to an external provider. It also separates the role of data owner from the role of data custodian.
Infrastructure as a Service (IaaS) basically provides virtualized computing resources over the Internet. A third-party provider hosts infrastructure components, applications, and services on behalf of its subscribers, with a hypervisor (such as VMware, Oracle VirtualBox, Xen, or KVM) running the virtual machines as guests. IaaS is a good choice not just for day-to-day infrastructure service, but also for temporary or experimental workloads that may change unexpectedly. IaaS subscribers typically pay on a per-use basis (within a certain timeframe, for instance, or sometimes by the amount of virtual machine space used).
Platform as a Service (PaaS) is geared toward software development, as it provides a development platform that allows subscribers to develop applications without building the infrastructure it would normally take to develop and launch software. Hardware and software are hosted by the provider on its own infrastructure so customers do not have to install or build homegrown hardware and software for development work. PaaS doesn’t usually replace an organization’s actual infrastructure; instead, it just offers key services the organization may not have onsite.
Software as a Service (SaaS) is simply a software distribution model—the provider offers on-demand applications to subscribers over the Internet. SasS benefits include easier administration, automated patch management, compatibility, and version control.
Along with the types of cloud, there are four main deployment models: public, private, community, and hybrid. A public cloud model is one where services are provided over a network that is open for public use (like the Internet). A private cloud model is, not surprisingly, private in nature. The cloud is operated solely for a single organization (a.k.a. single-tenant environment) and is usually not a pay-as-you-go operation. A community cloud model is one where the infrastructure is shared by several organizations, usually with the same policy and compliance considerations. A hybrid cloud model is exactly what it sounds like—a composition of two or more cloud deployment models.
NIST (National Institutes of Standards and Technology) released Special Publication 500-292: NIST Cloud Computing Reference Architecture to provide a “fundamental reference point to describe an overall framework that can be used government wide.” This publication defined five major roles within a cloud architecture: cloud carrier (the organization that has the responsibility of transferring the data; that is, the intermediary for connectivity and transport between subscriber and provider), cloud consumer (the individual or organization that acquires and uses cloud products and services), cloud provider (the purveyor of products and services), cloud broker (acts to manage use, performance, and delivery of cloud services, as well as the relationships between providers and subscribers), and cloud auditor (an independent assessor of cloud service and security controls).
FedRAMP is probably the most recognized and referenced regulatory effort regarding cloud computing. The Federal Risk and Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services. FedRAMP not only provides an auditable framework for ensuring basic security controls for any government cloud effort, but also offers weekly tips for security and configuration and even has free training available on the site. PCI Data Security Standard (PCI DSS) Cloud Special Interest Group’s Cloud Computing Guidelines also provides notables assistance and information for the cloud.
The Cloud Security Alliance (CSA) is the leading professional organization devoted to promoting cloud security best practices and organizing cloud security professionals. In addition to providing a certification on cloud security and offering all sorts of cloud-centric training, they published a general cloud enterprise architecture model to help professionals conceptualize the components of a successful cloud implementation. They also publish documentation on everything from privacy concerns to security controls, focus, and implementation.
Cloud security is really talking about two sides of the same coin—you must be concerned with the security of the provider as well as that of the subscriber. Both the provider and subscriber are responsible for security. Using virtualization introduces a hypervisor layer between the physical hardware and subscribed servers. Therefore, if you comprise the hypervisor, you compromise them all.
The Trusted Computing Model refers to an attempt to resolve computer security problems through hardware enhancements and associated software modifications. The Trusted Computing Group (TCG) is made up of a bunch of hardware and software providers who cooperate to come up with specific plans. Roots of Trust (RoT) is a set of functions within the trusted computing module that are always trusted by the computer’s operating system (OS).
Tools to assist in cloud security include CloudInspect and CloudPassage Halo. Core’s CloudInspect is “a tool that profits from the Core Impact & Core Insight technologies to offer penetration-testing as a service from Amazon Web Services for EC2 users.” It’s designed for AWS cloud subscribers and runs as an automated, all-in-one testing suite specifically for your cloud subscription. CloudPassage’s Halo “provides instant visibility and continuous protection for servers in any combination of data centers, private clouds and public clouds. The Halo platform is delivered as a service, so it deploys in minutes and scales on-demand. Halo uses minimal system resources, so layered security can be deployed where it counts, right at every workload—servers, instances and containers.” Other cloud-specific tools and toolsets mentioned include Dell Cloud Manager, Qualys Cloud Suite, Trend Micro’s “Instant On” Cloud Security, and Panda Cloud Office Protection.
Cloud Security Alliance released a publication titled “The Notorious Nine: Cloud Computing Top Threats in 2013,” and EC-Council has its own list. Important ones to remember include:
• Data breach or loss The malicious theft, erasure, or modification of almost anything in the cloud you can think of. While cloud providers deploy their own tools, methods, and controls to protect their overall environment, it’s generally and ultimately up to the subscribers themselves to protect their own data in the cloud. CSA recommends multifactor authentication and encryption as protection against data breaches.
• Abuse of cloud resources If attackers can create anonymous access to cloud services, they could then leverage the tremendous resources to do whatever they want. Typically this threat isn’t necessarily a specific concern of cloud subscribers, but it’s a very valid concern for the provider. The provider should perform active monitoring to detect any abuse instances as well as have a means to protect/recover from them. Generally speaking, threats of abuse of cloud services apply to the IaaS and PaaS models.
• Insecure interfaces and APIs Cloud services rely heavily on APIs and web services to function and operate, and without them, functions like auto-scaling, authentication, authorization, and sometimes the operations of cloud applications themselves will fail. Insecure interfaces and APIs can circumvent user defined policies and really mess around with input data verification efforts. Both provider and subscriber should ensure strong security controls are in place, such as strong encryption and authorization access to APIs and connectivity. This threat applies to all models of cloud.
Other threats mentioned that warrant inclusion in our discussion are insufficient due diligence (for example, moving an application from one cloud environment to another and not knowing the security differences between the two), shared technology issues (multitenant environments may not provide proper isolation between systems and applications), and unknown risk profiles (subscribers simply do not know exactly what security provisions are made in the background of and by the provider). Many others, such as malicious insiders, inadequate design, and DDoS are valid for both cloud services and traditional data centers.
SOAP (Service Oriented Architecture) is an API that makes it easier for application components to cooperate and exchange information on systems connected over a network. It’s designed to allow software components to deliver information directly to other components over a network. A wrapping attack occurs when a SOAP message is intercepted and the data in the envelope is changed and then sent/replayed.
In addition to every other attack mentioned previously in this book, two that ECC mentions explicitly are session riding and side channel attacks. Session riding is simply CSRF under a different name and deals with cloud services instead of traditional data centers. Side channel attacks, also known as cross-guest VM breach, deal with the virtualization itself: if an attacker can somehow gain control of an existing VM (or place his own) on the same physical host as the target, he may be able to attempt a litany of attacks and efforts.
Questions
1. Implementing cloud computing provides many benefits. Which of the following is the best choice of a security principle applicable to implementing cloud security?
A. Need to know
B. Least privilege
C. Job rotation
D. Separation of duties
2. Which of the following best represents SOA?
A. File server
B. An application containing both the user interface and the code allowing access to the data
C. An API that allows different components to communicate
D. A single database accessed by multiple sources
3. Which cloud computing model is geared toward software development?
A. IaaS
B. PaaS
C. SaaS
D. Private
4. Amazon’s EC2 provides virtual machines that can be controlled through a service API. Which of the following best defines this service?
A. IaaS
B. PaaS
C. SaaS
D. Public
5. Google Docs and Salesforce CRM are two examples of which cloud computing model?
A. IaaS
B. PaaS
C. SaaS
D. Public
6. Which of the following cloud computing attacks can be best described as a CSRF attack?
A. Session riding
B. Side channel
C. Cross-guest VM breach
D. Hypervisor attack
7. Which of the following best describes a wrapping attack?
A. CSRF-type attack against cloud computing resources.
B. An attack involving leveraging a new or existing VM on a physical device against another VM.
C. A SOAP message is intercepted, data in the envelope is changed, and then the data is sent/replayed.
D. The virtual machine management system on the physical machine is corrupted or administrative control is gained over it.
8. In the NIST Cloud Computing Reference Architecture, which of the following has the responsibility of transmitting the data?
A. Cloud provider
B. Cloud carrier
C. Cloud broker
D. Cloud consumer
9. In the NIST Cloud Computing Reference Architecture, which component acts to manage use, performance, and delivery of cloud services, as well as the relationships between providers and subscribers?
A. Cloud provider
B. Cloud carrier
C. Cloud broker
D. Cloud consumer
10. In the NIST Cloud Computing Reference Architecture, which component acquires and uses cloud products and services?
A. Cloud provider
B. Cloud carrier
C. Cloud broker
D. Cloud consumer
Answers
1. D. While implementing cloud computing doesn’t fully address separation of duties, of the choices provided it’s the only one that makes sense. The cloud, by its nature, can separate the data owner from the data custodian (the cloud provider assumes the role).
2. C. Service Oriented Architecture (SOA) is all about software components delivering information to one another on a network, and this is the best available answer.
3. B. PaaS provides a development platform that allows subscribers to develop applications without building the infrastructure it would normally take to develop and launch software.
4. A. Amazon’s EC2 provides resizable compute capacity in the cloud via VMs that can be controlled via an API, thus fitting the definition of IaaS.
5. C. Software as a Service best describes this. SaaS is simply a software distribution model—the provider offers on-demand applications to subscribers over the Internet.
6. A. Session riding is simply CSRF under a different name and deals with cloud services instead of traditional data centers.
7. C. Wrapping attacks involve messing with SOAP messages and replaying them as legitimate.
8. B. Akin to the power distributor for the electric grid, the carrier is the intermediary for connectivity and transport between subscriber and provider.
9. C. The broker “acts as the intermediate between consumer and provider and will help consumers through the complexity of cloud service offerings and may also create value added cloud services as well.”
10. D. The consumer is the subscriber, who engages a provider for services.




