Evade remote OS detection attempts by disguising your TCP/IP stack.
One method to thwart operating-system-detection attempts is to modify the behavior of your system’s TCP/IP stack and make it emulate the behavior of another operating system. This might sound difficult, but it can be done fairly easily in Linux by patching your kernel with code available from the
IP Personality project (http://ippersonality.sourceforge.net). This code extends the kernel’s built-in firewalling system, Netfilter [Hack #44], as well as its user-space component, the
iptables command.
Tip
This currently works for 2.4.x kernels only. However, this kernel version is still in widespread use.
To set up IP Personality, download the package that corresponds to your kernel. If you can’t find the correct one, visit the SourceForge patches page for the project (http://sourceforge.net/tracker/?group_id=7557&atid=307557), which usually has more recent kernel patches available.
To patch your kernel, unpack the IP Personality source distribution and go to the directory containing your kernel source. Then run the patch command:
#cd /usr/src/linux#patch -p1 < \ ../ippersonality-20020819-2.4.19/patches/ippersonality-20020819-linux-2.4.19.diff
If you are using a patch downloaded from the patches page, just substitute your patch command. To verify that the patch has been applied correctly, run this command:
# find ./ -name \*.rej
If the patch was applied correctly, this command should not find any files.
Now that the kernel is patched, you will need to configure the kernel for IP Personality support. As mentioned in “Lock Down Your Kernel with grsecurity” [Hack #13], running make xconfig, make
menuconfig, or even make
config while you are in the kernel source’s directory will allow you to configure your kernel. Regardless of the method you choose, the menu options will remain the same.
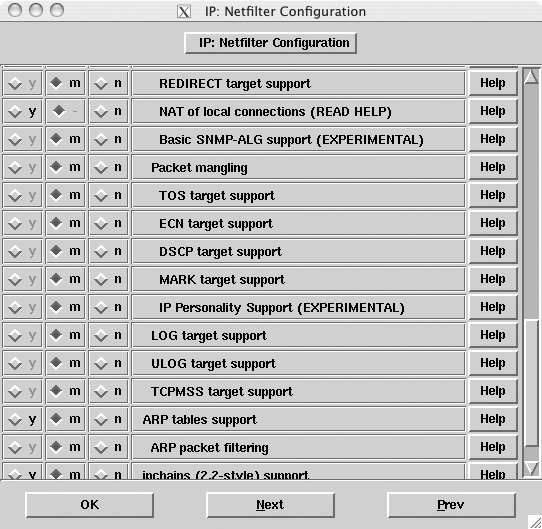
First, be sure that “Prompt for development and/or incomplete code/drivers” is enabled under “Code maturity level options.” Under “Networking Options,” find and enable the option for Netfilter Configuration.
Figure 6-1 shows the list displayed by make xconfig. Find the option labeled IP Personality Support, and either select y to statically compile it into your kernel or select m to create a dynamically loaded module.
After you have configured support for IP Personality, save your configuration. Now, compile the kernel and modules and install them by running the following commands:
#make dep && make clean#make bzImage && make modules#cp arch/i386/boot/bzImage /boot/vmlinuz#make modules_install
Reboot with your new kernel. In addition to patching your kernel, you’ll also need to patch the user-space portion of Netfilter, the
iptables
command. Go to the Netfilter web site (http://www.netfilter.org) and download the version specified by the patch that came with your IP Personality package. For instance, the iptables patch included in ippersonality-20020819-2.4.19.tar.gz is for Netfilter Version 1.2.2.
After downloading the proper version and unpacking it, you will need to patch it with the patch included in the IP Personality package. Then, build and install it in the normal way:
#tar xfj iptables-1.2.2.tar.bz2#cd iptables-1.2.2#patch -p1 < \../ippersonality-20020819-2.4.19/patches/ippersonality-20020427-iptables-\1.2.2.diffpatching file pers/Makefile patching file pers/example.conf patching file pers/libipt_PERS.c patching file pers/pers.h patching file pers/pers.l patching file pers/pers.y patching file pers/pers_asm.c patching file pers/perscc.c #make KERNEL_DIR=/usr/src/linux && make install
This will install the modified iptables command, its supporting libraries, and the manpage under the /usr/local hierarchy. If you would like to change the default installation directories, you can edit the makefile and change the values of the BINDIR, LIBDIR, MANDIR, and INCDIR macros. Be sure to set KERNEL_DIR to the directory containing the kernel sources you built earlier.
If you are using Red Hat Linux, you can replace the iptables
command that is installed by changing the macros to these values:
LIBDIR:=/lib BINDIR:=/sbin MANDIR:=/usr/share/man INCDIR:=/usr/include
In addition to running make install, you might want to create a directory for the operating system personality configuration files. These files are located in the /samples directory within the IP Personality distribution. For example, you could create a directory called /etc/personalities and copy them there.
Before setting up IP Personality, try running Nmap (http://www.insecure.org/nmap/) against the machine to see which operating system it detects:
# nmap -O colossus
Starting nmap 3.48 ( http://www.insecure.org/nmap/ ) at 2003-12-12 18:36 MST
Interesting ports on colossus (192.168.0.64):
(The 1651 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
111/tcp open rpcbind
139/tcp open netbios-ssn
505/tcp open mailbox-lm
631/tcp open ipp
Device type: general purpose
Running: Linux 2.4.X|2.5.X
OS details: Linux Kernel 2.4.0 - 2.5.20
Uptime 3.095 days (since Tue Dec 9 16:19:55 2003)
Nmap run completed -- 1 IP address (1 host up) scanned in 7.375 secondsIf your machine has an IP address of 192.168.0.64 and you want it to pretend that it’s running Mac OS 9, you can run iptables commands like these:
#iptables -t mangle -A PREROUTING -d 192.168.0.64 -j PERS \--tweak dst --local --conf /etc/personalities/macos9.conf #iptables -t mangle -A OUTPUT -s 192.168.0.64 -j PERS \--tweak src --local --conf /etc/personalities/macos9.conf
# nmap -O colossus
Starting nmap 3.48 ( http://www.insecure.org/nmap/ ) at 2003-12-12 18:47 MST
Interesting ports on colossus (192.168.0.64):
(The 1651 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
111/tcp open rpcbind
139/tcp open netbios-ssn
505/tcp open mailbox-lm
631/tcp open ipp
Device type: general purpose
Running: Apple Mac OS 9.X
OS details: Apple Mac OS 9 - 9.1
Uptime 3.095 days (since Tue Dec 9 16:19:55 2003)
Nmap run completed -- 1 IP address (1 host up) scanned in 5.274 secondsYou can, of course, emulate other operating systems that aren’t provided with the IP Personality package. All you need is a copy of Nmap’s operating system fingerprints file, nmap-os-fingerprints. You can then construct your own IP Personality configuration file for any operating system Nmap knows about.