Chapter 2. Spanning Tree Protocol
This chapter covers the following subjects:
Spanning Tree Protocol Fundamentals: This section provides an overview of how switches become aware of other switches and prevent forwarding loops.
Rapid Spanning Tree Protocol: This section examines the improvements made to STP for faster convergence.
A good network design provides redundancy in devices and network links (that is, paths). The simplest solution involves adding a second link between switches to overcome a network link failure or ensuring that a switch is connected to at least two other switches in a topology. However, such topologies cause problems when a switch must forward broadcasts or when unknown unicast flooding occurs. Network broadcasts forward in a continuous loop until the link becomes saturated, and the switch is forced to drop packets. In addition, the MAC address table must constantly change ports as the packets make loops. The packets continue to loop around the topology because there is not a time-to-live (TTL) mechanism for Layer 2 forwarding. The switch CPU utilization increases, as does memory consumption, which could result in the crashing of the switch.
This chapter explains how switches prevent forwarding loops while allowing for redundant links with the use of Spanning Tree Protocol (STP) and Rapid Spanning Tree Protocol (RSTP). Two other chapters also explain STP-related topics:
Chapter 3, “Advanced STP Tuning”: Covers advanced STP topics such as BPDU guard and BPDU filter.
Chapter 4, “Multiple Spanning Tree Protocol”: Covers Multiple Spanning Tree Protocol.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read the entire chapter. If you miss no more than one of these self-assessment questions, you might want to move ahead to the “Exam Preparation Tasks” section. Table 2-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A, “Answers to the ‘Do I Know This Already?’ Quiz Questions.”
Table 2-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping
Foundation Topics Section |
Questions |
Spanning Tree Protocol Fundamentals |
1–6 |
Rapid Spanning Tree Protocol |
7–9 |
1. How many different BPDU types are there?
One
Two
Three
Four
2. What attributes are used to elect a root bridge?
Switch port priority
Bridge priority
Switch serial number
Path cost
3. The original 802.1D specification assigns what value to a 1 Gbps interface?
1
2
4
19
4. All of the ports on a root bridge are assigned what role?
Root port
Designated port
Superior port
Master port
5. Using default settings, how long does a port stay in the listening state?
2 seconds
5 seconds
10 seconds
15 seconds
6. Upon receipt of a configuration BPDU with the topology change flag set, how do the downstream switches react?
By moving all ports to a blocking state on all switches
By flushing out all MAC addresses from the MAC address table
By temporarily moving all non-root ports to a listening state
By flushing out all old MAC addresses from the MAC address table
By updating the Topology Change version flag on the local switch database
7. Which of the following is not an RSTP port state?
Blocking
Listening
Learning
Forwarding
8. True or false: In a large Layer 2 switch topology, the infrastructure must fully converge before any packets can be forwarded.
True
False
9. True or false: In a large Layer 2 switch topology that is running RSTP, the infrastructure must fully converge before any packets can be forwarded.
True
False
Answers to the “Do I Know This Already?” quiz:
1 B
2 B
3 C
4 B
5 D
6 D
7 A, B
8 B
9 B
Foundation Topics
Spanning Tree Protocol Fundamentals
Spanning Tree Protocol (STP) enables switches to become aware of other switches through the advertisement and receipt of bridge protocol data units (BPDUs). STP builds a Layer 2 loop-free topology in an environment by temporarily blocking traffic on redundant ports. STP operates by selecting a specific switch as the master switch and running a tree-based algorithm to identify which redundant ports should not forward traffic.
STP has multiple iterations:
802.1D, which is the original specification
Per-VLAN Spanning Tree (PVST)
Per-VLAN Spanning Tree Plus (PVST+)
802.1W Rapid Spanning Tree Protocol (RSTP)
802.1S Multiple Spanning Tree Protocol (MST)
Catalyst switches now operate in PVST+, RSTP, and MST modes. All three of these modes are backward compatible with 802.1D.
IEEE 802.1D STP
The original version of STP comes from the IEEE 802.1D standards and provides support for ensuring a loop-free topology for one VLAN. This topic is vital to understand as a foundation for Rapid Spanning Tree Protocol (RSTP) and Multiple Spanning Tree Protocol (MST).
802.1D Port States
In the 802.1D STP protocol, every port transitions through the following states:
Disabled: The port is in an administratively off position (that is, shut down).
Blocking: The switch port is enabled, but the port is not forwarding any traffic to ensure that a loop is not created. The switch does not modify the MAC address table. It can only receive BPDUs from other switches.
Listening: The switch port has transitioned from a blocking state and can now send or receive BPDUs. It cannot forward any other network traffic. The duration of the state correlates to the STP forwarding time. The next port state is learning.
Learning: The switch port can now modify the MAC address table with any network traffic that it receives. The switch still does not forward any other network traffic besides BPDUs. The duration of the state correlates to the STP forwarding time. The next port state is forwarding.
Forwarding: The switch port can forward all network traffic and can update the MAC address table as expected. This is the final state for a switch port to forward network traffic.
Broken: The switch has detected a configuration or an operational problem on a port that can have major effects. The port discards packets as long as the problem continues to exist.
802.1D Port Types

The 802.1D STP standard defines the following three port types:
Root port (RP): A network port that connects to the root bridge or an upstream switch in the spanning-tree topology. There should be only one root port per VLAN on a switch.
Designated port (DP): A network port that receives and forwards BPDU frames to other switches. Designated ports provide connectivity to downstream devices and switches. There should be only one active designated port on a link.
Blocking port: A network that is not forwarding traffic because of STP calculations.

STP Key Terminology
Several key terms are related to STP:
Root bridge: The root bridge is the most important switch in the Layer 2 topology. All ports are in a forwarding state. This switch is considered the top of the spanning tree for all path calculations by other switches. All ports on the root bridge are categorized as designated ports.
Bridge protocol data unit (BPDU): This network packet is used for network switches to identify a hierarchy and notify of changes in the topology. A BPDU uses the destination MAC address 01:80:c2:00:00:00. There are two types of BPDUs:
Configuration BPDU: This type of BPDU is used to identify the root bridge, root ports, designated ports, and blocking ports. The configuration BPDU consists of the following fields: STP type, root path cost, root bridge identifier, local bridge identifier, max age, hello time, and forward delay.
Topology change notification (TCN) BPDU: This type of BPDU is used to communicate changes in the Layer 2 topology to other switches. This is explained in greater detail later in the chapter.
Root path cost: This is the combined cost for a specific path toward the root switch.
System priority: This 4-bit value indicates the preference for a switch to be root bridge. The default value is 32,768.
System ID extension: This 12-bit value indicates the VLAN that the BPDU correlates to. The system priority and system ID extension are combined as part of the switch’s identification of the root bridge.
Root bridge identifier: This is a combination of the root bridge system MAC address, system ID extension, and system priority of the root bridge.
Local bridge identifier: This is a combination of the local switch’s bridge system MAC address, system ID extension, and system priority of the root bridge.
Max age: This is the maximum length of time that passes before a bridge port saves its BPDU information. The default value is 20 seconds, but the value can be configured with the command spanning-tree vlan vlan-id max-age maxage. If a switch loses contact with the BPDU’s source, it assumes that the BPDU information is still valid for the duration of the Max Age timer.
Hello time: This is the time that a BPDU is advertised out of a port. The default value is 2 seconds, but the value can be configured to 1 to 10 seconds with the command spanning-tree vlan vlan-id hello-time hello-time.
Forward delay: This is the amount of time that a port stays in a listening and learning state. The default value is 15 seconds, but the value can be changed to a value of 15 to 30 seconds with the command spanning-tree vlan vlan-id forward-time forward-time.
Spanning Tree Path Cost
The interface STP cost is an essential component for root path calculation because the root path is found based on the cumulative interface STP cost to reach the root bridge. The interface STP cost was originally stored as a 16-bit value with a reference value of 20 Gbps. As switches have developed with higher-speed interfaces, 10 Gbps might not be enough. Another method, called long mode, uses a 32-bit value and uses a reference speed of 20 Tbps. The original method, known as short mode, is the default mode.
Table 2-2 displays a list of interface speeds and the correlating interface STP costs.
Table 2-2 Default Interface STP Port Costs
Link Speed |
Short-Mode STP Cost |
Long-Mode STP Cost |
10 Mbps |
100 |
2,000,000 |
100 Mbps |
19 |
200,000 |
1 Gbps |
4 |
20,000 |
10 Gbps |
2 |
2,000 |
20 Gbps |
1 |
1,000 |
100 Gbps |
1 |
200 |
1 Tbps |
1 |
20 |
10 Tbps |
1 |
2 |
Devices can be configured with the long-mode interface cost with the command spanning-tree pathcost method long. The entire Layer 2 topology should use the same setting for every device in the environment to ensure a consistent topology. Before enabling this setting in an environment, it is important to conduct an audit to ensure that the setting will work.
Building the STP Topology
This section focuses on the logic switches use to build an STP topology. Figure 2-1 shows the simple topology used here to demonstrate some important spanning tree concepts. The configurations on all the switches do not include any customizations for STP, and the focus is primarily on VLAN 1, but VLANs 10, 20, and 99 also exist in the topology. SW1 has been identified as the root bridge, and the RP, DP, and blocking ports have been identified visually to assist in the following sections.

Figure 2-1 Basic STP Topology

Root Bridge Election
The first step with STP is to identify the root bridge. As a switch initializes, it assumes that it is the root bridge and uses the local bridge identifier as the root bridge identifier. It then listens to its neighbor’s configuration BPDU and does the following:
If the neighbor’s configuration BPDU is inferior to its own BPDU, the switch ignores that BPDU.
If the neighbor’s configuration BPDU is preferred to its own BPDU, the switch updates its BPDUs to include the new root bridge identifier along with a new root path cost that correlates to the total path cost to reach the new root bridge. This process continues until all switches in a topology have identified the root bridge switch.
STP deems a switch more preferable if the priority in the bridge identifier is lower than the priority of the other switch’s configuration BPDUs. If the priority is the same, then the switch prefers the BPDU with the lower system MAC.
In Figure 2-1, SW1 can be identified as the root bridge because its system MAC address (0062.ec9d.c500) is the lowest in the topology. This is further verified by using the command show spanning-tree root to display the root bridge. Example 2-1 demonstrates this command being executed on SW1. The output includes the VLAN number, root bridge identifier, root path cost, hello time, max age time, and forwarding delay. Because SW1 is the root bridge, all ports are designated ports, so the Root Port field is empty. This is one way to verify that the connected switch is the root bridge for the VLAN.
Example 2-1 Verifying the STP Root Bridge
SW1# show spanning-tree root
Root Hello Max Fwd
Vlan Root ID Cost Time Age Dly Root Port
---------------- -------------------- --------- ----- --- --- ------------
VLAN0001 32769 0062.ec9d.c500 0 2 20 15
VLAN0010 32778 0062.ec9d.c500 0 2 20 15
VLAN0020 32788 0062.ec9d.c500 0 2 20 15
VLAN0099 32867 0062.ec9d.c500 0 2 20 15
In Example 2-1, notice that the root bridge priority on SW1 for VLAN 1 is 32,769 and not 32,768. The priority in the configuration BPDU packets is actually the priority plus the value of the sys-id-ext (which is the VLAN number). You can confirm this by looking at VLAN 10, which has a priority of 32,778, which is 10 higher than 32,768.
The advertised root path cost is always the value calculated on the local switch. As the BPDU is received, the local root path cost is the advertised root path cost plus the local interface port cost. The root path cost is always zero on the root bridge. Figure 2-2 illustrates the root path cost as SW1 advertises the configuration BPDUs toward SW3 and then SW3’s configuration BPDUs toward SW5.

Figure 2-2 STP Path Cost Advertisements
Example 2-2 shows the output of the show spanning-tree root command run on SW2 and SW3. The Root ID field is exactly the same as for SW1, but the root path cost has changed to 4 because both switches must use the 1 Gbps link to reach SW1. Gi1/0/1 has been identified on both switches as the root port.
Example 2-2 Identifying the Root Ports
SW2# show spanning-tree root
Root Hello Max Fwd
Vlan Root ID Cost Time Age Dly Root Port
---------------- -------------------- --------- ----- --- --- ------------
VLAN0001 32769 0062.ec9d.c500 4 2 20 15 Gi1/0/1
VLAN0010 32778 0062.ec9d.c500 4 2 20 15 Gi1/0/1
VLAN0020 32788 0062.ec9d.c500 4 2 20 15 Gi1/0/1
VLAN0099 32867 0062.ec9d.c500 4 2 20 15 Gi1/0/1
SW3# show spanning-tree root
Root Hello Max Fwd
Vlan Root ID Cost Time Age Dly Root Port
---------------- -------------------- --------- ----- --- --- ------------
VLAN0001 32769 0062.ec9d.c500 4 2 20 15 Gi1/0/1
VLAN0010 32778 0062.ec9d.c500 4 2 20 15 Gi1/0/1
VLAN0020 32788 0062.ec9d.c500 4 2 20 15 Gi1/0/1
VLAN0099 32867 0062.ec9d.c500 4 2 20 15 Gi1/0/1

Locating Root Ports
After the switches have identified the root bridge, they must determine their root port (RP). The root bridge continues to advertise configuration BPDUs out all of its ports. The switch compares the BPDU information to identify the RP. The RP is selected using the following logic (where the next criterion is used in the event of a tie):
The interface associated to lowest path cost is more preferred.
The interface associated to the lowest system priority of the advertising switch is preferred next.
The interface associated to the lowest system MAC address of the advertising switch is preferred next.
When multiple links are associated to the same switch, the lowest port priority from the advertising switch is preferred.
When multiple links are associated to the same switch, the lower port number from the advertising switch is preferred.
Example 2-3 shows the output of running the command show spanning-tree root on SW4 and SW5. The Root ID field is exactly the same as on SW1, SW2, and SW3 in Examples 2-1 and 2-2. However, the root path cost has changed to 8 because both switches (SW4 and SW5) must traverse two 1 Gbps link to reach SW1. Gi1/0/2 was identified as the RP for SW4, and Gi1/0/3 was identified as the RP for SW5.
Example 2-3 Identifying the Root Ports on SW4 and SW5
SW4# show spanning-tree root
Root Hello Max Fwd
Vlan Root ID Cost Time Age Dly Root Port
---------------- -------------------- --------- ----- --- --- ------------
VLAN0001 32769 0062.ec9d.c500 8 2 20 15 Gi1/0/2
VLAN0010 32778 0062.ec9d.c500 8 2 20 15 Gi1/0/2
VLAN0020 32788 0062.ec9d.c500 8 2 20 15 Gi1/0/2
VLAN0099 32867 0062.ec9d.c500 8 2 20 15 Gi1/0/2
SW5# show spanning-tree root
Root Hello Max Fwd
Vlan Root ID Cost Time Age Dly Root Port
---------------- -------------------- --------- ----- --- --- ------------
VLAN0001 32769 0062.ec9d.c500 8 2 20 15 Gi1/0/3
VLAN0010 32778 0062.ec9d.c500 8 2 20 15 Gi1/0/3
VLAN0020 32788 0062.ec9d.c500 8 2 20 15 Gi1/0/3
VLAN0099 32867 0062.ec9d.c500 8 2 20 15 Gi1/0/
The root bridge can be identified for a specific VLAN through the use of the command show spanning-tree root and examination of the CDP or LLDP neighbor information to identify the host name of the RP switch. The process can be repeated until the root bridge is located.
Locating Blocked Designated Switch Ports
Now that the root bridge and RPs have been identified, all other ports are considered designated ports. However, if two non-root switches are connected to each other on their designated ports, one of those switch ports must be set to a blocking state to prevent a forwarding loop. In our sample topology, this would apply to the following links:
SW2 Gi1/0/3 ← → SW3 Gi1/0/2
SW4 Gi1/0/5 ← → SW5 Gi1/0/4
SW4 Gi1/0/6 ← → SW5 Gi1/0/5
The logic to calculate which ports should be blocked between two non-root switches is as follows:
The interface is a designated port and must not be considered an RP.
The switch with the lower path cost to the root bridge forwards packets, and the one with the higher path cost blocks. If they tie, they move on to the next step.
The system priority of the local switch is compared to the system priority of the remote switch. The local port is moved to a blocking state if the remote system priority is lower than that of the local switch. If they tie, they move on to the next step.
The system MAC address of the local switch is compared to the system priority of the remote switch. The local designated port is moved to a blocking state if the remote system MAC address is lower than that of the local switch. If the links are connected to the same switch, they move on to the next step.
All three links (SW2 Gi1/0/3 ↔ SW3 Gi1/0/2, SW4 Gi1/0/5 ↔ SW5 Gi1/0/4, andSW4 Gi1/0/6 ↔ SW5 Gi1/0/5) would use step 4 of the process just listed to identify which port moves to a blocking state. SW3’s Gi1/0/2, SW5’s Gi1/0/5, and SW5’s Gi1/0/6 ports would all transition to a blocking state because the MAC addresses are lower for SW2 and SW4.
The command show spanning-tree [vlan vlan-id] provides useful information for locating a port’s STP state. Example 2-4 shows this command being used to show SW1’s STP information for VLAN 1. The first portion of the output displays the relevant root bridge’s information, which is followed by the local bridge’s information. The associated interface’s STP port cost, port priority, and port type are displayed as well. All of SW1’s ports are designated ports (Desg) because SW1 is the root bridge.
These port types are expected on Catalyst switches:
Point-to-point (P2P): This port type connects with another network device (PC or RSTP switch).
P2P edge: This port type specifies that portfast is enabled on this port.
Example 2-4 Viewing SW1’s STP Information
SW1# show spanning-tree vlan 1 VLAN0001 Spanning tree enabled protocol rstp ! This section displays the relevant information for the STP root bridge Root ID Priority 32769 Address 0062.ec9d.c500 This bridge is the root Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec ! This section displays the relevant information for the Local STP bridge Bridge ID Priority 32769 (priority 32768 sys-id-ext 1) Address 0062.ec9d.c500 Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec Aging Time 300 sec Interface Role Sts Cost Prio.Nbr Type ------------------- ---- --- --------- -------- -------------------------------- Gi1/0/2 Desg FWD 4 128.2 P2p Gi1/0/3 Desg FWD 4 128.3 P2p Gi1/0/14 Desg FWD 4 128.14 P2p Edge
Example 2-5 shows the STP topology for SW2 and SW3. Notice that in the first root bridge section, the output provides the total root path cost and the port on the switch that is identified as the RP.
All the ports on SW2 are in a forwarding state, but port Gi1/0/2 on SW3 is in a blocking (BLK) state. Specifically, SW3’s Gi1/0/2 port has been designated as an alternate port to reach the root in the event that the Gi1/0/1 connection fails.
The reason that SW3’s Gi1/0/2 port rather than SW2’s Gi1/0/3 port was placed into a blocking state is that SW2’s system MAC address (0081.c4ff.8b00) is lower than SW3’s system MAC address (189c.5d11.9980). This can be deduced by looking at the system MAC addresses in the output and confirmed by the topology in Figure 2-1.
Example 2-5 Verifying the Root and Blocking Ports for a VLAN
SW2# show spanning-tree vlan 1
VLAN0001
Spanning tree enabled protocol rstp
Root ID Priority 32769
Address 0062.ec9d.c500
Cost 4
Port 1 (GigabitEthernet1/0/1)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32769 (priority 32768 sys-id-ext 1)
Address 0081.c4ff.8b00
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300 sec
Interface Role Sts Cost Prio.Nbr Type
------------------- ---- --- --------- -------- --------------------------------
Gi1/0/1 Root FWD 4 128.1 P2p
Gi1/0/3 Desg FWD 4 128.3 P2p
Gi1/0/4 Desg FWD 4 128.4 P2p
SW3# show spanning-tree vlan 1 VLAN0001 Spanning tree enabled protocol rstp ! This section displays the relevant information for the STP root bridge Root ID Priority 32769 Address 0062.ec9d.c500 Cost 4 Port 1 (GigabitEthernet1/0/1) Hello Time 2 sec Max Age 20 sec Forward Delay 15 se ! This section displays the relevant information for the Local STP bridge Bridge ID Priority 32769 (priority 32768 sys-id-ext 1) Address 189c.5d11.9980 Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec Aging Time 300 sec Interface Role Sts Cost Prio.Nbr Type ------------------- ---- --- --------- -------- -------------------------------- Gi1/0/1 Root FWD 4 128.1 P2p Gi1/0/2 Altn BLK 4 128.2 P2p Gi1/0/5 Desg FWD 4 128.5 P2
Verification of VLANS on Trunk Links
All the interfaces that participate in a VLAN are listed in the output of the command show spanning-tree. Using this command can be a daunting task for trunk ports that carry multiple VLANs. The output includes the STP state for every VLAN on an interface for every switch interface. The command show spanning-tree interface interface-id [detail] drastically reduces the output to the STP state for only the specified interface. The optional detail keyword provides information on port cost, port priority, number of transitions, link type, and count of BPDUs sent or received for every VLAN supported on that interface. Example 2-6 demonstrates the use of both iterations of the command.
If a VLAN is missing on a trunk port, you can check the trunk port configuration for accuracy. Trunk port configuration is covered in more detail in Chapter 5, “VLAN Trunks and EtherChannel Bundles.” A common problem is that a VLAN may be missing from the allowed VLANs list for that trunk interface.
Example 2-6 Viewing VLANs Participating with STP on an Interface
SW3# show spanning-tree interface gi1/0/1 Vlan Role Sts Cost Prio.Nbr Type ------------------- ---- --- --------- -------- -------------------------------- VLAN0001 Root FWD 4 128.1 P2p VLAN0010 Root FWD 4 128.1 P2p VLAN0020 Root FWD 4 128.1 P2p VLAN0099 Root FWD 4 128.1 P2p
SW3# show spanning-tree interface gi1/0/1 detail ! Output omitted for brevity Port 1 (GigabitEthernet1/0/1) of VLAN0001 is root forwarding Port path cost 4, Port priority 128, Port Identifier 128.1. Designated root has priority 32769, address 0062.ec9d.c500 Designated bridge has priority 32769, address 0062.ec9d.c500 Designated port id is 128.3, designated path cost 0 Timers: message age 16, forward delay 0, hold 0 Number of transitions to forwarding state: 1 Link type is point-to-point by default BPDU: sent 15, received 45908 Port 1 (GigabitEthernet1/0/1) of VLAN0010 is root forwarding Port path cost 4, Port priority 128, Port Identifier 128.1. Designated root has priority 32778, address 0062.ec9d.c500 Designated bridge has priority 32778, address 0062.ec9d.c500 Designated port id is 128.3, designated path cost 0 Timers: message age 15, forward delay 0, hold 0 Number of transitions to forwarding state: 1 Link type is point-to-point by default MAC BPDU: sent 15, received 22957 ..

STP Topology Changes
In a stable Layer 2 topology, configuration BPDUs always flow from the root bridge toward the edge switches. However, changes in the topology (for example, switch failure, link failure, or links becoming active) have an impact on all the switches in the Layer 2 topology.
The switch that detects a link status change sends a topology change notification (TCN) BPDU toward the root bridge, out its RP. If an upstream switch receives the TCN, it sends out an acknowledgment and forwards the TCN out its RP to the root bridge.
Upon receipt of the TCN, the root bridge creates a new configuration BPDU with the Topology Change flag set, and it is then flooded to all the switches. When a switch receives a configuration BPDU with the Topology Change flag set, all switches change their MAC address timer to the forwarding delay timer (with a default of 15 seconds). This flushes out MAC addresses for devices that have not communicated in that 15-second window but maintains MAC addresses for devices that are actively communicating.
Flushing the MAC address table prevents a switch from sending traffic to a host that is no longer reachable by that port. However, a side effect of flushing the MAC address table is that it temporarily increases the unknown unicast flooding while it is rebuilt. Remember that this can impact hosts because of their CSMA/CD behavior. The MAC address timer is then reset to normal (300 seconds by default) after the second configuration BPDU is received.
TCNs are generated on a VLAN basis, so the impact of TCNs directly correlates to the number of hosts in a VLAN. As the number of hosts increase, the more likely TCN generation is to occur and the more hosts that are impacted by the broadcasts. Topology changes should be checked as part of the troubleshooting process. Chapter 3 describes mechanisms such as portfast that modify this behavior and reduce the generation of TCNs.
Topology changes are seen with the command show spanning-tree [vlan vlan-id] detail on a switch bridge. The output of this command shows the topology change count and time since the last change has occurred. A sudden or continuous increase in TCNs indicates a potential problem and should be investigated further for flapping ports or events on a connected switch.
Example 2-7 displays the output of the show spanning-tree vlan 10 detail command. Notice that it includes the time since the last TCN was detected and the interface from which the TCN originated.
Example 2-7 Viewing a Detailed Version of Spanning Tree State
SW1# show spanning-tree vlan 10 detail VLAN0010 is executing the rstp compatible Spanning Tree protocol Bridge Identifier has priority 32768, sysid 10, address 0062.ec9d.c500 Configured hello time 2, max age 20, forward delay 15, transmit hold-count 6 We are the root of the spanning tree Topology change flag not set, detected flag not set Number of topology changes 42 last change occurred 01:02:09 ago from GigabitEthernet1/0/2 Times: hold 1, topology change 35, notification 2 hello 2, max age 20, forward delay 15 Timers: hello 0, topology change 0, notification 0, aging 30
The process of determining why TCNs are occurring involves checking a port to see whether it is connected to a host or to another switch. If it is connected to another switch, you need to connect to that switch and repeat the process of examining the STP details. You might need to examine CDP tables or your network documentation. You can execute the show spanning-tree [vlan vlan-id] detail command again to find the last switch in the topology to identify the problematic port.
Converging with Direct Link Failures
When a switch loses power or reboots, or when a cable is removed from a port, the Layer 1 signaling places the port into a down state, which can notify other processes, such as STP. STP considers such an event a direct link failure and can react in one of three ways, depending upon the topology. This section explains each of these three possible scenarios with a simple three-switch topology where SW1 is the root switch.
Direct Link Failure Scenario 1
In the first scenario, the link between SW2 and SW3 fails. SW2’s Gi1/0/3 port is the DP, and SW3’s Gi1/0/2 port is in a blocking state. Because SW3’s Gi1/0/2 port is already in a blocking state, there is no impact to traffic between the two switches as they both transmit data through SW1. Both SW2 and SW3 will advertise a TCN toward the root switch, which results in the Layer 2 topology flushing its MAC address table.
Direct Link Failure Scenario 2
In the second scenario, the link between SW1 and SW3 fails. Network traffic from SW1 or SW2 toward SW3 is impacted because SW3’s Gi1/0/2 port is in a blocking state. Figure 2-3 illustrates the failure scenario and events that occur to stabilize the STP topology:

Figure 2-3 Convergence with Direct Link Failure Between SW1 and SW3
Phase 1. SW1 detects a link failure on its Gi1/0/3 interface. SW3 detects a link failure on its Gi1/0/1 interface.
Phase 2. Normally SW1 would generate a TCN flag out its root port, but it is the root bridge, so it does not. SW1 would advertise a TCN if it were not the root bridge.
SW3 removes its best BPDU received from SW1 on its Gi1/0/1 interface because it is now in a down state. At this point, SW3 would attempt to send a TCN toward the root switch to notify it of a topology change; however, its root port is down.
Phase 3. SW1 advertises a configuration BPDU with the Topology Change flag out of all its ports. This BPDU is received and relayed to all switches in the environment.
Phase 4. SW2 and SW3 receive the configuration BPDU with the Topology Change flag. These switches then reduce the MAC address age timer to the forward delay timer to flush out older MAC entries. In this phase, SW2 does not know what changed in the topology.
Phase 5. SW3 must wait until it hears from the root bridge again or the Max Age timer expires before it can reset the port state and start to listen for BPDUs on the Gi1/0/2 interface (which was in the blocking state previously).
The total convergence time for SW3 is 30 seconds: 15 seconds for the listening state and 15 seconds for the learning state before SW3’s Gi1/0/2 can be made the RP.
Direct Link Failure Scenario 3
In the third scenario, the link between SW1 and SW2 fails. Network traffic from SW1 or SW3 toward SW2 is impacted because SW3’s Gi1/0/2 port is in a blocking state. Figure 2-4 illustrates the failure scenario and events that occur to stabilize the STP topology:
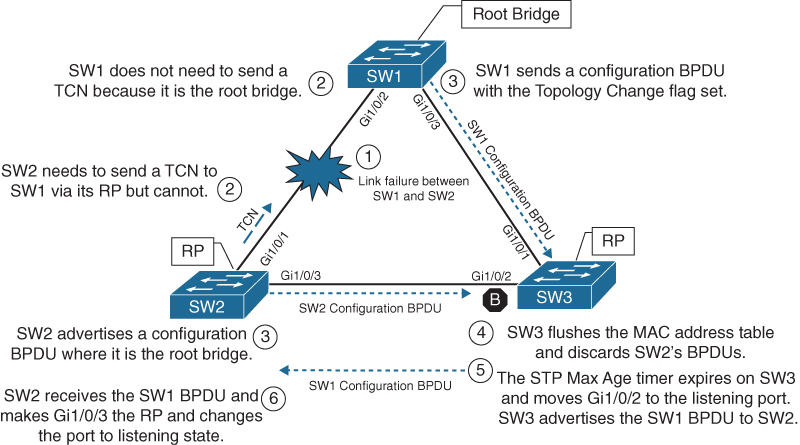
Figure 2-4 Convergence with Direct Link Failure Between SW1 and SW2
Phase 1. SW1 detects a link failure on its Gi1/0/1 interface. SW2 detects a link failure on its Gi1/0/3 interface.
Phase 2. Normally SW1 would generate a TCN flag out its root port, but it is the root bridge, so it does not. SW1 would advertise a TCN if it were not the root bridge.
SW2 removes its best BPDU received from SW1 on its Gi1/0/1 interface because it is now in a down state. At this point, SW2 would attempt to send a TCN toward the root switch to notify it of a topology change; however, its root port is down.
Phase 3. SW1 advertises a configuration BPDU with the Topology Change flag out of all its ports. This BPDU is then received and relayed to SW3. SW3 cannot relay this to SW2 as its Gi1/0/2 port is still in a blocking state.
SW2 assumes that it is now the root bridge and advertises configuration BPDUs with itself as the root bridge.
Phase 4. SW3 receives the configuration BPDU with the Topology Change flag from SW1. SW3 reduces the MAC address age timer to the forward delay timer to flush out older MAC entries. SW3 receives SW2’s inferior BPDUs and discards them as it is still receiving superior BPDUs from SW1.
Phase 5. The Max Age timer on SW3 expires, and now SW3’s Gi1/0/2 port transitions from blocking to listening state. SW3 can now forward the next configuration BPDU it receives from SW1 to SW2.
Phase 6. SW2 receives SW1’s configuration BPDU via SW3 and recognizes it as superior. It marks its Gi1/0/3 interface as the root port and transitions it to the listening state.
The total convergence time for SW2 is 52 seconds: 20 seconds for the Max Age timer on SW3, 2 seconds for the configuration BPDU from SW3, 15 seconds for the listening state on SW2, and 15 seconds for the learning state.
Indirect Failures
There are some failure scenarios where STP communication between switches is impaired or filtered while the network link remains up. This situation is known as an indirect link failure, and timers are required to detect and remediate the topology. Figure 2-5 illustrates an impediment or data corruption on the link between SW1 and SW3 along with the logic to resolve the loss of network traffic:
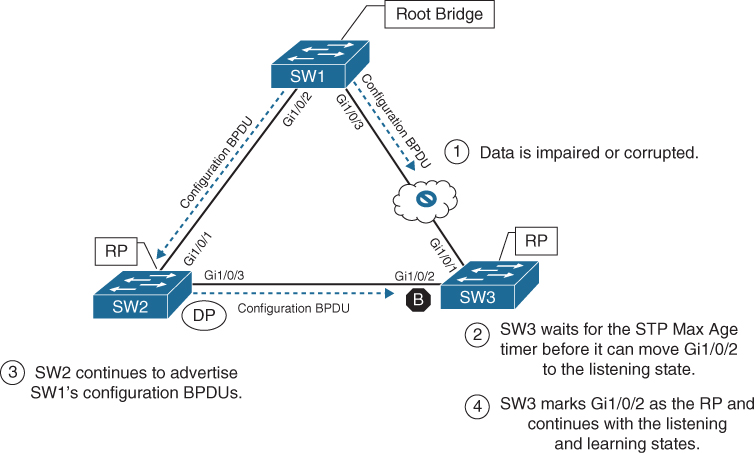
Figure 2-5 Convergence with Indirect Link Failure
Phase 1. An event occurs that impairs or corrupts data on the link. SW1 and SW3 still report a link up condition.
Phase 2. SW3 stops receiving configuration BPDUs on its RP. It keeps a cached entry for the RP on Gi1/0/1. SW1’s configuration BPDUs that are being transmitted via SW2 are discarded as its Gi1/0/2 port is in a blocking state.
Once SW3’s Max Age timer expires and flushes the RP’s cached entry, SW3 transitions Gi1/0/2 from blocking to listening state.
Phase 3. SW2 continues to advertise SW1’s configuration BPDUs toward SW3.
Phase 4. SW3 receives SW1’s configuration BPDU via SW2 on its Gi1/0/2 interface. This port is now marked as the RP and continues to transition through the listening and learning states.
The total time for reconvergence on SW3 is 52 seconds: 20 seconds for the Max Age timer on SW3, 2 seconds for the configuration BPDU advertisement on SW2, 15 seconds for the listening state on SW3, and 15 seconds for the learning state on SW3.
Rapid Spanning Tree Protocol

802.1D did a decent job of preventing Layer 2 forwarding loops, but it used only one topology tree, which introduced scalability issues. Some larger environments with multiple VLANs need different STP topologies for traffic engineering purposes (for example, loadbalancing, traffic steering). Cisco created Per-VLAN Spanning Tree (PVST) and Per-VLAN Spanning Tree Plus (PVST+) to allow more flexibility.
PVST and PVST+ were proprietary spanning protocols. The concepts in these protocols were incorporated with other enhancements to provide faster convergence into the IEEE 802.1W specification, known as Rapid Spanning Tree Protocol (RSTP).

RSTP (802.1W) Port States
RSTP reduces the number of port states to three:
Discarding: The switch port is enabled, but the port is not forwarding any traffic to ensure that a loop is not created. This state combines the traditional STP states disabled, blocking, and listening.
Learning: The switch port modifies the MAC address table with any network traffic it receives. The switch still does not forward any other network traffic besides BPDUs.
Forwarding: The switch port forwards all network traffic and updates the MAC address table as expected. This is the final state for a switch port to forward network traffic.
RSTP (802.1W) Port Roles
RSTP defines the following port roles:
Root port (RP): A network port that connects to the root switch or an upstream switch in the spanning-tree topology. There should be only one root port per VLAN on a switch.
Designated port (DP): A network port that receives and forwards frames to other switches. Designated ports provide connectivity to downstream devices and switches. There should be only one active designated port on a link.
Alternate port: A network port that provides alternate connectivity toward the root switch through a different switch.
Backup port: A network port that provides link redundancy toward the current root switch. The backup port cannot guarantee connectivity to the root bridge in the event that the upstream switch fails. A backup port exists only when multiple links connect between the same switches.
RSTP (802.1W) Port Types
RSTP defines three types of ports that are used for building the STP topology:
Edge port: A port at the edge of the network where hosts connect to the Layer 2 topology with one interface and cannot form a loop. These ports directly correlate to ports that have the STP portfast feature enabled.
Root port: A port that has the best path cost toward the root bridge. There can be only one root port on a switch.
Point-to-point port: Any port that connects to another RSTP switch with full duplex. Full-duplex links do not permit more than two devices on a network segment, so determining whether a link is full duplex is the fastest way to check the feasibility of being connected to a switch.

Building the RSTP Topology
With RSTP, switches exchange handshakes with other RSTP switches to transition through the following STP states faster. When two switches first connect, they establish a bidirectional handshake across the shared link to identify the root bridge. This is straightforward for an environment with only two switches; however, large environments require greater care to avoid creating a forwarding loop. RSTP uses a synchronization process to add a switch to the RSTP topology without introducing a forwarding loop. The synchronization process starts when two switches (such as SW1 and SW2) are first connected. The process proceeds as follows:
As the first two switches connect to each other, they verify that they are connected with a point-to-point link by checking the full-duplex status.
They establish a handshake with each other to advertise a proposal (in configuration BPDUs) that their interface should be the DP for that port.
There can be only one DP per segment, so each switch identifies whether it is the superior or inferior switch, using the same logic as in 802.1D for the system identifier (that is, the lowest priority and then the lowest MAC address). Using the MAC addresses from Figure 2-1, SW1 (0062.ec9d.c500) is the superior switch to SW2 (0081.c4ff.8b00).
The inferior switch (SW2) recognizes that it is inferior and marks its local port (Gi1/0/1) as the RP. At that same time, it moves all non-edge ports to a discarding state. At this point in time, the switch has stopped all local switching for non-edge ports.
The inferior switch (SW2) sends an agreement (configuration BPDU) to the root bridge (SW1), which signifies to the root bridge that synchronization is occurring on that switch.
The inferior switch (SW2) moves its RP (Gi1/0/1) to a forwarding state. The superior switch moves its DP (Gi1/0/2) to a forwarding state, too.
The inferior switch (SW2) repeats the process for any downstream switches connected to it.
The RSTP convergence process can occur quickly, but if a downstream switch fails to acknowledge the proposal, the RSTP switch must default to 802.1D behaviors to prevent a forwarding loop.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple of choices for exam preparation: the exercises here, Chapter 30, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 2-3 lists these key topics and the page number on which each is found.

Table 2-3 Key Topics for Chapter 2
Key Topic Element |
Description |
Page |
List |
802.1D port types |
|
Section |
STP key terminology |
|
Section |
Root bridge election |
|
Section |
Locating root ports |
|
Section |
STP topology changes |
|
Section |
RSTP |
|
Section |
RSTP (802.1W) port states |
|
Section |
Building the RSTP topology |
Complete Tables and Lists from Memory
There are no memory tables in this chapter.
Define Key Terms
Define the following key terms from this chapter and check your answers in the Glossary:
Use the Command Reference to Check Your Memory
Table 2-4 lists the important commands from this chapter. To test your memory, cover the right side of the table with a piece of paper, read the description on the left side, and see how much of the command you can remember.
Table 2-4 Command Reference
Task |
Command Syntax |
Set the STP max age |
spanning-tree vlan vlan-id max-age |
Set the STP hello interval |
spanning-tree vlan vlan-id hello-time hello-time |
Set the STP forwarding delay |
spanning-tree vlan vlan-id forward-time forward-time |
Display the STP root bridge and cost |
show spanning-tree root |
Display the STP information (root bridge, local bridge, and interfaces) for one or more VLANs |
show spanning-tree [vlan vlan-id] |
Identify when the last TCN occurred and which port was the reason for it. |
show spanning-tree [vlan vlan-id] detail |