See who’s doing what on your network over time with ntop.
If you’re
looking for real-time network statistics, check out the terrific ntop tool (http://www.ntop.org), a full-featured protocol analyzer with a web frontend, complete with SSL and graphing support. ntop isn’t exactly lightweight (the precise amount of resources required depends on the size of your network and the volume of network traffic), but it can give you a very nice picture of who’s talking to whom on your network.
ntop needs to run initially as root, to throw your interfaces into promiscuous mode and start capturing packets, but it then releases its privileges to a user that you specify. If you decide to run ntop for long periods of time, you’ll probably be happiest running it on a dedicated monitoring box (with few other services running on it, for security and performance reasons).
Here’s a quick reference on how to get ntop up and running. First, create an ntop user and group:
#groupadd ntop#useradd -c "ntop user" -d /usr/local/etc/ntop -s /bin/true -g ntop ntop
Then, unpack and build ntop per the instructions in docs/BUILD-NTOP.txt. After ntop has finished compiling, install it by running make install as root. During the installation process, a directory for ntop to store its databases in will be created. If you didn’t use the --prefix option when running configure, this directory should be /usr/local/var/ntop. It will be created as root during the install, so you’ll need to change its owner to the user you’ll be running ntop as in order for ntop to be able to write to it.
ntop will also copy a self-signed certificate to /usr/local/etc/ntop/ntop-cert.pem as part of the install process, so that you can securely access its web interface. Note that the default SSL key will not be built with the correct hostname for your server, so you’ll probably want to generate your own SSL certificate and key pair [Hack #69].
Now, you’ll need to set an administrative password to be used when configuring ntop through its web interface:
# ntop -A -u ntop
Fri May 5 22:03:27 2006 NOTE: Interface merge enabled by default
Fri May 5 22:03:27 2006 Initializing gdbm databases
ntop startup - waiting for user response!
Please enter the password for the admin user:
Please enter the password again:
Fri May 5 22:03:31 2006 Admin user password has been setFinally, run ntop as a daemon, and start the SSL server on your favorite port (4242, for example):
# ntop -u ntop -W4242 -d
By default, ntop also runs a standard HTTP server on port 3000. You should seriously consider locking down access to these ports, either at your firewall or by using command-line iptables rules [Hack #44].
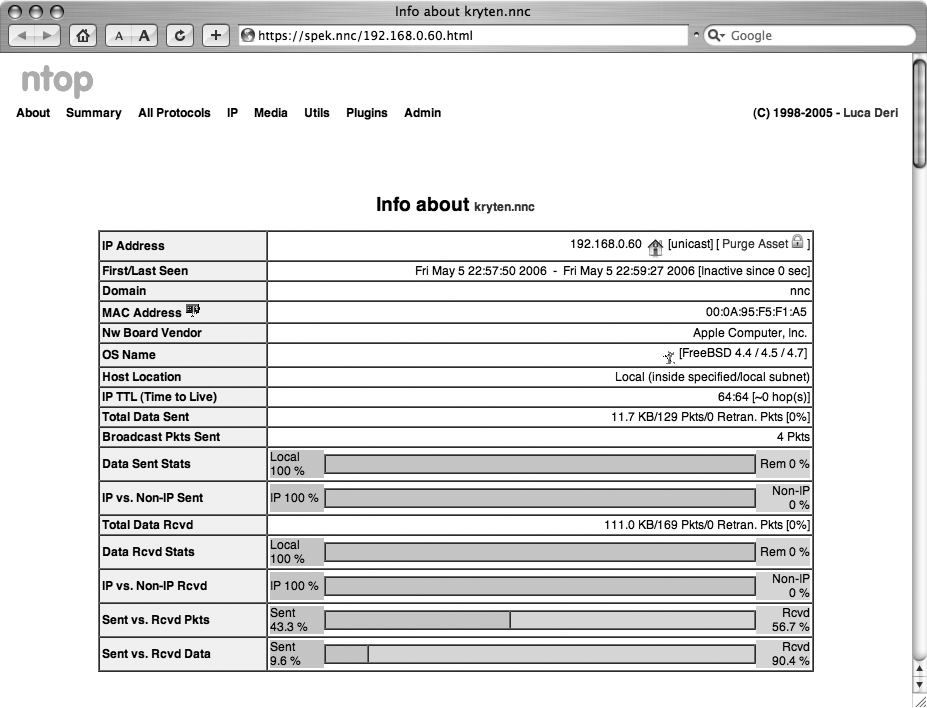
Let ntop run for a while, and then connect to https://your.server.here:4242/. You can find out all sorts of details about what traffic has been seen on your network, as shown in Figure 9-3.
While tools like tcpdump and Ethereal give you detailed, interactive analyses of network traffic, ntop delivers a wealth of statistical information in a very slick and easy-to-use web interface. When properly installed and locked down, it will likely become a favorite tool in your network analysis tool chest.
Rob Flickenger