Protect your users from phishing attacks by deploying SpoofGuard.
Internet scams that use fraudulent web sites and emails to gain sensitive information, known as phishing scams, have become quite the epidemic in the past few years. And, with ever more sophisticated techniques such as IDN spoofing, it has become increasingly harder for the average end user to tell a fake web site from its legitimate counterpart.
To combat phishing, you need to know the signs to look out for. However, even with the best advice on how to spot a phishing scam, if you don’t have foundational knowledge in how the Web operates it can be difficult to remember and spot all the warning signs.
One thing that would certainly help is to have an expert watch over your shoulder while you’re surfing the Web, though that’s obviously infeasible. The next best thing might be to use something like SpoofGuard (http://crypto.stanford.edu/SpoofGuard/).
SpoofGuard is an extension to Internet Explorer produced by the Security Lab at Stanford University. It allows users to spot suspicious sites easily by displaying a simple traffic signal indicator (e.g., green is safe, yellow is suspicious, and red is unsafe) that shows the safety level of the current site.
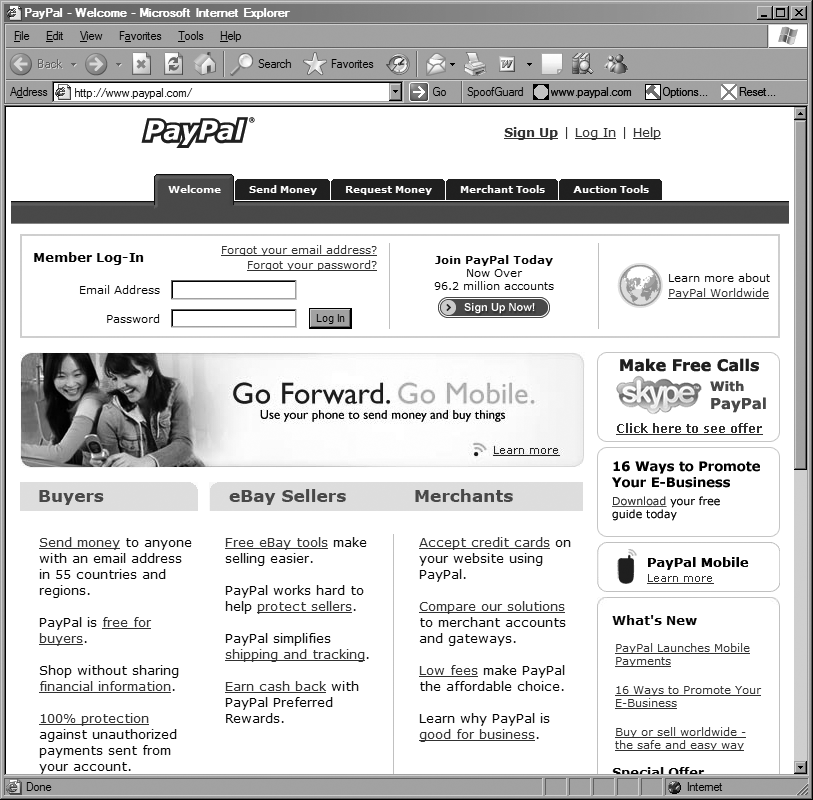
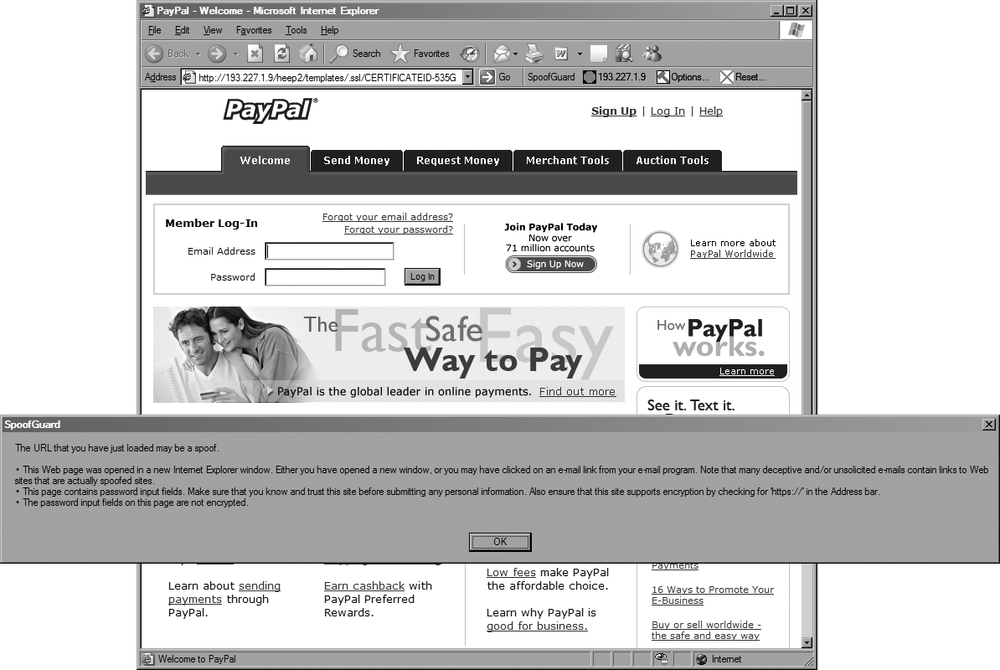
For example, Figure 3-7 shows the legitimate PayPal site (notice the green light on the toolbar), while Figure 3-8 shows a spoofed PayPal site.
Aside from the URL, the spoofed site looks very convincing. However, notice that the light on the toolbar is now red and SpoofGuard has kindly popped up a warning that explains why it thinks that this site is a scam.
Installing SpoofGuard is easy. Simply go to the download page, where both Default and Light versions are available. The Default version will report information back to the team at Stanford to help them gauge what methods are most effective in detecting spoofed web sites. If you don’t want to do this, download the Light version, which doesn’t report anything.
Once you’ve downloaded the installer, execute it and restart Internet Explorer. You should now see a toolbar like one shown earlier. If you don’t, choose View→Toolbars→WarnBar Class.
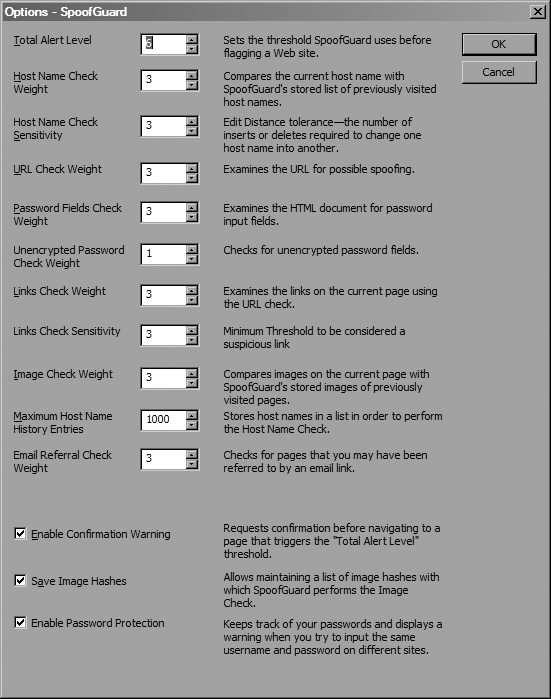
You can begin configuring SpoofGuard by clicking the Options toolbar button, which brings up the window shown in Figure 3-9.
SpoofGuard works by performing a series of checks on the URL and the contents of the web page you are viewing. You can configure each of these tests with a weight in the Options window. When one of the tests returns positive, its weight is added to the total score for the page. If the page’s score exceeds the Total Alert Level you’ve configured, SpoofGuard will warn you.
The first three tests are performed before the browser has even made the page request. When navigating to a site, SpoofGuard first checks the domain to see if it is similar to any domains in the browser history. It does this by computing the distances between the domain of the site being navigated to and the domains of sites in the browser history.
The distance is the number of changes that are required to transform one string into another one. For instance, google.com and googIe.com might appear to be the same in your address bar or on a web page, depending on what font is being used. The distance between these two domain names would be one, so the smaller the distance, the more similar it is to the legitimate site’s domain.
Next, SpoofGuard checks the URL to make sure it does not have a suspicious username embedded in it (e.g., http://www.paypal.com@10.0.0.1/...), because such tricks are often used to fool users into thinking they’re accessing a legitimate web site. In addition, SpoofGuard searches the URL for elements common to hostnames, such as www and commercially used TLDs to ensure that the domain of the site isn’t obscured. Next, it checks to make sure that the URL refers to commonly used port numbers (e.g., port 80 for HTTP and 443 for HTTPS).
The other thing that SpoofGuard checks before loading the page is the referrer field. If this field is blank, either the user has entered the URL manually or she’s followed it from an external application (e.g., an email client). SpoofGuard also checks to see if the referrer is a known web-based email site. If these checks cause SpoofGuard to flag the site as possibly being unsafe, you can choose to be alerted that the site might be unsafe and given the option to block it from loading.
Once a page finishes loading, SpoofGuard then performs a series of checks on the content of the page. It first looks for password fields and, if the page isn’t secured with SSL, displays a warning if it finds one. Next, it analyzes all links on the page, looking for suspicious URLs according to the same criteria it uses for analyzing the page URL before it is loaded. Finally, SpoofGuard generates hashes for the images on the current page and then looks through your browser cache and compares them to images on previously visited sites. If an image on the current page matches one on another site, a warning flag is raised.
In addition to all of these checks, you can configure SpoofGuard to monitor for usernames and passwords being used on more than one web site. SpoofGuard monitors forms for elements that look like usernames and passwords and then combines them to generate a hash. It then compares the hash of the username and password on the page that you’re visiting with previously generated values.
While SpoofGuard is a very powerful tool, it’s not foolproof. Make sure that you educate your users to look out for signs of phishing. With some education and tools like SpoofGuard, they might just stand a chance.