Intelligence gathering follows the pre-engagement activities as the second step in a penetration test. Your goals during intelligence gathering should be to gain accurate information about your targets without revealing your presence or your intentions, to learn how the organization operates, and to determine the best route of entry. If you don’t do a thorough job of intelligence gathering, you may miss vulnerable systems or viable attack vectors. It takes time and patience to sort through web pages, perform Google hacking, and map systems thoroughly in an attempt to understand the infrastructure of a particular target. Intelligence gathering requires careful planning, research, and, most importantly, the ability to think like an attacker. At this step, you will attempt to collect as much information about the target environment as possible. This can be an expansive amount of information, and even the most trivial data gathered during this stage can prove useful later on, so pay attention.
Before you begin intelligence gathering, consider how you will record everything you do and the results you achieve. You must remember and record as many details of your penetration test as possible. Most security professionals quickly learn that detailed notes can mean the difference between a successful and a failed penetration test. Just as a scientist needs to achieve reproducible results, other experienced penetration testers should be able to reproduce your work using your documentation alone.
Intelligence gathering is arguably the most important aspect of a penetration test, because it provides the foundation for all work that follows. When recording your work, be methodical, accurate, and precise. And, as stated earlier, be sure that before you fire off your exploits, you have learned all that you can about your target.
The excitement for most people comes in exploiting systems and getting to root, but you need to learn to walk before you can run.
Warning
If you follow the procedures in this chapter, you can actually damage your system and your target’s system, so be sure to set up your test environment now. (For help, see Appendix A.) Many of the examples in these chapters can be destructive and make a target system unusable. The activities discussed in this chapter could be considered illegal if they are undertaken by someone with bad intentions, so follow the rules and don’t be stupid.
By using passive and indirect information gathering, you can discover information about targets without touching their systems. For example, you can use these techniques to identify network boundaries, identify the network maintainers, and even learn what operating system and web server software is in use on the target network.
Open source intelligence (OSINT) is a form of intelligence collection that uses open or readily available information to find, select, and acquire information about a target. Several tools make passive information gathering almost painless, including complex tools such as Yeti and the humble whois. In this section, we’ll explore the process of passive information gathering and the tools that you might use for this step.
Imagine, for example, an attack against http://www.secmaniac.net/. Our goal is to determine, as a part of a penetration test, what systems the company owns and what systems we can attack. Some systems may not be owned by the company and could be considered out of scope and unavailable for attack.
Let’s begin by using Back|Track’s whois lookup to find the names of secmaniac.net’s domain servers.
msf >whois secmaniac.net[*] exec: whois secmaniac.net. . . SNIP . . .Registered through: GoDaddy.com, Inc. (http://www.godaddy.com) Domain Name: SECMANIAC.NET Created on: 03-Feb-10 Expires on: 03-Feb-12 Last Updated on: 03-Feb-10Domain servers in listed order: NS57.DOMAINCONTROL.COM NS58.DOMAINCONTROL.COM
We learn at  that the Domain Name System (DNS) servers are hosted by DOMAINCONTROL.COM, so this is a good example of systems that would not be included in a penetration test because we would have no authority to attack them. In most large organizations, the DNS servers are housed within the company and are viable attack vectors. Zone transfers and similar DNS attacks can often be used to learn more about a network from both the inside and outside. In this scenario, because DOMAINCONTROL.COM is not owned by secmaniac.net, we should not attack these systems and will instead move on to a different attack vector.
that the Domain Name System (DNS) servers are hosted by DOMAINCONTROL.COM, so this is a good example of systems that would not be included in a penetration test because we would have no authority to attack them. In most large organizations, the DNS servers are housed within the company and are viable attack vectors. Zone transfers and similar DNS attacks can often be used to learn more about a network from both the inside and outside. In this scenario, because DOMAINCONTROL.COM is not owned by secmaniac.net, we should not attack these systems and will instead move on to a different attack vector.
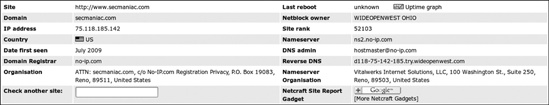
Netcraft (http://searchdns.netcraft.com/) is a web-based tool that we can use to find the IP address of a server hosting a particular website, as shown in Figure 3-1.
Having identified secmaniac.net’s IP address as 75.118.185.142, we do another whois lookup on that IP address:
msf > whois 75.118.185.142
[*] exec: whois 75.118.185.142
WideOpenWest Finance LLC WIDEOPENWEST (NET-75-118-0-0-1)
75.118.0.0 - 75.118.255.255
WIDEOPENWEST OHIO WOW-CL11-1-184-118-75 (NET-75-118-184-0-1)
75.118.184.0 - 75.118.191.255We see from the whois lookup and a quick search that this IP (WIDEOPENWEST) appears to be a legitimate service provider. While the actual subnet range isn’t specifically registered to secmaniac.net or secmaniac.com, we can tell that this site appears to be hosted inside the author’s home, because the IP block appears to be part of a residential range.
To get additional server information, we’ll use Back|Track to leverage nslookup, a tool built into most operating systems, to find information about secmaniac.net.
root@bt:˜#nslookupset type=mx>secmaniac.netServer: 172.16.32.2 Address: 172.16.32.2#53 Non-authoritative answer: secmaniac.net mail exchanger = 10 mailstore1.secureserver.net. secmaniac.net mail exchanger = 0 smtp.secureserver.net.
We see in this listing that the mail servers are pointing to mailstore1.secureserver.net and smtp.secureserver.net. Some quick research on these mail servers tells us that this website is hosted by a third party, which would not be within the scope of our penetration test.
At this point, we have gathered some valuable information that we might be able to use against the target later on. Ultimately, however, we have to resort to active information gathering techniques to determine the actual target IP, which is 75.118.185.142.
Note
Passive information gathering is an art that is not easily mastered in just a few pages of discussion. See the Penetration Testing Execution Standard (PTES; http://www.pentest-standard.org/) for a list of potential ways to perform additional passive intelligence gathering.