Use honeyd to fool would-be attackers into chasing ghosts.
As the saying goes, you’ll attract more flies with honey than with vinegar. (I’ve never understood that saying; who wants to attract flies, anyway?) A honeypot is used to attract the “flies” of the Internet: script kiddies and hacker wannabes who have nothing better to do with their time than scan for vulnerable hosts and try to attack them. A honeypot does this by pretending to be a server running vulnerable services, while in fact collecting information about the attackers who think themselves so clever.
Whether you want to simulate one or one thousand vulnerable network hosts,
honeyd (http://www.honeyd.org) makes the job as simple as editing a configuration file and running a daemon. The honeyd daemon can simulate thousands of hosts simultaneously and lets you configure what operating system each host will appear as when scanned with operating-system-detection tools such as Nmap [Hack #66].
Each system that honeyd simulates will appear to be a fully functioning node on the network. Besides simply creating hosts that respond to pings and traceroutes, honeyd also lets you configure what services each host appears to be running. You can either use simple scripts to emulate a given service or have honeyd act as a proxy and forward requests to another host for servicing.
As a daemon that has extensive capabilities in mimicking other daemons, honeyd has several prerequisites you’ll need to install before building the daemon itself:
libpcap, PCRE, Readline, Zlib, and Python should be available with most Linux and BSD flavors. You can easily install any of these prerequisites by downloading and unpacking them, running./configure && make, and then running make install as root.
After you’ve installed the libraries, install honeyd the same way. Then, copy the service emulation scripts from the source distribution to somewhere more permanent (e.g., /usr/local/share/honeyd/scripts). Only a few scripts come with honeyd itself, but additional service emulation scripts are available on honeyd’s contributions page (http://www.honeyd.org/contrib.php).
Once you’ve installed honeyd , you’ll need to create a configuration file that defines the types of operating systems and services honeyd will emulate and the IP addresses to which honeyd will respond. First, create some operating system templates:
### Windows computers create windows-web set windows-web personality "Microsoft Windows Millennium Edition (Me), Windows 2000 Professional or Advanced Server, or Windows XP" set windows-web default tcp action reset set windows-web default udp action reset set windows-web default icmp action open add windows-web tcp port 80 "perl scripts/win2k/iisemulator-0.95 /iisemul8.pl" add windows-web tcp port 139 open add windows-web tcp port 137 open add windows-web tcp port 5900 "sh scripts/win2k/vnc.sh" add windows-web udp port 137 open add windows-web udp port 135 open create windows-xchng set windows-xchng personality "Microsoft Windows Millennium Edition (Me), Windows 2000 Professional or Advanced Server, or Windows XP" set windows-xchng default tcp action reset set windows-xchng default udp action reset set windows-xchng default icmp action open add windows-xchng tcp port 25 "sh scripts/win2k/exchange-smtp.sh" add windows-xchng tcp port 110 "sh scripts/win2k/exchange-pop3.sh" add windows-xchng tcp port 119 "sh scripts/win2k/exchange-nntp.sh" add windows-xchng tcp port 143 "sh scripts/win2k/exchange-imap.sh" add windows-xchng tcp port 5900 "sh scripts/win2k/vnc.sh" add windows-xchng tcp port 139 open add windows-xchng tcp port 137 open add windows-xchng udp port 137 open add windows-xchng udp port 135 open ### Solaris create sol-mail set sol-mail personality "Sun Solaris 9" set sol-mail default tcp action reset set sol-mail default udp action reset set sol-mail default icmp action open add sol-mail tcp port 110 "sh scripts/pop3.sh" add sol-mail tcp port 25 "sh scripts/smtp.pl" add sol-mail tcp port 22 open add sol-mail tcp port 143 open add sol-mail tcp port 993 open
Then bind them to the IP addresses that you want to use:
bind 192.168.0.210 windows-web bind 192.168.0.211 windows-xchng bind 192.168.0.212 sol-mail
Save this configuration file in a good place (e.g., /usr/local/share/honeyd/honeyd.conf).
Instead of configuring IP aliases on your NIC for each IP address listed in your configuration file, you can use
arpd (http://www.honeyd.org/tools.php) to respond to the IP addresses. You can install arpd by running ./configure && make and then make install as root. However, if you’re using a recent version of GCC, you might encounter the following error:
arpd.c: In function 'arpd_lookup': arpd.c:285: error: syntax error before string constant arpd.c:294: error: syntax error before string constant arpd.c:297: error: syntax error before string constant arpd.c: In function 'arpd_recv_cb': arpd.c:426: error: syntax error before string constant make: *** [arpd.o] Error 1
This is because, as of Version 3.4 of the compiler, it’s no longer possible to concatenate __FUNCTION__ with other strings. To fix this problem, see http://seclists.org/lists/honeypots/2005/Jul-Sep/0035.html for a patch to arpd.c.
After you have installed arpd and honeyd, you can start them:
#arpd 192.168.0.210-192.168.0.212#cd /usr/local/share/honeyd#honeyd -p nmap.prints -x xprobe2.conf -a nmap.assoc -0 pf.os -f honeyd.confhoneyd[5861]: started with -p nmap.prints -x xprobe2.conf -a nmap.assoc -0 pf.os -f honeyd.conf honeyd[5861]: listening on eth0: (arp or ip proto 47 or (ip )) and not ether src 00:0c:29:e2:2b:c1 Honeyd starting as background process
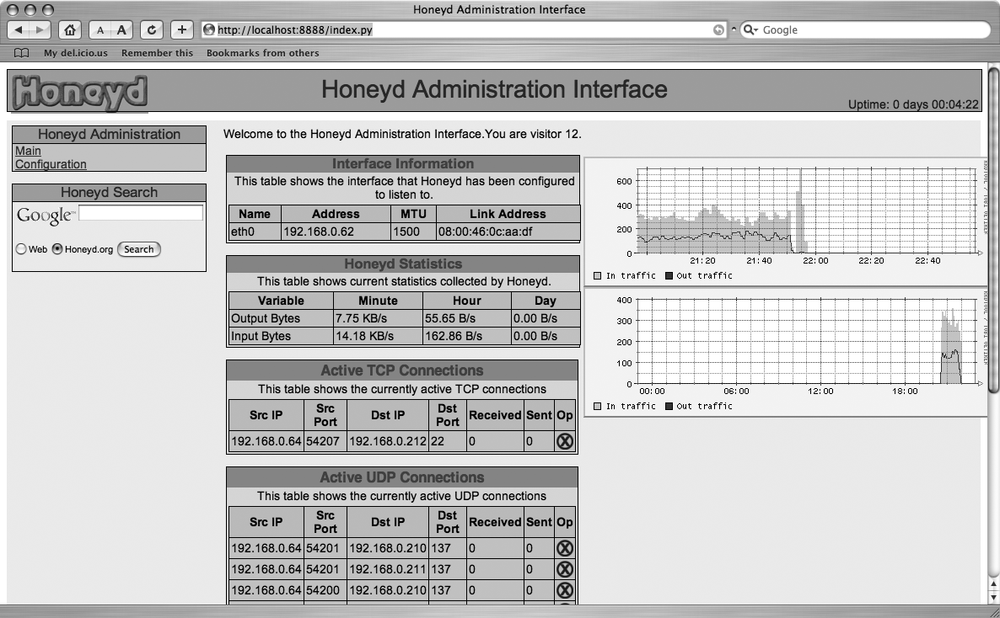
The most recent version of honeyd now includes a built-in web server, which lets you view the current status of your honeynet as well as its configuration, as shown in Figure 11-13.
The web interface allows you to view active TCP and UDP connections along with bandwidth statistics for your honeynet. In addition, you can view the settings for the different virtual hosts you have configured. If you don’t want to use the web interface, you can use the --disable-webserver option when starting honeyd.
Now, try running Nmap on the IP addresses that honeyd is handling:
# nmap -sS -sU -O 192.168.0.210-212
Starting nmap 3.70 ( http://www.insecure.org/nmap/ ) at 2006-05-06 15:45 MDT
Interesting ports on 192.168.0.210:
(The 3132 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
80/tcp open http
135/udp open|filtered msrpc
137/tcp open netbios-ns
137/udp open|filtered netbios-ns
139/tcp open netbios-ssn
5900/tcp open vnc
MAC Address: 08:00:46:0C:AA:DF (Sony)
Device type: general purpose
Running: Microsoft Windows 95/98/ME|NT/2K/XP
OS details: Microsoft Windows Millennium Edition (Me), Windows 2000 Professional or Advanced Server, or Windows XP
Interesting ports on 192.168.0.211:
(The 3129 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
25/tcp open smtp
110/tcp open pop3
119/tcp open nntp
135/udp open|filtered msrpc
137/tcp open netbios-ns
137/udp open|filtered netbios-ns
139/tcp open netbios-ssn
143/tcp open imap
5900/tcp open vnc
MAC Address: 08:00:46:0C:AA:DF (Sony)
Device type: general purpose
Running: Microsoft Windows 95/98/ME|NT/2K/XP
OS details: Microsoft Windows Millennium Edition (Me), Windows 2000 Professional or Advanced Server, or Windows XP
Interesting ports on 192.168.0.212:
(The 3133 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
110/tcp open pop3
143/tcp open imap
993/tcp open imaps
MAC Address: 08:00:46:0C:AA:DF (Sony)
Device type: general purpose
Running: Sun Solaris 9
OS details: Sun Solaris 9
Uptime 0.080 days (since Sat May 6 13:50:40 2006)You can certainly see that honeyd fools Nmap. You’ll notice that the MAC address reported for each host is the same as the network interface of the host on which honeyd is being run, though, which is a dead giveaway that something fishy is going on. This can be fixed by assigning a MAC address to each of the host templates in the configuration file:
create sol-mail set sol-mail personality "Sun Solaris 9" set sol-mail ethernet "08:00:20:23:45:EE" set sol-mail default tcp action reset set sol-mail default udp action reset set sol-mail default icmp action open add sol-mail tcp port 110 "sh scripts/pop3.sh" add sol-mail tcp port 25 "sh scripts/smtp.pl" add sol-mail tcp port 22 open add sol-mail tcp port 143 open add sol-mail tcp port 993 open
Now, run Nmap again:
# nmap -sS -sU -O 192.168.0.212
Starting nmap 3.70 ( http://www.insecure.org/nmap/ ) at 2006-05-06 15:52 MDT
Interesting ports on 192.168.0.212:
(The 3133 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
110/tcp open pop3
143/tcp open imap
993/tcp open imaps
MAC Address: 08:00:20:F9:6A:F3 (SUN Microsystems)
Device type: general purpose
Running: Sun Solaris 9
OS details: Sun Solaris 9
Uptime 0.023 days (since Sat May 6 15:18:57 2006)
Nmap run completed -- 1 IP address (1 host up) scanned in 7.394 secondsOne thing to note is that if you specify a MAC address for a host template, you do not need to have arpd answering ARP requests for the IP address associated with it. honeyd will handle this for you.
Everything has appeared to be realistic so far, but what happens when you try to access one of the services that are purportedly running? Try connecting to port 25 of the fake Windows mail server:
$ telnet 192.168.0.211 25
Trying 192.168.0.11...
Connected to 192.168.0.11.
Escape character is '^]'.
220 bps-pc9.local.mynet Microsoft ESMTP MAIL Service, Version: 5.0.2195.5329 ready at
Mon Jan 12 12:55:04 MST 2004
EHLO kryten
250-bps-pc9.local.mynet Hello [kryten]
250-TURN
250-ATRN
250-SIZE
250-ETRN
250-PIPELINING
250-DSN
250-ENHANCEDSTATUSCODES
250-8bitmime
250-BINARYMIME
250-CHUNKING
250-VRFY
250-X-EXPS GSSAPI NTLM LOGIN
250-X-EXPS=LOGIN
250-AUTH GSSAPI NTLM LOGIN
250-AUTH=LOGIN
250-X-LINK2STATE
250-XEXCH50}
250 OKPretty effective at first glance, isn’t it? If you’d like to specify some real services for attackers to play with, you can use the
proxy keyword to forward any port to a port on another machine. For example, the following line will forward SSH requests from our imaginary Linux host to the machine at 192.168.0.100:
add linux tcp port 22 proxy 192.168.0.100:22
Proxying works especially well when utilizing honeypots created from full-blown systems. This enables you to create a handful of dedicated honeypot machines and then set up honeyd to act as a frontend to them. The end result is that you appear to have more vulnerable systems than you actually have, and you can monitor any intruder’s activities in more detail in the richer user environment.
In addition to running the service emulation scripts, honeyd can limit inbound or outbound bandwidth, or even slow down access to a particular service. This can be used to tie up spammers’ resources, by holding open an apparently open mail relay. The possibilities provided by honeyd are limited only by your imagination and the time you’re willing to spend building your virtual fly-catching network.