Chapter 3. Cyber Stalking, Fraud, and Abuse
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
Know the various types of Internet investment scams and auction frauds
Know specific steps to take to avoid fraud on the Internet
Have an understanding of what identity theft is and how it is done
Know specific steps that can be taken to avoid identity theft
Understand what cyber stalking is and be familiar with relevant laws
Know how to configure a web browser’s privacy settings
Know what laws apply to these computer crimes
Introduction
In every new frontier, a criminal element is bound to emerge. In times past, the high seas gave rise to pirates, and America’s Wild West produced gangs of outlaws. The Internet is no different than any other frontier: It has its share of outlaws. Besides hacking and virus creation, both mentioned in Chapter 1, “Introduction to Computer Security,” there are other dangers. Fraud is one of the most common dangers of the Internet. As more people utilize the Internet as a conduit for commerce, there arises a greater opportunity for fraud. Fraud has been a part of life for as long as civilization has existed; in past centuries “snake oil” salesmen roamed from place to place, selling face cures and elixirs. The Internet makes such fraud even easier. In fact, many experts would consider fraud to be the most prevalent danger on the Internet. There are multiple reasons for the popularity of Internet fraud among con artists. First, committing Internet fraud does not require the technical expertise that hacking and virus creation require. Second, there are a great number of people engaging in various forms of online commerce, and this large amount of business creates a great many opportunities for fraud.
There are many avenues for fraud on the Internet. In this chapter, we will explore the various major types of fraud, what the law says, and what you can do to protect yourself. Fortunately for some readers, this particular chapter is not particularly technical because most Internet fraud does not rely on in-depth technological expertise. Internet fraud merely uses the computer as a venue for many of the same fraud schemes that have been perpetrated throughout history.
How Internet Fraud Works
There are a variety of ways that fraud can be perpetrated via the Internet. The U.S. Securities and Exchange Commission (SEC) lists several types of Internet fraud on its website;1 we will briefly discuss each of them and others, but it is not possible for us to cover every variation of each fraud scheme that has been used on the Internet. Such an undertaking would fill an entire book and possibly several volumes. What we can do is to cover the most common scams and try to extrapolate some general principles that you can apply to any potential fraud. If you use these specific cases to extrapolate some general principles, then you should be prepared to avoid most fraud schemes.
1. https://www.sec.gov/reportspubs/investor-publications/investorpubscyberfraudhtm.html
Investment Offers
Investment offers are nothing new. Even some legitimate stockbrokers make their living by cold calling—that is, simply calling people (perhaps from the phone book) and trying to get them to invest in a specific stock. This practice is employed by some legitimate firms, but it is also a favorite con game for perpetrators of fraud. The Internet has allowed investment offers—both genuine and fraudulent—to be more easily disseminated to the general public. Most readers are probably familiar with investment offers flooding their inbox on a daily basis. Some of these email notifications try to entice you to become directly involved with a particular investment plan; other emails offer seemingly unbiased information from investors, free of charge. (Unfortunately, much of this advice is not as unbiased as it might appear to be.) While legitimate online newsletters can help investors gather valuable information, keep in mind that some online newsletters are fraudulent.
Common Schemes
One of the more common schemes involves sending out an email that suggests that you can make an outrageous sum of money with a very minimal investment. Perhaps the most famous of these schemes has been the Nigerian fraud. In this scenario, an email is sent to a number of random email addresses. Each one contains a message purporting to be from a relative of some deceased Nigerian doctor or government official. The deceased person will be someone you would associate with significant social standing, thus increasing the likelihood that you would view the offer more favorably. The offer goes like this: A person has a sum of money he wishes to transfer out of his country, and for security reasons, he cannot use normal channels. He wishes to use your bank account to “park” the funds temporarily. If you will allow him access to your account, you will receive a hefty fee. If you do agree to this arrangement, you will receive, via normal mail, a variety of very official-looking documents, enough to convince most casual observers that the arrangement is legitimate. You will then be asked to advance some money to cover items such as taxes and wire fees. If you actually send any money, you lose it, and you will never hear from these individuals again.2
2. www.lbl.gov/IT/CIS/CITG/email/419-Fraud.html
Now consider this investment scam, and variations of it, from a logical point of view. If you had large sums of money you needed to transfer, would you send it to a person in a foreign country, someone you had never met? Wouldn’t you be worried that the recipient would cash out her account and take the next plane to Rio? If a person needs to transfer money internationally, why doesn’t he just transfer the money to an account in The Bahamas? Or cash out the account and send it via FedEx or UPS to a storage facility in the United States? The point is that there are many ways a person could get money out of a country without trusting some stranger he has never seen before. That fact alone should indicate to you that this offer is simply not legitimate. This concept is the first general principle you should derive concerning fraud. In any offer, consider the point of view of the person offering it. Does it sound as if he is taking an inordinately large risk? Does the deal seem oddly biased in your favor? Put yourself in his position. Would you engage in the deal if you were in his position? If not, then this factor is a sign that the deal might not be what it seems.
Investment Advice
Blatant fraud schemes like the Nigerian scheme just discussed are not the only investment pitfall on the Internet. Some companies pay the people who write online newsletters to recommend their stocks. While this activity isn’t actually illegal, U.S. federal securities laws do require the newsletters to disclose that the authors were paid to proffer this advice. Such laws are in place because when the writers are recommending any product, their opinion might be swayed by the fact that compensation is being provided to them for that opinion. Many online investment newsletters do not provide this disclosure, which means that the “unbiased” stock advice you are getting could actually be quite biased. Rather than getting the advice of an unbiased expert, you may be getting a paid advertisement. This pitfall is one of the most common traps of online investment advice; it is more common than the blatant frauds.
Sometimes these online stock bulletins can be part of a wider scheme, often called a pump and dump. A classic pump and dump is rather simple. The con artist purchases large amounts of a stock that is virtually worthless. The con artist then artificially inflates the value in several ways. One common method is to begin circulating rumors on various Internet bulletin boards and chat rooms that the stock is about to go up significantly. Often it is suggested by the trickster that the company has some new innovative product due to come out in the next few weeks. Another method is to simply push the stock on as many people as possible. The more people vying to buy a stock, the higher its price will rise. If both methods are combined, it is possible to temporarily double or triple the value of the worthless stock. The perpetrator of the fraud, who purchased volumes of the stock at a very low price before executing this scheme, dumps the stock when its price goes as high as she thinks it can. In a short time, and certainly by the time the company’s next quarterly earnings report is released, the stock returns to its real value. This sort of scheme has been very popular in the past several decades; thus, you should always be wary of such “insider” information. If a person is aware that Company X is about to release an innovative new product that will drive up her stock value, why would she share that information with total strangers?
The SEC lists several tips for avoiding pump and dump scams:3
3. www.sec.gov/investor/pubs/pump.htm
Consider the source. Especially if you are not well versed in the market, make sure you accept advice only from well-known and reputable stock analysts.
Independently verify claims. Do not simply accept someone else’s word about anything.
Research. Read up on the company, the claims about the company, its stock history, and so forth.
Beware of high-pressure tactics. Legitimate stock traders do not pressure customers into buying. They help customers pick stocks that customers want. If you are being pressured, that is an indication of potential problems.
Be skeptical. A healthy dose of skepticism can save you a lot of money. As the saying goes, “If it sounds too good to be true, it probably is.”
Make sure you thoroughly research any investment opportunity.
The truth is that these types of fraud depend on the greed of the victim. It is not my intent to blame victims of fraud, but it is important to realize that if you allow avarice to do your thinking for you, you are a prime candidate to be a victim of fraud. Your 401(k) or IRA may not earn you exorbitant wealth overnight, but it is steady and relatively safe. (No investment is completely safe.) If you are seeking ways to make large sums of money with minimal time and effort, then you are an ideal target for perpetrators of fraud.
Auction Fraud
Online auction sites, such as eBay, can be a wonderful way to find merchandise at very good prices. I routinely use such auctions to purchase goods. However, any auction site can be fraught with peril. Will you actually get the merchandise you ordered? Will it be “as advertised”? Most online auctions are legitimate, and most auction websites take precautions to limit fraud related to users’ transactions. But problems still occur. In fact, the U.S. Federal Trade Commission (FTC) lists the following four categories of online auction fraud:4
4. https://www.onguardonline.gov/articles/0020-shopping-online
Failure to send the merchandise
Sending something of lesser value than advertised
Failure to deliver in a timely manner
Failure to disclose all relevant information about a product or terms of the sale
The first category, failure to deliver the merchandise, is the most clear-cut case of fraud and is fairly simple. Once you have paid for an item, no item arrives. The seller simply keeps your money. In organized fraud, the seller will simultaneously advertise several items for sale, collect money on all the auctions, and then disappear. Typically, the entire process is done with a fake identification, using a rented mailbox and an anonymous email service. The person then walks away with the proceeds of the scam.
The second category of fraud, delivering an item of lesser value than the one advertised, can become a gray area. In some cases, it is outright fraud. The seller advertises something about the product that simply is not true. For example, the seller might advertise a signed copy of the first printing of a famous author’s book but then instead ship you a fourth printing with either no autograph or one that is unverified. However, in other cases of this type of problem, it can simply be that the seller is overzealous or frankly mistaken. The seller might claim his baseball was signed by a famous athlete but not be aware himself that the autograph is a fraud.
The second category is closely related to the fourth item on the FTC list: failure to disclose all relevant facts about the item. For example, a book might be an authentic first printing and autographed but be in such poor physical condition as to render it worthless. This fact may or may not be mentioned in advance by the seller. Failure to be forthcoming with all the relevant facts about a particular item might be the result of outright fraud or simply of the seller’s ignorance. The FTC also lists failure to deliver a product on time as a form of fraud. It is unclear whether or not that is fraud in many cases or merely woefully inadequate customer service.
The FTC lists three other areas of bidding fraud that are growing in popularity on the Internet:4
Shill bidding: This occurs when fraudulent sellers (or their “shills”) bid on the seller’s items to drive up the price.
Bid shielding: This occurs when fraudulent buyers submit very high bids to discourage other bidders from competing for the same item. The fake buyers then retract their bids so that people they know can get the item at a lower price.
Bid siphoning: This occurs when con artists lure bidders off legitimate auction sites by offering to sell the “same” item at a lower price. Their intent is to trick consumers into sending money without proffering the item. By going offsite, buyers lose any protections the original site may provide, such as insurance, feedback forms, or guarantees.
Shill Bidding
Shill bidding is probably the most common of these three auction frauds. It is not very complex. If the perpetrator is selling an item at an auction site, she will also create several fake identities. She will use these fake identities to bid on the item and thus drive up the price. It is very difficult to detect if such a scheme is in operation. However, a simple rule of thumb on auctions is to decide, before you start bidding, what your maximum price is. And then, under no circumstances do you exceed that price by even one penny.
Bid Shielding
While shill bidding may be difficult to combat, bid shielding can be addressed fairly easily by the proprietors of the auction site. Many of the major auction sites, such as eBay, have taken steps to prevent bid shielding. The most obvious is to revoke bidding privileges for bidders who back out after they have won an auction. So if a person puts in a very high bid to keep others away and then at the last moment retracts his bid, he might lose his ability to be on that auction site.
Bid Siphoning
Bid siphoning is a less common practice than the other forms of auction fraud. In this scheme, the perpetrator places a legitimate item up for bid on an auction site. But then, in the ad for that item, she provides links to sites that are not part of the auction site. The unwary buyer who follows those links might find himself on an alternative site that is a “setup” to perpetrate some sort of fraud.
All of these tactics have a common aim: to subvert the normal auction process. The normal auction process is an ideal blend of capitalism and democracy. Everyone has an equal chance to obtain the product in question if she is willing to outbid the other shoppers. The buyers themselves set the price of the product, based on the value they perceive the product to have. In my opinion, auctions are an excellent vehicle for commerce. However, unscrupulous individuals will always attempt to subvert a process for their own goals.
Identity Theft
Identity theft is a growing problem and a very troubling one. The concept is rather simple, though the process can be complex, and the consequences for the victim can be quite severe. The idea is simply for one person to take on the identity of another. This is usually attempted to make purchases; but identity theft can be done for other reasons, such as to obtain credit cards or even a driver’s license in the victim’s name. If the perpetrator obtains a credit card in someone else’s name, then he can purchase products, and the victim of this fraud is left with debts she was not aware of and did not authorize.
In the case of getting a driver’s license in the victim’s name, this fraud might be attempted to shield the perpetrator from the consequences of her own poor driving record. For example, a person might get your driving information to create a license with her own picture. Perhaps the criminal in this case has a very bad driving record and even warrants out for immediate arrest. Should the person be stopped by law enforcement officers, she can show the fake license. When the police officer checks the license, it is legitimate and has no outstanding warrants. However, the ticket the criminal receives will be going on your driving record because it is your information on the driver’s license. It is also unlikely that the perpetrator of that fraud will actually pay the ticket, so at some point you—whose identity was stolen—will receive notification that your license has been revoked for failure to pay a ticket. Unless you can then prove, with witnesses, that you were not at the location the ticket was given at the time it was given, you may have no recourse but to pay the ticket in order to reestablish your driving privileges.
The U.S. Department of Justice defines identity theft in this manner:5
5. https://www.justice.gov/criminal-fraud/identity-theft/identity-theft-and-identity-fraud
Identity theft and identity fraud are terms used to refer to all types of crime in which someone wrongfully obtains and uses another person’s personal data in some way that involves fraud or deception, typically for economic gain.
The Internet has made the process of stealing a person’s identity even easier than it used to be. Many states now have court records and motor vehicle records online. In some states, a person’s Social Security number is used as the driver’s license number. So if a criminal gets a person’s Social Security number, he can look up that person’s driving record, perhaps get a duplicate of the person’s license, find out about any court records concerning that person, and, on some websites, even run the person’s credit history. Later in this book, we will examine using the Internet as an investigative tool. Like any other tool, it can be used for benign or malevolent purposes. The same tools you can use to do a background check on a prospective employee can be used to find out enough information to forge someone else’s identity.
FYI: Alternate Means of Identity Theft
A perpetrator can conduct identity theft without using the Internet. A ring of criminals in the Dallas–Fort Worth metroplex were working with waiters in restaurants. When the waiter took your credit card or debit card to pay for the meal, he would also use a small handheld device (kept hidden in a pocket) to scan in your credit card information. He would then give this information to the identity theft ring, which could either make online purchases or use the stolen information to produce fake credit cards with your name and account data. The only way to avoid this sort of danger is to never use your credit or debit card unless it is going to be processed right in front of you. Do not let someone take your card out of your sight to process it.
Phishing
One of the more common ways to accomplish identity theft is via a technique called phishing, which is the process of trying to induce the target to provide you with personal information. For example, the attacker might send out an email purporting to be from a bank and telling recipients that there is a problem with their bank account. The email then directs them to click on a link to the bank website, where they can log in and verify their account. However, the link really goes to a fake website set up by the attacker. When the target goes to that website and enters his information, he will have just given his username and password to the attacker.
Many end users today are aware of these sorts of tactics and avoid clicking on email links. But unfortunately, not everyone is so prudent, and this attack still is effective. In addition, attackers have come up with new ways of phishing. One of these methods is called cross-site scripting. If a website allows users to post content that other users can see (such as product reviews), the attacker then posts content, but instead of being a review or other legitimate content, it is a script (JavaScript or something similar). Now when other users visit that web page, instead of loading a review or comment, their browsers will load the attacker’s script. That script may do any number of things, but it is common for the script to redirect the end user to a phishing website. If the attacker is clever, the phishing website looks identical to the real one, and end users are not aware that they have been redirected. Cross-site scripting can be prevented by web developers filtering all user input. Cross-site scripting will be dealt with in more detail in Chapter 6, “Techniques Used by Hackers.”
Phishing emails have become more sophisticated over the years. One particular phishing scam that began in 2018 exploits exposed passwords and the possible embarrassment of the victim. The scam works like this: The attacker gets a list of exposed passwords from a site such as https://haveibeenpwned.com, and then emails people from that list. The email claims the attacker has malware on the victim’s computer and validates that claim by sharing the victim’s password. The email then claims to have spyware on the computer, which has observed the victim viewing pornography and pleasuring himself while doing so. The email claims to have taken over the web cam and to have video proof. The attacker says that if a certain amount of money is not deposited in a bitcoin wallet within 24 hours, he will send the video to colleagues and family members. This is an example of a rather sophisticated phishing scam. First, the attacker gains credibility by using a real password. Then that attacker exploits the fact that if enough emails are sent out, at least some will be received by those who fall for the allegation (that is, visiting pornography and behaving in an embarrassing manner). This scheme shows that attackers are becoming better at their attack methodology. (More advanced forms of phishing, such as spear phishing and whaling, will be discussed in Chapter 7, “Industrial Espionage in Cyberspace.”)
Cyber Stalking
Stalking, which has often been a prelude to violent acts, including sexual assault and homicide, has received a great deal of attention in the past few years. Many states have passed a variety of anti-stalking laws. However, stalking has expanded into cyberspace. Cyber stalking involves using the Internet to harass another person; or, as the U.S. Department of Justice puts it:6
6. https://www.justice.gov/ovw/stalking
Although there is no universally accepted definition of cyber stalking, the term is used in this report to refer to the use of the Internet, e-mail, or other electronic communications devices to stalk another person. Stalking generally involves harassing or threatening behavior that an individual engages in repeatedly, such as following a person, appearing at a person’s home or place of business, making harassing phone calls, leaving written messages or objects, or vandalizing a person’s property. Most stalking laws require that the perpetrator make a credible threat of violence against the victim; others include threats against the victim’s immediate family; and still others require only that the alleged stalker’s course of conduct constitute an implied threat. While some conduct involving annoying or menacing behavior might fall short of illegal stalking, such behavior may be a prelude to stalking and violence and should be treated seriously.
If someone uses the Internet to harass, threaten, or intimidate another person, then the perpetrator is guilty of cyber stalking. The most obvious example is sending threatening email. The guidelines on what is considered “threatening” can vary a great deal from jurisdiction to jurisdiction. But a good rule of thumb is that if the email’s content would be considered threatening in normal speech, then it will probably be considered a threat if sent electronically. Other examples of cyber stalking are less clear. If you request that someone quit emailing you, yet she continues to do so, is that a crime? Unfortunately, there is no clear answer on that issue. The truth is that it may or may not be considered a crime, depending on factors such as the content of the emails, the frequency, the prior relationship between the recipient and the sender, and the jurisdiction.
Real Cyber Stalking Cases
The following cases, also from the Department of Justice website, illustrate cases of cyber stalking. Examining the facts in these cases might help you to get an idea of what legally constitutes cyber stalking. While many of the cases discussed here are recent, some older cases are also discussed to give you a complete understanding of this issue:
This first case is old, but it is a pivotal case in the history of cyber stalking. In the first successful prosecution under California’s cyber stalking law, prosecutors in the Los Angeles District Attorney’s Office obtained a guilty plea from a 50-year-old former security guard who used the Internet to solicit the rape of a woman who rejected his romantic advances. The defendant terrorized his 28-year-old victim by impersonating her in various Internet chat rooms and online bulletin boards, where he posted, along with her telephone number and address, messages that she fantasized about being raped. On at least six occasions, sometimes in the middle of the night, men knocked on the woman’s door, saying they wanted to rape her. The former security guard pled guilty in April 1999 to one count of stalking and three counts of solicitation of sexual assault. He faced up to 6 years in prison.
In 2016 Kassandra Cruz was sentenced to 22 months in prison for cyber stalking. Cruz was, ironically, a criminal justice student who became obsessed with a woman whose pictures she had found on a pornographic site. Cruz began a campaign of emailing, posting social media messages, and sending more than 900 phone calls and texts.
In 2017 the FBI and Waltham, Massachusetts, police investigated the case of Ryan Lin, of Newton, Massachusetts, who was accused of carrying out a campaign of computer hacking and online harassment. The alleged attacks went on for over a year. While his attacks never escalated to real-world physical attacks, Lin still committed a serious crime. Lin was also accused of sending child pornography, and he was ultimately sentenced to 17 years in prison.
In October 2017, Heriberto Latigo was sentenced to 5 years in prison for his cyber stalking crimes. The issues began in 2013, when he was involved in a romantic relationship with a woman. Latigo forced the woman to send him nude pictures of herself, harassed her online, and blackmailed her. After the relationship ended, he continued to blackmail his victim for sexual favors and sent her violent images as threats.
In September 2018 Joel Kurzynski pled guilty to cyber stalking charges. Kurzynski was a former information technology professional. Beginning in 2017, he conducted a campaign including death threats and hate speech against two individuals he knew. He created fake profiles of his victims on social media sites and used those profiles to seek sadomasochistic or underage relationships. Kurzynski was sentenced to 30 months in prison and 3 years of supervised release after that.
Robert James Murphy was the first person charged under federal law for cyber stalking. He was accused of violating Title 47 of U.S. Code 223, which prohibits the use of telecommunications to annoy, abuse, threaten, or harass anyone. Mr. Murphy was accused of sending sexually explicit messages and photographs to his ex-girlfriend. This activity continued for a period of years. He was charged and eventually pled guilty to two counts of cyber stalking.
James Allen was convicted in 2015 of both child pornography and cyber stalking. He was accused of having harassed 18 New York girls online. He used the harassment to extort illicit pictures from the girls.
Clearly, using the Internet to harass people is just as serious a crime as harassing them in person. And it can lead to real-world crimes. This problem has even extended to workplace issues. For example, court cases have held that unwanted email pornography can be construed as sexual harassment. If an employee complains about unwanted email, the employer has a duty to at least attempt to ameliorate the situation. This attempt can be as simple as installing a very inexpensive spam blocker (software that tries to limit or eradicate unwanted email). However, if the employer takes no steps whatsoever to correct the problem, that reticence may be seen by a court as contributing to a hostile work environment. As previously stated, if the stalking act would be considered harassment in person, then it would be considered harassment in cyberspace. Black’s Law Dictionary defines harassment as follows:7
7. Black’s Law Dictionary, 1999, West Publishing Company, 7th edition
A course of conduct directed at a specific person that causes substantial emotional distress in such person and serves no legitimate purpose.
Words, gestures, and actions that tend to annoy, alarm, and abuse (verbally) another person.
Usually law enforcement officials need some credible threat of harm in order to pursue harassment complaints. In simple terms, this means that if you are in an anonymous chat room and someone utters some obscenity, that act probably will not be considered harassment. However, if you receive specific threats via email, those threats would probably be considered harassment.
Many states specifically prohibit cyber stalking; and in general, existing anti-stalking laws can be applied to the Internet. In 2001, in California a man was convicted of cyber stalking under existing anti-stalking statutes.8 Other countries also have existing anti-stalking laws that can be applied to cyber stalking as well. Canada has had a comprehensive anti-stalking law since 1993. Unfortunately, there are many similar cases. Just a few include the following:
8. Identity Theft and Assumption Deterrence Act of 1998, U.S.C. 1028
This first case is a bit older, but it illustrates how these crimes can escalate. From 2010, there is the case of 70-year-old Joseph Medico, who met a 16-year-old girl at his church. Medico followed the girl to her car and tried to talk her into going to dinner with him and then back to his home. When she rejected his advances, he began calling and texting her several times a day. His activities escalated until the girl reported the activities and Medico was arrested for stalking.
In March 2018 Juan R. McCullum was sentenced to 1 year and 361 days in federal prison on conspiracy and cyber stalking charges. McCullum was a former aide to Virgin Islands Delegate Stacey Plaskett. He plead guilty to circulating nude images and video of a member of congress and her husband in an attempt to block Mrs. Plasketts re-election.
In December 2018, Joel Kurzynski was sentenced to 30 months in prison and 3 years of supervised release for conducting cyber stalking against multiple victims. Kurzynski was also ordered to pay over $37,000 in restitution. According to court documents, Kurzynski orchestrated spam phone calls, created fake dating profiles portraying a victim as seeking underage relationships, and made death threats.
In the summer of 2018 Jeron Ramos allegedly shot and killed five people in a Maryland newspaper office. According to court records, this violent attack was preceded by a lengthy harassment campaign including very angry Twitter postings and emails.
In February 2009 in the United Kingdom, Edward Richardson stabbed his wife to death because she had changed her marital status on her Facebook page from married to single.
In 2018 Ho Ka Terence Yung was convicted of cyber stalking. In this case the perpetrator did not attempt to directly physically attack the victim but rather to incite violence against the victim. According to court records, Yung was upset that he had been rejected from law school, and he began a campaign of cyber stalking against an admissions officer that included fabricating stories that his victim had raped an 8-year-old girl. Yung also posted ads on Craigslist, pretending to be the victim of the cyber stalking and indicating interest in sadistic and violent sexual activity.
In 2012, in the town of McKinney, Texas, which just happens to be very close to my own home, a man used Craigslist apartment ads to lure women to a location so he could rape them. He was captured, convicted, and sentenced to 20 years in prison.
2015 brought a new twist on cyber stalking. David Matusiewicz, his sister Amy Gonzalez, and his mother Lenore Matusiewicz were the first defendants in the United States charged with cyber stalking resulting in death. The three were found guilty of conspiracy and cyber stalking that led to the death of Mr. Matusiewicz’s ex-wife. The victim was killed by Mr. Matusiewicz’s father after a long pattern of cyber stalking by the defendants in this case. The shooter took his own life after shooting the victim and the victim’s friend as they showed up at a Delaware courthouse for a child support hearing.
One could fill several volumes with similar cases. The common element of all but the last of these is that a computer was used as either an agent or a catalyst for a real-world violent crime. These cases should make it clear that computer crime is not just about hacking, fraud, and property crimes. It is becoming more common for law enforcement officers to find a computer/Internet element in traditional crimes. And I am sure most readers have heard about Craigslist’s “erotic services” ads, which are in reality advertisements for prostitution. The last case shows that although a computer might not always be a part of the crime, it could lead to evidence of the crime. There are numerous other cases of criminals posting Facebook messages, tweets, and YouTube videos that contain incriminating evidence and, in some cases, full confessions.
Another phenomenon that has been growing in frequency is referred to as swatting. This occurs when someone calls 911, claiming that a violent crime is in progress and providing the address of the intended victim. The goal is to get police to come with an aggressive tactical response (that is, a SWAT team) and at least significantly frighten the victim. In May 2018, Tyler Barriss pled guilty to such an incident. He had made a swatting call claiming that the victim had shot his own father and was holding relatives hostage in the home. When police showed up at the victim’s home in response to the swatting call, the victim reached for his waistband, and the police believed he was reaching for a gun and shot him.
How to Evaluate Cyber Stalking
Unfortunately, it is not always clear if a given communication rises to the level of cyber stalking or not. One obvious example of cyber stalking is the sending of threatening email messages. But even the definitions of harass, threaten, and intimidate are somewhat vague. Obviously, if a person sends an email to another person, threatening to kill that person, and provides photos of the recipient to demonstrate that the sender is familiar with the target’s appearance and address, that would clearly be cyber stalking. But what about a situation in which a person is upset with a product and emails a harshly worded message to an executive at the product’s manufacturer? If the email has a vague threat, such as “You will get what you deserve,” is that cyber stalking? This is not an easy question to answer, and no single answer applies to all jurisdictions and all situations. What constitutes threatening, harassing, or intimidating can vary a great deal from jurisdiction to jurisdiction. But a general guideline is that that if the content of the email (or instant message, newsgroup posting, and so on) would be considered threatening in normal speech, then it would probably also be considered a threat if sent electronically.
Another element of a threat is viability. Is the threat credible? On the Internet, people are frequently more vocal and often more hostile than they are in other venues. That means a law enforcement officer must to some extent differentiate between someone simply spouting off or venting versus someone making a real, serious threat. How do you determine whether to take a threat seriously? The key is to look for four factors:
Credibility: For a threat to be credible, there must be some reasonable expectation that it could be carried out. For example, suppose a woman in Nebraska is on an Internet discussion board and receives a general threat from another user living in Bangkok in the course of a heated debate. In this scenario, the sender very likely has no idea where the recipient lives. Indeed, because many people use screen names on the Internet, the sender may not even know the recipient’s real name, gender, age, or appearance. That means this threat has a very low level of credibility. If, however, the woman in Nebraska receives a threat from the user in Bangkok accompanied with personal information such as her address, her place of work, or a photo of her, that is a very credible threat.
Frequency: Unfortunately, people often make ill-advised comments on the Internet. Often, however, a single hostile comment is just a person reacting too emotionally and too quickly online. For this reason, this type of comment is of less concern than a pattern of threats over a period of time. Frequently, stalkers escalate their comments and threats over time, gradually building up to a point where they act violently. While there certainly may be cases in which a single threat warrants investigation, as a general rule, isolated threats are of less concern than a pattern of harassment and threats.
Specificity: Specificity refers to how specific the perpetrator is regarding the nature of the threat, the target of the threat, and the means of executing the threat. Of course, it is very important for law enforcement officers to realize that real threats can sometimes be vague. Real threats aren’t always specific, but specific threats are usually real. As an example, an email saying “You will pay for that” is of less concern than an email containing a specific threat of a very specific type of violence, such as “I will wait for you after work and shoot you in the head with my 9mm” along with a photo of the recipient leaving work. (The photo also makes it very credible.) This threat is specific and should be of concern to law enforcement.
Intensity: Intensity refers to the general tone of the communications, the nature of the language, and the level of the threat. Graphic and particularly violent threats should always be taken very seriously by law enforcement. Often, when someone is simply venting or reacting emotionally, he may make statements that could be considered threatening. In these cases, however, most people make low-intensity statements, such as threatening to beat someone up. Threats such as these are of less concern than, say, a threat to dismember someone. This is because normal, nonviolent people can lose their temper and want to punch someone in the nose. But normal, nonviolent people don’t usually lose their temper and want to cut someone into pieces with a chainsaw. Anytime a threat is raised to a level that is beyond what a reasonable person might say, even in a hostile situation, that threat becomes of greater concern.
All four of these criteria need not be met for a cyber threat to be considered viable. Law enforcement officers must always rely on their own judgment and should err on the side of caution. A particular officer may feel a given threat is very serious even if several of these criteria are not met. That officer should then treat the threat as a serious concern. And if one or more of these criteria are present, the officer should always treat the matter seriously, regardless of her personal inclinations. A credible, frequent, specific, and intense threat is very often a prelude to real-world violence.
This is similar to the traditional law enforcement doctrine of examining means, motive, and opportunity. Does the person have the means to committee the crime? Does he or she have a motive? Does the person have an opportunity? These questions apply not just in the real world but in cyberspace, where the means and opportunity are significantly expanded.
Crimes Against Children
Of special concern are cyber stalking cases involving minors. Pedophiles now use the Internet extensively to interact with minors and, in many cases, arrange in-person meetings with children. This must be a significant concern for all parents, law enforcement officials, and computer security professionals. Often, pedophiles use chat rooms, online discussion boards, and various other Internet media to meet with children. The discussions often turn sexually explicit and eventually lead to attempts to meet in person. Fortunately, this sort of activity is relatively easy to investigate. The pedophile normally wishes to continue communication with the victim and to escalate communication. The process of cultivating a relationship with the victim is referred to as grooming, and it often includes sending gifts to the victim. A common gift is a cell phone, allowing the pedophile and the victim to communicate through a channel the victim’s parents are not aware exists. While variations exist, the common process is as follows:
The initial conversation the predator initiates with a minor is likely to be about an innocuous topic that is of interest to a minor. During this initial phase, the predator is often looking for key signs that this child might be a likely target. For example, children who feel like they don’t belong, are not getting enough attention from parents, or are going through some major life issue such as parental divorce are likely targets.
Once the predator has identified a potential target, he begins trying to extend the conversations outside the chat room or social page into private chats or emails. He is also likely be very sympathetic to whatever the child’s problem is. Predators often use flattery with their intended victims. Children who feel like they don’t belong or who have low self-esteem are very susceptible to these sorts of tactics.
The next step is to begin easing sexual content into the conversation. The predator’s intent is to gradually get the child comfortable discussing sexual topics. Usually he is careful to take this phase carefully so as not to cause the targeted child to panic. If this process proceeds far enough, the predator suggests a face-to-face meeting. In some cases the face-to-face meeting is expressly for the purpose of sex; in others, the predator lures the child to a location with the promise of some seemingly benign activity such as video games or a movie.
Of course, there are sometimes deviations from this pattern. Some predators move much quicker to meet with the child face to face. A predator may also avoid sexual conversations at all and simply try to lure the child out of her house with the intent of forcibly molesting her. Whether the predator chooses to lure the child and then force a sex act or attempts to seduce the child depends on how the predator views the act. It may surprise some readers to discover that some pedophiles actually view themselves not as child molesters but rather as being in a relationship with the child. They actually think their behavior is acceptable and that society simply doesn’t understand. This sort of pedophile is much more likely to use a method of gradually increasing the sexual content and explicitness of the online conversation. Their intent is to seduce the child.
A number of well-publicized sting operations have aimed to catch online predators. In these operations, adults (sometimes law enforcement officers, sometimes not) pose as minors online and wait for a pedophile to approach them and attempt to engage in sexually explicit conversations. These attempts have been quite controversial. Given the nature of the activities, however, it seems unlikely that a non-pedophile adult could accidentally or mistakenly become involved in explicit sexual discussions with a minor. It is even less likely that a non-pedophile adult would attempt to meet in the physical world with a person she believed to be a minor. It would certainly seem that these programs, if conducted properly, can be invaluable in combating online predation.
It should be noted that the U.S. government and many states have online sex offender databases that can be used to look up anyone who might be on the sex offender list. Many of these databases provide photos and birthdates to help prevent misidentifications due to similar names. The following are a few such directories:
Texas: https://records.txdps.state.tx.us/SexOffenderRegistry
U.S. Department of Justice: https://www.nsopw.gov/?AspxAutoDetectCookieSupport=1
Alabama: https://app.alea.gov/Community/wfSexOffenderSearch.aspx
New York: http://www.criminaljustice.ny.gov/SomsSUBDirectory/search_index.jsp
California: https://oag.ca.gov/sex-offender-reg
Unfortunately, child predators are a problem everywhere—in every state, city, and nation. Various nations have set up task forces to address these crimes. In the United States, each state has an Internet Crimes Against Children (ICAC) task force (see https://www.icactaskforce.org). In the ICAC program, state, local, and federal authorities work to combat crimes against children. Other nations have similar task forces.
Laws About Internet Fraud
Over the past several years, various legislatures (in the United States and in other countries) have passed laws defining Internet fraud and stating the prescribed punishments. In many cases, existing laws against fraud and harassment are applicable to the Internet as well; however, some legislators have felt that cybercrime warrants its own distinct legislation.
Identity theft has been the subject of various state and federal laws. Most states now have laws against identity theft. This crime is also covered by federal law. In 1998, the federal government passed 18 U.S.C. 1028, also known as the Identity Theft and Assumption Deterrence Act of 1998. This law made identity theft a federal crime. Throughout the United States, federal law now covers identity theft. In many states identity theft is also covered by state law.
One nation that has decided to crack down hard on cyber criminals is Romania. Some experts have described Romanian cybercrime law as the strictest in the world. However, what is especially interesting about Romanian law is how specific it is. The crafters of this legislation went to some effort to very specifically define all the terms used in the legislation. This specificity is very important in order to prevent defendants from finding loopholes in laws. Unfortunately, the Romanian government only took such measures after media sources around the world identified the country as a “Citadel for Cybercrime.” The country’s reactive approach to cybercrime is probably not the best solution.
The University of Dayton School of Law has a website devoted to cybercrime. The school has some rather extensive links on cybercrime, cyber stalking, and other Internet-based crimes. As we move forward in the twenty-first century, we can expect to see more law schools with courses dedicated to cybercrime.
An interesting phenomenon has begun in the past few years: Attorneys have begun to specialize in cybercrime cases. The fact that there are lawyers who specialize in this area of law is a strong indicator that Internet crime is a growing problem in modern society.
Protecting Yourself Against Cybercrime
Now that you know about the various types of fraud that are prevalent on the Internet and have looked at the relevant laws, you might be wondering what you can do to protect yourself. There are several specific steps you can take to minimize the chances of being the victim of Internet crime. There are also some clear guidelines for how to proceed if you become a victim.
Protecting Against Investment Fraud
To protect yourself against investment fraud, follow these guidelines:
Only invest with well-known, reputable brokers.
If it sounds too good to be true, then avoid it.
Ask yourself why this person is informing you of this great investment deal. Why would a complete stranger decide to share an incredible investment opportunity with you?
Remember that even legitimate investment involves risk; never invest money that you cannot afford to lose.
Protecting Against Identity Theft
When the issue is identity theft, prevention measures are clear:
Do not provide your personal information to anyone if it is not absolutely necessary. When communicating on the Internet with anyone you do not personally know, do not reveal anything about yourself—not your age, occupation, real name, or anything else.
Destroy documents that have personal information on them. If you simply throw away bank statements and credit card bills, then someone rummaging through your trash can get a great deal of personal data. You can obtain a paper shredder from an office supply store or many retail department stores for less than $20. Shred these documents before disposing of them. This rule may not seem like it is related to computer security, but information gathered through nontechnical means can be used in conjunction with the Internet to perpetrate identity theft.
Check your credit frequently. Many websites, allow you to check your credit and even get your credit score for a nominal fee. (I check my credit twice per year.) If you see any items you did not authorize, you might be a victim of identity theft.
If your state has online driving records, then check yours once per year. If you see driving infractions that you did not commit, this evidence is a clear sign that your identity is being used by someone else. In an Chapter 13, “Cyber Detective,” we will explore in detail how to obtain such records online, often for less than $5.
To summarize, the first step in preventing identity theft is restricting the amount of personal information you make available. The next step is simply monitoring your credit and driving records so that you will be aware if someone attempts to use your identity.
Another part of protecting your identity is protecting your privacy in general. This means preventing others from gaining information about you that you don’t explicitly provide them. That preventive method includes keeping websites from gathering information about you without your knowledge. Many websites store information about you and your visit to their site in small files called cookies. These cookie files are stored on your machine. The problem with cookies is that any website can read any cookie on your machine—even ones that the website you are currently visiting did not create. So if you visit one website and it stores items like your name, the site you visited, and the time you were there, then another website could potentially read that cookie and know where you have been on the Internet. One of the best ways to stop cookies you don’t want is to install anti-spyware software. We will discuss such software in more detail in a later chapter. Right now, let’s see how to change your Internet settings to help reduce threats to your privacy.
Secure Browser Settings
If you are using Microsoft Edge, you can go to Tools and use the drop-down menu to select Options. After that, you see a screen much like the one shown in Figure 3.1.
Select Advanced Settings, and you see the screen shown in Figure 3.2. Notice under settings, you can select various levels of general protection against cookies. It is recommended that you select Medium High as the level.
Note the Advanced button at the bottom of the screen. This button allows you to block or allow individual websites from creating cookies on your computer’s hard drive. Altering cookie settings on your machine is just one part of protecting your privacy, but it is an important part.
You probably also want to ensure that you have selected the InPrivate Browsing option, shown in Figure 3.2.
If you are working with Firefox, the process is similar. If you select Tools from the drop-down menu and then select Options, you see the screen shown in Figure 3.3.
If you select Privacy & Security on the left side of this screen, you then see a screen much like the one shown in Figure 3.4.
As you can see in Figure 3.4, there are a number of privacy settings for you to select, and they are self-explanatory.
If you are using Google Chrome, select Settings, and you see the screen shown in Figure 3.5. Click Advanced at the bottom of the screen to find the security settings.
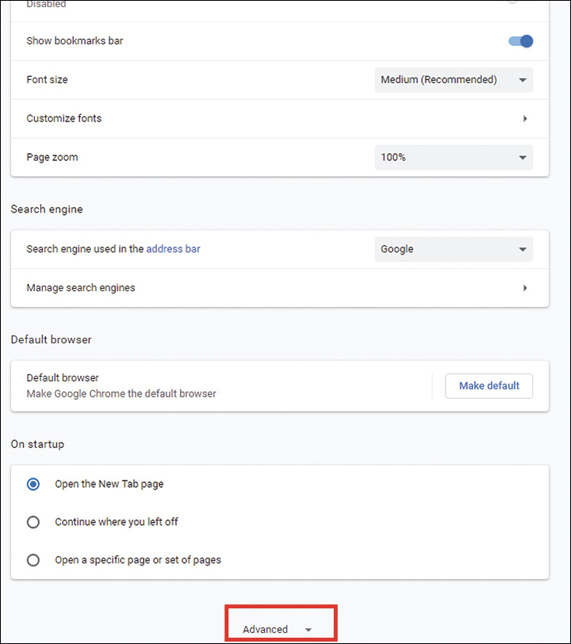
With any browser, if you make the security settings too strict, you won’t be able to view many web pages. You will have to experiment a bit with the settings to find the ones that work best for you.
Protecting Against Auction Fraud
Dealing with auction fraud involves a unique set of precautions; here are four good ideas:
Use only reputable auction sites. The most well-known site is eBay, but any widely known, reputable site will be a safer gamble than an unknown or obscure site. Such auction sites tend to take precautions to prevent fraud and abuse.
If it sounds too good to be true, don’t bid.
Some sites actually allow you to read feedback other buyers have provided on a given seller. Read the feedback and work only with reputable sellers.
When possible, use a separate credit card—one with a low limit—for online auctions. That way, should your credit card be compromised, your liability is limited. Using your debit card is simply inviting trouble.
Using online auctions can be a very good way to get valuable merchandise at low prices. However, one must exercise some degree of caution when using these services.
Protecting Against Online Harassment
Consider the following guidelines for protecting yourself from online harassment:
If you use chat rooms, discussion boards, and so forth, do not use your real name. Set up a separate email account with an anonymous service, such as Yahoo!, Gmail, or Hotmail. Then use that account and a fake name online. This makes it very hard for an online stalker to trace back to you personally.
If you are the victim of online harassment, keep all the emails in both digital and printed format. Use some of the investigative techniques we will explore later in this book to try to identify the perpetrator. If you are successful, then you can take the emails and the information on the perpetrator to law enforcement officials.
Do not, in any case, ignore cyber stalking. According to the Working to Halt Online Abuse website, 19% of cyber stalking cases escalate to stalking in the real world.
It is not the intent of this chapter or of this book to make you frightened about using the Internet. I routinely use the Internet for entertainment, commerce, and informational purposes. One simply needs to exercise some caution when using the Internet.
Summary
Clearly, fraud and identity theft are very real and growing problems. In this modern age of instant access to information and online purchasing, it is critical that you take steps to protect yourself against this issue. You must work to protect your privacy using steps outlined in this chapter. It is also imperative for law enforcement officers to obtain the skills needed to investigate and solve these sorts of cybercrimes.
Cyber stalking is one area that is often new to both civilians and law enforcement. It is very important that both groups have a clear understanding of what is, and is not, cyber stalking because, unfortunately, cyber stalking cases can escalate into real-world violence.
Test Your Skills
Multiple Choice Questions
1. Candice is discussing Internet fraud with a colleague. She is trying to explain the most common types of fraud. What is the term for the most common type of Internet investment fraud?
A. The Nigerian fraud
B. The Manhattan fraud
C. The pump and dump
D. The bait and switch
2. You have become quite active in online investing. You want to get some advice but are concerned about the veracity of the advice you receive. What is the most likely problem with unsolicited investment advice?
A. You might not earn as much as claimed.
B. The advice might not be truly unbiased.
C. The advice might not be from a legitimate firm.
D. You might lose money.
3. Juan is a security officer for an investment firm. He is explaining various scams to the brokers. What is the term for artificially inflating a stock in order to sell it at a higher value?
A. Bait and switch
B. The Nigerian fraud
C. Pump and dump
D. The Wall Street fraud
4. What is the top rule for avoiding Internet fraud?
A. If it seems too good to be true, it probably is.
B. Never use your bank account numbers.
C. Only work with people who have verifiable email addresses.
D. Don’t invest in foreign deals.
5. Which of the following is not one of the Security and Exchange Commission’s tips for avoiding investment fraud?
A. Don’t invest online.
B. Consider the source of the offer.
C. Always be skeptical.
D. Always research the investment.
6. Aliya is active on online auctions but wants to avoid auction fraud. What are the four categories of auction fraud?
A. Failure to send, failure to disclose, sending to wrong address, failure to deliver
B. Failure to send, failure to disclose, sending something of lesser value, failure to deliver
C. Failure to disclose, sending something to wrong address, failure to send, failure to deliver
D. Failure to disclose, sending something of lesser value, failure to send, sending something of greater value
7. What is the term for a seller bidding on her own item to drive up the price?
A. Bid siphoning
B. Bid shielding
C. Shill bidding
D. Ghost bidding
8. What is the term for submitting a fake but very high bid to deter other bidders?
A. Bid siphoning
B. Bid shielding
C. Shill bidding
D. Ghost bidding
9. What is typically the goal of identity theft?
A. To make illicit purchases
B. To discredit the victim
C. To avoid criminal prosecution
D. To invade privacy
10. According to the U.S. Department of Justice, identity theft is generally motivated by what?
A. Malicious intent
B. Personal hostility toward the victim
C. Economic gain
D. Thrill seeking
11. Clarence is a police detective with a small-town police department. He is trying to consider how seriously to take reports of cyber stalking. Why is cyber stalking a serious crime?
A. It is frightening to the victim.
B. It can be a prelude to violent crime.
C. It is using interstate communication.
D. It can be a prelude to identity theft.
12. What is cyber stalking?
A. Any use of the Internet to send or post threats
B. Any use of electronic communications to stalk a person
C. The use of email to send threats
D. The use of email to stalk a person
13. What do law enforcement officials usually require of a victim in order to pursue harassment allegations?
A. A verifiable threat of death or serious injury
B. A credible threat of death or serious injury
C. A verifiable threat of harm
D. A credible threat of harm
14. If you are posting anonymously in a chat room and another anonymous poster threatens you with assault or even death, is this person’s post harassment?
A. Yes; any threat of violence is harassment.
B. Probably not because both parties are anonymous, so the threat is not credible.
C. Yes; chat room threats are no different from threats in person.
D. Probably not because making a chat room threat is not the same as making a threat in person.
15. What must exist for cyber stalking to be illegal in a state or territory?
A. Specific laws against cyber stalking in that state or territory
B. Specific laws against cyber stalking in that nation
C. Nothing; existing stalking laws can apply
D. Nothing; existing international cyber stalking laws apply
16. What is the first step in protecting yourself from identity theft?
A. Never provide personal data about yourself unless absolutely necessary.
B. Routinely check your records for signs of identity theft.
C. Never use your real name on the Internet.
D. Routinely check for spyware on your computer.
17. What can you do on your local computer to protect your privacy?
A. Install a virus scanner.
B. Install a firewall.
C. Set your browser’s security settings.
D. Set your computer’s filter settings.
18. What is a cookie?
A. A piece of data that web servers gather about you
B. A small file that contains data and is stored on your computer
C. A piece of data that your web browser gathers about you
D. A small file made that contains data and then is stored on the web server
19. Which of the following is not an efficient method of protecting yourself from auction fraud?
A. Only use auctions for inexpensive items.
B. Only use reputable auction sites.
C. Only work with well-rated sellers.
D. Only bid on items that seem realistic.
20. What is the top rule for chat room safety?
A. Make certain you have antivirus software installed.
B. Never use your real name or any real personally identifying characteristics.
C. Only use chat rooms that encrypt transmissions.
D. Use chat rooms that are sponsored by well-known websites or companies.
21. Why is it useful to have a separate credit card dedicated to online purchases?
A. If the credit card number is used illegally, you will limit your financial liability.
B. You can keep better track of your auction activities.
C. If you are defrauded, you can possibly get the credit card company to handle the problem.
D. You can easily cancel that single card if you need to do so.
22. What percentage of cyber stalking cases escalate to real-world violence?
A. Fewer than 1%
B. About 25%
C. 90% or more
D. About 19%
23. If you are a victim of cyber stalking, what should you do to assist the police?
A. Nothing; it is their job, and you should stay out of it.
B. Attempt to lure the stalker into a public place.
C. Keep electronic and hard copies of all harassing communications.
D. Try to provoke the stalker into revealing personal information about himself.
24. What is the top way to protect yourself from cyber stalking?
A. Do not use your real identity online.
B. Always use a firewall.
C. Always use a virus scanner.
D. Do not give out email addresses.
Exercises
Exercise 3.1: Setting Web Browser Privacy in Microsoft Edge
This process is described in detail with images in the chapter, but here you should actually walk through the process on your own:
Select Settings from the ellipsis (…) drop-down menu in the right-hand corner of the Microsoft Edge window and then choose Settings.
Scroll down and select View Advanced Settings.
Scroll down to the Privacy and Services section.
Scroll down a bit and in the Cookies drop-down section, set your browser to Don’t Block Cookies, Block All Cookies, or Block Only Third Party Cookies.
Exercise 3.2: Using Alternative Web Browsers
If you don’t already have it, download the Firefox browser from www.mozilla.org.
Set privacy and security settings.
Projects
Project 3.1: Finding Out About Cyber Stalking and the Law
Using the Web or other resources, find out what your state’s, country’s, or province’s laws are regarding cyber stalking.
Write a brief paper describing those laws and what they mean. You may select to do a quick summary of several laws or a more in-depth examination of one law. If you choose the former, then simply list the laws and write a brief paragraph explaining what they cover. If you choose the latter option, then discuss the law’s authors, why it was written, and possible ramifications of the law.
Project 3.2: Looking for Auction Fraud
Go to any auction site and try to identify whether there are any sellers you think might be fraudulent. Write a brief paper explaining what about a particular seller indicates that he may not be dealing honestly.
Project 3.3: Examining Cyber Stalking Case Studies
Using the Web, find a case of cyber stalking that is not mentioned in this chapter. You may find some of the following websites helpful:
Write a brief paper discussing this case, with particular attention to steps you think might have helped avoid or ameliorate the situation.