CHAPTER 9
Security Assessments
This chapter presents the following topics:
• Security assessment methods
• Security assessment types
The complexity of both defending and attacking information systems is often equally underestimated. If many movies are to be believed, the penetration of systems is as simple as opening up a series of command-line interfaces and typing at warp speed. In just a few seconds, the infamous green “Access Granted” message comes up and the hacker takes a bow. No reconnaissance, probing, or security assessments needed—just skip straight to the treasure chest.
The irony facing the targets of hacking, and the malicious hackers themselves, is the prerequisite need for performing security assessments. Security practitioners must perform security assessments in order to discover and mitigate vulnerabilities—while hackers perform the same assessments in order to discover and attack vulnerabilities. Although movies tend to skip the assessment aspects for plotline acceleration, we cannot overstate the importance of performing security assessments on organizational systems—not to mention that many regulations also include requirements for organizations to perform security assessments.
This chapter will focus on the scenarios and methods surrounding proper security assessments. The point of a security assessment is to ensure that proper safeguards and security controls are in place for organizational assets. Assessments ensure many things, including that systems are patched, applications are not vulnerable, and networks are locked down. Many different approaches and methods fall under that very broad umbrella of “security assessments.” Some methods are best at addressing broad concerns whereas others are very specific in nature.
Security Assessment Methods
Security assessments are broad in both scope and depth. There are many organizational assets to assess plus multiple methods of assessing those assets. We may be assessing data, applications, hosts, internal and perimeter network security, physical security, policies, procedures, training, and, of course, people. Such assessments can be performed on local or cloud-based assets, while being performed by local security experts or outsourced to a security consulting team. Various methods are discussed in this section, including malware sandboxing, memory dumping, runtime debugging, and more.
Malware Sandboxing
Although there is some risk in deliberately grabbing a piece of malware, or what appears to be malware, and putting it “under the microscope,” malware sandboxing is a necessary requirement for rounding off your malware defenses. Despite our various antimalware tools being equipped with powerful signature and heuristic engines for malware remediation, these tools won’t find everything—not even close.
Before you uninstall that antivirus software and flee to the hills in fear, be aware that the point of this admission was not to decry antivirus software but rather to raise awareness that today’s malware resistance requires more than just antivirus software. Malware sandboxing is a necessary complement to our antimalware portfolio, allowing us to isolate real or potential malicious code into a safe and restricted environment for analysis. If you consider that over 300 million new malware threats are created every year, a large chunk of them will not yet be discovered by the mainstream antimalware security vendors. Many of the organizations under our charge—the very targets of such malware—must put on the white coats and discover/mitigate some of the malware themselves. If successful, we may be able to prevent or minimize the damage done by zero-day malware threats (that is, pieces of malware that have yet to be discovered and mitigated by the responsible vendors). Without vendor remediation, we’re on our own.
Organizations may choose to build their own internal malware sandboxing environment or use proven vendor products like Cuckoo Sandbox and Sophos Sandstorm.
Memory Dumping
Ever wonder what purpose was served by the notoriously vague “Blue Screen of Death” occasionally experienced on Windows machines during system crashes? Technically known as a “stop error,” this seemingly useless message often contains a subtle but important line on the bottom that reads “Beginning dump of physical memory.” This indicates that RAM contents are being downloaded to a memory dump file on the hard drive to permit offline crash analysis.
So, what does this have to do with security assessments? Simply take that same concept of analyzing memory dumps, but look for other things—say, cryptographic keys, certificates, usernames, passwords, and hashes. Memory dumps are an example of a security assessment in that they help organizations proactively discover and mitigate memory and application vulnerabilities before they’re exploited by malicious hackers.
Runtime Debugging
If runtime refers to the execution or running phase of an application, then runtime debugging refers to debugging the application during its runtime. Unlike memory dumping, which involves the analysis of software content after it has been dumped from memory to the hard drive, runtime debugging refers to analyzing code while it is actively running in memory. This provides live insight into possible inaccuracies of an application’s syntax while also revealing software vulnerabilities. Table 9-1 shows a comparison of different memory/runtime debugging tools.
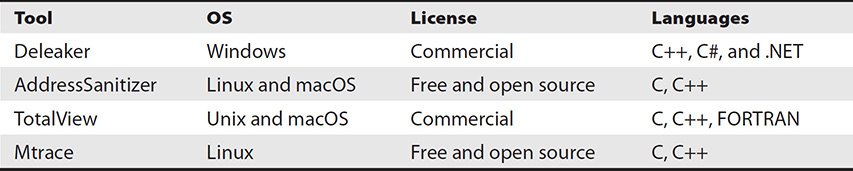
Table 9-1 Memory/Runtime Debugging Tools
Reconnaissance
Most of the time, hackers have to “do their homework” before they can successfully gain access to a target system. Reconnaissance (sometimes known as footprinting) is the first stage of hacking, and it consumes roughly 90 percent of all the time spent on hacking—malicious and ethical varieties included. Reconnaissance is the methodical process of collecting as much information about a target as possible before attempting to hack them. Such data collection will help guide the direction of the hack, possibly reveal vulnerabilities, and determine which tools and techniques will be needed to successfully complete the hack.
Most reconnaissance is passive in nature in that it is performed without direct interaction with the target. This involves gathering intel from various Internet sources, including the target’s website, vendors, competitors, and even job search sites. Active reconnaissance or footprinting requires the hacker to interact with the target through direct communication or visitation. This may be necessary for data collection that couldn’t be performed passively.
Reconnaissance requires hackers to acquire a large amount of target information to successfully complete the hack. Part of the reason for this is to achieve the dual benefit of successful target penetration while remaining invisible. Unlike the morbidly named “suicide hackers,” who will sacrifice their anonymity for the furtherance of the hacking mission, most hackers don’t want to get caught. As a result, proper reconnaissance can take days, weeks, or even months to complete.
Information about customers, employees, products, trade secrets, company plans, and so on, can be found from a variety of data sources. Here are some examples of the sources used in reconnaissance efforts:
• Search engines
• Google hacking
• Web services
• Social networking sites
• Website footprinting
• E-mail footprinting
• Competitive intelligence
• Whois footprinting
• DNS footprinting
• Network footprinting
• Social engineering
Fingerprinting
The high-level information obtained from reconnaissance is important, but it’s only a starting point. Specific details about target systems are also needed to successfully gain access. Fingerprinting will help carry us over the finish line through interactive scanning of networks and devices in order to learn important details like pingable systems, open ports, running services, banner grabbing, operating systems, network shares, accounts, and much more. Without those details in hand, we cannot know which exact vulnerabilities exist for exploitation.
Consider Nmap, which is a port-scanning tool that works for TCP and UDP services. It can test for ICMP acceptance, identify services running on discovered ports, and even produce an educated guess as to the application and operating system being examined. Quickly producing an accurate fingerprint is very important to a potential attacker. If an attacker is looking for vulnerable Linux systems, they don’t want to waste time attempting to exploit Windows or Solaris systems. If an attacker is looking for web servers running IIS 6 or later, then Apache-based web servers are not interesting at the moment.
From a security officer perspective, fingerprinting tools can be a great way to “see” what’s on your network. Scanning your own network will help you identify systems running unnecessary services, systems that do not appear on current inventories (and should not be connected to the network), and so on.
The following are examples of some tools you’ll rely on during your fingerprinting exercises in the field:
• Ping sweepers Angry IP Scanner, Nmap, NetScanTools Pro
• Open ports Nmap, NetScanTools Pro, Hping, SuperScan
• Running services Nmap, NetScanTools Pro
• Banner grabbing Netcraft, ID Serve, Netcat, Telnet, NetScanTools Pro
• Operating systems Nmap, NetScanTools Pro
• Network shares SuperScan, NetScanTools Pro
• User accounts SuperScan, NetScanTools Pro
• Mobile fingerprinters Fing, IP Scanner
Code Review
Code review is essentially proofreading of source code. Code reviews are intended to find programming errors and poor coding practices that can lead to vulnerabilities such as buffer overflows, memory leaks, unhandled exceptions, and so on. Code reviews can be done in various ways, ranging from the informal (one programmer looks over the shoulder of a fellow developer) to the extremely formal (such as a team walkthrough of an entire code base). Code reviews can be performed manually, but tools exist that provide automated code review capabilities. These automated review tools can be used to scan large codebases and identify potential issues or areas where issues may exist. Developers can then focus in on those areas without having to scan the entire codebase manually. Automated scanning followed by manual review is a widely accepted common practice that provides good coverage for far less “cost” than a manual review of the entire codebase.
The key benefit to code reviews is to find and address bugs and vulnerabilities as soon as possible—preferably before the software even enters formal testing. The earlier in the development process a bug can be caught and addressed, the cheaper is it to fix. Consider Microsoft Word—if a bug is caught in development, it is far, far cheaper to correct it there than it is to correct the bug in a released product. Addressing the bug in development may involve a few developers and a few lines of code with comments. Addressing that same bug in a released product involves code revisions, configuration management, regression testing, patch development, patch note development, and so on. As you can see, the sheer amount of effort required to address bugs post-production encourages many organizations to perform code reviews early and often during the development cycle.
Social Engineering
Social engineering is a broad term that describes “human hacking”—or what is sometimes called “no-tech hacking.” Social engineering techniques focus on manipulating or compromising people into revealing confidential information. The attacker seeks to convince people to circumvent or ignore existing security protocols, reveal sensitive data, grant access where none should be given, and so on. For example, someone attempting to access a particular organization’s infrastructure may call the organization’s help desk and impersonate an actual user in an attempt to get the user’s password reset to something the attacker will know.
Social engineering does not always have to involve direct contact or direct interaction. Social engineering can be performed via e-mail—ever gotten an e-mail informing you that your bank account or e-mail account has been compromised and you must log in right away and verify all your credentials? Phishing is social engineering via e-mail. The goal of phishing is to trick the user into either giving away information they shouldn’t (such as login credentials and bank account numbers), clicking links, or running software they shouldn’t. You may also have seen “scareware” ads that pop up, informing you that your system is infected and you need to install and run a specific software package that will “clean up and protect” your system.
Social engineering is a technique that is typically negotiated for use in a vulnerability or penetration test. Many penetration testers make heavy use of social engineering techniques because bypassing the human component of a security system is easier than bypassing the technology. Imagine how many of your users would give their login and password to someone from the “help desk” or “IT” when asked? It only takes a single person to make a bad decision and allow an attacker to bypass tens of thousands of dollars in security technology.
Human-Based Social Engineering
Human-based social engineering is a form of social engineering that requires more direct interaction with people. This section describes the various human-based social engineering techniques utilized by attackers.
Dumpster Diving Dumpster diving involves attackers digging through a victim’s trash to obtain confidential information. Valuable information can be found from discarded bills or other financial documents, calendars, organizational charts, printed e-mails, flash media, diagrams, contacts, and more.
Countermeasures include implementing a clean desk policy to ensure all confidential data materials are removed from the desks and are locked inside of them. Plus, adequate paper-shredding practices should be implemented through cross-cutting or preferably micro-cutting paper shredders.
Eavesdropping Eavesdropping involves the unauthorized interception of communications between other parties. The intercepted materials can be in written, auditory, or video form, and obtained over the phone, through e-mail, instant messaging, SMS, or in person.
Eavesdropping mitigations include strong physical security controls, encrypted communication lines, paper shredding, and regular security awareness training.
Impersonation Impersonation is the practice of pretending to be someone else. This is the oldest, most common, and most powerful form of social engineering because it quickly establishes trust between attacker and target. Trust is the key to convincing people to willingly provide attackers with confidential information. Typically, the attacker will impersonate a legitimate individual such as a family member, friend, colleague, end user, important user, help desk, management, or even a celebrity. The best countermeasure for impersonation is security awareness training because it’ll help victims spot and deflect impersonation attempts.
Piggybacking Piggybacking takes place when unauthorized individuals trick an authorized individual into allowing them access into a restricted area. This is necessary due to the unauthorized user having no other means of traversing such checkpoints on their own. Piggybacking generally involves the consent of the authorized individual to permit access into the area due to the bogus excuse of a forgotten ID badge. Strong physical security controls like security guards, ID badges, and mantrap doors can reduce piggybacking attacks.
Tailgating To the untrained eye, tailgating and piggybacking are the same thing. The key difference being piggybacking occurs with the victim’s consent, whereas tailgating does not. The attacker may pull this off by wearing a fake badge so that nobody pays any mind to the apparent stranger.
Reverse Social Engineering Most social engineering attacks follow the same pattern—the attacker initiates contact with a victim to extract confidential information. Although “going first” provides the attacker with some advantages, the boldness of it might tip off the victim. As a workaround, a more covert baiting technique can be employed.
Reverse social engineering occurs when attackers trick victims into initiating contact with the attackers. The victim is less likely to suspect a scam because they initiated the dialogue. To pull this off, the attacker creates a situation in which the victim is likely to contact the attacker for help. For example, the attacker may put a business card on the victim’s keyboard offering computer repair services. The attacker then breaks the victim’s computer in some way so that the victim will call the phone number requesting assistance with the computer. The subtle nature of this ploy accelerates the victim’s trust with the attacker. Physical security and security awareness training are important to offset this threat.
Shoulder Surfing Shoulder surfing is the act of observing someone inputting their credentials into a system. The attacker’s goal is to learn all—or a portion of—the input provided by victims in order to illegally access their account. Even if just a few characters of the password are known, the attacker could plug the known portion into a password cracker to potentially solve the remainder. This is known as a rule-based password attack. Camera-equipped smartphones can zoom in and take pictures or videos of passwords and PIN numbers as they’re being typed. Skimmers are also frequently used to capture inputted credentials at gas stations, banks, and wherever else credit card/debit transactions are performed.
Users need to be aware of their surroundings during login scenarios. To mitigate shoulder surfing, users can use privacy screens, keystroke interference software, and keyboard privacy shields that impair the visibility of the keys. They should also cover PIN number keypads as they’re typing. Switching to biometrics or token-based authentication can also minimize the shoulder surfing threat.
Vishing Often referred to as the voice equivalent of phishing, vishing is the process of calling people on the phone while pretending to be a trusted entity such as a friend, colleague, family member, customer service, and so on. Like with phishing, the attacker’s goal is to extract confidential information from the victim. Since victims have become fairly keen on e-mail-based phishing techniques, attackers are increasingly reliant on the more personal touch provided by a friendly and professional voice on the phone. This leads to more trust by the victim. Countermeasures include the following:
• Using caller ID
• Using screening services
• Letting phone calls go to voice mail
• Sharing your phone number with a limited amount of people
• Limiting the information you provide over the phone
Computer-Based Social Engineering
Computer-based social engineering involves attackers socially engineering their targets through computers. This provides a few benefits including the ability to reach the target from afar, while also improving the attacker’s ability to shield their own identity. The following section goes over several examples of computer-based social engineering tactics.
Phishing Phishing is social engineering via e-mail and one of the original Internet attack vectors. Typically, the goal of phishing is to use e-mail to trick victims into revealing confidential account and financial information through malicious links, filling out website forms, or running software they shouldn’t.
The e-mail may suggest that the user’s eBay account has been suspended due to inactivity, malicious activity, or access by an unauthorized device. Then to re-enable the account, the user is advised to click a friendly looking link labeled www.ebay.com, visit a mirrored site that looks like eBay, and then fill out a form chock-full of sensitive information questions.
Phishing can be broken down into multiple varieties, including the following:
• Spear phishing Attackers target a specific individual as opposed to the random individuals targeted by regular phishing.
• Whaling Attackers target important individuals such as executives, politicians, or celebrities.
• Pharming Attackers use phishing e-mails to redirect victims to hacker websites.
Using anti-phishing tools like Netcraft, Microsoft SmartScreen filter, and PhishTank is a strong defense. In addition, awareness of the following phishing signs is also advised:
• Sender’s e-mail address is in your address book.
• Sender’s e-mail address appears auto-generated.
• Sender’s domain name doesn’t match the stated organization.
• Request is urgent.
• Poor grammar.
• Attachments.
• Hyperlinks.
Spam Spam is an electronic form of unsolicited message that arrives through e-mail. Over 90 percent of the world’s e-mails sent every day is spam. Spam exists to advertise products or make unsubstantiated claims, while preying on the gullibility of inexperienced computer users. Although some spam is harmless, other spam messages may contain malicious HTML code, attachments, links, and malware. Even though most people can spot spam a mile away, it is so easily and cheaply generated that spammers can turn a profit on just a minority of victims. You can expect this to continue indefinitely.
Spam countermeasures include user awareness training, anti-spam filters, using e-mail addresses that are difficult to guess by spam generators, and keeping your e-mail address private.
Pop-Ups Pop-ups are website windows that suddenly “pop up” to offer the user a prize or request log in to a website. Although these are often harmless, they may be a sign of adware, spyware, or malicious code on the website. As a result, these should be blocked by a pop-up blocker, or avoided altogether.
Hoax Letters Hoax letters are e-mails that may falsely claim that a particular piece of malware is in circulation and therefore some kind of action must be taken. The trouble with this is not the false advertisement but rather the cure—“download this particular antivirus software to protect yourself from the malware.” Training users on the signs of hoax e-mails, blocking them, and disregarding them are usually suitable mitigations. You can also look up the hoax e-mails on the Internet to see if they have been verified as false.
Chain Letters Unlike hoax letters, chain letters generally aren’t preaching doom and gloom—rather they make requests about forwarding the message to a certain number of users so that donations are made or awareness is raised regarding a supposed cause. Even though most of these chain letters are based on false pretenses, they create more of a privacy, distraction, or inbox space issue than being outright dangerous. The same defensive approach we take with hoax letters will apply here as well.
Spim Spim is a spinoff of spam that sends unsolicited messages through instant messenger clients as opposed to e-mail. Although automated, these messages often appear human-generated to improve their credibility. Typically, the messages will start off with a story such as being new in town looking to network, or advertise adult materials or other products. The goal is to acquire confidential information, spread malware, or take over the victim’s machine—just like with spam or phishing attacks. Security training will educate users on how to spot, block, or disregard spim messages.
Mobile-Based Social Engineering
Given the billions of mobile devices permeating the globe, it only makes sense for attackers to add mobile-based social engineering tactics to their repertoire. With people relying on their smartphones and tablets to download applications from app stores—while also spending many hours each week interacting with family members, friends, and colleagues through social media applications—hackers are using these tools to launch social engineering attacks against the mobile device owners. This section will cover the different mobile-based social engineering techniques employed by hackers.
Malicious Mobile Apps With millions of apps on the Google and Apple app stores, it’s inevitable that some apps exist for the sole purpose of infecting users with malware while harvesting their credentials. To the outsider, the app appears like any other. It’ll be usable, well-reviewed, supported, and probably even enjoyable. Limiting or preventing app downloads as well as carefully choosing apps from trusted sources with verifiable code signatures are the best mitigations to deal with this threat.
Repackaged Mobile Apps Some attackers will repackage legitimate apps with malware and then upload them again to the app stores in order to attract downloads and spread malware. If you ever do an app search and notice multiple versions of the same exact app, beware. The countermeasures to this are similar to those made earlier regarding malicious mobile apps.
Smishing Smishing is similar to phishing and spimming; however, it involves sending unsolicited SMS messages to targets. Attackers are increasingly relying on this tactic since most people are more responsive to SMS messages than e-mails and voice mails. Its goals are similar to that of other phishing-related attacks; therefore, user awareness training requirements should be observed.
Pivoting
Pivoting is the process of compromising a host in order to use that host to compromise other hosts on the network. This is necessary because the other hosts are likely inaccessible until the first host is compromised. The first host is essentially a base that the hacker sets up shop on in order to traverse the network from an inside trusted position. Although Metasploit is the most well-known tool for pivoting attacks, Netcat (Ncat), proxy servers, SSH port forwarding, Burp Suite, and even various backdoor Trojan horses can pull this off.
Mitigations to pivoting include configuring firewall rules, IDS/IPS rules, patching, implementing the principle of least privilege, limiting account rights, and locking down ports.
Open Source Intelligence
Open source intelligence (OSINT) refers to the collection of valuable information from public sources. As described earlier in the reconnaissance section, attackers and penetration testers will typically “case the establishment” by frequenting various Internet and non-Internet sources for information about targets. The following sections cover a few different open source intelligence locations.
Social Media
Opinions about social media typically range from it being a great tool for networking, customer engagement, promoting products, and recruitment, to it being a time-wasting distraction with a plethora of privacy issues. To the more trained eye, social media can be very dangerous to businesses and individuals. Several years ago, the U.S. government issued a warning about the severe risks that social media presents at the government and organizational levels, and the need for a collective response to the challenges. Some of these challenges include:
• Lack of social media policies Without a social media policy, organizations have little to no enforcement over how their staff members use social media products like Facebook, Twitter, LinkedIn, Snapchat, Instagram, and YouTube. Not to mention, users are less likely to understand proper usage of social media with respect to their employer—which puts the organization at greater risk. Social media policies not only provide for these directives but they also may include best practices and guidance.
• Mobile apps (privacy) Ever wonder why there isn’t much privacy in social media? Because social media and privacy literally have opposite meanings. Social media is about sharing information, whereas privacy is about not sharing information. In a strong sense, there is no such thing as social media privacy. More importantly, social media mobile apps typically collect an egregious amount of user information, including texts, call logs, camera access, microphone access, contacts, location, photos, and more.
• Data leakage Social media is all about publishing and consuming content in a social setting. People often lose their inhibitions in cyberspace; therefore, they may feel free to share information more aggressively—possibly confidential business information—with friends, family, colleagues (and strangers). The trouble arises when information reaches the wrong people due to the transitive nature of information flow on social media platforms (as in points A and C connect through B). Not to mention, not all “friends” on social media platforms are who they claim to be. Whatever the cause, when information gets into the wrong hands, it has “leaked.”
• Profile squatting/evil twin attacks Profile squatting or evil twin attacks occur when attackers create a fake social media profile that impersonates another individual. It is effortless to create a profile with a real person’s name, upload that individual’s picture into the profile, and populate the profile with that individual’s information. This allows attackers to befriend family members, colleagues, and friends in order to acquire confidential information from them—or worse.
• Malware Social media platforms are rife with pictures, links, friend requests, and—we’ve saved the best for last—irresistible video content. Ever wonder where the videos come from? Or why there are so many videos of the hilarious or shocking variety circulating the feeds? Some of it is used to infect people with malware. One of the easiest ways to give people malware is by first giving them what they want. Videos, pictures, and links can contain malicious software, or redirect you to a place that contains the malware.
• Social engineering As described previously with evil twin and malware attacks, social engineering is incredibly easy to perform on social media due to the simplicity of impersonating others and sharing irresistible content.
• Lack of privacy In addition to the preceding comments on mobile apps, social media platforms have a combination of complex and frequently changing privacy controls. Social media companies aren’t going to make as much money if they make it easy for customers to disable all data collection and ad placements. The complexity and changing of privacy controls are vital to the social media company’s survival.
Whois
Whois is a global database of registered domain names and all related registration and ownership details of those domains. This information includes the following:
• Domain details
• Domain registration and expiration dates
• DNS servers
• Network ID range
• Registrant contact name, e-mail, phone number, address
• Administrative contact name, e-mail, phone number, address
• Technical contact name, e-mail, phone number, address
• DNSSEC signature status
• Autonomous system (AS) router information
When website owners register a domain name such as www.microsoft.com, by default the information will be published online in a public database made available by several regional Internet registries (RIR), including the following:
• American Registry for Internet Numbers (ARIN) Covers the U.S., Canada, parts of the Caribbean region, and Antarctica
• African Network Information Center (AFRINIC) Covers Africa
• Asia-Pacific Network Information Centre (APNIC) Covers Asia, Australia, New Zealand, and other adjacent countries
• Latin America and Caribbean Network Information Centre (LACNIC) Covers Latin America and other parts of the Caribbean
• Réseaux IP Européens Network Coordination Centre (RIPE NCC) Covers Europe, Russia, West Asia, and Central Asia
The earlier section on reconnaissance described how hackers, pen testers, and security consultants will use a variety of Internet sources to profile an organization for information and vulnerabilities. Whois is one of the first consulted resources due to the value and accessibility of its information. Administrative and technical contact details like names, e-mail addresses, phone numbers, and addresses can provide footprinters with social engineering opportunities. Plus, the registered IP address range provides pingable and port-scanning targets for vulnerability assessments.
SmartWhois is a popular downloadable Whois tool that aggregates all Whois information for a particular domain. Also consider web-based tools like whois.icann.org and ww.whois.net.
Arguments exist for the preservation of a public Whois database, although some suggest it should be improved or eradicated entirely. Those in favor of it point to the benefits to law enforcement, who need domain contact details to conduct Internet crime investigations. Others believe going public with information helps legitimize an organization. Yet, others suggest that the public information gives spammers and other social engineers a buffet of information from which to exploit organizations.
Routing Tables
Before we get into routing tables, we’ll provide a quick primer on routers. Routers are critical infrastructure devices that forward information from one network to another. This common process of connecting networks to networks is known as internetworking—which is where the “Internet” term originated.
Since most source and destination systems are not located on the same network, routers are used to bridge the gap. Granted, a Layer 3 Ethernet switch can perform basic routing functions, but it is not a complete substitute for a router.
Whether you’re traveling to work or routing traffic across an internetwork, many paths to the destination can exist. It’s the job of routers to know which network destinations exist, which routing paths (routes) exist to the destinations, and which routes are the best choice at any given moment. Routers make decisions based on the information stored in a routing table. Routing tables store a combination of destinations and the routes to those destinations for a given router. Routing tables are built and managed by two different methods:
• Static routing This occurs when a person manually programs the routes and destinations into a routing table. Its advantages include increased control over traffic, security improvements, and reduction of traffic. The disadvantages include increased workload on administrators and the increased time it takes for a network to adapt to a downed router. We generally use static routing for smaller internetworks.
• Dynamic routing This involves routers using dynamic routing protocols to automatically broadcast routing table updates to other routers. The automation of this reduces an administrator’s workload, while also improving reaction times for downed routers. The downside is it decreases security (due to hackers potentially hijacking the routing table updates) and increases traffic loads. We generally use dynamic routing for larger internetworks.
Several protocols are used to communicate routing table updates between routers:
• Routing Information Protocol (RIP)
• Open Shortest Path First (OSPF)
• Border Gateway Protocol (BGP)
• Exterior Gateway Protocol (EGP)
• Interior Gateway Routing Protocol (IGRP)
• Enhanced Interior Gateway Routing Protocol (EIGRP)
• Intermediate System–to–Intermediate System (IS-IS)
Although dynamic routing protocols make life easier for administrators, their chatty nature exposes the organization to some risk. Hackers may be looking to intercept routing table update traffic—or inject malicious update traffic of their own—to compromise other routing tables and redirect traffic to a destination of the hacker’s choosing. To mitigate these risks, routers can employ authentication methods to ensure communications come from trusted routers, and that the information itself maintains integrity.
Although plaintext authentication results in passing credentials between routers, this can easily be intercepted by any packet sniffer. A better choice is to use MD5 authentication or key chains because these will ensure passwords don’t traverse the network in cleartext.
DNS Records
DNS records are vital to the functionality of a network. They provide important system identifiers to help clients translate system hostnames to IP addresses, reverse IP addresses to hostnames, and to help clients locate servers that provide special services. Not surprisingly, malicious and ethical hackers will attempt to harvest DNS records early on in their vulnerability assessments in order to progress to the more important later stages of vulnerability assessments.
Several types of DNS records are important to understand. Table 9-2 shows the most common DNS record types.
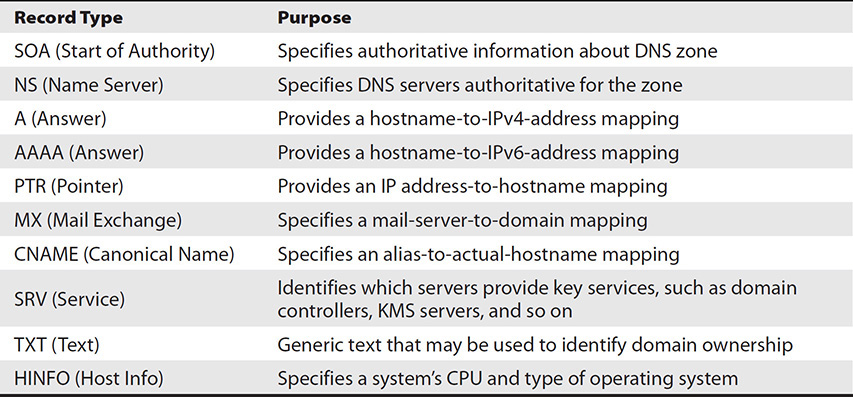
Table 9-2 DNS Record Types
Since DNS records are stored in zone files located on DNS servers, hackers and pen testers will use a variety of DNS footprinting and enumeration techniques to acquire them. Based on the security posture of the DNS servers, we may be able to acquire a lot of records or—more likely—very few. Learning IP addresses and hostnames can be achieved in a few different ways. Assuming we learned the target’s IP address range from a Whois lookup, we may be able to use a ping sweeping tool like Angry IP Scanner to not only determine live pingable systems but to also perform DNS reverse lookups on the IP addresses. As stated previously, reverse lookups resolve IP addresses to names.
Another option is to use Nmap to perform a list scan, which, like Angry IP Scanner, will perform a DNS reverse lookup on a range of hosts. The biggest challenge is performing these scans without being detected by the IDS/IPS appliances on the network.
A third and less likely option is to request a DNS zone transfer of all DNS records from the target’s DNS server. Keep in mind that any administrator worth their salt will configure DNS servers to only allow DNS zone transfers to other trusted DNS servers. In other words, such a zone transfer should fail for us. Although it’s unlikely to work, it’s still worth trying.
A popular tool for performing zone transfers is nslookup. A sample nslookup process is shown next:
1. Type nslookup at the Windows command prompt.
2. Type server dns1.example.com to connect to an example.com DNS server.
3. Type set type=any to indicate that you are interested in all available records.
4. Type ls -d example.com to attempt to transfer all available records from the example.com zone.
Another option for enumerating the DNS records located in zone files is to use a web-based DNS lookup tool such as DNSstuff.com or the tools from www.ultratools.com. Web-based tools are often easier to use for organizing the information better.
Search Engines
Although it may seem a bit cliché, using a search engine like Google, Bing, Yahoo, Ask.com, and even DuckDuckGo is a great way to extract information about a target. Organizations are often unaware of the valuable information that exists about them on the Internet, including technology platforms, organizational details, employee details, external and internal login portals, error messages, and even the occasional password file.
Although most search engines have advanced search operators to help filter search results based on keywords in website titles, addresses, domain names, file types, and more, Google is unquestionably the best search engine to use. Google’s advanced operators are so richly designed that entire books, and web pages, are dedicated to the art and science of “Google hacking,” which is used to create the most advanced search queries possible on the Internet. These queries will help you find virtually anything about a target that is published online. Table 9-3 provides several Google hacking examples.
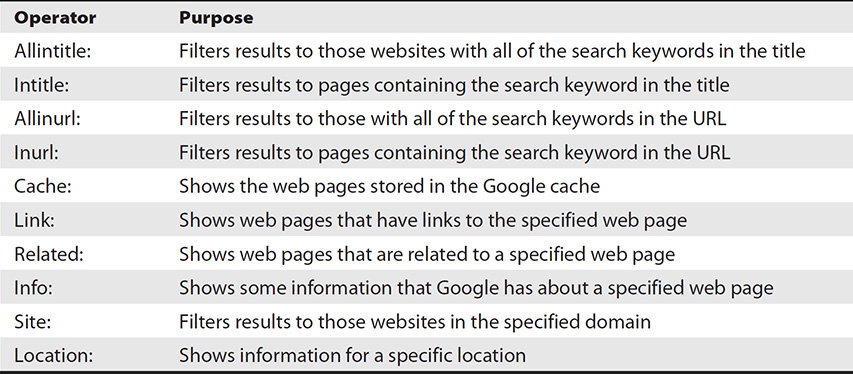
Table 9-3 Google Hacking Techniques
Additional search engines like Shodan and Censys are helpful for vulnerability scans in that they target devices like servers, routers, IoT devices, and so on.
Security Assessment Types
This chapter is about methods of security assessments and types of security assessments. What’s the difference? In the context of this book, think of it as “what” versus “when.” Hitting a homerun is what we did; while playing baseball is when we did it. Methods describe the actual technical procedures demonstrated in the security assessment, whereas types describe the scenario in which the methods were employed. If memory dumping is what we did, a penetration test represents when we did the memory dump. The upcoming sections discuss various types of security assessments.
Penetration Testing
A penetration test (or pen test) simulates an attack from a malicious outsider—probing your network and systems for a way in (often any way in). Pen tests are often the most aggressive form of security testing and can take on many forms, depending on what is considered “in” or “out” of scope. For example, some pen tests simply seek to find a way into the network—any way in. This can range from an attack across network links, to having a tester physically break in to the building, to social engineering and anything in between. Other pen tests are limited—only attacks across network links are allowed, with no physical attacks.
Regardless of the scope and allowed methods, the goal of a penetration test is the same—to determine if an attacker can bypass your security and access your systems. Unlike a vulnerability assessment, which typically just catalogs vulnerabilities, a penetration test will attempt to exploit vulnerabilities to see how much access that vulnerability allows. Penetration tests are very useful in that they can do the following:
• Show relationships between a series of “low-risk” items that can be sequentially exploited to gain access (making them a “high-risk” item in the aggregate).
• Be used to test the training of employees, the effectiveness of your security measures, and the ability of your staff to detect and respond to potential attackers.
• Often identify and test vulnerabilities that are difficult or even impossible to detect with traditional scanning tools.
Well-known security testing methodologies exist from various organizations to help standardize our approach to penetration testing or vulnerability assessments. Take a look at the Open Web Application Security Project (OWASP), the Open Source Security Testing Methodology Manual (OSSTMM), the Information Systems Security Assessment Framework (ISSAF), and EC-Council’s Licensed Penetration Tester (LPT) methodology for process guidance.
Black Box Testing
Black box testing is a software-testing technique that basically consists of finding implementation bugs using malformed/semi-malformed data injection in an automated fashion. Black box techniques test the functionality of the software, usually from an external or user perspective. Testers using black box techniques typically have no knowledge of the internal workings of the software they are testing. They treat the entire software package as a “black box”—they enter input and look at the output. They have no visibility into how the data is processed inside the application, only the output that comes back to them. Tests cases for black box testing are typically constructed around intended functionality (what the software is supposed to do) and focus on providing both valid and invalid inputs.
Black box software testing techniques are very useful for examining any web-based application. Web-based applications are typically subjected to a barrage of valid/invalid/malformed/malicious input from the moment they are exposed to public traffic. By performing black box testing before an application is released, developers can hopefully find and correct errors in the development or testing stages.
Black box testing can also be applied to networks or systems. Pen tests and vulnerability assessments are often performed from a purely external perspective, where the testers have no inside knowledge of the network or systems they are examining.
White Box Testing
White box testing is almost the polar opposite of black box testing. Sometimes called “clear box testing,” white box techniques test the internal structures and processing within an application for bugs, vulnerabilities, and so on. A white box tester will have detailed knowledge of the application they are examining—they’ll develop test cases designed to exercise each path, decision tree, input field, and processing routine of the application.
White box testing is often used to test paths within an application (if X, then go do this; if Y, then go do that), data flows, decision trees, and so on. Sometimes the term white box testing is applied to network assessments where the tester will have detailed knowledge of the network, including but not limited to IP addresses, network routes, and valid user credentials. In those cases, the tester is typically referred to as a “white hat.”
Gray Box Testing
In a gray box test, the testers will typically have some knowledge of the software, network, or systems they are testing. Gray box testing can be very efficient and effective because testers can often quickly eliminate entire testing paths, test cases, and toolsets because they have some inside knowledge and can rule out things that simply won’t work and are not worth trying.
Vulnerability Assessment
Vulnerability assessments are a series of tests and scans performed on organizational resources to discover vulnerabilities. A vulnerability assessment is designed to answer the following questions: Do we have issues? How many? How bad are they? A well-performed vulnerability assessment should identify and evaluate the vulnerabilities in the system, network, application, or process being examined.
Although many people think “network” or “application” when the term vulnerability assessment is mentioned, in reality vulnerability assessments can and are performed on anything from public water supplies, to transportation systems, to production processes. Although there are many different kinds of vulnerability assessments, shown next are some processes common to a vulnerability assessment:
• Defining and classifying the network, system(s), or processes What will be examined, what value does it have, and what capabilities does it have?
• Valuation How important is this system as compared to that system? How important is something to the organization? And so on.
• Threat identification What are the potential threats, how bad are they, and how serious would it be if someone were able to exploit those vulnerabilities?
• Mitigation strategies How does one reduce the risk from the discovered vulnerabilities and how can the network/system/process be better protected?
A vulnerability assessment is good for evaluating the security posture of your network, critical systems, and so on. Being able to identify the threats and quantify their impact can help determine what mitigation/protection strategies to pursue. Vulnerability assessments can help determine where to spend security budgets, where to devote manpower, and can even be used to help obtain additional resources. Often the first step in securing your network or systems is finding out how badly it is broken.
Self-Assessment
Although it’s important for organizations to have third parties conduct the vulnerability assessments to prevent bias, there’s no law that says organizations cannot “also” perform vulnerability or penetration assessments on themselves. In fact, once a penetration tester completes their pen test, they will often advise the client to perform security assessments on themselves as a form of risk mitigation.
Tabletop Exercises
Part of any self-assessment is the initial tabletop exercise, which brings together security-minded people and other stakeholders to the table to discuss their roles and ideas for a particular situation such as a security assessment. They may go over things like preferred tools, techniques, targets, and the time and place of assessments.
Internal and External Audits
Vulnerability assessments and penetration tests focus on the negatives in that they either look for vulnerabilities or look for ways to exploit vulnerabilities. Security audits focus more on the positives in that they are looking to measure the efficacy of security controls for systems, facilities, personnel and processes. In other words, are the security controls for these assets compliant with a formal set of requirements set forth by a standard such as SAS 70 (replaced with SSAE), PCI DSS, GLBA, ISO 27000 series, or FISMA?
Security audits tend to look for the following:
• Policy weaknesses
• Physical security gaps
• Disaster recovery plans
• Business continuity plans
• Access control mechanisms
As with other security assessment methods, a combination of external audits to eliminate bias—and internal audits to ensure the audit complies with internal security policy requirements—will provide organizations with a strong and balanced approach to determining the strength of their security controls.
Color-Team Exercises
Color-team exercises turn security assessments into the most effective demonstration of an organization’s security strengths and weaknesses—an actual competition or game between the “good guys” and the “bad guys.” The offensive bad guys simulate attacks against the network, whereas the defensive good guys respond to the attack with analysis while measuring the efficacy of security controls. To be clear, all participants are hired security professionals working toward a common goal. The differences are denoted by the roles of these separate teams, as detailed in the next section.
Red Team
The red team is made up of offensive penetration testers or security experts who are tasked with simulating attacks against organizational systems. Footprinting the target as well as scanning and gaining access to systems are all fair game. They depict black hat hackers by starting off with little to no knowledge about the target—nor are they given much access. They have to start from scratch, which is akin to black box testing.
Blue Team
The blue team is made up of defensive penetration testers or security experts who respond to the red team’s attacks. Their job is to anticipate and observe red team attacks, measure the effect the attacks have on the systems, and determine any gaps in security controls that were exploited by the red team. They will look at logs, reports, packet-sniffing captures, and, if available, powerful security information event management (SIEM) tools that can correlate security events from various angles.
White Team
Think of the white team as the referees, because this team’s job is to oversee the red team’s attacks and blue team’s defensive methods, successes, and failures. They make sure that both sides are following the rules.
Chapter Review
This chapter is the first of two chapters that address enterprise security operations in the context of conducting security assessments using the appropriate methods. Security assessments are vital because if we don’t test an organization’s security posture, we cannot determine the organization’s readiness to withstand attacks from malicious hackers. We cannot turn weaknesses into strengths if we haven’t determined the weaknesses.
We began with the first of many security assessment methods: malware sandboxing. It’s important for organizations to isolate and discover malware themselves rather than relying on third parties to do it all for them. Next, we talked about memory dumping and runtime debugging. These topics make clear the importance of analyzing archived and live code to check for vulnerabilities that can be exploited by attackers. We also discussed reconnaissance for high-level information gathering, and fingerprinting for low-level system-specific data collecting.
Code reviews are important for discovering and correcting flaws with software before they are committed into the finished product. We provided extensive coverage of social engineering due to human beings being the weakest link in security. Pivoting was described as a form of transitive attack in which an attacker compromises one system in order to daisy-chain from that system to another more important target. We next discussed open source intelligence topics like social media. Social media is a treasure trove for attackers, given the value and accessibility of information.
Whois lookups are also easy and accessible for attackers to determine important domain information about an organization. We discussed routing tables and how they provide a virtual map of the network for an attacker’s benefit. Coverage of DNS records was also provided due to their importance in establishing a list of specific targets for hackers to compromise. We wrapped this section up with coverage on search engines and how we can utilize complex search queries to fine-tune the results provided by target websites.
The last half of the chapter focused on security assessment types, which can be broken into two camps—penetration testing and vulnerability assessments. Penetration testing is the practice of simulating hacker attacks on targets to help them understand their weaknesses and improve their security. We touched on multiple types of penetration tests, including black box, white box, and gray box. Black box tests start with the attacker knowing nothing about the target, gray box tests provide the attacker with some knowledge of the target, and white box tests provide the attacker with complete knowledge of the target.
Vulnerability assessments differ by only discovering vulnerabilities, not actually attacking them. Although most vulnerability assessments are conducted by third parties, organizations should complement those third-party assessments with self-assessments. Tabletop exercises help to brainstorm the ideas of an eventual assessment. Internal and external audits help determine the strengths and weaknesses of security controls for an organization. Finally, we talked about color-team exercises, which implement a combination of offensive and defensive teams for a 360-degree approach to security assessments. The red team attacks the network, the blue team defends the network, and the white team referees both sides.
The next chapter focuses on the specific tools used to perform different methods and types of security assessments. These tools are delineated based on network tool type, host tool type, and physical security tool.
Quick Tips
The following tips should serve as a brief review of the topics covered in more detail throughout the chapter.
Security Assessment Methods
• Malware sandboxing is the practice of isolating real or potential malicious code into a safe and restricted environment for analysis.
• Memory dumping helps organizations proactively discover and mitigate memory and application vulnerabilities by dumping software to the hard drive for offline analysis.
• Runtime debugging allows us to analyze code while it is actively running in memory.
• Reconnaissance is the methodical process of collecting as much information about a target as possible before attempting to hack it.
• Fingerprinting is the process of determining specific details about a system, including port numbers, services, operating systems, vulnerabilities, and accounts.
• Code review is the proofreading of source code to discover and mitigate software vulnerabilities before they make it into the finished product.
• Social engineering focuses on manipulating or compromising people into revealing confidential information.
• Dumpster diving involves digging through people’s trash to find confidential information.
• Eavesdropping entails the unauthorized interception of communications between other parties.
• Impersonation occurs when people pretend to be someone else.
• Piggybacking takes place when unauthorized individuals trick an authorized individual into consenting to give them access into a restricted area.
• Tailgating takes place when unauthorized individuals trick an authorized individual into providing access into a restricted area without their consent.
• Reverse social engineering tricks victims into first initiating dialogue with the attacker.
• Shoulder surfing involves observing someone entering in credentials.
• Vishing is the process of calling people on the phone while pretending to be a trusted entity.
• Phishing uses e-mail to trick victims into revealing confidential account and financial information through malicious links, filling out website forms, or running software they shouldn’t.
• Spear phishing targets a specific individual as opposed to the random individuals targeted by regular phishing attacks.
• Whaling targets important individuals like executives, politicians, or celebrities.
• Pharming uses phishing e-mails to redirect victims to hacker websites.
• Spam is an electronic form of unsolicited message that arrives through e-mail.
• Pop-ups are website windows that suddenly “pop up” to offer the user a prize or request logging in to a website.
• Hoax letters are e-mails that may falsely claim that a particular piece of malware is in circulation; therefore, some kind of action must be taken.
• Chain letters make requests about forwarding a message to a certain number of users so that donations are made or awareness is raised regarding a supposed cause.
• Spim is a spinoff of spam that sends unsolicited messages through instant messaging clients as opposed to e-mail.
• Malicious mobile apps appear friendly but have malicious intentions on app stores.
• Repackaged mobile apps are normal apps that are repackaged as malware and then upload again to an app store.
• Smishing involves sending unsolicited SMS messages to targets.
• Pivoting is the process of compromising a host in order to use that host to compromise other hosts on the network.
• Open source intelligence (OSINT) refers to the collection of valuable information from public sources.
• Social media is a frequent target for information due to its value, accessibility, and the inherent social engineering opportunities uniquely afforded to it.
• Whois is a global database of registered domain names and all related registration and ownership details of those domains.
• Routing tables are records on a router that contain route and network destination information.
• DNS records provide important system identifiers to help clients translate system hostnames to IP addresses as well as reverse IP addresses to hostnames, and to help clients locate servers that provide special services.
• Search engines provide easy access to information about a target.
Security Assessment Types
• Penetration testing is the practice of simulating attacks on organizational targets in order to prepare organizations for malicious hackers.
• Black box testing simulates black hat hackers by starting off penetration tests without prior knowledge of the organizational network.
• White box testing simulates a malicious administrator who has complete knowledge of the network.
• Gray box testing simulates a malicious non-administrator who has partial knowledge of the network.
• Vulnerability assessments employ various techniques to discover vulnerabilities but do not exploit them.
• Self-assessments are in-house vulnerability assessments conducted by local staff.
• Tabletop exercises are brainstorming sessions conducted by security professionals and other stakeholders to discuss an upcoming security assessment.
• Internal and external audits involve third-party and local security staff to audit the strengths and weaknesses of security controls.
• Color-team exercises pit offensive versus defensive penetration testers to ensure a complete security posture is assessed.
• Red team testers simulate malicious hacking attacks.
• Blue team testers respond to the red team attacks with analysis techniques.
• White team testers referee the red and blue teams.
Questions
The following questions will help you measure your understanding of the material presented in this chapter. Read all the choices carefully because there might be more than one correct answer. Choose all correct answers for each question.
1. A port-scanning tool like Nmap looks for which types of ports? (Choose all that apply.)
A. Only closed ports
B. Only open ports
C. Only filtered ports
D. All of the above
2. Which protocols do port scanners most commonly scan?
A. ICMP and SNMP
B. TCP and SNMP
C. UDP and TCP
D. UDP and RIP
3. Which of the following is performed by organizations to isolate and discover new forms of malware?
A. Malware dumping
B. Malware debugging
C. Malware sandboxing
D. Code review
4. Utilizing open source intelligence sites like Facebook to gather target information is an example of which of the following? (Choose all that apply.)
A. Fingerprinting
B. Footprinting
C. Reconnaissance
D. Social engineering
5. Which of the following is the best solution for ensuring that software still in development is secure “out of the box”?
A. Memory dumping
B. Runtime debugging
C. Code review
D. Reconnaissance
6. In order to access an important server at the headquarters, a hacker first uses Metasploit to establish a connection on a workstation located at a branch office. Which of the following techniques will the hacker consider employing?
A. Pivoting
B. Sandboxing
C. DNS harvesting
D. Whois
7. Which of the following is a popular tool used for pivoting?
A. Nmap
B. Angry IP Scanner
C. Nessus
D. Metasploit
8. Which of the following is not a typical step in a vulnerability assessment?
A. Valuation of examined systems
B. Threat identification
C. Exploiting vulnerabilities to penetrate systems
D. Developing mitigation strategies
9. A penetration test usually simulates an attack from which of the following?
A. A malicious outsider
B. Malware and worms
C. A rival organization
D. ICMP floods
10. Which of the following are true statements concerning a tester using black box testing techniques? (Choose all that apply.)
A. Has detailed knowledge of function calls inside the software being tested
B. Has some knowledge of function calls inside the software being tested
C. Has no knowledge of function calls inside the software being tested
D. Simulates the attack methods utilized by black hat hackers
11. Fingerprinting is often:
A. One of the first steps in an assessment
B. Rarely used by professional penetration testers
C. Used in conjunction with dictionary files
D. Only performed on Linux-based systems
12. Code reviews are intended to:
A. Find programming errors and poor coding practices
B. Validate placement of punctuation
C. Catch bugs after software is released
D. Count lines of code
13. Which of the following are true statements concerning the use of social engineering as a technique? (Choose all that apply.)
A. It targets Facebook and Twitter accounts.
B. It bypasses firewalls by tunneling traffic.
C. It attacks the human element and not technology.
D. It is best mitigated through security awareness training.
14. Which of the following box test types is best for simulating a rogue administrator attacking the organization?
A. White box
B. Black box
C. Gray box
D. Red box
15. Google hacking is an example of which of the following? (Choose all that apply.)
A. Hacking Google
B. Using Google to perform advanced searches on the Internet
C. Using Google to access cached copies of websites
D. Using Google to limit results according to a specific domain
16. Which of the following are examples of human-based social engineering? (Choose all that apply.)
A. Dumpster diving
B. Tailgating
C. Phishing
D. Spam
E. Spim
17. Which of the following are examples of computer-based social engineering? (Choose all that apply.)
A. Dumpster diving
B. Tailgating
C. Phishing
D. Spam
E. Spim
18. Which of the following is an example of mobile-based social engineering?
A. Spim
B. Spam
C. Phishing
D. Smishing
19. Which of the following are reasons that organizations conduct penetration tests? (Choose all that apply.)
A. Regulatory requirements
B. Damage control from recent hack
C. To improve security to reduce hacking risk
D. All of the above
20. Which vulnerability are hackers hoping to take advantage of while searching for the target’s DNS records? (Choose the best answer.)
A. DNS server is missing patches.
B. DNS server doesn’t have DNSSEC enabled.
C. DNS server supports zone replication to any entity.
D. None of the above.
21. Why are some organizations using static routing as opposed to dynamic routing? (Choose all that apply.)
A. Static routing requires less administrative effort.
B. Static routing generates less traffic.
C. Static routing is more secure.
D. Static routing automatically encrypts all traffic.
E. All of the above.
Answers
1. D. Nmap looks for open ports, closed ports, and ports filtered by a firewall.
2. C. Port scanners typically scan for TCP and UDP protocols due to ports being assigned at the Transport layer of the OSI model.
3. C. Malware sandboxing takes place when organizations isolate and analyze real or potential malware themselves.
4. B, C. Footprinting and reconnaissance typically utilize open source intelligence websites and are often interchangeable terms.
5. C. Code review takes place during an application’s development in order to discover and mitigate flaws before the product is finalized.
6. A. Pivoting is a daisy-chaining concept in which hackers compromise one host in order to use that host to compromise other hosts.
7. D. The Metasploit Framework is one of the most popular hacking tools for pivoting.
8. C. Vulnerabilities scans primarily discover vulnerabilities. Penetration tests exploit vulnerabilities.
9. A. A malicious outsider is the most likely hacker to attack an organization; therefore, in most cases, this is the most appropriate hacker to simulate during a penetration test.
10. C, D. Black box testers typically have no knowledge of function calls inside the software being tested. They are recruited to simulate the hacking techniques utilized by black hat hackers.
11. A. Fingerprinting identifies key system details and therefore is often one of the first steps in an assessment.
12. A. Code reviews are designed to find programming errors and poor coding practices before software is fully released.
13. A, C, D. Social engineering targets the human element, which can also be done over targets like Facebook and Twitter. It is best mitigated through security awareness training.
14. A. White box tests simulate the attacks that could be done by a powerful internal employee like an administrator.
15. B, C, D. Google hacking advanced searches include accessing cached copies of websites and limiting the results to a particular domain.
16. A, B. Dumpster diving and tailgating are examples of human-based social engineering.
17. C, D, E. Phishing, spam, and spim are all examples of computer-based social engineering since computers are used to conduct the social engineering.
18. D. Smishing involves the usage of SMS to send unsolicited messages to targets.
19. D. Regulations, damage control, and reducing hacking risks are all good reasons to conduct penetration tests.
20. C. Hackers are hoping that administrators forgot to disable zone replication to any server while configuring the DNS server settings.
21. B, C. Static routing generates less traffic and is more secure than dynamic routing.



