In September 2000, the Colorado-based Privacy Foundation[105] released a report on a new technology for monitoring Internet users, which the foundation called web bugs . Although the use of this technology had been widely known in advertising circles, it had not previously been publicized to the larger community of Internet users.
Web bugs are small graphic images placed on web pages or in email messages to facilitate third-party tracking of users and collection of statistics. A typical web bug consists of a 1-pixel-by-1-pixel transparent GIF, making it invisible to the unassisted eye. To see a web bug, you must view the source of an HTML page or email message.
According to the foundation’s Web Bug FAQ:[106]
The word bug is being used to denote a small, eavesdropping device. It is not a euphemism for a programming error.... Rather than the term `Web bugs,’ the Internet advertising community prefers the more sanitized term `clear GIF.’ Web bugs are also known as `1-by-1 GIFs,’ `invisible GIFs,’ and `beacon GIFs.’
Here are two web bugs that the Privacy Foundation found on the Intuit’s home page for Quicken.COM:
<img src="http://ad.doubleclick.net/ad/pixel.quicken/NEW" width=1 height=1 border=0> <IMG WIDTH=1 HEIGHT=1 border=0 SRC="http://media.preferences.com/ping?ML_SD=IntuitTE_Intuit_1x1_RunOfSite_Any&db_ afcr=4B31-C2FB-10E2C&event=reghome&group=register&time=1999.10.27.20.5 6.37">
The first web bug causes a single 1 x 1 image to be fetched from the Doubleclick advertising server ad.doubleclick.net. This bug alerts Doubleclick to each individual that views the Quicken.COM home page. Doubleclick has built a sophisticated system for monitoring individuals who view Doubleclick’s advertisements; this web bug allows Intuit to use Doubleclick’s monitoring system without the need to first show a banner advertisement.
The second web bug fetches a 1 x 1 image from the MatchLogic media.preferences.com server. This bug is slightly more interesting in that it apparently sends to MatchLogic a unique user identification, similar to what might be found in a cookie. This web bug might allow Intuit and MatchLogic to knit together their two disparate user databases.
Using two web bugs allows Intuit to compare Doubleclick’s tracking and monitoring results with those of MatchLogic. Both, of course, can also be compared with the results that Intuit gets from analyzing its own log files.
Web bugs do not need to be 1 x 1 pixel graphics. Any image or other content that is pulled from a third-party web server can be used by a web site to monitor its users. Mainly, web bugs are a form of outsourced web site monitoring. They impact privacy by introducing a third party into a consumer web site relationship. Potentially, web bugs also allow movements between multiple web sites to be correlated, although the same can be done through banner advertisements or by the sharing of log files.
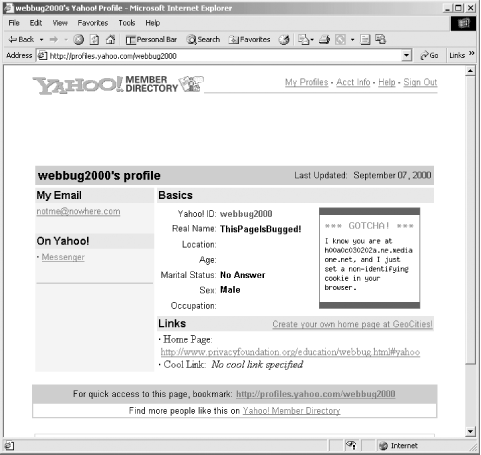
Web bugs can be placed on any piece of HTML. For example, the Privacy Foundation created a Yahoo user called webbug2000 and placed a web bug in the fictitious user’s Yahoo Profile (see Figure 8-5).
Web bugs can be used in HTML email messages to determine whether a person reads an email. When the email message is viewed, the web bug is fetched from the remote server. If each web bug is given a unique identifier and causes a cookie to be downloaded, then an email-based web bug can also be used to determine if an email message is forwarded from one person to another.
Tip
Email-based web bugs are only active if the email message is read with a mail client that can display HTML messages, and even then, only if that computer is connected to the Internet.
Here’s an example of two email-based web bugs the Privacy Foundation discovered:
<img width='1' height='1' src="http://www.m0.net/m/logopen02.asp?vid=3&catid=370153037&email=SMITHS%40tiac.net" alt=" "> <IMG SRC="http://email.bn.com/cgi-bin/flosensing?x=ABYoAEhouX">
Web bugs can be placed in HTML Usenet messages to determine how many times a Usenet message is viewed.
Web bugs can also be placed in Microsoft Word files. This is possible because Microsoft Word allows images downloaded from web pages to be pasted directly into Word documents. Each time the Word document is opened, the image is downloaded anew. This in turn allows the web bug to track the usage and the movement of the Word document.
According to the Privacy Foundation, companies use web bugs to accomplish the following tasks:
Gather viewing and usage statistics for a particular page.
Correlate usage statistics between multiple web sites.
Profile users of a web site by gender, age, Zip code, and other demographics.
Transfer personally identifiable information from the web site directly to an Internet marketing company. This transfer would be accomplished with a web bug URL that contains the personal information that the company wishes to transfer.
Transfer search strings from a search engine to a marketing company.
Verify the statistics reported by a banner advertising company, to gauge the effectiveness of different banner advertisements.
Have third-party providers prepare web usage statistics for web sites that do not have the technical capability to prepare their own statistics.
“Cookie sync,” which is for synchronizing personal information in two different databases.
See if users have enabled JavaScript, Java, ActiveX, and other technologies.
Check if email messages are actually read and, if they are read, to see if they are forwarded.