In this chapter, we’ll look at a few classes of programs that you can use to safeguard your privacy while using the Web. Collectively, these technologies are frequently referred to as privacy-protecting technologies.
For each major section in this chapter, we have attempted to introduce the broad program category (blocking ads, crushing cookies, anonymous browsing, and secure email), give a few examples of programs in the category, and then finally show one or two of these programs in action. Because the Internet is a fast-changing place, it’s quite possible that some or all of the programs discussed here will no longer be available by the time this book appears in print. It’s also possible that new programs will be introduced that are not mentioned here. That’s why you should use this chapter as a survey of the kinds of tools that are available for enhancing web privacy, rather than as an actual buyer’s guide.
If you are interested in protecting your privacy from web advertisers—or if you simply want to see fewer advertisements when you browse the Internet—then you will find yourself in something of a quandary. That’s because the companies that are developing web browsers—Microsoft, Netscape, and Opera Software—have all developed business units that make money by showing advertisements to consumers.[115] Browsers have become programs for delivering ads (see Figure 10-1).
Figure 10-1. On today’s Internet, companies that develop web browsers have also created large web sites that are funded by advertising dollars. Browsers have become, in effect, programs for delivering advertisements to consumers.
A web that is filled with advertisements doesn’t pose a problem for many consumers. After all, advertisements are everywhere: they are on our highways, in our newspapers and magazines, on television, and even on so-called “public radio” stations. Why should the Internet be any different?
But as we saw in the previous chapter, the Web is different from other advertising venues. For starters, it’s simply not possible for a company buying a billboard along a busy highway to get a list of the names, addresses, and phone numbers of all the people who glance up to read their advertisement. A company that sells magazine advertisement space can’t correlate the advertisements in five different publications that you’ve responded to, and then sell your name as a “premium customer.” Yet these kinds of invasive practices are possible on the Internet. Fortunately, the design of the Internet also makes it possible to mount a significant defense against the primary privacy-invading tools of advertisers—their cookies—as well as against the advertisements themselves.
To allow browsing from behind a corporate firewall, web browsers often use services called proxy servers . A proxy server is a program that receives a request from a web browser and forwards the request to the remote web server. The proxy then waits for the response from the remote server and, when it is received, sends the request back to the original browser client that made the request. Most proxy servers are located on corporate firewalls. They allow organizations to carefully control the information that passes between the corporate LAN and the rest of the Internet.
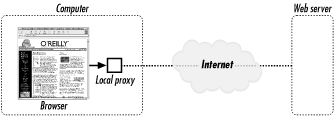
A local HTTP proxy is a program designed to proxy HTTP (web) traffic. It runs on your local computer (see Figure 10-2). The local HTTP proxy’s position between your computer and the rest of the Web gives the proxy the opportunity to monitor what you are doing, preview the pages, and, optionally, modify the content that you see.
Figure 10-2. A local HTTP proxy sits between the browser on your computer and the rest of the Internet. Because of its position, a local proxy can change the way that you view the Web.
A local HTTP proxy can do many things, including:
Record every web page that is viewed.
Selectively grant or block access to specific web sites or pages within those sites.
Introduce new cookies into your browser.
Remove cookies sent from remote web sites to your computer, or vice versa.
Edit the HTML your computer receives, changing the content of web pages.
Modify the images that are downloaded via HTTP before they are displayed on your computer’s screen.
Many of these functions sound quite nefarious and they can be—if somebody else is running the HTTP proxy. But if you have control of the HTTP proxy, then the proxy gives you the ability to control your web browser in ways that were not envisioned (or are simply not allowed) by the browser’s creator.
Tip
One thing that most local HTTP proxies won’t do is intercept encrypted traffic between your web browser and a remote web site. The traffic isn’t intercepted because such an interception would trigger a warning message from your web browser saying that the certificate on the web site did not match the web site’s domain name. This type of interception is precisely what the SSL protocol was designed to prevent, so it’s a good thing SSL prevents it. There are some HTTP proxies that can intercept SSL-encrypted traffic, however. One way to do so is by creating SSL certificates on the fly using a public key/private key combination that is embedded into the HTTP proxy. Another way to do it is by intercepting the TCP/IP traffic as it moves through the computer’s operating system, tapping into the data flow after the data has been decrypted but before it has been given to the application program. This type of interception is easy on Windows for people using Internet Explorer, but it’s difficult on other operating systems.
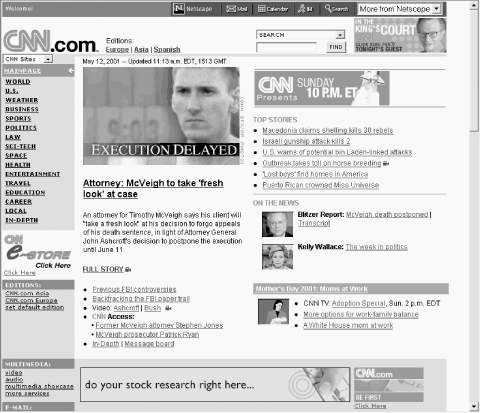
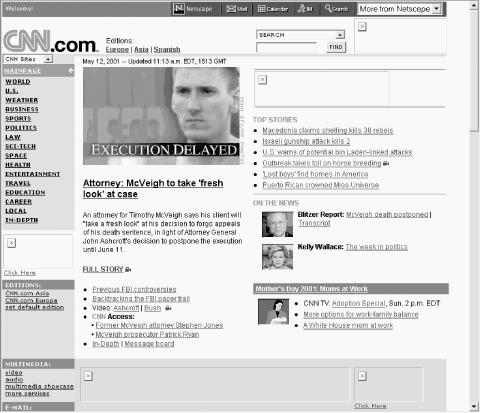
One of the most obvious things to do with a local HTTP proxy is to prevent web advertisements. There are two ways a local proxy can block advertisements. Assuming the proxy can identify an advertisement (a tricky task), the proxy could block the URLs associated with the ads or could edit out the HTML that causes the advertisement to be displayed. These techniques are demonstrated in Figures Figure 10-3, Figure 10-4, and Figure 10-5.
Figure 10-4. The CNN.com home page, as viewed through the Junkbuster HTTP proxy. Junkbuster recognizes the URLs of many advertisements and blocks them from being downloaded. The web browser displays these blocked images as boxes with an “X.”
Figure 10-5. The CNN.com home page, as viewed through the AdSubtract HTTP proxy. AdSubtract edits the HTML as it travels from the web site to the browser and automatically removes the tags that cause some advertisements to be displayed. Notice how the page is automatically reformatted so that more content appears on the screen.
There are many reasons you might want to block an advertisement on a web site:
Advertisements are annoying and distracting.
Advertisements take up space on web pages that is better spent on content.
It takes time to download advertisements. By blocking them, you can make web pages download 5 to 10 seconds faster than they would download with the advertisements. Over a day of browsing, this time savings adds up.
Many advertisements contain built-in tracking technology, such as cookies. By blocking the advertisements, you limit the amount by which you are tracked.
Of course, there are disadvantages as well to blocking advertisements:
Some advertisements contain useful information. By blocking these ads, you might miss out on this information, special offers, and other distractions.
Many web sites are advertiser-supported. When you block advertisements, you deny these web sites needed revenue. If everybody blocked advertisements, these web sites would be forced to close or find another way to support themselves, such as by inserting advertising content directly into their editorial product.
Many programs that block advertisements also crush cookies ; that is, they can selectively allow or deny the transfer of cookies between remote sites and your computer.
One of the big advantages of selective cookie blocking is that you can block cookies from some companies, such as Internet advertising firms, while still allowing cookies from companies that you do business with, such as banks and online brokerage firms.
Ad blockers can perform many other useful functions beyond blocking advertisements and crushing cookies, including:
Removing background music from web pages
Removing background images from web pages
Removing JavaScript, Java, and ActiveX from web pages
Modifying animated GIFs so that they don’t move around
Blocking pop-up windows
Preventing web sites from reprogramming your “Back” button and web browser’s history
Disabling web pages that automatically refresh themselves
Blocking refer links from being transmitted from one web site to another
It is simply astonishing how effective ad blockers can be—and how many advertisements are present on today’s Web. Spend a few minutes browsing on the Web with an ad blocker, and you might discover that upwards of 50 advertisements have been blocked after viewing only a handful of pages.
Many companies have incorporated ad blocker technology into their products. Some of the products are free; others have a small charge. Most of the programs run only on Windows. In some cases, a Windows-based proxy can provide an ad blocking service to other computers on your local area network. Table 10-1 provides a summary of some ad-blocking programs currently available.
Table 10-1. A survey of ad blocking programs
Program | Features | Comments |
|---|---|---|
AdSubtract[a] http://www.adsubtract.com | Ad blocking Cookie managementSophisticated filtering | Windows only. Several different versions (some free) with different features available. |
Internet Junkbuster Proxy http://www.junkbuster.com | Ad blockingCookie management | Free. Windows and a variety of Unix systems. |
Freedom Internet Privacy Suite http://www.freedom.net | Ad blockingCookie managementForm-fillingMany other privacy features | Free. Windows and Linux. Optional subscription service provides for anonymous web browsing and email. |
Norton Internet Security http://www.symantec.com/sabu/nis/nis_pe/ | Ad blockingCookie managementPersonal firewallMany other security features | Windows only. |
WebWasher http://www.webwasher.com | Ad blockingCookie managementSophisticated filtering | Windows only. |
[a] Simson Garfinkel is on the advisory board of AdSubtract’s publisher, InterMute. | ||
[115] Mozilla, the open source browser based on Netscape’s code, has no such profit motive, and contains per-site image filtering that can be used to block advertisements.