Use Nessus to quickly and easily scan your network for services that are vulnerable to attack.
As
a network administrator, you need to know not only which hosts are on your network and what services they are running, but also if those services are vulnerable to exploits. While a port scanner can show you what machines and ports are reachable on your network, a security scanner such as Nessus (http://www.nessus.org) can tell you if those machines are vulnerable to known exploits.
Unlike a regular port scanner, a security scanner first locates listening services and then connects to those services and attempts to execute exploits against them. It then records whether the exploits were successful and continues scanning until all available services have been tested. The key benefit here is that you’ll know at a glance how your systems perform against known exploits, and thus whether they truly are vulnerable to attack.
With the release of Version 3, Nessus has become a closed-source project. Because of this, the current release and future versions are available only as packages, instead of as source code. However, the old Version 2.8.8 is still available in source form. If you want to use Nessus 2.x, read on. Otherwise, skip to the “Nessus 3.x” section.
If you want to use Version 2.8.8, download the nessus-installer-2.2.8.sh script from the Nessus download page (http://www.nessus.org/download/index.php) and execute it. You will be asked where you want to install Nessus (the default is /usr/local) and prompted for your root password. The script will then create a temporary SUID shell that is accessible only through your user account. This might sound alarming at first, but it tells you the filename for the shell, so you can verify that it is indeed accessible only to you and make sure that it is deleted when the installation is complete.
After the installation has finished, you’ll need to create a Nessus user (not the same thing as a Unix account). Since Nessus uses a client/server model, you’ll also need to generate a certificate so that all communications can be encrypted.
To create a new Nessus user, run nessus-adduser. You’ll be prompted for a name and a password. To create a certificate, you can run nessus-mkcert, or, if you have your own Certificate Authority (CA) [Hack #69], you can use that to create a certificate for Nessus to use. If you do use your own CA, you’ll need to edit nessus.conf to tell it where to look for the CA certificate and the certificate and key that you generated.
The configuration file usually lives in /etc or /usr/local/etc. To tell Nessus the location of its certificates, add lines similar to the following:
cert_file=/etc/ssl/nessus.key key_file=/etc/ssl/nessus.crt ca_file=/etc/ssl/ca.crt
If you generated a certificate/key pair and used a password, you can specify that password here as well:
pem_password=mypassword
After you’ve done that, you can start the Nessus daemon. This is the business end of Nessus and is what actually performs the scans against the hosts on your network.
To start it, run this command:
# /usr/local/sbin/nessusd -D
Now, you can start the Nessus client and connect to the server. Several Nessus clients are available, including a command-line interface, an X11 application, and a Windows client. The figures in this hack show the X11 interface.
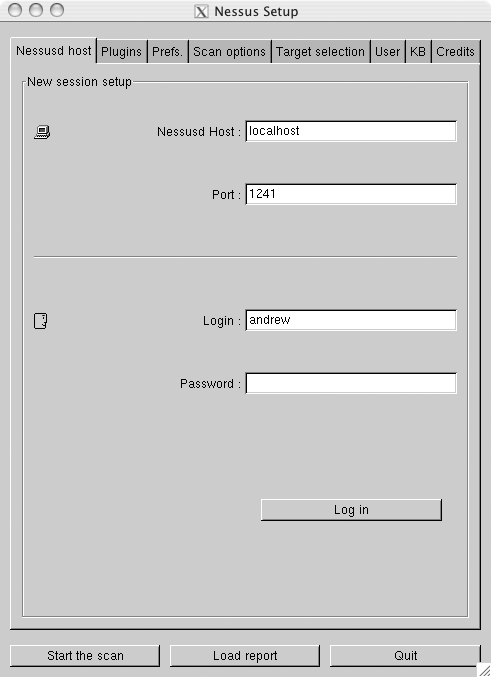
Start the client by simply typing nessus. You should see a window like the one shown in Figure 6-2.
Fill in the information for the user that you created and click the Log In button. You’ll be presented with a dialog that allows you to verify the information contained in the server’s certificate.
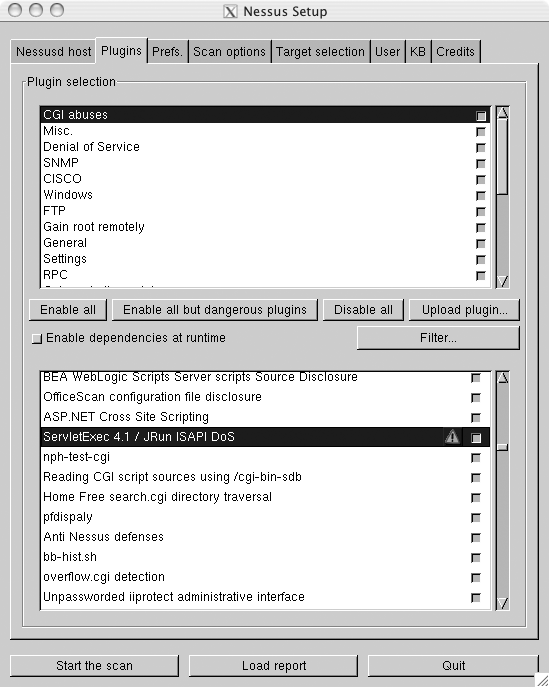
To select which types of vulnerabilities to scan for, click on the Plugins tab to display the screen shown in Figure 6-3.
In the top pane, you can enable or disable types of scans, and in the bottom pane, you can disable individual vulnerability checks that belong to the category selected in the top pane.
Warning
Scans listed in the bottom pane that have an exclamation icon next to them will potentially crash the server against which they’re run. If you want to enable all scans except for these, you can click the “Enable all but dangerous plugins” button. If you’re running Nessus on a noncritical machine, you can probably leave these scans on, but you have been warned!
You’ll probably want to disable several types of scans, unless you need to scan a machine or group of machines that run a wide variety of services; otherwise, you’ll waste time having Nessus scan for services that you aren’t running. For instance, if you want to scan a Solaris system, you might disable CGI abuses, CISCO, Windows, Peer-To-Peer File Sharing, Backdoors, Firewalls, Windows User Management, and Netware plug-ins.
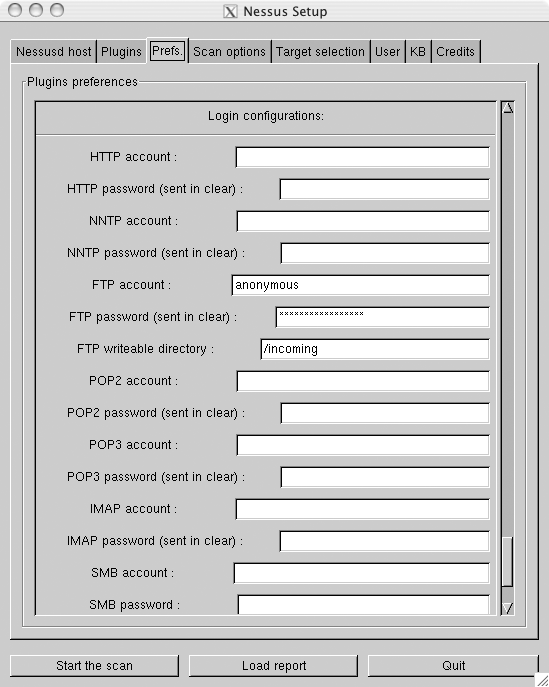
To enable Nessus to more thoroughly test your services, you can supply it with login information for various services. This way, it can actually log into the services that it is testing and have access just like any normal user. You can tell Nessus about the accounts to use with the Prefs tab, shown in Figure 6-4.
In addition, you can tell Nessus to attempt brute-force logins to the services it is scanning. This can be a good test not only of the services themselves, but also of your intrusion detection system (IDS) [Hack #106] and log-monitoring infrastructure.
The “Scan options” tab lets you configure how Nessus conducts its port scans. You can leave most of these settings at their default values, unless you are also checking to see whether Nessus can evade detection by the hosts that you are scanning. For instance, Nessus is configured by default to perform full TCP connect scans and to ping the remote host that it is scanning. You can change this behavior by going to the “Scan options” tab, enabling “SYN scans” instead of “TCP connect,” and disabling the ping. To specify which hosts you want to scan, use the “Target selection” tab.
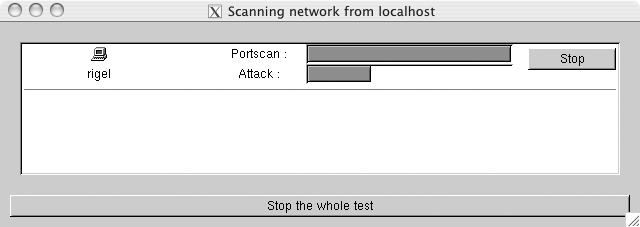
After you’ve made your selections, try scanning a host by clicking “Start the scan” at the bottom of the window. You should now see a window similar to Figure 6-5. In this case, Nessus is performing a scan against a Solaris machine.
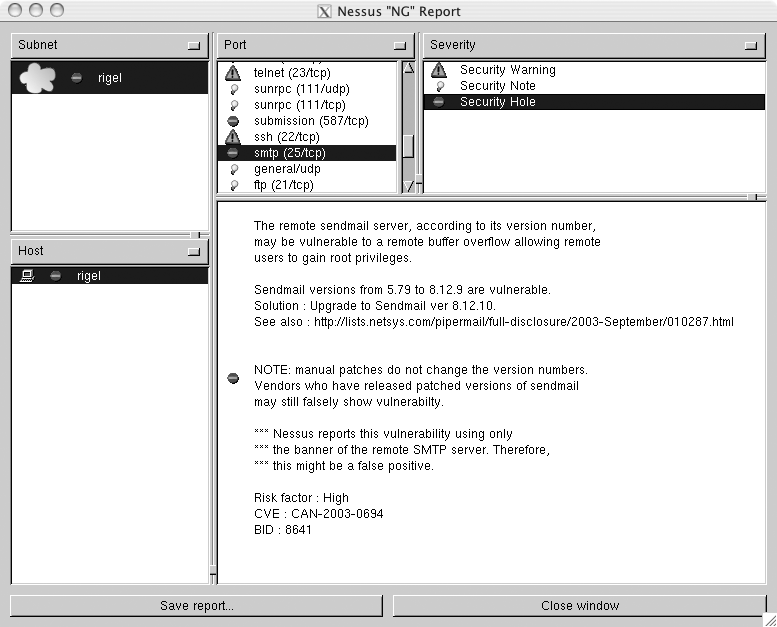
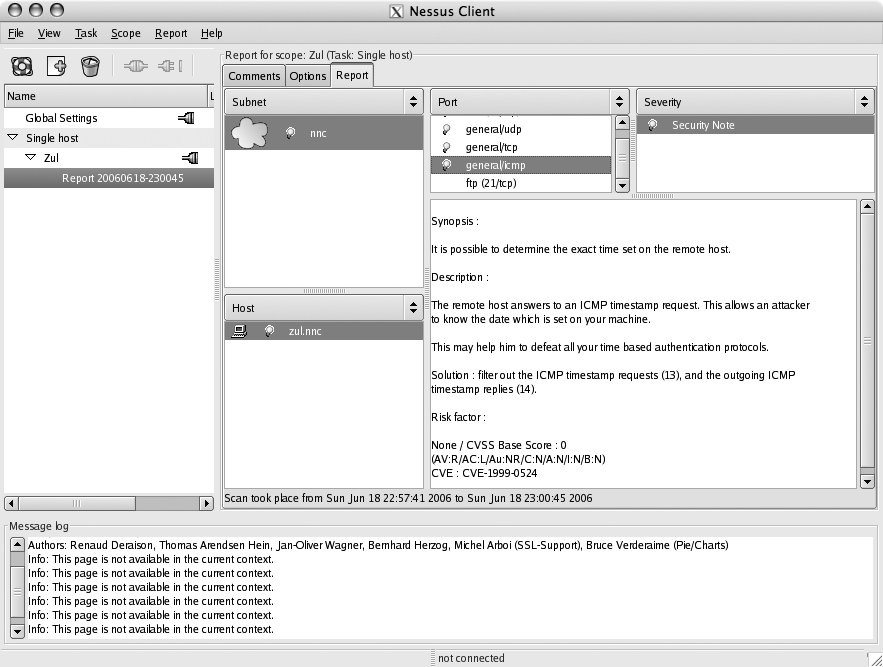
Figure 6-6 shows the results of the scan.
If you scanned multiple subnets, you can select those in the Subnet pane. Any hosts that are in the selected subnet will then appear in the Host pane. Similarly, when you select a host, the list of open ports on it will appear in the Port pane. You can select these to view the warnings, notes, and possible security holes that were found for the selected port.
You can view the information that Nessus provides for these by clicking on them in the Severity pane. Don’t be too alarmed by most of Nessus’s security notes and warnings; they are designed mainly to let you know what services you are running and to tell you if those services present potential vulnerabilities. Security holes are far more serious and should be investigated.
To save the report that you are viewing, click the “Save report” button. Nessus will let you save reports in a variety of formats. If you want to view the report in Nessus again at a later date, use Nessus’s own report format (NBE). To view reports in this format, click the “Load report” button in the main Nessus client window. Additionally, you can save reports in XML, HTML, ASCII, and even LaTeX format.
As mentioned at the beginning of this hack, Nessus 3.0 and later are available only in package form for Linux, FreeBSD, Solaris, and Windows. Download the package appropriate for your system and install it. In order to do this, you’ll have to provide some personal information. You’ll also receive a registration code that can be used to download the latest Nessus plug-ins.
Nessus will install certificates as part of the installation process, so you no longer need to run nessus-mkcert. You can also choose to install your own certificates using the same method used for Nessus 2.x.
Once you’ve installed the package, you’ll need to create a user in the Nessus system (unless you’re using Windows) by running nessus-adduser, which will prompt you for a name and a password. Next, download the plug-ins. Run nessus-fetch, specifying your registration code:
#nessus-fetch --registerYour activation code has been registered properly - thank you. Now fetching the newest plugin set from plugins.nessus.org... Your Nessus installation is now up-to-date. If auto_update is set to 'yes' in nessusd.conf, Nessus will update the plugins by itself.XXXX-XXXX-XXXX-XXXX-XXXX
As mentioned in the output, putting auto_update=yes in your nessusd.conf file instructs Nessus to automatically update its plug-ins, but it should already be set up to update its plug-ins every 24 hours.
Another key difference between Nessus 2.x and 3.x is that the latter doesn’t come with a GUI client (the exception to this is the Windows package). For that, you’ll need to go back to the Nessus site, download the NessusClient package, and install it.
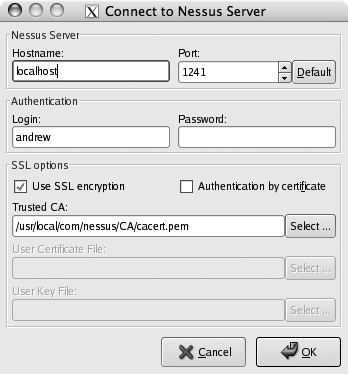
After you’ve installed the NessusClient package, you can launch it by simply typing NessusClient. Then, open the File menu and click Connect. You should be presented with a dialog like the one shown in Figure 6-7, where you can choose what server to connect to and specify your username and password.
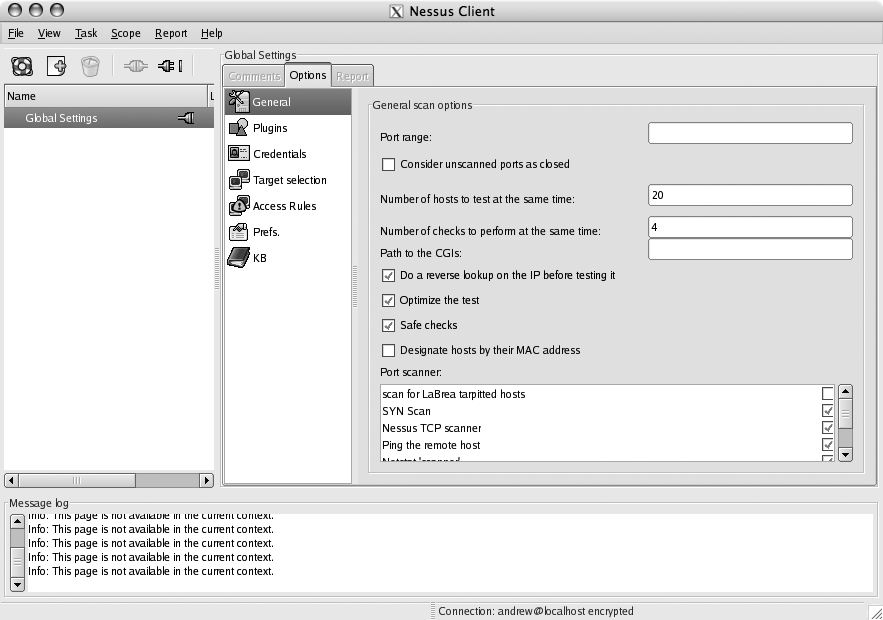
After you’ve connected to the Nessus server, you can configure the global settings that will serve as a basis for all of the scans that you conduct. If you want to limit the ports that are scanned on each host, whether to do TCP connect() scanning or SYN scanning, or any other general scanning engine parameters, click the General icon in the Options tab, as shown in Figure 6-8.
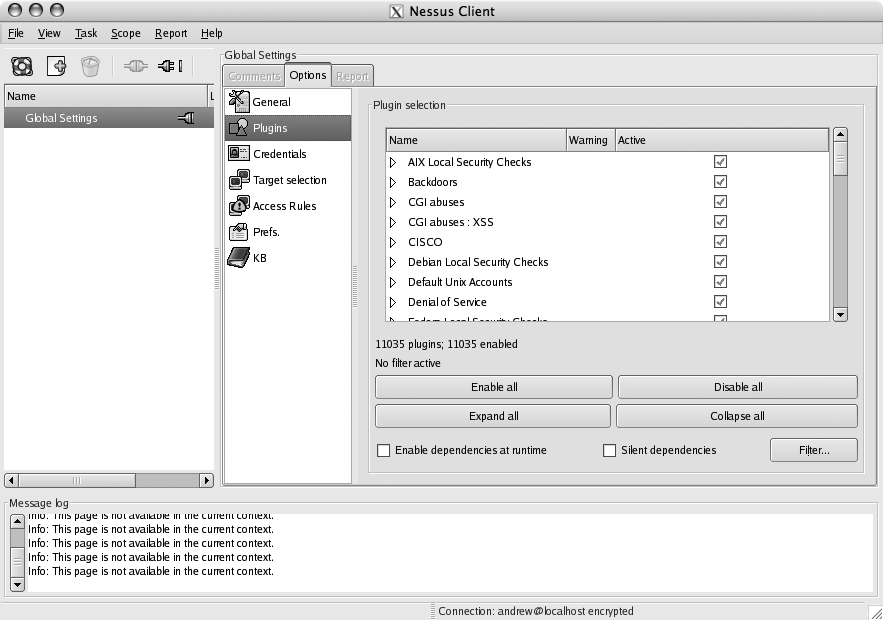
Enable or disable plug-ins by clicking the Plugins icon. As shown in Figure 6-9, Nessus 3 organizes the plug-ins into a categorized tree view, unlike previous versions.
You can disable whole categories of plug-ins by unchecking them. Likewise, you can disable an individual plug-in by using the checkbox next to it.
Warning
As in previous versions of Nessus, plug-ins with an exclamation icon next to them are likely to disrupt service on the device they’re scanning.
After you’re done configuring Nessus’s global settings, the easiest way to start scanning your network is to use the Scan Assistant, which is accessible under the File menu. This is where the new Nessus client departs greatly from the 2.x version. NessusClient uses the concept of tasks and scopes. A task is something like “Scan the local subnet” or “Scan a single host.” When a task is being performed, it has a scope that defines what systems are scanned in order to complete the task. The Scan Assistant prompts you to create a task and then to define a scope. Once that’s been done, you can execute the scan.
After the scan has completed, you’ll see the task and scope that the Scan Assistant created in the left pane of NessusClient. Here, you can also view reports of the current and past scans, as shown in Figure 6-10, in just the same way as in previous versions of Nessus.
If you want to perform the scan again, simply open the Scope menu and click Execute. You can also modify the scan settings for an individual scope by selecting it and then changing any settings, just as you would for the Global Settings.
While Nmap [Hack #66] is probably the champion of network reconnaissance, Nessus goes even further to demonstrate whether your own services are vulnerable to known attacks. Of course, new exploits surface all the time, so it’s important to keep your Nessus plug-ins up-to-date. Using Nessus, you can protect your own services by attempting to break into them before the bad boys do.