In this chapter, you will learn how to
• Define a cellular network, list different mobile devices, and describe the hardware and software characteristics of mobile devices
• Provide an overview of a mobile operating system and discuss different types of mobile operating systems
• Articulate what a criminal can do with mobile phones
• Describe different mobile forensics challenges, including the various memory considerations in mobiles
• Explain the process involved in mobile forensics, including which precautions to take prior to the investigation
• List several hardware and software tools for mobile forensics
Some of us go back to the days of the “personal digital assistant” (PDA). Aside from acting as a geek badge of coolness, a PDA was actually occasionally useful! I myself owned a Palm Pilot, a HandSpring Visor (always looking for bigger real estate), and a Sony Clie that is still alive and ticking. When a colleague bought a Sharp Zaurus SL-5500 that had a pull-out keyboard and ran Linux, I suffered such an attack of geek envy that I ran out and bought one immediately. It, too, is still alive and mostly well. (Given that these devices are over 10 years old, I think it’s testimony to how well they were made to begin with.)
Of all the areas of digital forensics, mobile devices have seen the most change over the last five years. New models appear about every year, along with new versions of handheld operating systems, new applications (apps), and new communications capabilities.
What exactly is a mobile device? Is a smart phone running Android OS with a cellular telephone connection and a Wi-Fi connection a mobile device? How about an Android 7″ tablet with a Wi-Fi connection? What about a laptop computer using a wireless modem to send and receive data over the Internet? For the purposes of this chapter, we’re going to restrict ourselves to digital devices that communicate via cellular telephone networks as their primary means of external communication, whether it is voice, data, or both. One distinguishing characteristic of all mobile devices, however, is that their network location will change over time as they move, and this change is transparent to the user; that is, their network address isn’t static. This distinguishes a true mobile device from a moveable device where an address is assigned and remains unchanged until the machine is rebooted or manually changed by the user, or reassigned by a local server (such as a DHCP server) from its local pool.
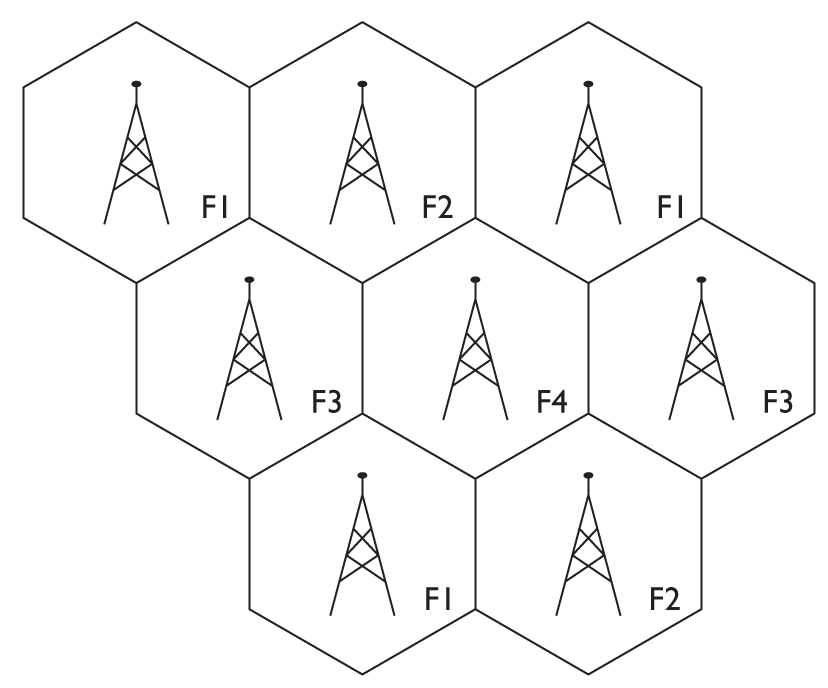
Before we get started, let’s do a little review. Cellular networks are used for sending and receiving voice traffic. In its simplest form, a cellular network consists of two radio transceivers: the mobile device and the cell tower. A set of cell towers, each arranged in some geometric configuration (circle, square, hexagon, and so on), can talk to each other, to intermediary switching and network equipment, and to other mobile devices. Figure 10-1 shows a model configuration. Cell tower ranges don’t overlap much, just enough so that as the mobile device moves, it associates with a particular tower. As it moves out of range of that tower, the tower will “hand off” the call to an adjacent tower. This is transparent to the user.

Figure 10-1 Cellular network model, showing frequency assignments
There were initially three main categories of cellular networks, based on their mode of transmission. The first was based upon the older Global System for Mobile Communications (GSM) standard, used by the whole world except for the United States, which used one flavor of Time Division Multiple Access (TDMA). The other flavor of TDMA was based on IS-36, and the two protocols did not interoperate. Circuit Division Multiple Access (CDMA) was previously used in the United States by particular cellular service providers, though these days, most U.S. carriers have also migrated to GSM and its technological descendants. A device using one of those technologies couldn’t communicate on a network that uses another. Your CDMA phone would have been useless on a GSM network, though some vendors previously offered a dual-mode phone that supported both GSM and CDMA, sometimes called world phones.
Life is different these days (perhaps not better, but different). With the advent of 3G technologies (Edge, UMTS, iDEN, and so on), phones increased in speed and memory capacity. Over time, these technologies have merged into today’s 4G Long Term Evolution (LTE) standards and technologies. Figure 10-2 shows the wireless specifications for my Samsung S III. For me, the most important aspect was the check box that read “World Phone” (not shown). What can I say? I’m old school.
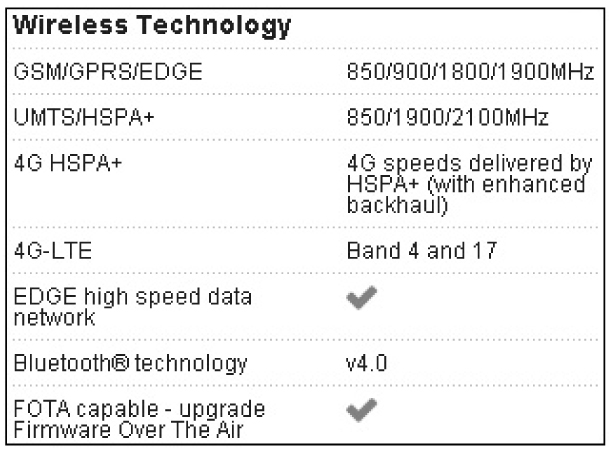
Figure 10-2 Wireless specifications for my Samsung S III
There are three essential components of a cellular network (NIST SP-101):1
• The base transceiver station (BTS), more commonly described as a cell tower.
• The base station controller (BSC)—the hardware and software to manage calls. A BSC will connect to the MSC.
• The mobile switch center (MSC), which supports routing of digital packets and maintains a database that contains information on location data, account data, and other subscriber information. Obtaining data from an MSC will require a warrant or a subpoena.
The GSM standard calls the mobile device a “mobile station” (MS). Each MS consists of a subscriber identity module, the universal integrated circuit card (UICC), frequently referred to as the subscriber identity module (SIM), and the mobile equipment (ME) that comprises the rest of the phone. The SIM itself is a tiny device (about the size of a fingernail or smaller) that has a CPU, RAM (program execution), ROM (the OS), and EEPROM. Together, they comprise the mobile device execution environment: A device won’t function without the UICC.
The international mobile equipment identifier (IMEI) consists of 15 digits (14 digits plus a check digit), and is illustrated in Figure 10-3. The first eight digits represent a type allocation code (TAC), while the last six identify the manufacturer and possibly the phone type as well. The TAC is further broken down in two subfields. The first two digits of the TAC represent the reporting body identifier and are always decimal. If the first two digits are 0xA0 or greater, the identifier is understood to be a mobile equipment identifier (MEID) used in CDMA phones.
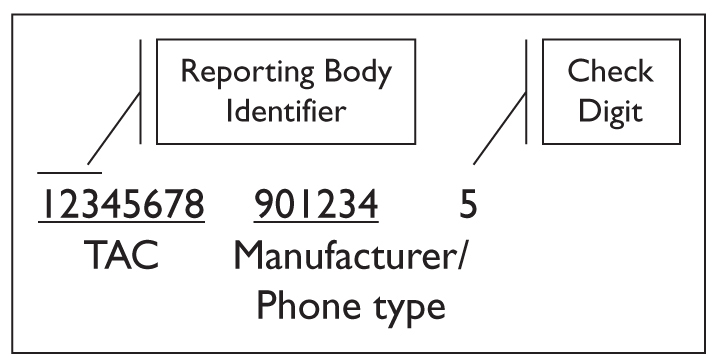
Figure 10-3 IMEI fields
If a GSM phone is powered on, you can retrieve the IMEI by keying in “*#06#”. If the phone is turned off, you can remove the back of the phone and the battery, which should reveal the identification number. Figure 10-4 shows my late, lamented Blackberry 8510 with the back and battery removed so that the IMEI number is clearly visible. On more modern phones, such as the Samsung S III, the IMEI can be displayed in the “About Device” page that’s part of the System settings.
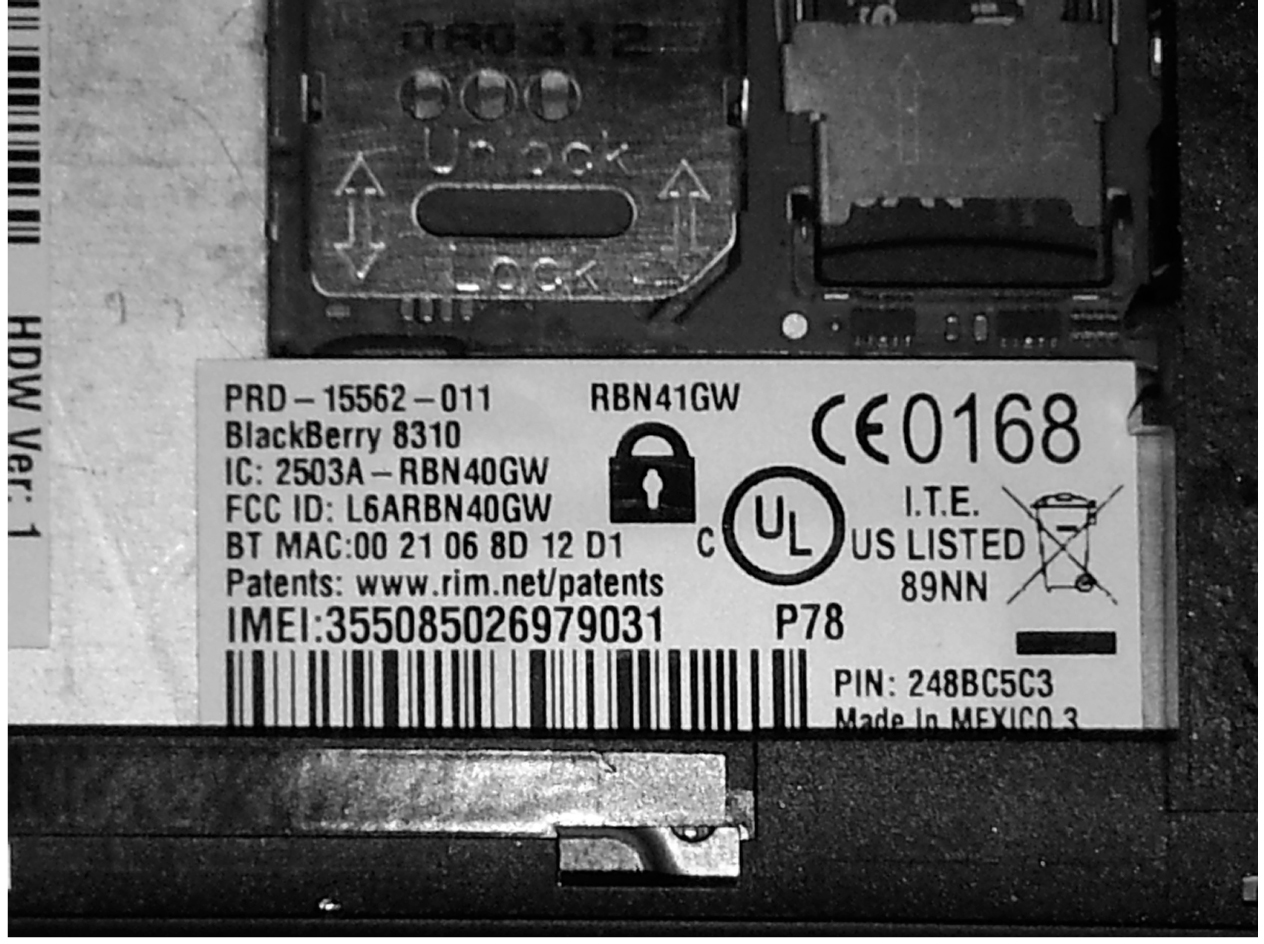
Figure 10-4 Blackberry 8310 with battery removed showing IMEI number
The UICC contains several identifiers. The integrated circuit chip identifier (ICCID) identifies a particular UICC to the network service provider or operator. The ICCID can be up to 20 digits long. The first portion, the issuer identification number (IIN), is a maximum of seven digits—the first two digits are the major industry identifier (MII) (these are two-digit codes; 89 is for telecommunications). The next three digits are the country code, and the last field, the issuer identifier, can be from one to four digits long. The rest of the ICCID represents an account identification number that will vary, depending on the length of the previously mentioned fields, but all account IDs from the IIN are the same length. Table 10-1 summarizes these fields.
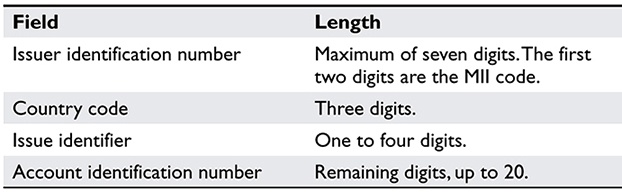
Table 10.1 ICCID Identifier Fields and Their Lengths
The international mobile subscriber identity (IMSI) consists of a three-digit mobile country code, two to three digits for the mobile network code (three digits are used in the United States and Canada), followed by either nine or ten digits that represent the mobile subscriber identification number (MSIN) for that particular country and network. All of this means that, given a particular phone, we can identify the manufacturer, the device identifier, and an identifier that tells us who the subscriber is on a particular network. Table 10-2 summarizes the IMSI fields and their lengths.
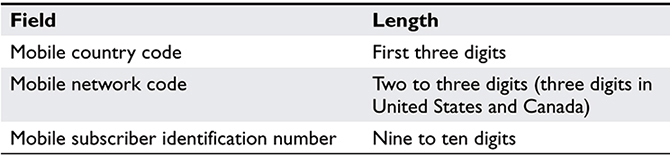
Table 10.2 IMSI Field Identifiers and Their Lengths
The DFI may find that the device is locked and it requires a personal identification number (PIN) to unlock. The device has two passwords: the PIN and a personal unblocking code (PUK) for PIN unlocking. This code is sometimes called a personal unlock code (PUC) or PIN unlocked key (PUK). Some phones will respond with an unlock code if you key in “#*06#” from the keyboard. Other manufacturers may provide different unlock codes. If an incorrect password is entered three times in a row, the SIM card is blocked and must be unblocked using the provided code.

EXAM TIP You should know the difference between a PIN, a PUC, and a PUK. A quick tip: C for code, K for key.
Although mobile devices share many of the same characteristics as less-mobile devices (laptops come to mind), there are differences in how these devices secure the data. Many devices support a configuration such that data will be wiped from the device if a correct password or PIN isn’t entered in a certain number of tries (10 tries is common). This is in addition to wiping the device by means of a remote command. Given that the number of password attempts is limited, it’s not a good idea to guess.
The file structure on a SIM card is a hierarchy based in the root directory (the master file, or MF). Beneath the root directory are directory files (DF) directories, each of which contains element files (EF). Figure 10-5 illustrates the hierarchy of the SIM file system. The MF contains an entry for all the other files in the file system. Files are either DF or regular files, called element files (EF). Note that the directory files contain information based on the type of network to which the device can connect and has connected to (some phones support dual band in that they have a GSM and a CDMA radio).
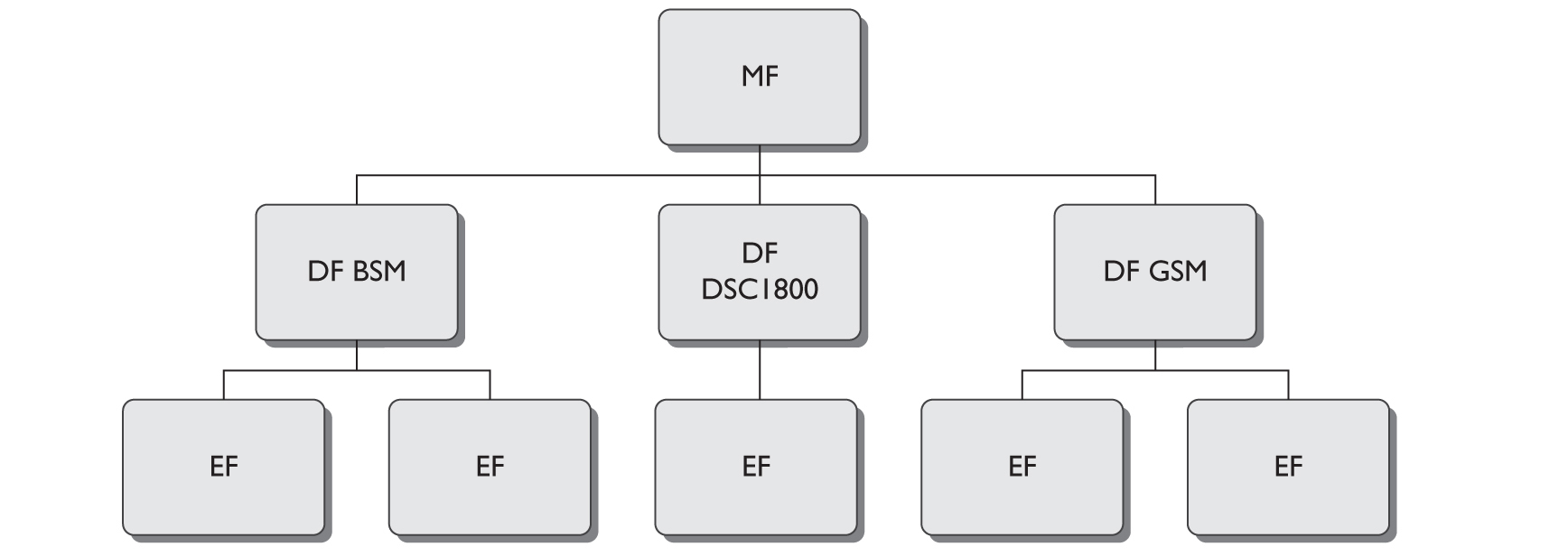
Figure 10-5 SIM card hierarchy (Source: Ayers, R., Brothers, S., Jansen, W. Guidelines on Mobile Device Forensic, NIST Special Publication 800-101, Revision 1, (dx.doi.org/10.6028/NIST.SP.800-101r1), p. 9.)
The data stored on a SIM card is a treasure trove of information for the DFI. A subscriber to a cellular phone service is charged based on usage and location (roaming charges), and if there’s one thing that phone companies are good at, it’s keeping detailed call records and charging you for the minutes you used. The SIM file structure can include the ICCID and the IMSI identifiers. Additional information stored on the device includes
• An abbreviated dialing number (AND) that accesses the phonebook stored on the SIM
• The last number dialed (LND)
• Short Message Service (SMS) and Enhanced Messaging Service (EMS) messages
• Location area information (LAI) for voice
• Routing area information (RAI) for data communications
The LAI indicates where the device was last located. Cross-checking this evidence with GPS data or other location data as determined by gathering Wi-Fi data can create a strong circumstantial case that the suspect’s device (and, we assume, the suspect) was indeed at a particular location at a particular time.
Armed with this information, a DFI can approach a vendor and request call records, assuming a valid warrant has been issued. Pertinent fields from the call record are listed in Table 10-3. An “M” in the Key field indicates a mandatory field; a “C” means the field is conditional.

Table 10-3 Call Record Fields of Forensic Interest
Given this information, we can identify the number dialed and the country, the manufacturer, and the brand of the calling party. Since the IMSI has local significance, the provider can be asked to deliver subscriber information that is used for billing purposes. Notice that while this identifies the person who received the call, this doesn’t necessarily mean that the owner of the phone is the individual who actually answered the call. Nor does it prove conclusively that the owner was in possession of the phone at the time of the call.
Cellular phone networks also support data communications, which is unsurprising given that people have been using modems attached to phone lines for decades.
Just as with a voice connection, transmission between source and destination IP networked devices must survive a hand-off between cell towers, similar to transferring a Wi-Fi connection between access points (APs). Addressing is different—a mobile device has two Internet addresses: its “home” address and its “mobile” address (a “care of” address). Initial contact is made with the device’s “home” network, and the sender is then told to access that device via its “care of” address.
At 3G transmission levels and above, data are encrypted between the mobile device and the cell tower. People who are concerned about privacy and confidentiality of their data communications will want to use a higher-level protocol such as Internet Protocol Security (IPsec), Secure Shell (SSH), or Secure Socket Layer/Transport Layer Security (SSL/TLS) to enforce end-to-end encryption.
Keeping up with the latest models, software revisions, and new applications is more than a full-time job—as you can undoubtedly see from the number of pundits and bloggers. There are shared characteristics that let us generalize across device types. In this section, we’ll address these shared characteristics and then approach four different classes of devices: personal digital assistants (PDAs), music and game players (personal entertainment devices), standard cell phones, and smart phones.
All mobile devices share certain hardware and software characteristics. All devices will have, at a minimum, a transceiver for voice and data communication. All devices will have various types of memory: read-only memory (ROM) for the OS, random-access memory (RAM) for use by applications, and on-board memory for persistent SIM storage. All devices will have a connector (some use a form of USB; others use proprietary connectors) that allows the device to communicate with another device for backup and upload. Most devices will have a built-in GPS receiver and a camera.
In the case of software, mobile devices will have an operating system, supporting utilities for device management and configuration, and a set of hard-wired applications. A clock, an address book/contact list, a calendar, to-do list, and memo-pad applications—the usual personal information manager (PIM) applications—are standard. Different vendors may supply additional software that highlights their additional features, such as a camera application, an audio and video player, and an application to manage photographs and other images and so forth.
Handheld devices that offered PIM capabilities were called personal digital assistants (PDAs). In most cases, access was restricted to synchronizing either with a desktop application provided by the manufacturer or with applications that were already installed with the desktop OS. We’ll look at two such systems that are still extant (as of 2014).
PalmOS first appeared with the Palm Pilot PDA in 1996. This generation didn’t have much in the way of untethered network connections. My Clie could communicate using infrared, using a proprietary protocol over a USB cable, or using TCP running over a USB cable. In all cases, though, it was intended to allow the device to synchronize with the desktop software. It came standard with the usual PIM suite, as well as an e-mail application that would synchronize with Palm’s own desktop software or Microsoft’s Outlook software. The latest release running on my Clie was 4.1.0.3. The last release of PalmOS (as WebOS from HP) was in 2011.
In Palm OS, both the OS and the standard applications were stored in ROM. RAM was divided into dynamic RAM, used by running applications, and storage RAM, used for actual file storage. Since memory protection wasn’t available, applications could use each other’s data and potentially modify each other’s code, whether intentionally or unintentionally. Security features were minimal, although the screen could be locked when turned off and require a password to unlock.
Another example of a PDA was the Windows Pocket PC running the Windows CE (Compact Edition) OS. The original Pocket PC became available in 2002 and lives on under the name of Windows Phone. The OS and certain applications are stored in ROM; otherwise, applications run and store data in RAM. RAM is divided into three sections: the registry, file system, and property databases. Property databases act as data stores where data can be stored, searched, and retrieved.2
The original cell phones offered a minimal user experience: black and white screen, call logs, phonebooks (name and number), and user-assignable ringtones. Navigation was via arrow keys and possibly by a track ball. Competition between manufacturers and cellular telephone companies resulted in ever-increasing capabilities (“creeping featurism”), leading up to today’s smart phones. What’s the difference between a “smart phone” and a “not-so-smart” phone (a feature phone3)? Table 10-4 compares and contrasts the two.4
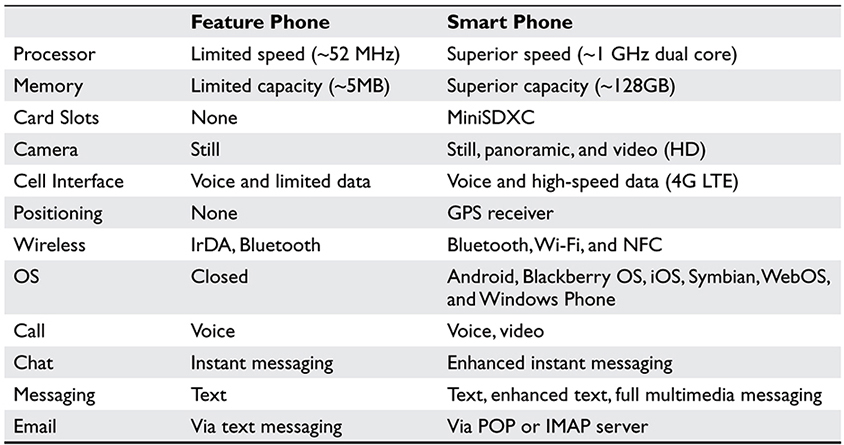
Table 10-4 Feature Phones Versus Smart Phones
As more and more audio was delivered as digital content instead of vinyl records, cassette tapes, or compact discs (CDs), music players such as the Diamond Rio became more popular. The iPod is the classic example of this kind of device. The original iPod (now called the iPod Classic) used USB for file transfer and a click wheel for navigation. The iPod touch, released in 2007, ran the same OS (iOS) as the iPhone, as well as offering the same set of applications through the Apple iTunes Store. Earlier versions of the iPod offered up to 80GB of storage, accessible via a USB interface and formatted as FAT32 or Hierarchical File System (HFS)+, depending on whether the desktop was a Windows or Macintosh machine. Later releases of iOS and the iPod only allowed access to the device via the iTunes software and a proprietary protocol.
At present (spring 2014), Apple’s iOS-based iPhone line is battling with Samsung, a legion of Android-based phone makers, and Windows-based phones for global market share. We already talked briefly about the Windows Phone OS earlier in this chapter.
iOS is a closed-source, proprietary OS from Apple, Inc. (www.apple.com) that was released in 2007 with the first iPhone. Applications for this platform are only available via the iTunes Store. Versions 4 and above support multitasking; iOS 7 includes the ability for foreground applications to execute updates in the background. For forensics, access to data is through backup via the iTunes desktop software or by using a driver that mimics the behavior of the iPhone software.
Google released the Android OS in 2007 as well (clearly, 2007 was a good year for mobile operating systems). Now at revision 4.4, the OS is used by many device manufacturers (Samsung, Motorola, Asus, and HTC, just to name a few of the major ones). Android is a Linux-based, multitasking OS that supports many apps for examining the file system, as well as transferring data from the device to a desktop computer. If mounted as a USB device, disk images can be acquired by imaging the device using the dd command on Linux or other device-imaging software.
Android also allows applications to run in the background while the device is turned on, even if another app is running in the foreground (displaying on the screen). Some devices support MicroSD cards for permanent storage, although regular RAM is available, usually in 8-, 16- or 32-GB configurations. Apps are available at the Google Play Store (http://play.google.com/store) or from other major vendors (such as the Amazon Store for Kindle variants of Android), and from third parties such as F-Droid (www.f-droid.org). Given the nature of the open source, alternative versions of the OS exist, such as CyanogenMod.
The release of the Apple iPad in 2010 started a major change in mobile computing. Tablet computers (sometimes called slates), powered by operating systems originally developed for smart phones, rapidly became powerful enough to replace laptops as the computer of choice for frequent travelers. The original specs for the iPad 1, running iOS, were 9.56″ × 7.47″ × 0.5″ thick. Smaller tablets quickly followed: The Nexus 7 2013 tablet, running the Android OS, measures 7.87″ × 4.49″ × 0.34″.
As tablets grew smaller, smart phones grew larger. Samsung released the original Galaxy Note in 2011. The current Note 3 measures 5.95″ × 3.12″ × 0.33″ and weighs 3 grams. It also sports a 1920 × 1080 screen—the same resolution as my current 21″ monitor. Was it a large phone or a small tablet or a mixture of the two (and hence “phablet”)? Moreover, should a DFI care? Patience, dear reader, patience.
There’s an old joke that goes like this. Question: What can an 800-pound gorilla do? Answer: Anything it wants. So it is with mobile phones and criminal activity. Communication, either by telephone or data networks, recordkeeping, audio, video, photographs… all available for storing and communicating information. Space is not an issue: A 128-GB MicroSD card was recently announced by SanDisk. You can run your business from a mobile phone. Both iOS and Android support encryption of main storage, and stolen or lost devices can be wiped remotely. Cellular phones have become enough of a commodity that purchasing a “throw-away” for transient communications is available to virtually anyone, especially for the “pay as you go” phones that provide (semi)anonymous communication. A criminal also can use the phone in the commission of a crime: sending abusive e-mail, text messages, spam, replacing the SIM card, and so on. Given enough storage, a phone could carry illegal materials, such as stolen intellectual property or child pornography.
A DFI can obtain a wealth of data from a mobile device.5 Even the earliest PDAs could provide the following capabilities:
• Phonebook
• Calendar
• To-do list
• Electronic mail
• Electronic documents
• Photos
• Videos
• Audio
• Graphics
The addition of phone capabilities to PDAs (for example, the Palm Treo added telephone capabilities), or mobile phones themselves (such as the Motorola flip-phone), provided more information sources specific to telecommunications:
• Instant messages
• Web information
• Subscriber identifiers
• Equipment identifiers
• Service provider
• Last dialed numbers
• Phone number log
• Short text messages (SMS)
• Last active location (voice and data)
• Other networks encountered
In addition, smart phones included Wi-Fi networking along with existing cellular networking. In some instances, Wi-Fi was added to music players: The Apple iPod touch looks remarkably like the iPhone series without the telephone portion (including running the same version of the OS as well as applications from the iTunes Store). Smart phones also enabled enhanced messages and multimedia messages along with text.
Is a smart phone or phablet with a cellular data connection the equivalent of a laptop with a cellular data connection? Strictly speaking, yes. These devices share similar sets of applications and similar hardware characteristics (smart phones now have up to 3GB of RAM, along with up to 32GB of flash storage). In February 2014, SanDisk announced a 128-GB MicroSD card. Cards are usually formatted as FAT32 devices. Ultimately, the DFI will use similar tools, techniques, and processes to analyze data from these devices as they would to acquire evidence from more traditional desktop or laptop computers.
Mobile devices come with their own set of challenges. Accessing memory is different from on a laptop computer. With mobile devices, there is memory you can get to, and memory you can’t get to easily. Memory used as a file system can be acquired using logical or physical acquisition. Electrically erasable programmable read-only memory (EEPROM) is harder to acquire.
Another consideration is that each device requires a different cable—even devices in the same family from the same manufacturer. Figure 10-6 shows a set of different USB connectors.6 Some devices require Micro USB B-type, USB 1.1 Micro, Mini USB B-type, female A-type, male A-type, or male B-type. The female A-type connector is displayed “upside down” in Figure 10-6 in order to make the pins visible. In addition to USB connectors, a DFI needs proprietary connectors such as those from Apple and Samsung (and, with Apple, it will vary depending on the generation of your device). You need a large collection of cables, or a single cable with a set of replaceable connectors.
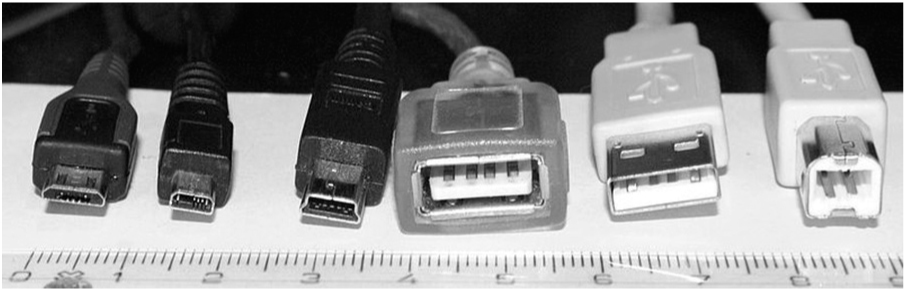
Figure 10-6 USB connectors
Mobile devices, especially smart phones, have progressed to the point where they compete with laptops in terms of storage and software. Given the range of software available, as well as the various types of network connectivity (Wi-Fi, mobile data, Bluetooth, NFC), a criminal can effectively keep all their information on a mobile device. Data sent via Bluetooth or near-field communication (NFC) is less subject to eavesdropping or wiretapping, but it does require the owners of the equipment to be in close proximity.
Given the “always on, always connected” nature of mobile devices, a DFI must take precautions when seizing the device, since a criminal can issue commands to lock the phone or to delete all data on that phone via the network. This means leaving the device connected to the network, but shielded from radio communication by means of a Faraday bag or another means of blocking the transmissions.
Once the device has been isolated from the network, the DFI can begin to acquire the data on that device. A DFI can acquire data from the device itself by mounting the device as a USB device, looking for data backups on a desktop machine (Macintosh or Windows), or using an external device to read memory not available via the file system. Once the DFI has acquired the data, analysis can proceed in much the same way as with data collected from any other digital device.
The first challenge that arises when working with mobile devices is simply trying to acquire the data. Tools and techniques can be classified in various ways: one classification system (NIST) categorizes each tool into one of five classes, as shown in Figure 10-7. As we progress from level 1 to level 5, the “methodologies involved in acquisition become more technical, invasive, time consuming, and expensive.”7
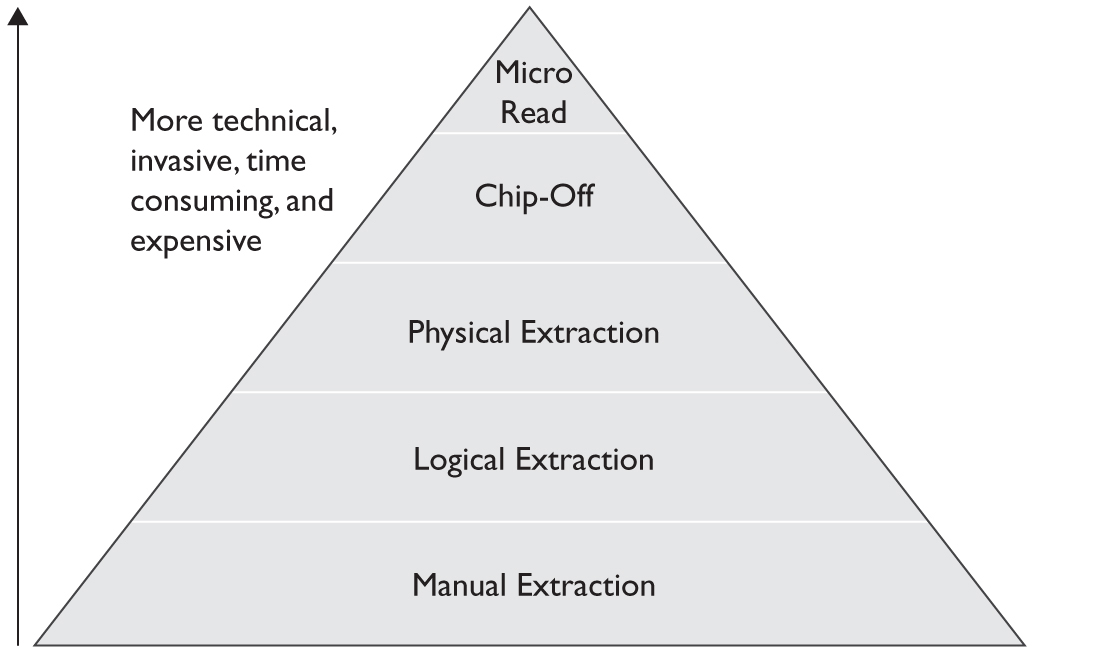
Figure 10-7 Classifications of acquisition methods (Source: Ayers, R., Brothers, S., Jansen, W. Guidelines on Mobile Device Forensic, NIST Special Publication 800-101, Revision 1, (dx.doi.org/10.6028/NIST.SP.800-101r1), p. 17.)
1. Manual Extraction This method only involves viewing and recording the information displayed on the device’s screen. There’s no access to deleted data, and navigating through the device’s menu hierarchy may have side effects such that crucial data are obscured or deleted. Information is collected by taking photographs of the device screen.
2. Logical Extraction The DFI connects to the mobile device using one of a number of wired or wireless network connections (USB, RS-232, IrDA, Wi-Fi, or Bluetooth).
3. Physical Extraction This method varies from acquiring an image of device storage mounted as a USB device to using a particular device called a flasher box to read protected memory.
4. Chip-Off Here, the DFI removes the memory chip from the device and creates a binary image of the contents. This image will need to be parsed by software that understands the logical and physical composition of the device (for example, understanding how the wear-leveling algorithm of the memory functions to gather logical contiguous memory blocks).
5. Micro Read The DFI captures the changes to the gates on a chip, using an electron microscope.
Depending on the importance of the case, a DFI would most usually use tools and techniques classified from levels 1 to 3. Chip-off techniques are the highest level currently available—while micro read is theoretically possible, time, expense, and training all weigh against this method.
Once the data have been obtained, tools can be used to perform a standard analysis based on the nature of the investigation. Are we looking for evidence that the owner committed a crime, such as storing illicit materials on the device? On the other hand, are we looking for evidence of connections to others who may have been involved in planning or committing the crime? Regardless, work with the data as you would any other digital evidence. Maintain the chain of custody; document all analysis work performed; and store the evidence in locations where it will not be destroyed by heat, cold, or dampness. Make sure that you consider and correlate all available information, including GPS location, cell locations, etc., in addition to messages sent and received and data stored or modified in the file system.
Many software tools are available to the DFI for analysis. Some focus on data extraction; others on data analysis. We’ll focus on three of them in this section.
EnCase Forensic 7.0 incorporates mobile device acquisition into the main product. Data can be acquired directly into EnCase Forensic and stored in EnCase evidence format. EnCase will usually recognize the appropriate OS simply by plugging in the device; recognized operating systems include Apple iOS, Google Android, BlackBerry, Windows Mobile OS, iTunes, and backup files and SIM cards. The predefined smart phone report will provide information about the data stored on the device.
Paraben Corporation (www.paraben.com) offers several different products that support mobile forensic investigations. Their Mobile Field Kit8 offers a one-stop shopping product for the DFI. Forensic hardware includes the Project-A-Phone ICD-8000 for photographing mobile device screens, a SIM reader, and a Bluetooth adapter. Acquisition hardware includes a remote charger, a multihead charging cable, AC power adapter, a DC car adapter, and a multimedia card reader. A Stronghold (Faraday) bag isolates live devices from their connected networks, and a Save-A-Phone drying bag helps preserve devices that have been submerged in water.
Device seizure cables are provided for many mobile products (iPhone, Samsung Galaxy tablets, Nokia, Samsung, Motorola, and LG phones). Software products available on a tablet computer include Device Seizure, Deployable Device Seizure, and analysis software. The link2 software is used for visualizing interactions between individuals identified by phone records, e-mails, SMS messages, and so on, and the P2 Commander Companion software is used to perform the actual analysis.
The Oxygen Forensic Suite 2014 provides an analytical tool and a stand-alone data extraction tool. The data extraction tool can retrieve and analyze data from various devices. Since each device is supported by a particular device driver, adding a new device only requires developing a driver. Figure 10-8 shows the device information screen when applied to a third-generation iPod. The panel on the left displays both common and extended device information, including the device model, serial number, and MAC addresses for both Wi-Fi and Bluetooth. The panel on the right contains information about the case (inspector, case number, and evidence number) and details about the device owner—useful when the device must be returned.
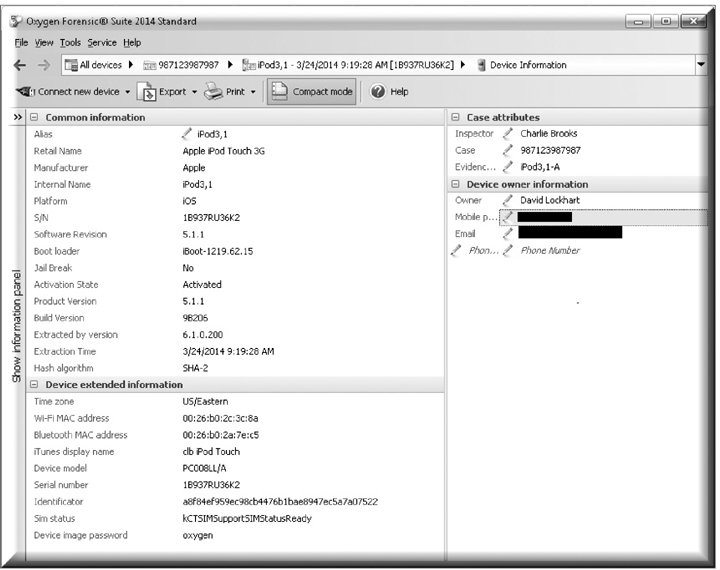
Figure 10-8 Oxygen Forensic Suite 2014 device information screen
The Standard edition supports the overall device information as well as displays for files, calendar, notes, and phonebook. A separate screen displays search results across all these data sources. The Analyst edition of the product includes timeline reporting of activities, aggregated contact information (all contacts, regardless of the method used to store them), and bookmarks for emphasizing key evidence. The tool also collects and displays web connections and location services, such as Wi-Fi hotspots, social graphs, a dictionary of a user’s vocabulary, and a catalog of links and statistics based on the types of communication (voice, SMS, e-mail, and so on).
The addition of time and location data to the investigation results in a much larger context for the investigator. Given that the purpose of an investigation is to “place the suspect at the keyboard,” the combination of the type of communication, duration, date and time, and results of that communication (files uploaded, downloaded, or deleted) can provide strong circumstantial evidence that the suspect was indeed the person who operated the mobile device.
A cellular network is a telephone network that divides a geographic area into a set of cells, each with its own transmission/reception tower. All mobile devices share similar characteristics: Hardware includes the radio portion (receiver/transmitter, or transceiver), as well as storage for managing personal information such as address, contacts, to-do lists, calendar, and so on. The most common mobile operating systems are Android, Windows, and iOS, although there are others, such as Symbian, Palm OS, WebOS, or Windows CE, that may appear depending on the age of the device.
A criminal can take advantage of smart phone features to store information about associates and contact them via e-mail, phone, or text messages as well as exchanging data using Bluetooth or NFC. Criminals can also use mobile devices to send spam, threatening, or harassing messages. Expanded storage supports storing and distributing outlawed materials such as child pornography.
Mobile devices provide their own sets of challenges. Some memory within the UICC isn’t accessible to user programs and requires special hardware and software to acquire. Devices can be locked or wiped clean of information by remote commands. Because of this, prior to beginning an investigation, the DFI must isolate the device from its networks by turning off communications, either by setting the device into “airplane” mode or encasing the device in a Faraday bag (taking precautions to ensure that the device has sufficient power so as not to empty the battery).
A DFI must take care to determine the time on the device in order to correlate the time of phone call and the location, perhaps cross-checking by using GPS data. Once data have been acquired, the process of analyzing data captured from a mobile device is essentially identical to the process used to capture any other digital information.
Forensic software for mobile devices can provide for data acquisition, data analysis, or both. Oxygen Forensic Suite 2014, Paraben’s Device Seizure hardware and software, and EnCase Forensic all have separate data acquisition software that can be run independently from their analysis software. All can integrate mobile device data into the context of a larger investigation.
1. Where would an investigator find details of calls made, subscriber information, and the locations of those calls?
A. BTS
B. ME
C. MCS
D. MS
2. When did encryption of voice traffic first appear?
A. LTE
B. 4G
C. 2G
D. 3G
3. What problem can result from putting a mobile device into a Faraday bag?
A. Moisture accumulation
B. Excessive battery drain
C. Overheating
D. Notification of loss of network connectivity
4. What kind of memory is not found in a SIM card?
A. ROM
B. RAM
C. EEPROM
D. NDROM
5. Which communication technologies require the sender and receiver to be in close proximity? (Choose all that apply.)
A. NFC
B. Bluetooth
C. Wi-Fi
D. IrDA
6. Using a standard file copy from a mobile device to local storage is an example of ______ acquisition.
A. Micro read
B. Physical
C. Manual
D. Logical
7. In addition to cell phone records, a device’s location can be determined by ________
A. Web sites visited
B. GPS
C. E-mail server domain
D. Default language for the device
8. The ability to delete the contents of a cell phone or tablet is known as _______.
A. Remote wiping
B. Secure deletion
C. Secure wiping
D. Remote delete
9. What would you need to support a new mobile device in Oxygen Forensic Suite 2014?
A. Analysis module
B. Device driver
C. Content-specific module
D. Multihead cable connector
10. What functions are usually provided by mobile forensic software? (Choose all that apply.)
A. Data extraction
B. Data analysis
C. Data verification
D. Data archiving
1. C. The MCS (mobile switch center) maintains the databases.
2. D. Encryption of cellular voice traffic first appeared in 3G.
3. B. Inserting a device into a Faraday bag can result in excessive battery drain.
4. D. NDROM is a distractor: SIM cards support ROM, RAM, and EEPROM.
5. A, B, D. IrDA, NFC, and Bluetooth require that the sender and receiver be within 50 feet or so of each other.
6. D. Logical acquisition.
7. B. GPS data can help pinpoint the location of a mobile device.
8. A. Remote wiping.
9. B. Oxygen Forensic Suite 2014 supports new devices by adding new device drivers.
10. A, B. Most mobile forensic suites will provide data extraction and analysis capabilities.
1. Ayers, R. et al. Guidelines on Mobile Device Forensics (DRAFT), NIST SP800-101 (revision 1). Retrieved from http://csrc.nist.gov/publications/PubsDrafts.html#SP-800-101-Rev.%201, p. 16.
2. EC-Council. Computer Forensics: Investigating Wireless Networks and Devices (NY: EC-Council, 2010), pp. 2–5.
3. Ayers, R. et al. Guidelines on Mobile Device Forensics (DRAFT), pp. 5–6.
4. Ibid.
5. Ayers, R. AAFF–Mobile Device Forensics. Retrieved from www.cftt.nist.gov/AAFS-MobileDeviceForensics.pdf.
6. Viitanen, V. USB Conectors.jpg. Retrieved from http://commons.wikimedia.org/wiki/File:Usb_connectors.JPG. Placed into the public domain by the creator of the work.
7. Ayers, R. et al. Guidelines on Mobile Device Forensics (DRAFT), p. 16.
8. Paraben’s Mobile Field Kit 2.0: Data and Specifications Sheet. Retrieved from www.paraben.com/downloads/mfk-brochure.pdf.