
In this chapter, you will learn how to
• Set up a computer forensics lab
• Discuss the investigative services in computer forensics
• Define the basic hardware requirements in a forensics lab
• List and summarize various hardware forensics tools
• Discuss the basic software requirements in a forensics lab
• List and summarize various software forensics tools
In the previous chapter, we discussed a process to follow before being called out on an investigation, and we talked about the kind of equipment you needed to bring to the crime scene.
If you’re a digital forensics investigator (DFI), you will need a workspace to perform your data extraction, your analysis, and your reporting. You’ll need a place to store your gear while you’re performing your analysis and a place to secure the evidence once you’ve taken custody of it. This workspace may be your own place of business, such as your home or a one-person office, or it may be one workspace among several others at a large firm. Regardless of the size of the organization and number of coworkers, both of these situations have much in common. We’ll talk about these commonalities in the rest of this chapter, as well as the differences.
Regardless of your role in the organization, the same two basic principles apply:
• You are responsible for the preservation and protection of evidence when it is in your custody; that is, you must prevent it from becoming “lost, stolen, or strayed.” In addition, avoid contamination of the evidence from environmental factors (smoke, dust, and others).
• You will maintain professional standards.1 Among them are standards that apply to lab accreditation, minimal education, experience and certification requirements, insurance, bond and liability standards, lab equipment, and software certifications. We’ll address some of these later on in this chapter.
There are two primary roles within a forensics laboratory. The lab manager is responsible for the operations of the lab itself, while the forensics scientist or the forensics examiner actually performs the analysis, writes the reports, and provides testimony if needed. A third role associated with the lab is that of the forensics investigator. The forensics investigator is usually a member of law enforcement who is initially responsible for securing the crime scene and acquiring the evidence. The role of the DFI as we have defined it combines the roles of the forensics examiner and the forensics investigator. A good DFI needs to understand how these two roles complement each other. In some organizations, a single person may act in both roles (this may be the case in corporate investigations). In larger organizations, these roles may be split out into separate organizations: Law enforcement collects the evidence, and the forensics examiners actually analyze the evidence.
If you anticipate forming your own digital forensics business, you’ll have to decide on what services you are going to offer. Chances are that they will be forensics investigative services, analysis, and expert testimony.
Investigative services is the actual retrieval of digital evidence. If you’re not a member of law enforcement, you will be doing this within a corporate environment. In either case, however, you will need to maintain proper procedures for searching, acquiring, and extracting information. We’ll have more to say on this in another chapter; for the moment, let’s just say that there are laws governing what you can get without a search warrant and what you can get without violating the suspect’s right to privacy. Recall that a warrant is only necessary for agents of the government or law enforcement, and doesn’t usually apply in a corporate environment unless the corporate investigation reveals that a crime was committed.
Examination and analysis services should remain the same whether this is a civil, criminal, or enterprise case. The best course to assume in all instances is that your actions and the evidence you extract will be presented in court. Moving from an enterprise investigation to a criminal investigation requires you involve the proper legal authorities immediately.

TIP Know who your external contacts are: local police, state police, and Federal Bureau of Investigation (FBI). Make a point of reaching out to them at the earliest possible moment to establish a working relationship.
If you believe that you might be called as a witness during a trial, make sure that you have documented everything. There are many ways to do this: pen and paper, creating a text note on a smart phone, taking a picture, creating a video, creating an audio note, or a mixture of these. Regardless of how you’ve chosen to record your initial notes, recapture them in a standard format as soon as possible to keep your memory fresh.
You might also wish to offer forensic deletion of data. As mentioned earlier, you will need a “forensically sterile” media to receive the copy of your digital data, and creating this “sterile” media means that you need to be familiar with data deletion standards. This “forensically sterile” media means that there are no data remaining from any previous use of that medium (usually referred to as data remanence). Data remanence can compromise security by leaving portions of files on a previously written disk; in the case of forensics, data remaining from a prior investigation could compromise the integrity of the data used for analysis in a current case.
Each country has its own data deletion standards. In the U.S. government, the old standard was DoD 5220.22-M, the National Industrial Security Program Operating Manual (NISPOM). The first version of this document described an algorithm for overwriting files multiple times with a random selection of characters. The latest version, however, doesn’t include any particular methods, but instead refers to standards for individual branches of the government, known as the “cognizant security agency.” The more general case is addressed by the National Institute of Standards (NIST) special publication 800-88, “Guide to Media Sanitization, Revision 1.”2
The original algorithm documented in NISPOM was to make three passes over the data. Each pass over the data would perform a different write operation, specifically writing a character (for example, 0x00), verify the write, write the character’s complement (0xFF in our example), verify the write, and then write a random character (0 × 97, for example) and verify the write. You may hear this described as “the DoD three-pass wipe” and sometimes as “the DoD seven-pass wipe.” The prevailing wisdom as of 2013 is that given today’s disk technology (especially for multigigabyte drives), one pass is sufficient. Take note that this doesn’t address issues with wiping a solid-state drive (SSD). For the latest recommendations, the NIST document is probably the most up-to-date.

EXAM TIP DOD 5220.22-M is often referred to as a source for standards for data destruction, although it no longer contains detailed instructions on how to destroy digital data.
Of the two main roles within the forensics laboratory, the lab manager is responsible for the overall operations of the lab. This includes staffing needs, workload estimates, arranging training for technical staff (recall that the SWDGE—Scientific Working Group on Digital Evidence—recommendations indicated requirements for training), and determining needs for accreditation. Technical staff includes anyone and everyone who actually accesses or handles the evidence. Your staffing needs will be determined in part by your anticipated workload for the coming year. As a lab manager, planning doesn’t stop once the facility is built and everyone moves in. Prior to moving in to the new facilities, a lab manager needs to have a business continuity/disaster recovery (BC/DR) plan in place. This is even more critical if the lab is going to handle dangerous materials (flammable, explosive, or biological). Disaster recovery is one aspect of business continuity and occurs during and immediately after the disaster. Business continuity itself is focused on how the company can continue to operate after the immediate effects of the disaster have ceased.
If you will be building a large forensics laboratory, you will need to be certified. The organization that provides that certification is the American Society of Crime Laboratory Directors (ASCLD)–their site is www.ascld.org–although the actual organization performing the certifications is ASCLD/LABS (www.ascld-lab.org). Their certification process is based on the ISO 17025:2005 standard, General Requirements for the Competence of Testing and Calibration Laboratories, and demonstrates that the lab’s technical and management systems meet the requirements established by that standard. Labs can apply for accreditation as either Forensic Science – Testing or Forensic Science – Calibration. A computer lab would fall under the Forensic Science – Testing category for Digital and Multimedia Evidence.3
If you’re starting out in business on your own, your choice of laboratory space may be straightforward. You may be setting up a home office, or you may be renting office space. If the actual space you’ll be using already exists, then you will need to evaluate this environment based on physical security needs. Figure 4-1 lists physical, technological, and administrative considerations for setting up your computer lab (as well as any other space where security is required—it’s not really a question of whether it’s required or not, but rather what are the appropriate levels of security given the assets you need to protect). You’ll notice that many of these considerations are exactly the same as for other kinds of enterprises. Information is information security after all, and the same principles apply when you have information such that you would incur a substantial loss (reputation, economic) if you lost the confidentiality, integrity, and availability (CIA) for that information.
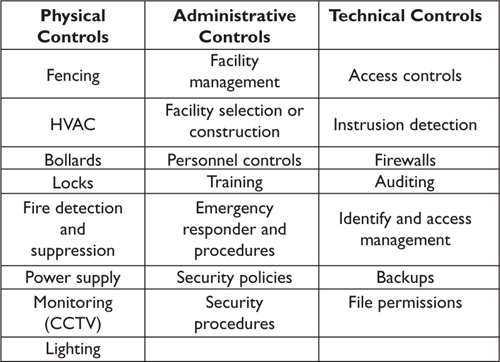
Figure 4-1 Types of security considerations (Source: Harris, S. CISSP All-In-One Exam Guide, Second Edition (CA: McGraw-Hill Education, 2003), pp. 256–257.)
On the other hand, if you’re responsible for building a large laboratory facility from scratch, such as a Regional Computer Forensics Laboratory (RCFL) for law enforcement, you will have a lot of work ahead of you. Typical administrative activities will include planning, generating a budget, determining the number of clients, and understanding the kinds of investigations you’ll be asked to perform. The document “Forensic Laboratories: Handbook for Facility Planning, Design, Construction, and Moving”4 lists multiple considerations; we’ll address a few of them here that are applicable to a computer forensics lab.
There is a truism in the real estate industry that states the value of a piece of property is dependent on three things: location, location, and location. The actual location of your lab requires careful planning, and considerations include access to emergency services (ambulance, fire, police), access to electrical power, and Internet communications.
At the heart of information security are mechanisms that we use to protect our assets: physical security (gates, locks, cameras, and dogs), logical security (passwords and others), and administrative (policies, background checks, and more). We can further categorize these mechanisms as to their intended purpose:
• Preventive Prevents a security incident from happening
• Detective Discovers if a security event is in progress or has already occurred
• Corrective Aimed at fixing the root cause of the vulnerability that gave rise to the incident
• Recovery Restores the computing environment back to a “good known state”
Other categories that are sometimes included are
• Deterrent Keeps an event from happening by creating an obstacle for the attacker
• Compensating A control inserted to compensate for lack of a permanent control
Some authors only list the first four, although all these types are used in information security design.
We can categorize a particular technique based on its category and its mechanism. For example, guard dogs might be considered as a preventive, deterrent, or compensating physical control. A popular overall strategy is to focus on preventive controls. Detective controls mean that you have discovered a security violation of some kind (either in progress or sometime in the past). Recovery and corrective controls are meant to stop the bleeding.
Physical security is the first consideration when constructing a forensics laboratory or when obtaining space for a lab. Two principles apply, regardless of whether you are setting up a home office or constructing a large regional forensics investigation center:
• Ensure the physical security of the lab.
• Ensure the physical security of the evidence within the lab.
One question you might well ask regarding the first principle is: What might destroy the entire facility? Some answers that come to mind are fire, flood, and explosion. A compensating control for those threats would be a location close to emergency services: a fire station, police, hospital, and ambulance service.5
The next step is to consider the physical security of the building itself and its employees. Make sure that lighting is sufficient (people can see and be seen). Don’t provide places for an intruder to conceal themselves (bushes close to an outside wall, clumps of bushes or evergreen trees).5 Parking is another concern: The NIST document “Forensic Laboratories: Handbook for Facility Planning, Design, Construction, and Moving” lists the following recommendations:
• Level 1 Insecure. Close to visitor entrance.
• Level 2 Partially secure. The lot should be fenced in. The lot provides controlled access to the facility by service people.
• Level 3 Secured. Restricted to staff parking. Gaining access to the parking facility requires some form of identification (perhaps a proximity key or a card-key).
• Level 4 High security. Restricted to specific individuals; access may require a thumbprint or palmprint reader or at least a combination lock.
Higher-security areas may require an intrusion alarm (this is true inside and outside the building). Guards can patrol the premises; guard dogs often act as a deterrent control. Closed-circuit TVs (CCTVs) can observe areas that aren’t physically visible to guards or other employees. Access to the laboratory proper should be via a single entrance that can be monitored. This doesn’t mean that there can’t be multiple exits from the lab (as would be the case for fire regulations), but these doors would probably be locked and alarmed. Last, windows should be kept closed, removing them from consideration as a way of entering the premises (but remember to add increased costs for heating, ventilation, and air conditioning—HVAC—into your budget). All access to the lab by nonemployees should be recorded in a log book: who they are, the reason for the visit, the time of day in and out, whom they are representing, and whom they are visiting.
Our second principle is protecting the evidence and the work products that are stored at the lab. Of all the disasters that can strike a laboratory, the most common and the most devastating is probably fire. Something as simple as the freezing of a disk actuator can start a fire due to overheating. Fire suppression systems are a necessity for a laboratory, especially class C fire extinguishers (dry chemical) for electrical fires and sprinkler systems according to building codes (don’t forget to include water damage as part of your disaster recovery plan).

EXAM TIP Know your fire extinguisher classification! Only certain kinds of fire extinguishers are suitable for electrical fires (water isn’t a good idea for obvious reasons).
Evidence storage (the evidence locker or fire-rated safe) should address both unwanted illegal access and damage by fire or water. These lockers should be constructed of steel, should always remain locked, and must be monitored closely. Access to the evidence locker must be limited to authorized personnel. How far you want to go depends on the kind of forensics investigations you’re doing, but you might want to consider recording all access to the locker, regardless of what evidence is actually accessed (and recorded in a chain-of-evidence form).6
The size of your workspace again will depend on your place and kind of employment. As a sole employee, you might have two separate tables: one with two forensics workstations that usually aren’t connected to any network and one with two plain workstations that have Internet connectivity. This is probably the safest configuration but begs the question whether remote access is needed to the forensics workstations. If remote access is required, consider the bandwidth requirements, not only for software performance but also for the transfer of data. Compute the bandwidth needed internally and externally. Other communications considerations include dial-up access (perhaps your site won’t be reachable via the Internet), disconnection from the network (in the case of forensics workstations), and relationships with your Internet service provider (ISP).
NOTE Consider this quick heuristic: Assume 10 bits per byte (this makes the math easier). A data rate of 16 Mbits/second is 1.6MB/second, or 96 Mbytes/minute, or 10.5 minutes to copy a 1GB file. That assumes you’re getting all the bandwidth on the line, and your drive can sustain that data rate, and on and on. It’s still true, at least in this case, that bigger and faster are better.
Why two instances of a forensics workstation and two instances of a plain workstation? We’ve already mentioned Internet connectivity—forensics workstations should only connect to the corporate local area network (LAN) or the Internet when absolutely necessary. A second instance of the forensics workstation can run certain forensics software that you can use to validate the results of other forensics software. Remember that you should be able to get the same results when different analysis tools claim to offer the same functions—a good case in point is disk imaging. Having two plain workstations allows you to perform updates and upgrades on one while still having the other as backup if the changes result in the first workstation becoming unusable.
Otherwise, planning for a forensic lab is much like planning for any other technical office space. A workspace should be large enough to allow collaboration with a colleague, and space enough for reference materials, lab manuals, and so on. Locking storage is another good thing to have, good for storing tools and any work in progress that shouldn’t be left lying around. You’ll need space for printers, scanners, extra hard-drives, and backup storage (disk or tape). Some of the material can be shared, but remember that some cases may require physical separation of materials. Don’t forget about conference rooms, large enough for your entire staff, and smaller conference rooms for working and discussion groups. You’ll need to stock other materials as well: cables, power cords, network interface cards (NICs)–all the incidentals that are required to support local and remote connectivity.
How much power do you need? If you’re running a large lab, you’ll want an uninterruptable power supply (UPS). How much amperage do you need? You’ll need power for lighting, both emergency and regular; all evidence sections (segregated by type of investigation, determining the kind of clearance needed); all the security devices; workstations; storage systems; and possibly such equipment as X-ray processing rooms and photo-processing rooms. Make sure that each workspace has sufficient power outlets (extension cords stretched throughout the workplace is an accident waiting to happen).
The software that you need in your lab requires you to be able to process information from old hardware and old operating systems (OS). These operating systems include multiple versions of Windows, Linux, various flavors of UNIX (Sun/Oracle Solaris), Apple Macintosh systems with OS X, and antiquated systems such as Commodore. More general applications include software to display graphical images (QuickView and IrfanView are examples of this software), accounting software (Quicken QuickBooks), personal databases (Microsoft Access, LibreOffice database), and video players (VLC, RealPlayer, Windows Media Player). For some of these applications, a full-featured demo version might suffice for a short investigation. That said, many demo versions will not allow results to be saved, or will print reports with the word “DEMO” conspicuously displayed on every page. Consider, too, that paying the license fee gets you updates and maintenance. Imagine the impact on your workload if you are stymied by a software bug and you have to wait for your HR and legal departments to negotiate and sign a maintenance contract. Equally important is the necessity of legally licensed software if your investigation should go to court. In some cases, an investigator may be subpoenaed to provide a list of software used in the analysis and investigation along with proof of license. Failure to do so may call into question the integrity of the investigator and the results of the tool.
Along with commercial software, you need to build up your forensics software toolset. Your toolset should support the following general activities:7
• Acquisition
• Validation and discrimination
• Extraction
• Reconstruction
• Reporting
How you go about obtaining these tools depends on your client base and how well your chosen tools are recognized throughout the forensics industry and by the courts. Guidance Software’s EnCase product and Accessdata’s FTK are both widely recognized and extensively used. Brian Carrier’s The Sleuth Kit and the Autopsy browser are freeware tools that provide many of the same capabilities (we’ll see a comparison of these three products in Chapter 8). Another well-established tool that I’ve used is X-Ways WinHex Forensics. Guidance Software and AccessData both offer training and certifications in the use of their tools. Becoming certified in the use of a tool is a good idea if you’re planning on standardizing on one or the other.

NOTE Ultimately, EnCase, FTK, or The Sleuth Kit should provide the essential capabilities to support an investigation. Your decision may rest on personal preference, the choice of your employer, or the standard used by your colleagues in law enforcement or security services.
How do we make a choice regarding what other tools to acquire? The NIST Information Technology Laboratory (www.nist.gov) runs the Computer Forensic Tool Testing (CFTT) project. The project is described as follows:
Overview: The CFTT project provides a measure of assurance that the tools used in the investigations of computer-related crimes produce valid results. It also supports other projects in the Department of Homeland Security’s overall computer forensics research program, such as the National Software Reference Library (NSRL).
Industry Need Addressed: There are approximately 150 different automated tools routinely used by law enforcement organizations to assist in the investigation of crimes involving computers. These tools are used to create critical evidence used in criminal cases, yet there are no standards or recognized tests by which to judge the validity of results produced by these tools.
Impact: The implementation of testing based on rigorous procedures will provide impetus for vendors to improve their tools and provide assurance that their results will stand up in court. […]. Law enforcement and other investigatory groups can use results as a basis for deciding when and how to use various tools.8
NIST publishes a catalog of tested software: “The Computer Forensics Tool Testing Handbook.”9 The most recent version is dated 2012, and the versions tested are not the most current. Regardless, the test results are useful for differentiating among the various tools and should prepare you to ask probing questions of the vendors when it comes time to actually write the check. NIST’s Computer Forensic Reference Data Sets (CFReDS) provide a baseline for tool testing by “[providing] to an investigator documented sets of simulated digital evidence for examination.”10 Each data set is documented as to its contents and its structure so you can tell, for example, that the tool found a particular byte offset at a particular byte location with the file.
Your hardware requirements will be dictated by whether you are performing searching and seizing in the field or whether you will be performing examination and analysis in the lab. One aspect of your choice is portability of hardware if you’re going to be carrying it into the field. In either case, common activities need to be done when acquiring evidence, regardless of where you’re doing the acquisition.
You need a well-stocked field toolkit when you go out on an investigation. You essentially need to prepare for any eventuality when you arrive at the crime scene, as demonstrated by the items in the accompanying list:6,11
• Faraday isolation bags or aluminum foil to block wireless communication, including 3G and 4G phones as well as Wi-Fi (802.11), Bluetooth, and near-field communication (NFC).
• Cardboard boxes (or original packaging if available at the scene) and cable ties.
• Notepads.
• Gloves.
• Various sizes of evidence bags: paper, antistatic, and so forth.
• Write-blocker (in case you have to perform a data acquisition on site). Some tests have indicated that a journaled file system, such as NT File System (NTFS), may actually write journaled information back to the device even if the device is mounted read-only. Figure 4-2 shows a typical attachment of a write-blocker between the disk and the acquiring device.
• Various kinds of cables (printer, USB, power).
• SIM card reader.
• Camera (photo and video capture) for capturing screen images as well as the crime scene itself.
• Remote chargers for your equipment and other digital devices found on the scene.
• Permanent markers (different colors).
• Evidence tape, crime scene tape, evidence stickers and tags.
• Flashlight (torch for our UK readers).
• Your fully charged cell phone, which can double as a camera and a note-taking device (written or audio).

Figure 4-2 Write-blocker
Every lab needs some kind of device that quickly can make copies of large disks. Time is your enemy here: The more time you spend moving bits around is time taken away from the timely resolution or determination of the extent of a criminal act. Once you have captured the device image, you will need hardware and software to archive and restore these images to your working storage, whether it be physically attached to your workstation or accessible via your LAN. Other hardware can include photographic hardware for still photographs (color and black and white) and video equipment.
We’ve already discussed mobile forensics laptops and forensics workstations in a previous chapter. It bears repeating that if you are buying a commercial product, you should buy the biggest iron you can afford. Load up on memory, disk interfaces (IDE, SCSI, US), and a SAN card (ISCSI or Fibre Channel) if you’re using a storage area network (SAN) for file storage. If you decide to build your own forensics workstation, obtain a write-blocker, a data acquisition tool, and a data analysis tool, and build your own custom hardware. However, building your own forensics workstation requires a degree of comfort and familiarity with computer hardware that is greater than a DFI has to know in order to perform an acquisition.
Make sure that lab procedures are documented and that lab staff is familiar with these procedures and actually follows them. Having this information readily available will be a big help when it comes time to get certification.
Depending on the sensitivity of an investigation, an investigator may need a private room such that no one else can observe the evidence collected. Private rooms will require additional hardware if physical isolation is needed. It’s possible that access to a virtual machine that accesses the data may be acceptable, but the use of virtualization technologies within the practice of digital forensics is still a work in progress.
Determining which computer forensics investigative services you wish to offer will determine what kind of hardware and software you will need, as well as the physical workspace you will need to support those services.
Setting up a computer forensics lab requires that you plan for the physical security of the building and for the lab itself, as well as protecting the evidence you have within the lab from loss or destruction.
Hardware requirements for your lab include hardware that will quickly create an image of a disk drive; photographic and video hardware; write-blockers for data acquisition; and all the cables, power supplies, power cords, and device readers that are needed to collect and transfer digital evidence.
Software requirements for your lab include software tools that support acquisition, validation and discrimination, extraction, reconstruction, and reporting. Examples of this kind of forensics software include EnCase, FTK, The Sleuth Kit and Autopsy, and WinHex Forensics.
1. Landscaping, lighting, and parking lot security are all examples of _______ security.
A. Technical
B. Physical
C. Logical
D. Administrative
2. True or false: DoD 5220.22-M is the final authority on data destruction techniques.
A. True
B. False
3. Which of the following is a characteristic that does not belong in a computer forensics lab?
A. Windows that open
B. Secured single entrance
C. Visitors logbook
D. Locking evidence (cage)
4. Which standard is often referred to as the source for data sanitization?
A. ISO 27001
B. NIST SP800-88r1
C. NAVSO P-5239-26 (MFM)
D. DoD 5220.22-M
5. What is the purpose of a write-blocker when used with digital imaging? Choose all that apply.
A. Prevent changes to the metadata of the device performing the capture
B. Avoid updating the last accessed timestamp on the captured files
C. Prevent changing the data on a drive being captured
D. Reads from the capturing machine will occur more quickly if writes are blocked
6. True or false: SIM card readers are general-purpose devices that can read data from a number of different device types.
A. True
B. False
7. Which of these would not provide shelter for an intruder?
A. Bushes
B. Clumps of bushes
C. Evergreens with low-hanging branches
D. A grove of maple trees
8. Which of these capabilities is a secondary requirement for investigative software?
A. Search
B. Cryptanalysis
C. Data recovery
D. Bit-stream copy
9. What are the reasons that you would use well-known forensics commercial tools? Choose all that apply.
A. Results judged acceptable in court
B. Well established in the industry
C. More capable than freeware tools
D. Commercial support and updates
10. The _______ project at NIST has the goal of evaluating forensics software against a set of criteria.
A. CFTT
B. FSTE
C. ESET
D. CERT
1. B. Landscaping, lighting, and parking lot security are all examples of physical security.
2. B. DoD 5220.20-M once specified a particular erasure algorithm, but now refers to different policies that apply to different government branches.
3. A. Windows that open are not a characteristic of a forensics laboratory since they may provide a way of forcibly entering the building.
4. D. DoD 5220.22-M (NISP Operating Manual) NISPOM.
5. A, B, and C. Write-blockers prevent any changes to the data on the drive from being captured. They do not increase the copying speed.
6. B. False. SIM card readers are meant specifically for mobile phones.
7. D. Maple trees are deciduous (lose their leaves in winter) and don’t provide low-hanging cover.
8. B. Cryptanalysis isn’t always needed in a forensics tool.
9. A, B, and D. Well-known commercial forensics toolkits have been proven within the industry, are more likely to have results accepted in court, and come with updates and support.
10. A. The Computer Forensics Tool Testing (CFTT) project tests multiple products in several categories according to a defined set of testing criteria and a standard set of test data.
1. ASCLD/LAB. “Guiding Principles of Professional Responsibility for Crime Laboratories and Forensic Scientists” (NC: ASCLD/LAB, 2013.)
2. Kissel, R. et al. “NIST SP800-88 Rev1: Guide to Media Sanitization” (MD: NIST, 2012). Retrieved from http://csrc.nist.gov/publications/PubsSPs.html.
3. ASCLD-LAB. “International Program Overview 2010 Edition” (NC: ASCLD/LAB, 2010), p. 5.
4. “Forensic Laboratories: Handbook for Facility Planning, Design, Construction, and Moving” (MD: NIST, 1998). Retrieved from http://www.crime-scene-investigator.net/forensiclabdesign.pdf.
5. “Forensic Laboratories: Handbook for Facility Planning, Design, Construction, and Moving” (MD: NIST, 1998), p. 20.
6. EC-Council. Computer Forensics: Investigation Procedures and Reponses (MA: Cengage, 2010), p. 2, 4–6.
7. Nelson, B. et al. Guide to Computer Forensics and Investigations (MA: Course Technology, 2010), p. 261.
8. CFTT Project Overview. Retrieved from http://www.cftt.nist.gov/project_overview.htm.
9. Computer Forensics Tool Testing Handbook (MD: NIST, 2012).
10. The CFReDS Project. Retrieved from http://www.cfreds.nist.gov.
11. Electronic Crime Scene Investigation, Second Edition (Washington, DC: USDoJ, 2008), pp. 13–14.