Note
Wednesday, September 17, 2008
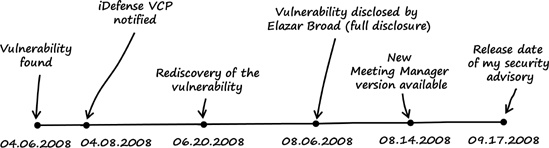
The vulnerability is fixed and a new version of WebEx Meeting Manager is available, so I released a detailed security advisory on my website today.[56] The bug was assigned CVE-2008-3558. Figure 5-12 shows the timeline of the vulnerability fix.
Figure 5-12. Timeline from discovery of the WebEx Meeting Manager vulnerability until the release of the security advisory
[45] COMRaider from iDefense is a great tool to enumerate and fuzz COM object interfaces. See http://labs.idefense.com/software/download/?downloadID=23.
[46] For more information, consult “Safe Initialization and Scripting for ActiveX Controls” at http://msdn.microsoft.com/en-us/library/aa751977(VS.85).aspx.
[47] See “Not safe = not dangerous? How to tell if ActiveX vulnerabilities are exploitable in Internet Explorer” at http://blogs.technet.com/srd/archive/2008/02/03/activex-controls.aspx.
[48] For more information on cross-site scripting, refer to https://www.owasp.org/index.php/Cross-site_Scripting_(XSS).
[49] See “MindshaRE: Finding ActiveX Methods Dynamically” at http://dvlabs.tippingpoint.com/blog/2009/06/01/mindshare-finding-activex-methods-dynamically/.
[51] WinDbg is the “official” Windows Debugger from Microsoft and is distributed as part of the free “Debugging Tools for Windows” suite, available at http://www.microsoft.com/whdc/DevTools/Debugging/default.mspx.
[55] For more information on Microsoft’s SiteLock, see http://msdn.microsoft.com/en-us/library/bb250471%28VS.85%29.aspx.
[56] My security advisory that describes the details of the WebEx Meeting Manager vulnerability can be found at http://www.trapkit.de/advisories/TKADV2008-009.txt.