Identify and describe various architectures, including embedded systems, client-server, n-tier, web, wireless, messaging, collaborative platforms, and analyze their impact on quality. (Analyze)
BODY OF KNOWLEDGE III.B
A system architecture
defines the system-level components (including subsystems), interfaces between those components, and the allocation of system-level requirements to those components and interfaces. The architectural design of a system may also consider timing and bandwidth of those interfaces. System-level components can be software, data, hardware, and humans (who implement processes and manual operations), and may also include “processes (for example, processes for providing services to users), procedures (for example, operator instructions), facilities, materials and naturally occurring entities” (ISO/IEC/IEEE 2011).
Good systems architectures address higher-level concepts and abstractions for the system. (Lower-level details are dealt with during the component design,
also called detailed design,
activities, which define the internals of each component at the hardware / software / data / process engineering level.)
Stakeholders of the systems architecture should be able to:
-
Understand what the system does
-
Understand how the system works
-
Understand how the system relates to its environment
-
Work on one piece of the system, independent of other pieces
-
Extend the system
-
Reuse one or more components or parts of the system to build another system
“Architecture is what remains when you can not take away any more things and still understand the system and explain how it works” (Kruchten 2000).
Levels of Architecture and Design
As illustrated in Figure 10.1
, there can be a hierarchy of architectures, which may include the following levels:
-
Enterprise Architecture: The enterprise architecture is the structure of organization-level components (for example, processes, systems, personnel, teams, organizational sub-units, and so on), and the relationships / interfaces between them. If software is part of the architecture used by the enterprise, then both the enterprise and its system(s) will have an impact on the design of that software.
-
System Architecture: For software that is part of a larger system, design may also include the architectural design of the system, which will be discussed in this chapter. As part of the system architecture, the system level requirements are allocated to various constituent components (subsystems or packages, including hardware, software, databases, and manual operations subsystems within the system, and so on). The major design activity at this level is to determine how to best segregate the system into its components, and to define the communications, interfaces, and interactions between those subsystems.This step may be skipped for software development projects that only include a single smaller software application, and not a complex software system or hardware/software system.
-
System of Systems: A system may also be part of a larger system of systems. For example, an organization’s financial system may be a system of systems, including a time-accounting system, payroll system, accounts payable system, account receivable system, and so on. A car is a system of systems, including an anti-lock brake system, fuel injection system, air bag system, and so on. The system of systems architecture defines the systems that make up the system of systems and the relationships and interfaces between those systems.
-
Software Architecture and Design: Software architecture and design are covered in Chapter 13 of this book.
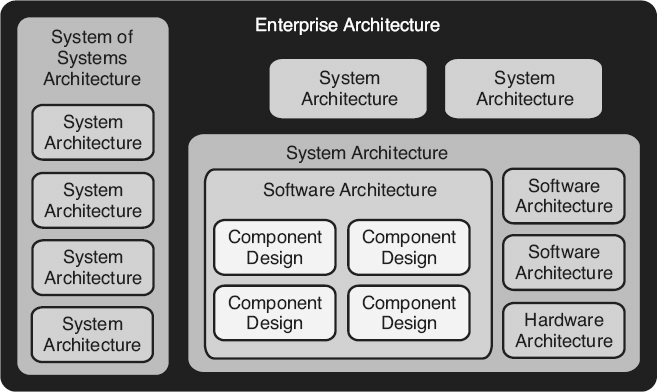
Figure 10.1
Levels of architecture and design—example.
Another example of different levels of architectural is from The Common Approach to Federal Enterprise Architecture,
(see whitehouse.gov/sites/default/files/omb/assets/egov_docs/common_approach_to_federal_ea.pdf2012
), which lists eight levels of scope for implementing an architecture:
-
International
-
National
-
Federal
-
Sector
-
Agency
-
Segment
-
System
-
Application
Embedded System
An embedded system
is a computer system with a dedicated function embedded as part of a larger system. For example, a software/hardware breaking system or fuel injection system that is a component of a larger system (car, airplane). If the software is installed into a hardware component it is often referred to as firmware,
and is stored in read-only memory (ROM), in a flash memory chip or other devices.
Embedded systems can vary widely in capability. Many embedded systems are limited to the performance of one, or a limited number of, dedicated functions or tasks, as opposed to a personal computer or mainframe. Digital watches, microwaves, mobile phones, traffic lights, and handheld calculators are just a few of the many examples of embedded systems. A system of systems like a modern automobile or aircraft has multiple embedded systems. Medical devices and weapons systems are examples of embedded systems that are complex and multifunctional. Embedded systems can range from having no user interface to a complex graphical user interface similar to a personal computer. Many embedded systems are also restricted by timing, size, power utilization, reliability, and other constraints imposed by the system’s environment.
n-Tier
In an n-tier architecture,
also called a multi-tier architecture,
the system is logically decomposed into two or more layers (levels), each with independent processing capability, creating a modularized approach to the architecture. The “n” in an n-tier architecture implies any number, such as two-tier, four-tier, five-tier, and so on.
Well-defined interfaces and information-hiding (abstraction) characterize a tiered or layered architectural style. As illustrated in Figure 10.2
, each tier interfaces with the tiers just above and/or below it, and performs part of the functionality of the whole
system. If communication is severed between two tiers, partial independent functionality within each tier, or between non-severed tiers, is still possible. For example, the telecommunications network is a classic tiered architecture. If the private branch exchange (PBX) inside a company loses connections with the local switch, employees can not make outside phone calls, but they may still be able to call other employees using the same PBX. If, however, the local switch has good connection to the PBX, but loses connection with the class 5 switch, employees can still call each other and may also have limited outside calling capacity with others sharing the same local switch.

Figure 10.2
Five-tier architecture—example.
The tiers provide abstraction because a tier does not need to know how the operations of the layer above or below it are implemented. In a tiered architecture, layers can be added, upgraded, or replaced independently without major impact to other parts of the system.
Client-Server
Client-server architectures
are a specific type of two-tier architecture, as illustrated in Figure 10.3
. For example, many computer networks within businesses are based on client-server architectures. Each computer or device on the network is either a client or a server. Central server
computers/devices on a network provide services, manage network resources (for example, the sharing of software licenses), and centralize most, or all, of the data.
The client
is the requester of services and typically runs on a decentralized access terminal, computer, or workstation. These clients download or access the centralized data, share the network resources, and utilize centralized processing capability available from the server. A thin client,
also referred to as a slim
or lean client,
primarily focuses on the user interface and on sending and receiving inputs/outputs from the server. A thin client depends on the server for most or all of its processing activities. Typically, the only software that is installed on a thin client is the user interface, networked operating system, and possibly a limited number of frequently used applications. In contrast, a fat client,
also referred to as a rich
or thick client,
typically has a large number of applications installed, and performs most of the processing functionality locally, depending on the server chiefly for shared data. A thick client can run much more independently. In fact, a thick client may be able to run without connectivity to the server for some period of time, requiring only periodic connection for data refreshing and synchronization with the rest of the system and
its users.
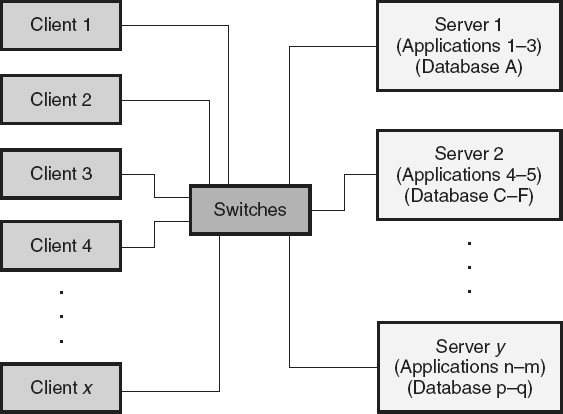
Figure 10.3
Client-server architecture—example.
Advantages of a client-server architecture include the:
-
Decentralized distribution of roles and responsibilities across the network
-
Sharing of resources and data
-
Simplified system management (for example, single point propagation of new / updated software and centralized backups)
-
Clients that can be disconnected from the server for job site remote entry and / or modification of data, coupled with the ability to refresh centralized, shared databases on the servers from distributed clients
-
Ability to have increased security protection at the server level
-
Potentially lower costs, especially if software licenses can be economically shared or if lower-cost equipment can be utilized (for example, using thin clients)
Disadvantages can include:
-
Degraded performance or resource unavailability under high network traffic conditions
-
Limitations on the level of processing available to the client if connection with the server is severed
-
Potential issues with backing up organizational assets that are not uploaded to the servers if the clients are disconnected at the time of back up
Peer-to-Peer Architecture
A peer-to-peer architecture
is a distributed applications architecture that partitions tasks or workloads between equally privileged, interconnected nodes (peers). As illustrated in Figure 10.4
, these peers are interconnected and share resources with each other across a network without the use of one or more centralized administrative systems (servers in the client-server architecture). Each peer can function as both a client and a server to other peers on the network.

Figure 10.4
Peer-to-peer architecture—example.
Web
There are three major types of web architectures, as illustrated in Figure 10.5
, including:
-
The Internet is a global network connecting millions of computers. The Internet is characterized by business-to-consumer (B to C) architectures, where Internet pages are created by businesses, organizations, and/or individuals to provide open access to consumers. This creates a community that consumers will revisit because of dynamic content-delivery capabilities.The TCP/IP network architecture is made up of four layers that interact to make the Internet work, including the:
-
Application layer: This layer provides services that can be used by applications on the host to communicate data to other applications on the same or different hosts. It defines how the Internet services operate and how those services can be used by the applications. For example, these services include FTP services for file transfer, HTTP services for web pages, and Simple Mail Transfer Protocol (SMTP) for e-mail.
-
Transportation layer: This layer performs host-to-host communications. On the sender’s side, this layer breaks up messages that an application wants to transfer into packets and attempts to deliver those packets. On the receiver’s side, this layer retrieves the information from the packets and passes it to the appropriate application. This is done using one of two protocols, Transmission Control Protocol (TCP) or User Datagram Protocol (UCP).
-
Internet layer: This layer transports Internet Protocol (IP) packets from the originating host across network boundaries to the destination host. For outgoing packets, this layer is responsible for the functions of addressing, routing, and congestion control for the Internet Protocol (IP) packets. It transmits the packet to the next-hop node by passing to the appropriate network interface layer. For incoming packets, this layer retrieves the packets and sends them to the transportation layer.
-
Network interface layer: This layer, also called the network access layer, is responsible for packet forwarding through the network, including routing through intermediate routers, to the appropriate destination node using its unique Internet Protocol (IP) address. Packets from the same message may take different routes. Some may never end up at their destination, in which case, if the TCP protocol is used, TCP requests retransmission of lost or damaged packages. If the UDP protocol is used, the application must take care of any errors.
-
-
An intranet resides behind the firewall of an organization and is only accessible to people within the organization. Intranets typically implement a business-to-employee (B to E) architecture where intranet pages integrate and consolidate enterprise information. This allows employees to access and utilize existing information more effectively from a point of self-service access, facilitates the capturing and sharing of new information, reduces data overload, and makes certain that current, up-to-date information is readily available. There can be many portals within a single organization for different departments, projects, geographic locations, and so on.
-
Extranets refer to intranets that have multiple levels of access, through various security protections, available to authorized outsiders. An extranet allows organizational partners to exchange information based on a business-to-business (B to B or B2B) architecture. Extranet pages provide business information and application functionality to external partners, including real-time access to important data. This can decrease the costs of partner support activities. Each portal has the ability to be customized and personalized to the needs of individual partners (for example, customers, suppliers and partners in joint ventures).
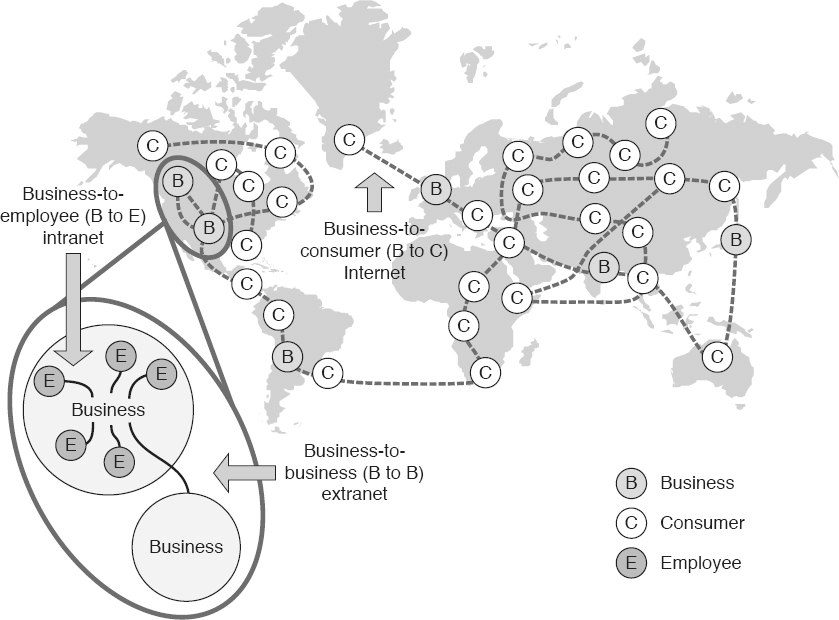
Figure 10.5
Web architecture—example.
Wireless
In today’s environment, many individuals need to take their computer processing power with them as they travel, without being tethered via cabling to a network. People need wireless
access to the Internet, to stored information and data, and so on, as they travel from site to site. For example, a doctor or nurse might use a personal electronic device to access patient records
from wherever that information is needed. Sales people, consultants, law enforcement, students, and many others need to stay in contact while traveling, which can be accomplished through wireless access on their electronic devices. Wireless access is often provided to guests of a company or for use in conference rooms or manufacturing areas where wires might be a problem.
Messaging
Messaging system architectures
are designed to accept messages from, or deliver messages to, other systems. An e-mail system or instant messaging (IM) are examples of a messaging system. In its simplest form, a messaging architecture:
-
Accepts messages from external systems, determines the internal recipients, and routes those messages appropriately
-
Accepts messages from internal sources, determines their destination systems, and routes them internally or externally as required
Collaboration Platforms
According to Wikipedia, “Collaboration platforms
offer a set of software components and software services that enable individuals to find each other and the information they need, and to be able to communicate and work together to achieve common business goals.” A collaboration platform helps individuals and teams work together regardless of how geographically dispersed they are. Examples of key components of a collaboration platform include:
-
Messaging via e-mail, databases, or lists of contacts or customers, and coordinated calendars and scheduling tools
-
Virtual meeting tools, including instant messages, web- based meetings, audio or video conferencing, and desktop sharing
-
Information sharing via shared files and data refreshing, document repositories with search capabilities, and mechanisms for sharing ideas and notes
-
Social computing tools such as blogs, wikis, chat rooms, and social media (for example, Facebook, LinkedIn and so on)