Keep prying eyes out of your temporary files.
Many Windows applications create intermediary files while they do their work. They typically store these files in a temporary folder within the current user’s settings directory. These files are usually created world-readable and aren’t always cleaned up when the program exits. How would you like it if your word processor left a copy of the last document you were working on for anyone to come across and read? Not a pretty thought, is it?
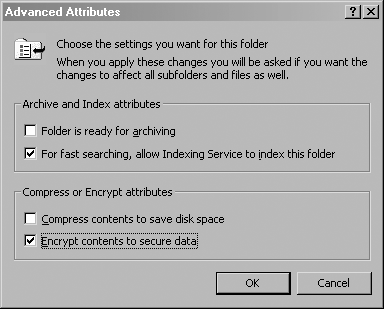
One way to guard against this situation is to encrypt your temporary files folder. Open an Explorer window and go to the C:\Documents and Settings<username>\Local Settings folder, where you should see another folder called Temp. This is the folder that holds the temporary files. Right-click the folder and bring up its Properties dialog. Make sure the General tab is selected, and click the button labeled Advanced. This will bring up an Advanced Attributes dialog, as shown in Figure 2-8. Here you can choose to encrypt the folder.
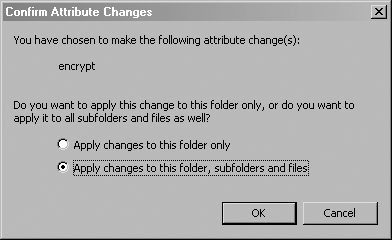
Check the “Encrypt contents to secure data” box and click the OK button. When you have done that, click the Apply button in the Properties dialog. Another dialog (shown in Figure 2-9) opens, asking you whether you would like the encryption to apply recursively.
To apply the encryption recursively, choose the “Apply changes to this folder, subfolders and files” option. This automatically creates a public-key pair if you have never encrypted any files before. Otherwise, Windows will use the public key that it generated for you previously.
When decrypting, Windows ensures that the private keys are stored in nonpaged kernel memory, so that the decryption key will never be left in the paging file. If you’re using an older version of Windows, beware. Windows 2000 uses the DESX algorithm, which is almost useless. However, versions from Windows XP SP1 onward support both 3DES and the much stronger AES.