CHAPTER 26
Care and Feeding of Mobile Devices
In this chapter, you will learn how to
• Troubleshoot common mobile device issues
• Explain basic mobile device security
• Describe typical mobile security troubleshooting issues
• Describe typical mobile application troubleshooting issues
By their very nature, mobile devices require troubleshooting and security practices that differ a lot from desktop computers and somewhat from other portable devices. This chapter explores general troubleshooting first, then covers security features and capabilities of devices common in the mobile market. The chapter finishes by jumping into the details of two different troubleshooting aspects: security troubleshooting and application troubleshooting. CompTIA loves those scenario questions, so get ready for some real-world issues when it comes to security and application troubleshooting.
901/902
Troubleshooting Mobile Device Issues
The CompTIA A+ exam objectives divide mobile device problems into two groups: hardware and OS issues, and security and application issues. In this section we’re going to cover the hardware and OS issues. These common problems happen across all varieties, types, and manufacturers of mobile devices. There are also issues that may affect network connectivity.
Touchscreen Is Nonresponsive
A nonresponsive touchscreen can be caused by several things. The first and simplest issue to resolve is a dirty screen. Sometimes simply wiping the touchscreen down and getting rid of fingerprints, dust, dirt, and other foreign objects may fix a responsiveness problem (see Figure 26-1).

Figure 26-1 Cleaning a smartphone
Dropping or getting a mobile device wet can cause issues with the touchscreen. Even if the glass doesn’t break, dropping a device can break internal connections. Moisture can cause internal shorts. Avoid both problem areas if possible.
There’s also the possibility that touchscreen responsiveness could be affected by apps or the device’s configuration settings. These might manifest in odd ways. You might touch a control or option, for example, and something completely unexpected occurs. The 902 exam calls these events “inaccurate touch screen responses,” but the rest of us call them, “really?” These issues are typically easy to fix, because they may involve reconfiguring an app, removing it and reinstalling it, or reconfiguring the display settings on the device itself.
App Not Loading
A mobile device app may not load properly or install correctly for several reasons. First, the app may not be intended for the mobile device, including the operating system version or flavor currently running. With Android devices, for example, there is a possibility that the version of the Android OS on the device itself is not compatible with the app. This is because different manufacturers can tweak the OS to suit their own needs, which may cause compatibility issues with other vendors’ apps.
Another reason an app may not load is that the device may not meet the hardware requirements of the app, such as amount of available RAM, storage space, and processor type. It’s always a good idea to review an app’s requirements before installing it.
Slow Performance
Mobile devices can suffer from performance issues just as regular desktop computers and laptops can, and often for the same reasons. Performance issues can be caused by storage space being almost filled up on a mobile device, making it unable to save data or install apps efficiently. Additionally, mobile devices can suffer from having too many apps running at the same time, eating up RAM. Usually, the mobile device’s OS has configuration settings that enable you to stop apps or view their resource usage, including memory and storage space. If storage space is an issue, you may have to uninstall some apps, or reinstall them so that they are stored on removable storage devices, such as micro- or mini-USB memory cards.
One of the first troubleshooting steps you can take in resolving slow-performance issues is to perform a hard reboot of the device, which clears RAM of all running apps, and maybe even apps that could be hanging up and not running properly. As far as troubleshooting tools go, there are plenty of apps that measure the device’s performance, telling you how much RAM, storage space, CPU time, and so forth, are being used. Sometimes those apps can help point the way to what’s causing the performance problems. If, in the end, you determine that a hardware issue is causing performance problems, you should take the device to an authorized repair facility.
E-mail Issues
Basically, we live in a world where e-mail is easily divided into two different types: Web-based e-mail like Google Gmail and Yahoo! Mail that uses a Web browser to access your mail, and traditional e-mail where you use a dedicated client like Microsoft Outlook or Mozilla Thunderbird to get your e-mail. In either case, issues may arise. Thankfully, we can deal with most e-mail issues by looking in just a few places.
The Best App
With mobile e-mail, almost all Web mail providers have a specialized app just for their e-mail. If you want to access Gmail, download the Gmail app. If you want to connect to a Microsoft Exchange server, you download a copy of Outlook for your mobile device. Make sure you have the correct app for your e-mail.
User Name/Password
Whatever e-mail app your mobile device uses, there will be a place to enter your e-mail account’s user name and password. On personal accounts, a common scenario after getting a new phone is to enter your password at the e-mail app’s prompting, only to discover you’ve forgotten the password! This typically requires going through the process of resetting your password.
Server Settings
If you’re configuring a traditional SMTP/IMAP/POP3 client, at some point you’re going to need to enter the name for your SMTP server and your IMAP/POP3 server. Figure 26-2 shows the e-mail server settings for Apple’s iOS e-mail app.
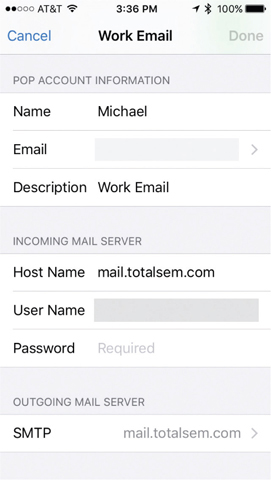
Figure 26-2 E-mail server settings
Encryption Problems
Using methods to secure e-mail messages from anyone but the intended recipient generally fall well outside the accepted parameters of the CompTIA A+ certification. The 902 exam has one line on troubleshooting mobile devices that reads, “unable to decrypt e-mail.” To go into any detail on these methods would take a lot of pages and provide you with a ton of information on a topic you won’t truly see until you take the CompTIA Security+ exam. So here’s the issue in a very tight nutshell.
For an e-mail message to be secure, it must be encrypted—scrambled according to some kind of standard like Pretty Good Privacy (PGP). For the recipient to read the e-mail message, he or she needs to have software that can unscramble or decrypt the message. To ensure the sender and recipient only can access the contents of the e-mail message, both people need specific keys that enable encryption and decryption.
In practice, if you receive a message and you are unable to decrypt the e-mail, you need to contact the sender to set up your mail client and exchange keys.
If you find the idea of securing e-mail on your computers interesting, the PGP Corporation has a great intro Web site here: http://www.pgpi.org/doc/pgpintro/
Battery Life
Mobile devices run on batteries and batteries eventually run out of power. These two simple facts don’t adequately address the issues that battery life can cause, and the issues that can cause problems with battery life itself. Mobile devices are rated differently in terms of how long the battery should power a device during normal use, how long the device can go between battery charges, and the levels of power that both the battery provides and requires in order to charge.
Most modern mobile devices use Lithium-Ion (Li-Ion) batteries. Over the years, as device features have increased, displays have gotten bigger, mobile CPUs have gotten faster, and apps have become more graphics intensive, battery power has become a premium for mobile devices. Batteries have not necessarily kept pace with the other rapidly evolving hardware and features on mobile devices, however. While marketing ads proclaim extended battery life as a feature of the latest and greatest models, newer, faster hardware and features in proportion seem to neutralize any benefits of that extended battery life.
Several factors can affect battery life. One of the main factors is network usage. Any time the device is connected to a network, such as a wireless network or even the cellular one, the device is constantly transmitting and receiving data, sometimes in the form of simple management messages that are sent back and forth to the network entry point device. Even when there is no real data being transmitted or received over the network, these management messages require power from the device, and they can, over time, significantly reduce the battery charge. Often, when traveling, a device such as a smartphone or tablet will constantly roam or try to pick up the strongest cellular or wireless signal it can find, and this constant search for stronger signals can significantly drain battery power. This unintended power drain can be controlled with most smart devices, however, through configuration changes that limit device roaming or searching for new wireless networks.
Another significant cause of battery charge reduction is the constant use of GPS or location services. When location services are turned on, the device is constantly receiving GPS data in order to fix its location. This could be for apps that require location data in the background, or for active apps, such as mapping software, that use the GPS receiver. In any event, the user will notice significant reduction in battery charge, and over the life of the device this will reduce the life of the battery as well. The simple solution to this is to be judicious with networking location services. When they are not required, they should be turned off. Another tip is to review configuration settings for apps that use location services and disable the ones that don’t need to have immediate location data. In the event that you may actually use an app that requires location data, you can always turn the setting back on and let the app get a location fix. Some examples of apps that require location data include those used to find restaurants and movie theaters, for example, as well as specialized apps, such as geocaching, mapping, and navigation apps.
Another factor that affects battery life is screen display and brightness. A screen that is configured to constantly show the brightest level will significantly reduce the battery life. Users often mistakenly adjust the screen brightness to be constantly at the highest level, thinking that they will see it better in bright sunlight or in darkened indoor areas, when often this isn’t the case. The display controls on a mobile device should typically be configured to automatically adjust the screen brightness based upon factors such as device sleep or suspension, app usage, or even smartphone call use. Figure 26-3 displays the battery usage for an Android smartphone. Notice how much of the battery is being drained from the screen configuration alone!
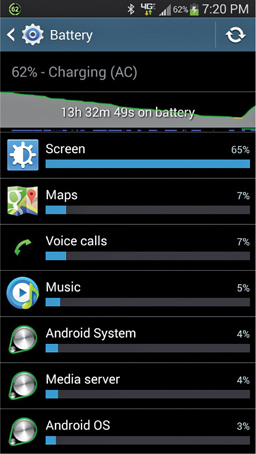
Figure 26-3 Battery usage for a smartphone
Swollen Battery
Batteries on mobile devices can experience a phenomenon known as swelling. When this happens, the battery casing actually swells; it heats up, often cracks, and can cause leakage of the material inside. There a few reasons why this might happen. First, overcharging the battery by leaving it on the charger for long periods of time can cause swelling. Li-Ion batteries have been known to swell due to overcharging. The device should be removed from the charger when it’s fully charged. Second, using a non-OEM charger may cause swelling, if you are using a charger that is not rated for the correct voltage and wattage the computer requires. An overheated computer or battery can also cause swelling. Finally, in rare cases, you may occasionally get a battery that is simply bad from the manufacturer.
When you encounter a swollen battery, there really is no recourse except to replace it with a known good battery, preferably an OEM battery that came from the original device vendor.
Overheating
A mobile device that overheats is never a good thing. An obvious reason for overheating would be leaving it in contact with direct sunlight for long periods of time. That can damage the screen and other components. Our concern here primarily, however, is a device that overheats on its own. This is almost always caused by some sort of hardware issue, possibly a defective battery or other power circuit within the device. There’s really not much you can do for this issue, except take it to a service center. The dangers of not addressing an overheating mobile device are, at least, an eventual device failure, resulting in lost data, and, at worst, a device that overheats so much it becomes a safety issue for the user by becoming so hot that it burns to the touch, electrically shocks the user, or causes the battery to leak or explode.
Frozen System
A mobile device that locks up or freezes can be a huge annoyance. There are several possible causes for this issue. First, an app that’s not written properly, or is incompatible with the device, may cause the device to freeze because it is using too many resources, or using them incorrectly. An example of this would be an app that uses too much RAM, improperly accesses particular memory addresses, or consumes too much CPU time. A second cause could be a network connectivity issue. A device will often seem to freeze when it’s desperately trying to find or maintain a network connection, and this will consume a lot of resources until it finally gives up. Finally, faulty hardware can cause a device to freeze. This can manifest itself as a frozen touchscreen, hanging apps, and generally poor performance.
The solution to a frozen system is often to reboot it, clearing its RAM and restarting it. If the device frequently freezes, especially when using a particular app, then the solution is probably to reinstall that app or find a replacement for it. Sometimes operating system issues can cause device freezes, so look for OS patches that may correct those types of issues. If the device randomly (and with increased frequency) freezes up, whenever using any type of app, then it’s likely a hardware issue and the device may need to be serviced.
Cannot Broadcast to an External Monitor
Back in Chapter 25, “Understanding Mobile Devices,” we saw that the vast majority of mobile devices have some form of video output that enables you to broadcast the display onto an external monitor or projector. When done correctly this is usually an almost automatic process: plug some adapter into your mobile device then plug that adapter into your external monitor’s VGA or HDMI port and it just all works.
Well, that’s the theory. In reality, broadcasting your mobile device’s screen to an external monitor is fraught with problems. While these vary by type of device, here are a few tried and true issues to look at when your device cannot broadcast to an external monitor:
• Is your source correct on the external monitor? All monitors, TVs, projectors, whatever have lots of inputs. Is the external monitor pointing at the right source?
• Do you have the right adapter for your device? Apple alone has come out with five different types of videos adapters in the last few years—and don’t even get me started on the many dongles for Android! Make sure you have an adapter that is known to work for your device!
• Does your dongle need its own power source? Many do not. Many do.
• For HDMI: Did the HDMI recognize your device and your external monitor? Depending on the make and model, it’s common to have to reset one or both devices to give the HDMI time to see who its plugging into and set itself up.
No Sound from Speakers
Sound issues are also common in mobile devices. The most obvious, and probably most common, issue is that the volume is turned down through software configuration or an app, or the speakers are muted. This is easy to fix, but sometimes you have to go through many configuration settings for both the device and apps to figure out which one is controlling the volume at the moment or which one may actually be muting the speakers. Many mobile devices have hardware volume controls on them, so check them. If that doesn’t work, then start going into the configuration settings for the device and apps. If none of these steps works, then you may have a hardware issue, in that the speakers simply may no longer be connected properly inside the device, or they may be damaged. As with all other hardware issues, you’ll likely have to take the device into a service center to be fixed.
GPS and Location Services Problems
Aside from some of the issues with devices, hardware, and the operating system itself, there are occasionally issues with location services on mobile devices. Most mobile devices today are made with some type of built-in technology designed to ascertain the device’s location. Some devices use built-in GPS capabilities, while others use 3G and 4G cellular technologies and Wi-Fi in place of GPS (or to supplement it) to get location data for the device. Location data is used for some of the obvious things, such as map apps, GPS coordinates, and so forth, but it’s also used for some things that are not so obvious to the user.
Most apps use location data for a variety of reasons. In some cases, it’s used to assist the user with whatever functions the app performs, such as locating a restaurant or a bank, for example, near the user. In other cases, location data may be used to provide services such as weather or local traffic conditions. And, for better or for worse, some apps use location data rather covertly for the purposes of marketing and reporting user data back to their respective vendors for various reasons. For the most part, this particular use is usually unknown by and undetected by the user. In any case, there are many different uses for location data, so it’s considered an important feature of most modern mobile devices.
Symptoms of location issues include a map app not being able to identify the exact location of the device, or error or other messages from the device, OS, or various apps that rely on location data (see Figure 26-4).
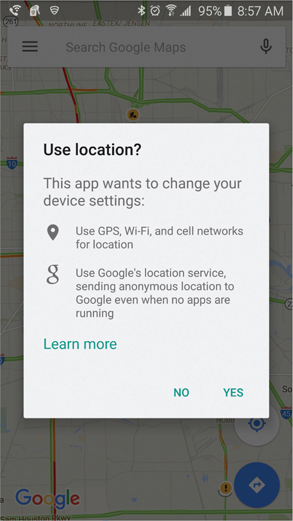
Figure 26-4 GPS prompt
Troubleshooting location problems begins with simple actions such as making sure that your GPS, cellular data, and Wi-Fi are turned on and functioning properly, as sometimes these services can be inadvertently turned off by the user or by an app, and have to be periodically reactivated. Typically, a warning message would indicate whether or not GPS or data services are turned off, so this would be an easy problem to identify and fix. Other issues may only affect specific apps because they may have been configured such that they are not allowed to access or use location services. This is usually a matter of going into the app configuration or location services settings and allowing the app to make use of those services.
There also other problems that may cause location issues that are related to the operating system and the hardware in the device. Along with the OS issues discussed previously, there could be OS configuration settings that are configured incorrectly for GPS, cellular, and Wi-Fi services that may prevent location services from functioning properly. These configuration items should be checked when location service symptoms are being seen with more than one app. Hardware problems may lie in the actual GPS or network hardware with the device, and should be treated as described in the previous sections on hardware. Although laptops and other mobile devices may have removable network or GPS modules in them, most of these components are not user serviceable and have to be replaced or repaired by authorized service technicians.
System Lockout
System lockouts can occur for a couple of reasons. The first, and most common, reason is that the user forgets her PIN. With some mobile devices, the user may only get a certain amount of tries before the device locks and doesn’t allow her to continue to attempt to unlock it. An additional issue would be that some devices are configured to completely erase themselves after a certain number of failed unlock attempts. This can be configured on the device itself, or centrally through the organization’s mobile device management (MDM) software. Either way, you should probably advise the user to not exceed the maximum number of retries for unlocking the device. If it is a company-owned device, the company should probably securely store PINs for all the mobile devices it owns, in case just such an issue occurs, as well as maintain current backups of all its mobile devices. With devices owned by individual users, you have to hope that they have backed up their data as well.
If the device can be unlocked through finger swipe patterns or fingerprint authentication, then a failure of either of these two methods to unlock the device probably means that the device has lost its configuration and the user needs to be reenrolled with the authentication configuration on the device to use those methods. Typically, when these methods are used, the backup method to unlock the device is by using a PIN.
In any event, if the device is controlled through centrally managed MDM software, the organization has the ability to remotely unlock the device. If it’s not centrally controlled, then the user may have to plug the device in to a computer and use an application provided by the manufacturer to access the device with a passcode. In the end, if the user can’t unlock the device, the only solution may be to restore the device from a backup, if available, or completely reinstall the OS and apps from scratch. This may cause the user to lose data on the device.
Troubleshooting Steps and Tools
Because mobile devices typically aren’t user or field technician serviceable, there aren’t many things that can be done to fix them out in the field. The few things that can be done are fairly common to all mobile devices, and typically follow a kind of common-sense pattern of steps, much like troubleshooting steps for desktop computers. If these initial troubleshooting steps do not work, then the end solution is to take the device to an authorized service center. Some of these steps may involve data loss, if active apps and data are in memory when the steps are taken, and some steps may involve data loss simply because the device may have to be reinstalled from scratch.
In order of precedence from least damage to data and apps to the worst-case scenarios, the most common troubleshooting steps for mobile devices include the following:
1. Close running apps.
2. Force an app to stop running.
3. Adjust configurations/settings.
4. Uninstall/reinstall apps.
5. Soft reset.
6. Hard reset.
7. Restore the device from a complete backup.
8. Reset the device to factory defaults.
This is simply notional order of troubleshooting steps; the order that you take may be dictated by your organization or your repair facility. You can also use the different troubleshooting methodologies discussed elsewhere in this book. The steps you take depend upon the nature the problem in the first place, and affect which steps you may take and in which order. Additionally, different devices have different ways to perform some of these steps. For example, Android devices enable you to force stop an app in its configuration settings. There are also different ways to perform soft and hard resets on the different mobile devices, depending upon the manufacturer. You’ll have to research these particular steps based upon the type of device you are working on. Many of them, including forcing apps to stop, reinstalling apps, and any kind of resets, will probably cause you to lose some data, which may require restoration from a backup, if a backup exists for that device.
Securing Mobile Devices
Mobile devices require security. This applies to company-owned devices and personal ones. All need to handle damage, malware, data loss, and theft.
BYOD Versus Corporate-Owned Devices
The Bring Your Own Device (BYOD) war was one that was briefly fought and lost by organizations hoping to continue the long-held tradition that IT assets belonged to (and were strictly controlled by) the company, not the individual. As more and more mobile devices were brought into the infrastructure, however, IT folks realized that the genie was out of the bottle and they would never completely be able to control these new technologies. In some cases, companies may be able to enforce a policy that prohibits the use of personal devices to access corporate data and resources, particularly those in high-security environments. At the other end of the spectrum, some companies allow (and even encourage) personal devices, as it saves corporate IT dollars and can contribute to a much happier employee. Most organizations, however, probably fall into the middle of the spectrum and have a mixed environment of both corporate-owned and personally owned mobile devices. In some cases the organization may institute a cost-sharing program, subsidizing an employee’s personally owned device by offering a monthly phone stipend or through discount agreements with mobile device and telecommunications vendors. Regardless of the degree of BYOD in the organization, there are challenges that must be dealt with.
One challenge is device control and how much control the corporation has versus the individual. If corporate data is processed or stored on the device, then, rightfully so, the organization should have some degree of control over the device. On the other hand, if the device also belongs to the employee, then the employee should have some control over it. Another challenge is who pays for the device and its use. If the organization allows the user to use her own device for company work, does the organization help pay for the monthly bill or compensate the user for its use? Again, this issue is probably better solved by defined formal policy and procedures. Yet another and equally important challenge in a BYOD environment is employee privacy. If policy allows the organization some degree of control over the device, what degree of privacy does the user maintain on her own device? Can the organization see private data or have the ability to remotely access or control a user’s personal device and its use?
Profile Security Requirements
A profile is a collection of configuration and security settings that an administrator has created in order to apply them to particular categories of users or devices. A profile can be created in several different ways, including through the MDM software, or in a program such as the Apple configurator, for example. Profiles are typically text-based files, usually in an eXtensible Markup Language (XML) format, and are pushed out to the different devices that require them. Profiles should be developed based upon the needs of the organization. You can develop a profile that is device-specific, and applies to only certain platforms or operating systems, so that a particular type of device will get certain settings.
You can also develop profiles that are specific to different user categories or management groupings. For example, if you have a group of mobile sales users, you might create a profile that would contain certain settings for security, apps, network connections, and so forth. Your senior organizational executives may have a specific profile that is applied to them based upon their unique requirements. Frequently, senior managers or executives may be allowed to do more with a corporate device, in terms of what’s acceptable to the organization. There also may be unique apps or connection requirements for these executives. Likewise, middle managers may require unique profiles that have configuration settings applicable to what functions they need to perform on the network using a mobile device. These managers also may have specific apps such as human resources or payroll-related apps installed on devices.
There are also group-specific profiles that may apply to external users, such as consultants or business partners, for example. These users may require limited access to organizational resources using their own mobile device, their organization’s mobile devices, or even mobile devices issued from your organization. A group-specific profile applied to these external users may give them particular network configuration and security settings so that they can access a business extranet, for example, or use specific VPN settings. They may also require access to particular enterprise or business-to-business (B2B) apps hosted on your organization’s servers. In any case, both device- and user-specific profiles can be very helpful in managing larger groups of users, delivering uniform security and configuration settings to their devices based upon different mission or business requirements.
Depending upon your organizational needs, you could conceivably apply several different profiles to a device at once, based upon platform, user group, and so forth. It’s possible that some profile settings will conflict with those in a different profile. For example, some restrictive settings for a device profile may not be consistent with some less-restrictive ones in a group or user profile. When both are applied to the device, the different configuration settings may conflict and overwrite each other so you may want to pay special attention to profile precedence when applying them to the device. You may decide to configure settings precedence in the MDM server to resolve conflicts based upon a number of criteria, including user group membership, or security requirements, for instance.
As far as devices go, in addition to vendor- or OS platform–specific profiles, you should also develop profiles that may apply to corporate-owned versus personally owned devices. A profile applied to a device in a BYOD environment may be considerably different than one applied to an organizationally owned device. This would be based upon policy settings affecting privacy, acceptable use of the device, and so on. Figure 26-5 shows how you can conceptually apply different profiles to different device and user groups.
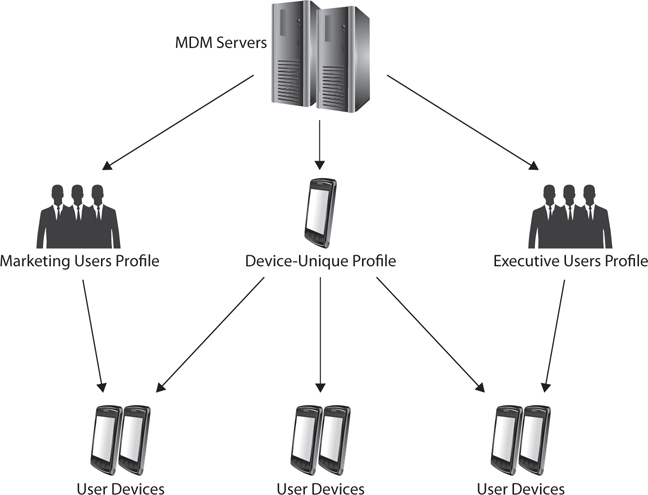
Figure 26-5 Applying profiles to different device and user groups
Preventing Physical Damage
Mobile devices cost a fair amount of money and thus aren’t disposable media for most people. That means you need to take steps to prevent damage. The first step you must take is to get a protective cover or sleeve for the mobile device. It doesn’t help the HD camcorder in your new iPad if you get a scratch across the lens! You’ll get a scratched, blurry movie even though the camcorder is capable of much, much more. Apple makes very nice covers for iPhones and iPads, plus you can get many third-party covers and sleeves (see Figure 26-6).

Figure 26-6 Putting an Apple Smart cover on an iPad
Depending on the amount of money you’re willing to spend, you can get a cover that helps protect your screen from scratches, impacts, and small amounts of water. Like to scuba with your Android device? There are waterproof cases that enable you to check your Facebook account from 40 feet underwater. (These are specialty cases and not very typical.)
Do the obvious to protect your devices. Don’t get them anywhere near liquids. Don’t run your smartphone through the wash in your trousers. Don’t even think about placing heavy objects on that ~$600 tablet! Use common sense.
Combating Malware
Malware on mobile devices is an interesting issue. Tight controls on the OS and apps make traditional malware infections almost impossible on iOS and Windows Phone devices. When malware strikes, the OS maker supplies periodic patching/OS updates, automatic updates and operating system patches. Android lacks a few of the controls that we see in iOS and Windows Phone. To plug the gap, there are third-party antivirus and anti-malware single-user (user-level) and enterprise-level solutions available. Figure 26-7 shows an example of user-level antivirus software for an Android device.
Figure 26-7 Antivirus app for Android
Any anti-malware solutions used on mobile devices should cover the widest possible range of malware threats, and should, to the best degree possible, cover the widest range of mobile devices used in the corporate network. In a heterogeneous infrastructure, because there may be different varieties of mobile devices using different operating systems and coming from different vendors, a one-size-fits-all anti-malware solution may not work. Different solutions may be necessary for the different devices present on a network, or, in some cases, different modules that cover specific types of devices may be available from the vendor to integrate into an enterprise-level anti-malware solution.
In any case, the important part of an enterprise-level anti-malware solution is to deliver timely updates to the devices on a routine basis. Network access control solutions can ensure that when a device attempts to connect to the network, it is checked for the latest anti-malware signatures and updated as necessary before being allowed to connect to the network. In the case of user-managed solutions, when necessary, policy, network access control, and other technical solutions may be needed to ensure users are updating their own devices in a timely manner.
Dealing with Loss
Losing a mobile device creates a series of issues that you need to address. First, protect your data from access by putting a good passcode lock or screen lock on the device, which requires you to type in a series of letters and/or numbers, or perhaps use motion patterns, fingerprints, or even facial recognition, to unlock the mobile device each time you press the power button or touch the screen. Don’t assume that you’ll never set the phone down in the lavatory at an airport and forget about it or lose it to a thief. Most mobile devices enable you to set a passcode lock or screen lock from Settings (see Figure 26-8). Do it right now! Modern versions of iOS and Android encrypt the contents of the built-in storage, so even if a “finder” dismantles the device to access the drive, he or she will not get your documents.
Figure 26-8 Passcode option in Settings
Mobile devices may also have a preset restriction on the number of failed login attempts that, when exceeded, locks up the mobile device. This system lockout slows down someone trying to hack into a found mobile device while you use locator services or applications to try to recover it or remotely wipe it.
Apple, Microsoft, and Google offer locator services for discovering the whereabouts of a misplaced mobile device. Using Apple’s iCloud as an example, log in to your iCloud account and click the Find My iPhone button. (This works for both iPhones and iPads.) As soon as the device in question accesses the Internet (and thus receives an IP address and posts its MAC address), iCloud will pinpoint the location within a few yards (see Figure 26-9). Very slick!
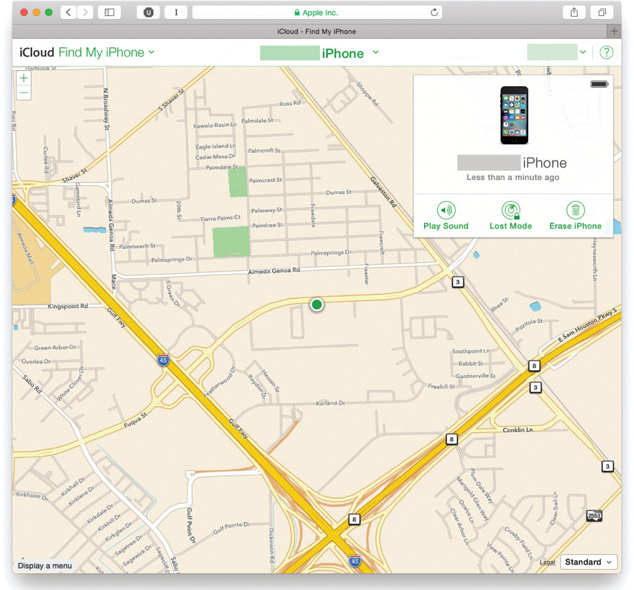
Figure 26-9 Locating a device in iCloud
Recovering from Theft
If your mobile device gets stolen and contains sensitive information, then you have a couple of options for dealing with it. Certainly the locator services help, but if you have credit card information or other very damaging information on your mobile device, you need to act quickly.
First, make sure you have your data backed up. You should have everything synced to a local machine and, if possible, backed up to one of the remote backup applications—like Microsoft’s One Drive cloud service—to put your data beyond the reach of even a disaster that takes out your house. With Windows Phone 8.1, for example, go into Settings and select Backup. This screen lets you select what items on your phone get backed up (see Figure 26-10).
Figure 26-10 Selecting items to get backed up
For Apple devices, you back up to one of several services, such as iTunes or iCloud, and use the Apple Configurator to restore. Android devices use the Google Sync feature to backup and restore.
Second, you can remotely wipe your mobile device. Microsoft makes it supremely easy through your Microsoft account. Log in, locate, and nuke your device (see Figure 26-11). You may never get the device back, but at least the bad guys won’t have your data.
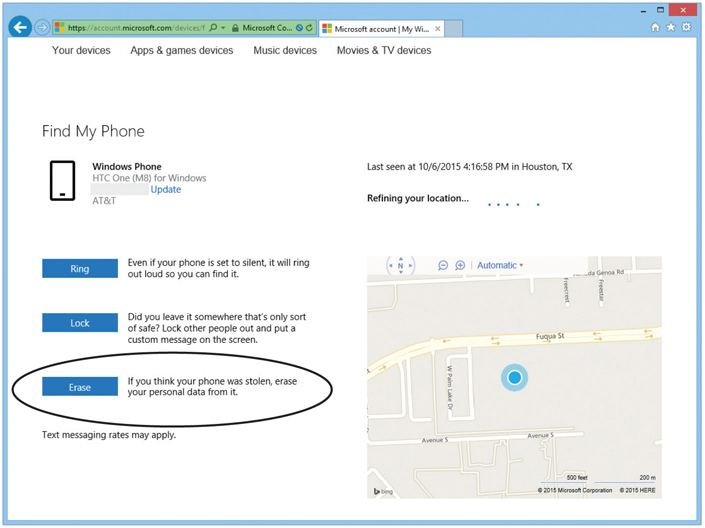
Figure 26-11 Remote wipe
Securing Your Data
Every security scenario we’ve discussed so far (remote wipe excepted) was designed to secure the device itself. Let’s now get into what we can do to protect our actual data.
Multifactor Authentication
Before we discuss multifactor authentication, it’s worth explaining single-factor authentication, as well as the different factors that exist. In order to understand single-factor authentication, it helps to understand what the authentication factors actually are. First, there is the knowledge factor. This is attributed to something the user knows, such as a user name and password. The second factor is the ownership or possession factor. This is something the user has in her possession, such as a smartcard or token. A third factor is the inherence factor. This is something the user either is or something they do. An example of an inherence factor is a biometric identifier, such as a fingerprint or retinal pattern. You commonly hear these three factors referred to as something the user knows, something the user has, and something the user is.
There are other authentication factors as well that are not as commonly considered in security authentication, but exist nonetheless. For example, something you do (an inherence factor) could be used in an authentication scheme whereby the user draws a certain pattern on the screen of a mobile device. Another authentication factor is the location factor, or somewhere you are. This can be used if the individual’s location can be pinpointed via GPS or some other method. The individual may be required to be at a certain location in order to log in to the system, for example. Yet another factor is the temporal factor. This factor is time based, and may require logon at a certain time of day, for example, within a narrowly defined time period, or even within so many seconds or minutes of another event. Token methods of authentication also use time factors, as the PIN displayed on a token is only good for a finite amount of time.
Now that you know what the various authentication factors are, let’s get back to the simplest form of authentication, single-factor authentication. In single-factor authentication, the user has to use only one of the factors in order to authenticate. You most commonly see this in authentication methods that require only a user name and password combination. Although it seems that these are two different elements, it is still only one factor being used, the knowledge factor.
It makes sense that since single-factor authentication uses only one factor, multifactor authentication uses more than one factor. In the past, the trend was to refer to it as two-factor authentication, which meant that the authentication scheme required more than one factor. Over the years, however, authentication methods have developed that require even more than two factors, so it has become more correct to say multifactor authentication. Multifactor authentication can use a variety of methods, as long as it uses more than one. There are many examples of multifactor authentication that you may see in your everyday life. For example, when you use a bank’s ATM, you’re using multifactor authentication because of something you possess (the ATM card) and something you know (the correct PIN). To access data and systems, multifactor authentication can use that method as well.
Biometric Authentication
Combined with other authentication factors, biometric elements can provide a very secure multifactor authentication mechanism. An example of biometric authentication might be presenting a smartcard to a proximity badge reader and then having your fingerprint scanned on a fingerprint reader before being granted access to a secure area.
Mobile devices are now using biometrics as well to authenticate to them. Laptops have included fingerprint readers for a few years now, and we are now seeing other mobile devices, such as smartphones, that are able to use these readers as well. A prime example of this is Apple’s Touch ID; starting with the iPhone 5s, the iPhone can unlock with a fingerprint. To enable Touch ID, use the Settings app to enroll a finger, or five! (see Figure 26-12).
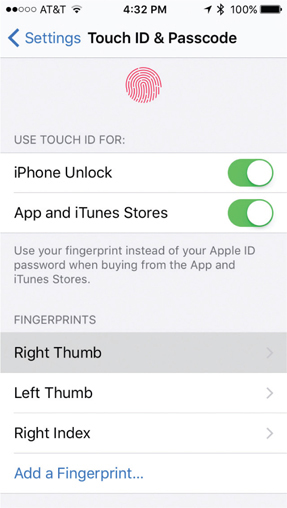
Figure 26-12 Touch ID options
Authenticator Applications
Access into third-party or corporate networks often requires strong authentication methods. Most often, authenticating to a network or service requires some type of app to facilitate the authentication process. To access a corporate VPN, for example, may require a specific app, approved and published by the organization, configured with the correct security settings. There are also generic applications that can be used for a variety of authentication needs, and may offer the ability to use multiple sets of credentials to access different Web sites, networks, or network-based services (for example, corporate e-mail, VPN access, and so forth). There are also several apps that can handle multifactor authentication and act as tokens or issue temporary session PINs.
They key consideration about any of these apps is configuration. This means that you must have the right network configuration, to include IP address, subnet mask, DNS servers, and using the correct port and secure protocol. Configuring any of these items incorrectly will likely result in no connection to the service or network you’re trying to connect to. Additionally, however, from the security perspective, you also need the correct authentication and encryption settings (if encryption is required during authentication, which, hopefully, should be). These settings might include the correct authentication method, the right encryption algorithm, and the right settings for both. If anything is configured incorrectly, the mobile device won’t be able to authenticate to the network.
Trusted Sources Versus Untrusted Sources
For the most part, getting software from legitimate app stores run by the major vendors, such as Apple, Google, Microsoft, and Amazon, is not only easy, but usually secure. Different vendors have different requirements for developers to get an app into the app store, and these include security requirements as well. Some of this stems from the development and support model used by the vendor. Apple is very monolithic in their device and application structure, strictly controlling all aspects of both the device and the apps that run on it. Apple is extremely strict, for example, in terms of how developers must create an application that is sold in iTunes. Android, on the other hand, is based upon a multitier model, where the devices are developed separately from the apps, and even the operating systems that run on them. There are variations in the Android devices’ operating system flavors that require developers to develop differently for each variation. What may run on devices sold by one vendor isn’t necessarily guaranteed to run on another vendor’s device, although they all use variations of the Android operating system. A prime example of this is Amazon’s line of Kindle devices, which can only get apps from the Amazon Appstore. Additionally, Android apps aren’t always subject to the same strict developer guidelines that Apple apps are. That doesn’t necessarily mean they are less secure, but this can cause issues for secure development.
The security weakness that exists with third-party app stores is essentially getting apps from unapproved or unofficial sources. There are definitely legitimate app sources outside of Google Play, for example, such as device manufacturers, communications carriers, and in-house corporate development sources. Some sources, however, are not so legitimate, and are usually unapproved by the vendors, manufactureres, and corporate customers for use. In some cases, you can get just the app, but getting it to run on the device may be problematic, as some of these apps require root-level access to the device. This is typically not allowed on most consumer devices unless the device is rooted or hacked. See “Unauthorized Root Access” later in the chapter for more details.
When getting apps from questionable sources, problems include apps that contain malware, apps that steal personal data and transmit it to a third party, and even apps that can be used as hacking tools. Additionally, some apps require replacing the operating system with one that’s not approved by the vendor, which not only invalidates the warranty on most devices, but also could cause the device to be unstable and not operate properly.
Firewalls
Software firewalls are typically installed on individual hosts, and as such, are normally used to protect the host itself from network-based threats. A software firewall is typically installed into an existing operating system. Apple and Windows systems have built-in firewalling features that are part of the mobile OS. Android systems require third-party firewalls. There is a surprising number of software firewalls for Android devices. One example of a software firewall for Android is shown in Figure 26-13.
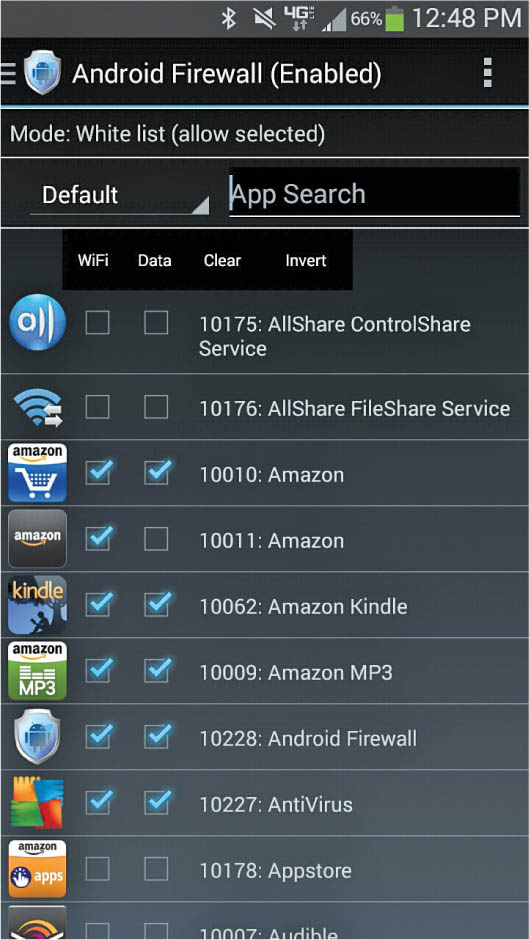
Figure 26-13 An Android firewall app
Android software firewall packages include basic rule elements that can be used to construct rules to filter specific traffic coming into the host. Many of these packages also include anti-malware solutions and basic intrusion detection solutions. Some of these software firewall solutions are standalone and have to be configured and managed by the user, whereas some are enterprise-level solutions and can be centrally configured, updated, and managed by the systems administrator. Keep in mind that the software firewall packages work at the very basic level and can’t possibly keep out every single network threat that the host is exposed to. But they serve as a second line of defense for the host, and are part of any good layered defense-in-depth security design.
Mobile OS and Application Security Issues
We’ve already discussed mobile device security at various points in the chapter in different contexts, but it’s worth mentioning some other security issues here that could affect mobile device usage. These are things that the user and the organization need to be aware of, and take steps to prevent. This set of issues that mobile devices can encounter includes network connectivity and security issues, issues that are frequently outside of the control of the user or even the technician. Some, however, have to do with device configuration. We’ll look at each of these factors in the upcoming sections. We’ll also talk about security issues that could occur with mobile devices that may involve data loss or unauthorized access.
Connectivity and Data Usage Issues
Network connectivity issues in general that affect all devices have been covered elsewhere within the book. For mobile devices in particular, there are some additional network connectivity issues you should be aware of that you will likely encounter at some point. Some of these have to do with the cellular signal from the mobile device, and others have to do with Wi-Fi and Bluetooth network connections.
One of the most prominent issues plaguing mobile devices is weak signals or signal drops in signals, typically from cellular networks. This issue usually occurs when traveling between carrier coverage areas, or in rural areas where there aren’t enough cell towers. There isn’t much you can do to troubleshoot this, except monitor it. There are cellular signal boosters you can purchase, but these are of dubious value in some situations. Usually these are effective when the user stays in a location that’s far from the cell tower, and typically aren’t very effective while the user is actively traveling.
Another issue that typically comes from cellular networks is slow data speeds. If the device is between geographic cells, or farther away from cell towers, data speeds may get slower. Also, roaming between carriers may cause slow data speeds, as some carriers may limit data rates for nonsubscribers.
In addition to cellular issues that can cause slow data speeds, there also performance issues on the device itself that may cause an appearance of slow data connectivity. Most of these have been discussed already, but include high resource utilization, such as CPU and RAM usage, and a device’s struggle to maintain a solid network connection.
Yet another issue that users may encounter doesn’t necessarily affect connectivity, but it may affect their ability to use cellular data services. This may happen when a user exceeds their data usage limits set by the carrier. CompTIA calls this data transmission overlimit. Typically a user will be notified, via e-mail or text message, before this happens, but they may not notice it. Some carriers may restrict or stop cellular data usage beyond the preset limits. The biggest problem with exceeding the data transmission limits set by the carrier, however, is that any additional data usage beyond those limits is charged to the user at a much higher cost. This will cause the user’s bill to go up significantly, and if it is a company-owned device, will cause the company’s expenses to go up. In this case, the user or the company may consider raising the data limits, albeit at a modest increase in cost. Another solution is to disable cellular data usage in the configuration settings of the device (see Figure 26-14).
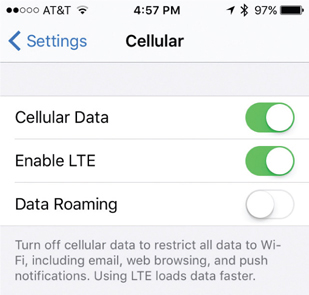
Figure 26-14 Option to disable cellular data in iOS
Unauthorized Connections
A major security issue is unintended network connections, such as those that would apply to cellular, Wi-Fi, and Bluetooth networks. Unintended cellular network connections aren’t common, since these are preprogrammed into the phone by the carrier, and periodically updated, but there is a technique called tower spoofing that we should discuss here. Tower spoofing involves setting up equipment that can spoof a carrier’s tower and infrastructure and cause a cellular device to use it instead of the normal tower equipment. It requires overpowering the nearest legitimate cell signal, causing the cellular device to lock onto it instead. Equipment used in tower spoofing can also be used to eavesdrop on any conversation, even if it is encrypted. In some cases, the equipment can be used to fool the device into turning off encryption completely.
Just as hackers have been using this technique for a few years, law enforcement officials have been reportedly using it as well. Since 2010, there have been numerous court cases highlighted in the media questioning the admissibility of evidence obtained from cell signal interception. A device called a “Stingray” has been reported by the media as used by various federal, state, and local law enforcement agencies to intercept a suspect’s cell traffic using tower spoofing equipment and techniques.
Wi-Fi and Bluetooth connections are typically controlled in the configuration settings for the device. Unintended Wi-Fi and Bluetooth connections can lead to unauthorized access to the device over those connections, allowing data access, theft, and modification by malicious persons. To prevent connections to unauthorized Wi-Fi networks, or pairing with unauthorized Bluetooth devices, you typically only have to configure these options in the configuration settings. This includes settings that tell your mobile device to not automatically connect to unknown Wi-Fi networks, and settings that turn Bluetooth pairing off by default. This will require you to manually connect to a known and trusted Wi-Fi network, and manually pair to a Bluetooth device. The same settings can also be enforced through MDM software to the device through profile settings, if the device is centrally managed.
Unauthorized Data Access
Data access can be an issue with mobile devices, simply because they can be lost or stolen. Typically, device locks and remote wipe can prevent unauthorized users from accessing data on a mobile device. Data can also be leaked through other means, however, such as removable memory storage cards, as well as configuration settings on the device or in different applications. Removable memory cards should be encrypted if they contain sensitive data, so that if they are removed from the device, data can’t be accessed by an unauthorized person. Configuration settings on the device can be set to protect personal data by setting privacy and security settings, and the same settings can be configured in different apps that are allowed to access personal data.
Unauthorized Account Access
Unauthorized account access is not only a big deal for the mobile device itself, but also the organizational network it may connect to. If account credentials are disclosed, or someone is able to access the mobile device, then they have an entry point into an organizational network. VPNs and e-mail connections should be secured on the device, meaning that user names and passwords should not be stored by default, allowing the device to automatically connect to the service in question. This way, if the device is lost or stolen, the services can’t be automatically accessed, since they still require authentication. Unauthorized account access can lead to a malicious person stealing or accessing data not only on the device, but also on the larger network.
Unauthorized Root Access
All mobile operating systems have an all-powerful root account that is normally locked so that no one but the manufacturer of the device may access it. Locking the root account is critical for mobile device security. In order to gain true root access to a mobile device, a user has to either jailbreak (iOS) or root (Android/Windows) the device.
Jailbreaking means that the user installs a program on the device that changes settings on the device that are not normally intended by the manufacturer to be changed. Jail-breaking allows a user to install software not normally allowed, such as apps that don’t come from the manufacturer’s legitimate app store or apps that don’t meet legal or quality requirements of the device manufacturer. Jailbreaking also allows a user to unlock functionality on the device. For example, some iPhones that use AT&T as a service provider can’t be used to tether (which means to allow another device to use their Internet connection). Jailbreaking an iPhone can unlock that functionality and allow other devices to use the iPhone’s connection to the Internet.
Jailbreaking is normally not supported by the manufacturer at all; in fact, jailbreaking typically voids the warranty on a device. Additionally, the manufacturer or service provider, if they detect that jailbreaking has taken place on the device, can prevent the device from connecting to their services. In some cases, the jailbreaking process fails, and the device is rendered non-operational. Usually this can be fixed by restoring the device completely using a backup; however, this also removes the jailbreaking software. Rendering a device non-operational due to jailbreaking is popularly called “bricking” the device. In rare occasions, bricking a device can be permanent and can’t be fixed by restoring from a clean backup.
Rooting an Android or Windows device means that the user now has full administrative access to the lower-level functionality of the device. This is useful in that it allows the user to perform functions on the device that they would not normally be able to, and access functions that may be prohibited by the device manufacturer. Again, as in the case of jailbreaking, this is done to install software that could not otherwise be used on the device, or to unlock functionality from a device. Although none of the popular device vendors condone rooting, in most cases, since the device belongs to the user, the vendors really have no recourse against this practice, except to void the warranty.
Unauthorized Location Tracking
We discussed the benefits of GPS and location tracking earlier, but there are also issues that go with this. The primary one is unauthorized location tracking. Configuration settings on the device and apps may allow a user’s location to be sent to third parties, sometimes without their consent or knowledge. When not in use, the best way to prevent this is to turn off the GPS function, which also saves battery power. Another way is to configure the device and apps that use geotracking in such a way as to prevent unauthorized tracking, if the device allows it. Some apps simply won’t allow geotracking to be turned off, and others simply won’t work without geotracking. Keep in mind that the GPS functionality in a mobile device is not the only way to track its location; cellular networks and Wi-Fi are also used to track locations of devices, although they are not as precise as GPS.
An organization could conceivably geotrack its employees, a process called geofencing, and this might not sit too well with users. Employees might consider this a form of workplace surveillance, and in some cases may rebel somewhat against the organization’s use of geofencing. In the most benign cases, employees may simply leave the device somewhere on a desk and leave the building anyway, or, in the most serious instances, they may seek legal advice and consider bringing litigation against the organization for invasion of privacy. Depending upon how geofencing is used to track employee movement within the bounds of the employer’s property, there may be legal ramifications to using it to track workers. It’s a good idea to research the legal issues of using geofencing to track employees, as well as intelligently discuss the merits and pitfalls from an employee satisfaction perspective so that you can get a realistic view of what benefit your organization may or may not actually accrue from this practice.
Unauthorized Camera and Microphone Activation
There are ways that malicious individuals can remotely activate different features on a mobile device. This may be through app features, or even malware on the device. It can also be accomplished through unauthorized network connections to the device. Two of the features that can be activated remotely that are of serious concern are the built-in camera and microphone. This would allow a malicious person to effectively spy on the mobile device user, through video or by eavesdropping on conversations (or both). The ways to prevent these sorts of actions are by restricting camera and microphone permissions in apps or operating systems (when they allow it), by taking the steps previously described to prevent unauthorized network connections, and by using anti-malware solutions on the device.
Troubleshooting Steps and Tools
Which tools you should use to troubleshoot network, security, app, and device issues vary between the different types of devices, depending upon the operating system being used and the manufacturer of the device. Examples of these tools are the iTunes/iCloud /Apple Configurator, the Windows Phone app for a desktop PC, and different third-party apps that may help you with Android and Microsoft devices. Additionally, some of these providers may also have cloud-based apps that can remotely analyze and help troubleshoot problems with your mobile devices. You can also send diagnostics information files from the devices to the different manufacturers, simply by running diagnostics commands or software apps on the devices.
There are also generic tools that will help you, regardless of the type of device you are working on. These include anti-malware apps and application scanners. Anti-malware apps can scan for, detect, and remove malware from the device. App scanners typically run before an app is installed or updated, and can give you information such as what network connectivity the app requires, what permissions it needs, and what access the app has to certain hardware and functions on your device. App scanners can also tell you what type of data access the app has to your personal information, such as contacts and media files (see Figure 26-15).
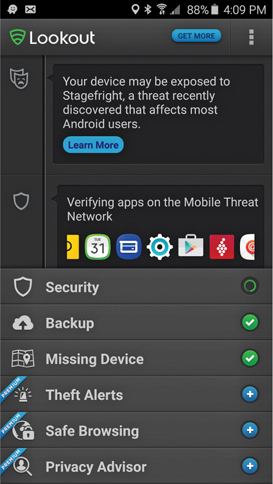
Figure 26-15 Combined anti-malware and app scanner
Always maintaining a current backup of your device is one measure you need to take in case all else fails. Different tools used to perform backups and restore data include iTunes and the various synchronization tools for Android and Microsoft devices; another option is to back up the data to the manufacturer’s user cloud storage, such as Microsoft OneDrive or Apple iCloud.
Chapter Review
Questions
1. Which of the following would be a legitimate reason a mobile device is running slowly?
A. Incorrect calibration
B. RAM too slow
C. Lack of storage space
D. Incorrect version of application
2. Patty has both Gmail and a traditional (SMTP/POP3) e-mail account. She wants to consolidate the traditional account into her Gmail account. Where does she do this? (Select two.)
A. In the Gmail app
B. In the mobile device’s connection settings
C. In the traditional e-mail server’s settings
D. This happens automatically on all mobile devices
3. Pamela decides to add a traditional e-mail app to get her e-mail. Which of the following will she most probably need to configure the app? (Select two).
A. Name of her DNS server
B. Name of her IMAP server
C. Name of her DHCP server
D. Name of her SMTP server
4. Joyce notices her GPS map app gives the error “GPS coordinates not available.” What should she try first?
A. Try running another GPS app
B. Stop and start GPS on the mobile device
C. Move to a place where she can get a good GPS signal
D. Update the mobile device’s firmware
5. You’ve lost your iPhone. What would you use to try to find it?
A. iTunes
B. iFind
C. Location Services
D. iCloud
6. Fred wants to play World of Warcraft on his desktop system. He logs in and then the game asks for a code that is generated by an authenticator app on his Android phone. This is an example of:
A. Multifactor authentication
B. Factor authorization
C. Multifactor authorization
D. Factor authentication
7. Jailbreaking an iPhone gives access to:
A. The administrator account
B. The root account
C. The /bin folder
D. The system BIOS
8. A great way to protect data on a removable media card is to
A. Encrypt it
B. Lock it
C. Remove it when unneeded
D. Format it
9. Which mobile operating system requires a third-party software firewall?
A. Android
B. Mac OS X
C. Windows Mobile
D. iOS
10. Users bringing personally owned mobile devices into an enterprise environment is called:
A. Importing
B. CYMK
C. Providing
D. BYOD
Answers
1. C. Lack of storage space would be a legitimate reason a mobile device is running slowly.
2. A, C. She can add an account to her Gmail app and forward the e-mail in the traditional e-mail server’s settings to Gmail.
3. B, D. A traditional e-mail app would need the name of the SMTP server and the name of either the IMAP or POP3 e-mail server.
4. C. Joyce needs to move to a place where she can get a good GPS signal.
5. D. Apple’s iPhone uses the Find My iPhone feature of iCloud.
6. A. Using both a password and a security code is an example of multifactor authentication.
7. B. Jailbreaking is unique to iOS to provide access to the root account.
8. A. A great way to protect data on a removable media card is to encrypt it.
9. A. Only Android requires a third-party software firewall.
10. D. Users bringing personally owned mobile device into an enterprise environment is known as Bring Your Own Device (BYOD).















