In order to analyze the vulnerability described in Chapter 6, I needed a way to debug the Windows kernel. I set up a debugging environment with VMware[92] and WinDbg[93] by following these steps:
Note
Throughout this section, I used the following software versions: VMware Workstation 6.5.2 and WinDbg 6.10.3.233.
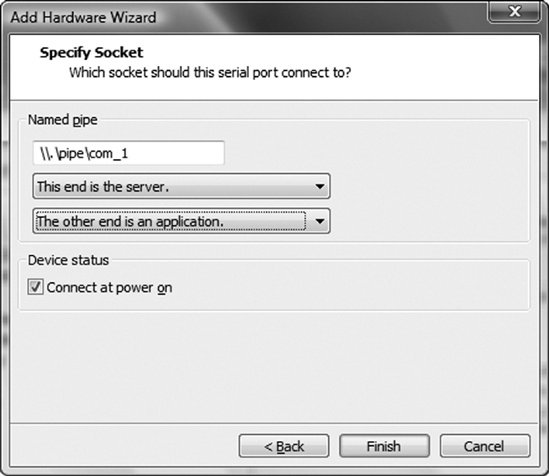
After I installed a Windows XP SP3 VMware guest system, I powered it off and chose Edit Virtual Machine Settings from the Commands section of VMware. I then clicked the Add button to add a new serial port and chose the configuration settings shown in Figure B-1 and Figure B-2.
After the new serial port was successfully added, I selected the Yield CPU on poll checkbox of the “I/O mode” section, as shown in Figure B-3.
I then powered up the VMware guest system and edited the boot.ini file of Windows XP to contain the following entries (the bold one enabled kernel debugging):
[boot loader] timeout=30 default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS [operating systems] multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional" /noexecute=optin /fastdetectmulti(0)disk(0)rdisk(0)partition(1)\WINDOWS="MicrosoftWindows XP Professional - Debug" /fastdetect /debugport=com1
I then rebooted the guest system and chose the new entry Microsoft Windows XP Professional – Debug [debugger enabled] from the boot menu to start the system, as shown in Figure B-4.
The only thing left was to configure WinDbg on the VMware host so that it attached to the kernel of the VMware guest system using a pipe. To do this, I created a batch file with the content shown in Figure B-5.
I then double-clicked the batch file to attach WinDbg on the VMware host to the kernel of the VMware Windows XP guest system, as shown in Figure B-6.