How Outlook 2010 Junk Email Filtering Works 329
How Outlook 2010 Phishing Protection Works 333
Enabling and Configuring Junk Email Filtering 334
Controlling Automatic Downloads 335
Marking and Unmarking Junk Email 338
Creating Other Junk Email Rules 338
Other Spam Filtering Solutions 339
Managing Junk Email Effectively 341
TIRED of wading through so much junk email? Anyone with an email account these days is hard-pressed to avoid unsolicited ads, invitations to multilevel marketing schemes, or unwanted adult content messages. Fortunately, Microsoft Outlook 2010 offers several features to help you deal with all the junk email coming through your Inbox.
Outlook 2010 improves on the junk email and adult content filters in earlier versions of Outlook to provide much better anti-junk-mail features. As in Outlook 2007, anti-phishing measures scan email for suspicious content and automatically disable it. The Junk E-Mail folder restricts certain email functionality, displaying email messages as plain text and preventing replies to messages contained in the folder, as well as blocking attachments and embedded links.
Outlook 2010 offers four levels of junk email protection, with Safe Senders and Safe Recipients lists to help you identify valid messages. It also provides a Blocked Senders list to help you identify email addresses and domains that send you junk email, which enables you to exclude those messages from your Inbox. Email can also be blocked based on the originating top-level domain or language encoding used.
If you’re familiar with the junk email filters in earlier versions of Outlook, you already know a little about how Outlook 2010 filters junk email. Before you start configuring Outlook 2010 to filter your junk email, you should have a better understanding of how it applies these filters.
As described earlier, Outlook 2010 provides four filter levels. To specify the filter level, click Junk in the Delete group of the ribbon’s Home and click the Junk E-mail Options tab to display the Junk E-Mail Options dialog box, shown in Figure 12-1. The following sections explain the four filter levels.
Figure 12-1. Use the Junk E-Mail Options dialog box to configure Outlook 2010 quickly to filter unwanted messages.
This option protects only against mail from individuals and domains in your Blocked Senders list, moving it to the Junk E-Mail folder. All other mail is delivered to your Inbox.
This option functions essentially like the junk email and adult content filters in earlier versions of Outlook. Outlook 2010 uses a predefined filter to scan the body and subject of messages to identify likely spam.
You can’t specify additional filter criteria for subject or content checking for this junk email filter, although you can create your own custom junk email rules to block messages using additional criteria.
This level uses the same filtering as the Low level, but it also uses additional message scanning logic to determine whether a message is spam. Outlook 2010 scans the message body and message header for likely indications that the message is spam. You do not have any control over this scanning, other than to enable it by choosing the High scanning level.
If you choose the High option, you should not enable the option to delete junk email messages rather than move them to the Junk E-Mail folder. Although Outlook 2010 will catch most spam, it will also generate false positives, blocking messages that you expect or want. You should review the Junk E-Mail folder periodically and mark any valid messages as not being junk email. Marking messages in this way is explained in the section Marking and Unmarking Junk Email, on page 338.
This level provides the most extreme message blocking. Only messages originating with senders in your Safe Senders and Safe Recipients lists are treated as valid messages, and all others are treated as junk email.
Although this protection level offers the highest chance of blocking all your junk mail, it also offers the highest chance of blocking wanted messages. To use this level effectively, you should allow Outlook 2010 to place messages in the Junk E-Mail folder and review the folder periodically for valid messages. When you find a valid message, add the sender to your Safe Senders list.
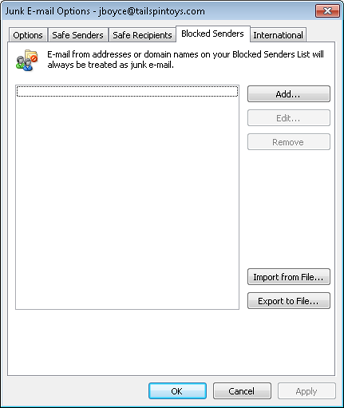
Outlook 2010 maintains three lists: Safe Senders, Safe Recipients, and Blocked Senders. Figure 12-2 shows a Blocked Senders list, which blocks all messages from these senders. Messages originating from an address or a domain on the list are filtered out. Entering a domain in the Blocked Senders list blocks all messages from that domain, regardless of the sender. Add wingtiptoys.com to the list, for example, and Outlook 2010 would block messages from joe@wingtiptoys.com, jane@wingtiptoys.com, and all other email addresses ending in @wingtiptoys.com.
The Safe Senders and Safe Recipients lists identify senders and domains that Outlook 2010 should not filter, regardless of subject or content. Use the Safe Senders list to identify valid messages by their originating address. Use the Safe Recipients list to identify valid messages by their target address. For example, if you participate in a mailing list, messages for that list are sometimes addressed to a mailing list address rather than your own address, such as list@wingtiptoys.com rather than jim@wingtiptoys.com. Add the mailing list address to the Safe Recipients list to prevent Outlook 2010 from treating the mailing list messages as junk email.
You have two options for adding entries to each of the three filter lists: specify an email address, or specify a domain. As mentioned earlier, if you specify a domain, Outlook 2010 blocks all messages from that domain, regardless of sender. However, Outlook 2010 is rather selective in blocking. Specify @wingtiptoys.com, for example, and Outlook 2010 will block messages from joe@wingtiptoys.com and jane@wingtiptoys.com but will not block messages from joe@sales.wingtiptoys.com. You must specify the subdomain explicitly in a list to either accept or block that subdomain. For example, to block the subdomain sales.wingtiptoys.com, enter sales.wingtiptoys.com in the Blocked Senders list.
Tip
INSIDE OUT Simplify management of filter lists
Outlook 2010 recognizes wildcard characters, so you can simply enter *.<domain> to block all messages from a domain and its subdomains. For example, use *.wingtiptoys.com to block sales.wintiptoys.com, support.wingtiptoys.com, and all other subdomains of wingtiptoys.com. You can import and export a filter list, which enables you to move a list between computers or share the list with others. The filter list is simply a text file with a single email address on each line, making it easy to create and manage the list.
Outlook 2010 also lets you specify a set of top-level domains and language encodings to block as part of its junk email filtering. These options are set on the International tab by selecting the desired domains and encodings from the provided lists.
Outlook 2010 by default moves junk email to the Junk E-Mail folder, which it creates in your mailbox. The Junk E-Mail folder gives you the capability to review your junk email messages before deleting them. If you prefer, you can configure Outlook 2010 to delete messages instead of placing them in the Junk E-Mail folder. As a general rule, you should configure Outlook 2010 to delete messages automatically only after you have spent a month using the Junk E-Mail folder, adding senders to your Safe Senders list and otherwise identifying to Outlook 2010 valid messages that have generated false positives.
Phishing is an attempt to obtain personal information fraudulently by luring you to a website and asking you to disclose things like passwords, credit card numbers, and so on. This website is spoofed, or pretending to be a trusted site—sometimes remarkably well—when it is actually a fake set up to help steal your personal information. Phishing is often done by sending email that directs you to the spoofed site. With the widespread use of Hypertext Markup Language (HTML) email, it’s easier to disguise the actual destination of a link, and accordingly, it is harder for you to detect the misdirection.
Fortunately, Outlook 2010 contains anti-phishing features to help protect you from suspicious websites and email addresses. Email messages are evaluated as they arrive, and messages that appear to be phishing are delivered to the Inbox, not the Junk E-Mail folder, but are otherwise treated much like junk email, with a number of functions disabled.
Disable Links And Other Functionality In Phishing Messages If Outlook 2010 determines that a message appears to be phishing, the message is delivered to the Inbox, but attachments and links in the message are blocked and the Reply and Reply All functions are disabled.
Warn Me About Suspicious Domain Names In E-Mail Addresses This option warns you when the sender’s email domain uses certain characters in an attempt to masquerade as a well-known, legitimate business. Leaving this functionality enabled protects you against phishing attacks using spoofed email addresses.
To begin filtering out unwanted messages, start Outlook 2010 and follow these steps:
Open the Inbox folder and on the Home tab of the ribbon, click Junk and choose Junk E-mail Options to open the Junk E-Mail Options dialog box (shown in Figure 12-1).
Choose a level of protection on the Options tab, as explained earlier.
If you want to delete messages rather than move them to the Junk E-Mail folder, select the Permanently Delete Suspected Junk E-Mail Instead Of Moving It To The Junk E-Mail Folder check box.
Select the Disable Links And Other Functionality In Phishing Messages check box to protect against common phishing schemes.
If you want to be warned when a domain name appears to be spoofed, select Warn Me About Suspicious Domain Names In E-Mail Addresses.
To configure the lists that Outlook 2010 uses in filtering junk email, start Outlook 2010 and follow these steps:
Open the Junk E-Mail Options dialog box as described in the previous procedure.
Click the Safe Senders tab, and then click Add and enter the email address or domain of the sender that you want Outlook 2010 to deliver to your Inbox, regardless of content or subject. Click OK, and then repeat this for each sender that you want to add.
On the Safe Senders tab, select the Also Trust E-Mail From My Contacts check box if you want Outlook 2010 to always accept email from senders in your Contacts folder, regardless of content or subject. You can also choose to select the Automatically Add People I E-Mail To The Safe Senders List check box.
Click the Safe Recipients tab, and add the target addresses or domains for which Outlook 2010 should allow messages (used typically to accept email sent to a mailing list).
Click the Blocked Senders tab, and add the addresses or domains of junk email senders whose messages you want Outlook 2010 to explicitly block.
Click the International tab, and select the top-level domains and types of language encoding that Outlook 2010 should always block.
Click OK to apply the filter changes.
Images and other online content present another potential hazard in email because you usually, at minimum, confirm that your email address is valid when you download this content. Content from unknown sources can also be malicious, containing Trojan horses, viruses, and so on.
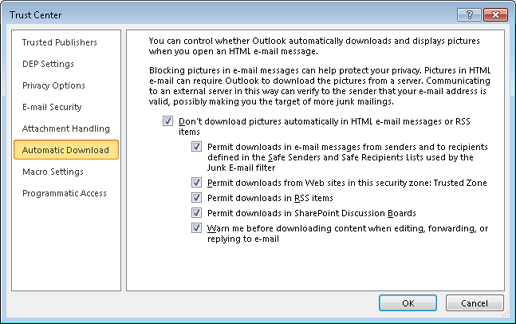
The Trust Center, shown in Figure 12-3, lets you decide when Outlook 2010 should download external content in email messages, Really Simple Syndication (RSS) items, and Microsoft SharePoint discussion boards. The Safe Senders and Safe Recipients lists can be used to determine downloading settings, as can Security Zones.
The Automatic Download options are described in the following list:
Don’t Download Pictures Automatically In HTML E-Mail Messages Or RSS Items This setting prevents images from downloading to your computer automatically, except as directed by additional settings on this page. Blocking automatic image downloads protects you from spammers who use your connection to their server to verify your identity as well as from malicious content (a Trojan horse disguised as an image, for example).
Permit Downloads In E-Mail Messages From Senders And To Recipients Defined In The Safe Senders And Safe Recipients Lists Used By The Junk E-Mail Filter You can tell Outlook 2010 to use the safe lists that you have created to determine which images it will download automatically. This lets you see images from those sources that you have already decided you trust while blocking other images.
Permit Downloads From Web Sites In This Security Zone: Trusted Zone Content that resides on a website included in the Trusted Zone is downloaded automatically when this setting is enabled. This lets you receive images and other content from trusted sources, such as corporate servers or partners, based on a common list, reducing the amount of configuration needed.
Permit Downloads In RSS Items Control over images downloading in RSS feeds is configured separately, allowing you to block images in RSS feeds without affecting email messages.
Permit Downloads In SharePoint Discussion Boards You can configure whether to download content from SharePoint discussion boards separately, offering you greater control over the content that is downloaded to your computer.
Warn Me Before Downloading Content When Editing, Forwarding, Or Replying To E-Mail If this setting is enabled, Outlook 2010 will warn you before downloading content in messages that you are replying to, forwarding, or editing. If you choose not to download the images and continue with your actions, Outlook 2010 will remove the images from the message, and the recipient will not be able to retrieve them. This is an improvement over Outlook 2003, in which you could complete your operation only if you downloaded the images.
To configure image downloading, start Outlook 2010, and then follow these steps:
Click File, Trust Center, and Trust Center Settings, and then select Automatic Download to view the options for handling image downloads (shown in Figure 12-3).
To stop Outlook 2010 from automatically downloading images, select the Don’t Download Pictures Automatically In HTML E-Mail Messages Or RSS Items check box.
If you want to view images from sources that you trust, select the Permit Downloads In E-Mail Messages From Senders And To Recipients Defined In The Safe Senders And Safe Recipients Lists Used By The Junk E-Mail Filter check box.
To allow sites that you trust to download images, select Permit Downloads From Web Sites In This Security Zone: Trusted Zone.
If you want to view images in RSS feeds, select Permit Downloads In RSS Items.
To view images from SharePoint sites, select Permit Downloads In SharePoint Discussion Boards.
If you want Outlook 2010 to alert you that images are being downloaded when you take action on an email message, select Warn Me Before Downloading Content When Editing, Forwarding, Or Replying To E-Mail.
Apply the changes by clicking OK.
The junk email filters in Outlook 2010 might not catch all the messages that you consider to be junk. You can mark and unmark messages as junk mail easily without opening the Junk E-Mail Options dialog box. When you receive a message that is junk but that Outlook 2010 does not place in the Junk E-Mail folder (or delete), right-click the message, choose Junk, and then choose the list to which you want the sender added. You also can add the sender to the Blocked Senders list (Block Sender) if you want.
If Outlook 2010 marks a message as junk mail and moves it to the Junk E-Mail folder but you don’t want the message treated as junk mail, you can mark the message as not junk (essentially, unmark the message). Open the Junk E-Mail folder, right-click the message, and choose Junk, Not Junk. Outlook 2010 displays a Mark As Not Junk dialog box. If you click OK without taking any other action, Outlook 2010 moves the message back to the Inbox. Select the Always Trust E-Mail From option to also have the sender’s email address added to the Safe Senders list. Any address that a message was sent to can also be added to the Safe Recipients List.
Once you configure it and make adjustments for false positives, the filtering technology built into Outlook 2010 can be an effective tool for waging your daily fight against junk email. The filtering technology in Outlook 2010 isn’t perfect, however, so you might need to handle junk email in other ways. One technique is to create your own rules to handle exceptions that the built-in filters can’t adequately address.
You can create rules that look explicitly for keywords or phrases in the subject or body of a message or look for specific other criteria and then move those messages to the Junk E-Mail folder (or delete them). See Chapter 11, for details on creating and working with rules.
The spam blocking features in Outlook 2010 can help considerably in blocking unwanted messages, but there are other options that you should consider in addition to the Outlook 2010 filtering technologies.
If your company or organization uses Microsoft Exchange Server, you can perform some spam filtering tasks right at the server without adding third-party software. Exchange Server 2003 and later support domain filtering for virtual Simple Mail Transfer Protocol (SMTP) servers.
Exchange Server 2007 and 2010 offer some additional features not included in Exchange Server 2003, making it potentially more effective for blocking spam. One server in an organization is designated as the Edge Transport server and is responsible for mail flow and control between internal email servers and the Internet. By default, only unauthenticated, inbound email from the Internet is filtered, although internal email can also be filtered if desired.
Exchange Server 2007 and 2010 can filter email based on a number of different criteria, including:
Content Email messages are examined to see whether they have characteristics of spam and are checked against a safe list aggregated from the Safe Sender lists of Outlook 2007 and 2010 users within the organization.
Attachment Attachments can be filtered based on either the Multipurpose Internet Mail Extensions (MIME) type of the file or the file name. Administrators can choose to strip the attachment and deliver the message or reject the message, either with a failure message to the sender or silently.
Connection Email is evaluated based on the Internet Protocol (IP) address of the server that is attempting to send the message using a variety of safe and blocked lists to determine whether the message should be delivered.
Recipient The addresses that the email is sent to are compared to a local directory and an administrator-managed blocked list to determine what to do with the email.
Sender Like the Recipient filter, this filter uses a locally maintained blocked list to block certain addresses from sending email to the organization.
Sender ID The sending system’s Domain Name System (DNS) server is queried to determine whether the IP address of the system that originated the message is authorized to send email from that domain. This verification process protects you against spoofed email addresses, a ploy commonly used by spammers and phishers alike.
Sender Reputation This feature collects information about email senders and evaluates incoming email based on a number of characteristics to assign a Spam Confidence Level (SCL) rating. This rating determines whether the message is delivered, and the rating is passed to other computers running Exchange Server when the message is sent to them.
If you are responsible for administering a computer running Exchange Server, you will find additional information in the Help files provided with Exchange Server.
Several third-party antispam solutions are available that you can consider for your organization. For example, Symantec’s Mail Security for Microsoft Exchange Server provides content scanning and filtering capabilities. Mail Security filters incoming messages for content, spyware, adware, and attachment file types (not just file name extensions).
Mail Security is available for Exchange Server, Domino, and SMTP servers. You’ll find more information about Mail Security at http://www.symantec.com/business/mail-security-for-microsoft-exchange.
Another product to consider is GFI Mail Essentials (www.gfi.com/mes). Mail Essentials provides several levels of content filtering with support for blocked lists, safe lists, and additional header checking options that enable it to detect and block spam based on a broad range of criteria.
These are just a few of the solutions available for filtering and managing messages. Many mail servers offer their own filtering capabilities, and many other products provide filtering services for existing mail servers.
One of the most prevalent spam filtering solutions is SpamAssassin, based on an open-source heuristic scanning application developed originally for UNIX-based servers. You can find information about open-source SpamAssassin at spamassassin.apache.org.
Email is a critical tool for most people, but it can also be a frustration when you feel overwhelmed by junk email. By using the features provided in Outlook 2010 and taking a few additional steps, you can greatly reduce the amount of junk email that you receive and the corresponding risks:
Use the Outlook 2010 junk email filters and phishing protection The default option of Low on the Options tab in the Junk E-Mail Options dialog box provides some protection, but it might not be enough. You might want to raise the level to High and check your Junk E-Mail folder regularly to ensure that Outlook 2010 is not sending legitimate messages there. Use the International tab in the Junk E-Mail Options dialog box to block top-level domains from which you never want to receive messages or to block messages in specific languages.
Use the Safe Senders list and Blocked Senders list Building both your blocked and safe lists will make a considerable difference in how well Outlook 2010 can filter your email.
Update the Outlook 2010 junk email filters regularly Updates for Outlook 2010 can be obtained by clicking File, Help, and Check For Updates. You can also download updated filters from office.microsoft.com/en-us/officeupdate/.
Disable functionality that can confirm your identity inadvertently Features like read and delivery receipts and automatic acceptance of meeting requests can confirm your identity to a spammer. Outlook 2010 lets you configure receipt processing for Internet email differently from messages within your corporate network so that you can leave receipts on for your business contacts while disabling them for messages from outside the organization.
Guard your primary email address Many people have a secondary email address—often from a free public provider such as Windows Live Hotmail or Gmail—that they use when posting on message boards, newsgroups, and so on. Even so, you might want to change your email address when posting it in public by changing the @ to AT or inserting extra characters (such as chrisHillREMOVE@wingtiptoys.com). This can help prevent automated gathering of your address by spammers’ robots.
Don’t reply to spam Even a seemingly simple unsubscribe message confirms that your email address is valid, so unless you know the sender, just delete the message.
Don’t automatically download images and other online content Spammers can verify your email address when you connect to the server to download the external content in a message. Online content is blocked by default, and it’s a good idea to leave it that way. You can download content for an individual message by right-clicking the message box telling you that the content has been blocked and then selecting Download Pictures.
Don’t forward chain email These messages clutter up inboxes, expose email addresses, and are all too often hoaxes. If you absolutely must forward a message, send it to only the few people who will definitely be interested, and use the BCC option for their email addresses.
Never provide personal information in email Even with a trusted correspondent, you should avoid sending critical data such as credit card or social security numbers in unencrypted email.
Don’t provide personal information to links you get in email If you get email that appears to be from a company that you do business with, don’t assume it actually is. Most email that provides a link and asks for personal data is spoofed in an attempt to get you to disclose this information. If you think the email might be valid, type the Uniform Resource Locator (URL) of the business into your browser rather than clicking the link in the email message to be sure you end up at the correct site.
Read each website’s privacy policies Get in the habit of checking privacy policies before providing your email address to a website. Sure, this can take a minute or two, but it takes more than that to handle the spam that you will get if a site misuses or sells your email address. Most websites explain what they do with the information they collect; you might want to carefully consider whether to provide any information to those that do not.
Keep antivirus, spyware, and firewall protection up to date Outlook 2010 can help you avoid most junk email and the associated threats, but the most effective protection is a multilayered approach. You should also install firewall and antivirus software and make sure that it is kept up to date. You might also want to obtain utilities that protect against spyware and other malicious software.