Invented by Brendan Eich and originally called LiveScript, JavaScript is a programming language that Netscape developed to add forms validation, other local calculations, and some forms of interaction to web browsers. JavaScript programs reside in HTML files, usually surrounded by <script> tags (so that they will be recognized by JavaScript-enabled browsers) and HTML comment tags (so that they will be ignored by browsers that do not understand JavaScript).
Full JavaScript allows HTML files to command the browser. JavaScript programs create new windows, fill out fields in forms, jump to new URLs, process image maps locally, change the HTML content of the page itself, compute mathematical results, and perform many other functions. JavaScript can also modify the appearance of web browsers, making visual elements of the web browser appear or disappear dynamically. JavaScript makes messages appear in the status line of web browsers—some of the earliest JavaScript applications displayed moving banners across the web browser’s status line. Early versions of JavaScript could even reprogram a browser’s history, although this feature has now been disabled. (It was abused by pornographic web sites.)
A web page can contain multiple JavaScript sections, called scripts . The scripts are programmed to run when the web page loads, when a button or link on the page is touched or clicked with the mouse, or after a certain amount of time has passed. Scripts can also access elements on the page using the Document Object Model (DOM).
Unlike Java, JavaScript code is interpreted directly by the web browser. This fact has made it difficult to filter JavaScript out of web pages—in many cases, it is possible to send HTML to a web browser that appears to be free of JavaScript, but that actually contains JavaScript programs.
Here is a simple HTML file that contains an embedded
JavaScript program. The HTML comment characters (<!-- and -->) are largely anachronistic. They
are present so that a browser that does not understand the
<script> and </script> tags will simply treat the
JavaScript as a comment and not display the program. These days,
many JavaScript developers are dropping the comment characters, as
the vast majority of browsers in use understand the <script>
tag (although they may ignore the embedded JavaScript):
<html>
<head>
<title>Hello World!</title>
<body>
This is a JavaScript Demo
</body>
<script language="JavaScript">
<!--
alert("Hello World!");
-->
</script>
</html>When this program runs, it displays a little window that says “Hello World!”, as shown in Figure 13-9.
JavaScript programs can interact with forms, frames, and other objects on a web page using the browser’s Document Object Model. Briefly, DOM exposes specific objects and functionality of the browser to a running JavaScript program. JavaScript can also be used to control a browser—for example, JavaScript can be used to open new windows, click the browser’s Back button, and even access the browser’s history (but only the history of the current site).
JavaScript is an amazing language; the more you study it, the more things you find.[142] For example, if you wish to draw a graph in your HTML file, you can do so with a very simple piece of JavaScript in your program and the JavaScript Graph Builder library created by Netscape Engineer Michael Bostock. Here is an example of the JavaScript needed to create a simple graph of coin flipping results:
<html><head>
<title>Coin Flipping Results</title>
<body><CENTER>
<SCRIPT LANGUAGE="JavaScript1.2" SRC="graph.js"></SCRIPT>
<SCRIPT LANGUAGE="JavaScript">
if(parseInt(navigator.appVersion) >= 4) {
var g = new Graph(300,200);
g.addRow(100,90,110,101,102,103);
g.addRow(100,90,85,93,98,102);
g.scale = 50;
g.setDate(7,11,2001);
g.title = "Daily Coin Flipping Results";
g.xLabel = "Date";
g.yLabel = "Heads";
g.setLegend("Penny","Quarter");
g.build( );
} else {
document.writeln("<b>This graph requires a Netscape version 4 or higher browser to
display</b>");
}
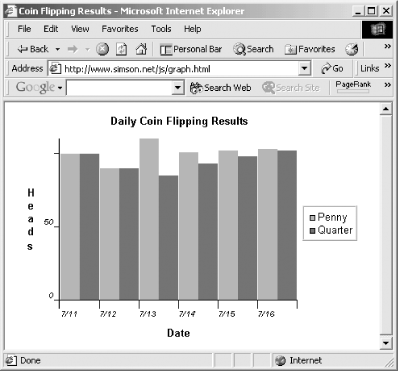
</center></script></body></html>When this HTML file is loaded, it produces a graph similar to the one shown in Figure 13-10.
Figure 13-10. Michael Bostock’s Graph Builder Library can create impressive graphics using JavaScript.
JavaScript’s ultimate utility is somewhat muted by incompatibilities among the JavaScript implementations in different web browsers. With each new version of Netscape Navigator, Netscape has made significant and occasionally incompatible changes to the JavaScript language. Microsoft did not license JavaScript from Netscape, but instead created its own clone named JScript. These versions were theoretically merged into a scripting language, specification ECMA-262, also known as ECMAScript, in June 1997.[143] Unfortunately, continuing differences in the Document Object Model between Netscape Navigator and Microsoft Internet Explorer mean that most web pages that use complicated JavaScript require “client-sniffing” code that detects the browser that the user has, and adjusts the JavaScript appropriately.
JavaScript programs should be inherently more secure than programs written in Java or other programming languages for a number of reasons:
There are no JavaScript methods that directly access the files on the client computer.
There are no JavaScript basic methods that directly access the network, although JavaScript programs can load URLs and submit HTML forms.[144]
With code signing, individual JavaScript programs can be given access to some system functionality (such as the ability to read files) without opening others (such as the ability to open network connections).
Alas, the anticipated security of JavaScript’s design was not realized in its execution. As with Java, JavaScript was developed without a formal security model. Instead, security relied on hunches and common-sense reasoning on the part of its creators. Add to this the fact that most JavaScript implementations have had significant bugs, and you can understand why many security flaws and problems have been traced to buggy or poorly thought out JavaScript implementations. In many circumstances, JavaScript’s creators were simply unable to anticipate the interaction between their language and the other aspects of various web browsers.
All of the discovered flaws were fixed shortly after they were reported. Navigator 3 was relatively free of JavaScript problems, and Navigator 4 finally implemented a security model for JavaScript code running on browsers.
But alas, even when JavaScript is running properly, normal, “well behaved” JavaScript programs have the ability to open new browser windows without your permission, and to lock up your browser so that it is unusable. For versions of Netscape prior to 6.1 running on Unix computers, you can even use JavaScript to crash the user’s window system.
We recommend that users in high security environments disable JavaScript.
Because a piece of downloaded JavaScript runs inside the browser itself, it potentially has access to any information that the browser has. Early JavaScript implementations featured a variety of problems that could lead to loss of confidentiality or privacy, including the following:
JavaScript could be used to create forms that automatically submitted themselves by email. This allowed a malicious HTML page to forge email in the name of the person viewing the page. (“Viewing this page automatically sends the President and his cat an electronic death threat from your web browser.”) This feature could also be used to collect the email addresses of people visiting a web page. (“Thank you for visiting our web page; your name and email address have automatically been added to the Flat Earth Society mailing list.”)
JavaScript programs had access to the user’s browser “history” mechanism. This allowed a web site to discover the URLs of all of the other web pages that you had visited during your session. This feature could be combined with the previous feature to perform a form of automated eavesdropping.
A remote site could use JavaScript to upload arbitrary files from the user’s disk drives to the hostile server.
A JavaScript program running in one window could monitor the URLs of pages visited in other windows.
All known bugs that could compromise the privacy or the security of the user’s computer were corrected by Microsoft and Netscape shortly after the bugs were discovered. Unfortunately, users are not quick to upload patches—especially as many of these “patches” have required users to download a new multimegabyte program and reinstall the browser, and have sometimes broken needed functions.
JavaScript can be used to mount effective denial-of-service attacks against the users of web browsers. A denial-of-service attack is an attack in which a user (or a program) takes up so much of a shared resource that none of the resource is left for other users or uses. These attacks can be resident on web pages or they can be sent to users with JavaScript-enabled mail readers in electronic mail. Most of these attacks result in the crashing of the computer on which the web page is running. This can represent an annoyance or a loss of productivity for most users and corporations, and it can be a serious problem for web browsers that are used in safety-critical applications or in network monitoring systems.
Of course, any programming language or environment that allows systemwide resources to be allocated and then places no limitations on the allocation of such resources is subject to denial-of-service attacks. But JavaScript is especiallysensitive to such attacks because of the power that it gives active content over the computer’s web browser.
Both Navigator and Explorer’s Java and JavaScript implementations suffer from the fact that you can’t break out of a running Java or JavaScript program (easily or at all, depending on version). If you want to terminate a program, your only real choice is to exit the browser itself.
Unfortunately, exiting the browser can be complicated by the fact that the browser itself may have stopped listening to menu commands as a result of an ongoing denial-of-service attack. In this case, it will be necessary to find some other way to terminate the browser, such as typing Control-Alt-Del under Windows or Command-Option-Escape under Mac OS.
Many users do not know about these “tricks” for forcing a running program to quit. Therefore, your typical Macintosh or Windows users, faced with this JavaScript-based HTML attack, may find themselves with no choice other than turning off their machines:
<html>
<head><title>Denial-of-service Demonstration</title>
</head>
<body>
<script>
while(1){
alert("This is a JavaScript alert.");
}
</script>
</body>To further complicate matters, it turns out that the JavaScript alert( ) method has had different semantics when running under some versions of Windows and Mac OS from those used when running on Unix. For web browsers running on Windows and Mac OS clients, the JavaScript alert( ) method is blocking: it waits for you to click the OK button before going on. But under Netscape’s Unix clients prior to Navigator 6.1, the alert( ) method does not block. Instead, Netscape brings up hundreds (or even thousands) of little alert windows. This will actually cause most Unix window managers to crash, making this an effective denial-of-service attack not only against the browser, but against the user’s entire workspace.
Both Java and JavaScript allow downloaded code to create and manage windows on the user’s machine. Graphical User Interface (GUI) operations consume a tremendous amount of system resources on most computers. By creating many windows, the user’s entire computer can be rendered inoperable.
One of the more annoying features of JavaScript is the ability to register a JavaScript function that will be executed when the current JavaScript page is unloaded—that is, if the Back button is hit or if the window is closed. Many porn sites on the Internet use this feature to bring up new windows when you attempt to close an existing window. A particularly amusing exploit that uses this feature was first introduced by Kevin McCurley on his "DigiCrime” web site (http://www.digicrime.com/). The exploit consists of an HTML file with an embedded JavaScript attack that causes two new windows to be opened every time you attempt to close the window on which the HTML page resides. A message displayed on the screen says “Your only way out now is to kill the browser.”
Here is an example of such a script:
<html>
<script language="JavaScript">
function again( ) {
var n1 = Math.floor(Math.random( )*1000000);
var n2 = Math.floor(Math.random( )*1000000);
window.open('js-close-attack.html', n1, 'width=300,height=200');
window.open('js-close-attack.html', n2 , 'width=300,height=200');
}
</script>
<head>
<title>JavaScript onUnload Demonstration</title>
</head>
<body onUnload="again( )">
<center><h1>Thanks to Digicrime!</h1>
<hr>
Your only option now is to turn off your computer.
<a href="javascript:again( )">attack</a>
<hr>
</center>
</html>The real culprit here is not JavaScript’s ability to hook
onto the unLoad event, of course, but its ability to make new
windows. Change the onUnload
tag to an onLoad tag in this
script for even more highjinks!
Tip
Netscape 6 gives the user the option of preventing a script from opening new windows. For details, see: http://www.mozilla.org/projects/security/components/ConfigPolicy.html.
Not everything is doom and gloom in the denial-of-service attack department, however. Early versions of Internet Explorer and Netscape Navigator were both susceptible to CPU and stack-space attacks written in JavaScript. But these vulnerabilities have now largely been repaired.
Consider this HTML file that uses JavaScript to display the first 100,000 Fibonacci numbers:
<html>
<head><title>Fibonacci Test Page</title>
</head>
<body>
<h1>The Fibonacci Series</h1>
<script>
function fibonacci(n)
{
if(n>1) return fibonacci(n-1)+fibonacci(n-2);
if(n>=0) return 0;
return 1;
}
for(i=0;i<100000;i++){
document.write("Fibonacci number "+i+" is "+fibonacci(i)+"<br>");
}
</script>
</body>
</html>When this page is loaded into either browser, the browser becomes unresponsive. After a pause of approximately 30 seconds, both Internet Explorer and Netscape Navigator will display a warning that allows you to abort the execution of the running script (see Figure 13-11).
Ed Felten at Princeton University notes that people are constantly making security-related decisions. To make these decisions, people use contextual information provided by their computer. For example, when a user dials in to a computer, the user knows to type her dialup username and password. At the same time, most users know to avoid typing their dialup username and password into a chat room on America Online.
Java and JavaScript can be used to confuse the user. This can result in a user’s making a mistake and providing security-related information to the wrong party.
When an untrusted Java applet creates a window, most web browsers label the window in some manner so that the user knows that it is unsecure. Netscape Navigator, for instance, will display the window with the message “untrusted applet.” The intention of this labeling is to alert the user: users may not wish to type their login usernames and passwords into a window that’s not “trusted.”
When an applet runs inside a browser window itself, no such labeling takes place. A rogue HTML page can easily display an innocuous background and then use a Java applet to create a traditional web browser username/password panel. The applet can even detect an attempt to drag the spoofed “window” and make it move on the page appropriately. The user can’t determine the difference unless she tries to drag the window outside the browser’s window.
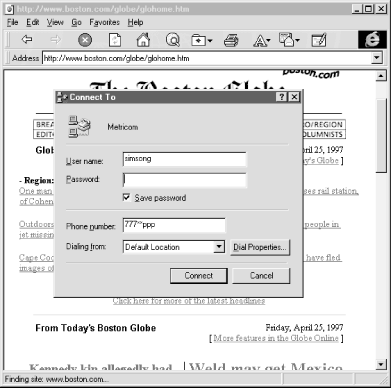
Applets aren’t limited to spoofing web username/password panels. An applet could easily display other username/password panels. For example, a web server could check to see if a user has accessed a web page using a Windows personal computer dialed up with the Microsoft PPP dialer. If this is detected, the applet could display a window that told the user that the connection had been disconnected, followed by a request to reconnect (see Figures Figure 13-12 and Figure 13-13).
The applet could even play the sound of a modem dialing and connecting. An astute user might realize that the modem is still connected, but many probably would not. Send such an applet to a few thousand users, and you’ll probably get dozens of dial-up usernames and passwords.
Felten notes that many users’ security decisions are based on URLs and filenames. A Windows user might know that downloading a file called HAPPY.EXE might be more dangerous than downloading a file called HAPPY.GIF because the first is an executable program, whereas the second is an image. Now consider these two URLs:
https://www.mall.com/order.html https://www.university.edu/users/guest/open/order.html
Although the naming of both of these URLs implies that they are secure order pages, either or both may not be. At that, the first URL might inspire trust, but fewer users might feel comfortable typing a credit card number into the second.
JavaScript has several tools that can be used for spoofing user context. These include the following:
JavaScript can display boxes containing arbitrary text.
JavaScript can change the content of the browser’s status line.
On some browsers, JavaScript can be used to hide the browser’s “Goto:” field and replace it with a constructed field built from a frame.
For example, the status line of the browser normally displays the URL that will be accessed if the user clicks on a link. But using JavaScript, you can make a user believe that one URL actually points someplace else. For example, this HTML link will display the URL http://www.shopping.com/order-entry.html when the mouse is moved over the link, but clicking on the link will jump to the web page http://www.attacker.org/trapped.html.
<a href="http://www.attacker.org/trapped.html" onMouseover="window.status='http:// www.shopping.com/order-entry.html';return true">Click Here to enter your credit card number</a>
Many users might be willing to run any program that they downloaded from a trusted domain. However, there are many ways to trick a user’s web browser into downloading a program from one domain but displaying visual cues that indicate the program is in fact being downloaded from another. Consider these issues when downloading a file SETUP.EXE, apparently from a host at Microsoft Corporation:
The user may think that the file is being downloaded from the domain MICROSOFT.COM, when the file is in fact being downloaded from MICROS0FT.COM (a domain in which the letter “O” has been changed to the digit “0”).
The user may see that the file is being downloaded from MICROSOFT.CO.FI, and not know whether or not that is a domain associated with Microsoft.
The web browser may display the beginning and the end but truncate the characters in the middle of a large URL. For example, the browser may display that a file is being downloaded from the address http://www.microsoft.co.../setup.exe. But the user might not realize that the file being downloaded actually has the URL http://www.microsoft.com.attacker.org/guests/users/hacker/setup.exe.
One way to minimize spoofing risks is by producing “unspoofable” areas—status displays on the browser’s window that cannot be rewritten by JavaScript or Java. For example, Netscape Navigator may display part of the web server’s DNS name in an area that cannot be overwritten by a program running in the web browser. This may help solve some problems. A better approach would be to have the web browser display, in a prominent area, the distinguished name that is on a web server’s public key certificate. (See Chapter 17 for more information on server certificates.)
Felten et al. have demonstrated that it is possible to use the techniques mentioned in the preceding sections to create a mirror World Wide Web site. The site uses a combination of URL rewriting, JavaScript substituting techniques, long hostnames, and caching to replicate the content of one web site on another.
A mirror world constructed in this fashion can essentially trap users, monitoring all of the pages that they request, capturing passwords, and even conducting man-in-the-middle attacks (described in Chapter 5) on SSL connections. A suspicious user could detect such a mirror world attack by looking at the distinguished name on an SSL certificate, and he could break out of the mirror world by using the web browser’s Open Location function or using a bookmark. However, it is conjectured that most users would not discover the attack, and would divulge significant information to the attacker.
There are many ways to lure a user into a mirror world. The URL could be put in a public area where it is likely to be tried. For example, it could be sent to a mailing list or posted on a web-based bulletin board. The URL could be added to a search engine. Once inside the mirror world, the only way out would be by using a bookmarked web site or using the browser’s Back button.
Although a mirror world attack is easily traced back to the web site that is conducting it, this information may not in itself be useful. The attacking site may be in a foreign country. Alternatively, it may be a web site that has itself been compromised.
[142] Much of Netscape Navigator 6.0 is written in JavaScript!
[143] For information on ECMA see http://www.ecma.ch/. The ECMA-262 specification can be downloaded from http://www.ecma.ch/ecma1/stand/ecma-262.htm.
[144] Netscape Navigator Version 6 supports “signed JavaScript” code, which is allowed to access the full API of the browser through the XPConnect System. This provides access to the network and files.